Security protocol analysis method and device
A security protocol and analysis method technology, which is applied in the field of security protocol analysis methods and devices, can solve problems such as difficult to realize automatic analysis and authentication attacks without considering the special algebraic properties of the protocol, and achieve automatic analysis, enhanced message processing capabilities, The effect of increasing the probability of analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
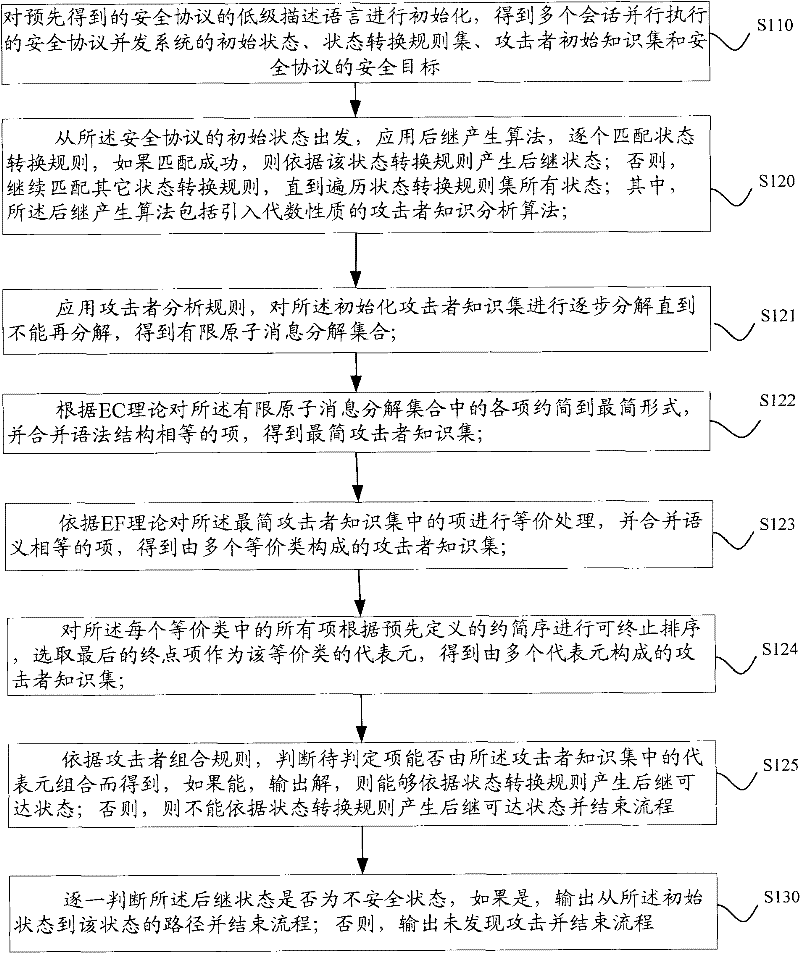
[0054] see figure 1 , figure 1 It is a flowchart of a security protocol analysis method according to an embodiment of the present application. The security protocol analysis method may be the following steps:
[0055] S110: Initialize the pre-obtained low-level description language of the security protocol to obtain the initial state of the security protocol, the state transition rule set, the attacker's initial knowledge set, and the security goal of the security protocol.
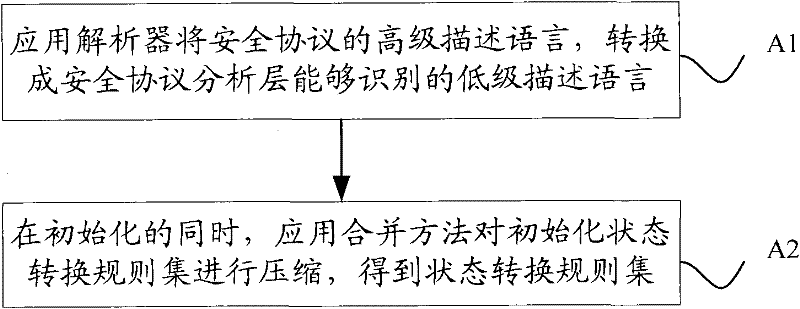
[0056] In this step, the low-level description language is used as the input of the security protocol analysis layer, and the low-level description language is initialized and preprocessed to obtain the initial state, the state transition rule set, and the attacker's initial knowledge of the security protocol concurrent system executed in parallel by multiple sessions Security goals for sets and security protocols.
[0057] At the same time of initialization, apply the merging method to the initializat...
Embodiment 2
[0070] This embodiment will introduce the specific steps and flow of the attacker knowledge analysis algorithm in the first method embodiment. First analyze the existence of the attacker's knowledge analysis algorithm:
[0071] According to the characteristics of the equation set E applied in the analysis of most of the existing security protocols, the equation set E can be divided into two categories, one is the equivalence class induced by a limited number of elements. A collection of formulas, such as x 1 ⊕x 2 ≈x 2 ⊕x 1 ,(x 1 ⊕x 2 )⊕x 3 ≈x 1 ⊕(x 2 ⊕x 3 ) and so on, the set of these equations is called a finite set of equations, and the equivalence theory induced by it is called EF theory; one is a set of equations whose induced rewriting relationship can make the depth of terms smaller ,Such as exp ( exp ( x 1 , x ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com