Method and system for updating authentication key of user equipment and user equipment
A technology of user equipment and update method, which is applied in the field of authentication code update, can solve the problem of not being able to limit the communication function of the copy card, and achieve the effect of protecting legal rights and achieving low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
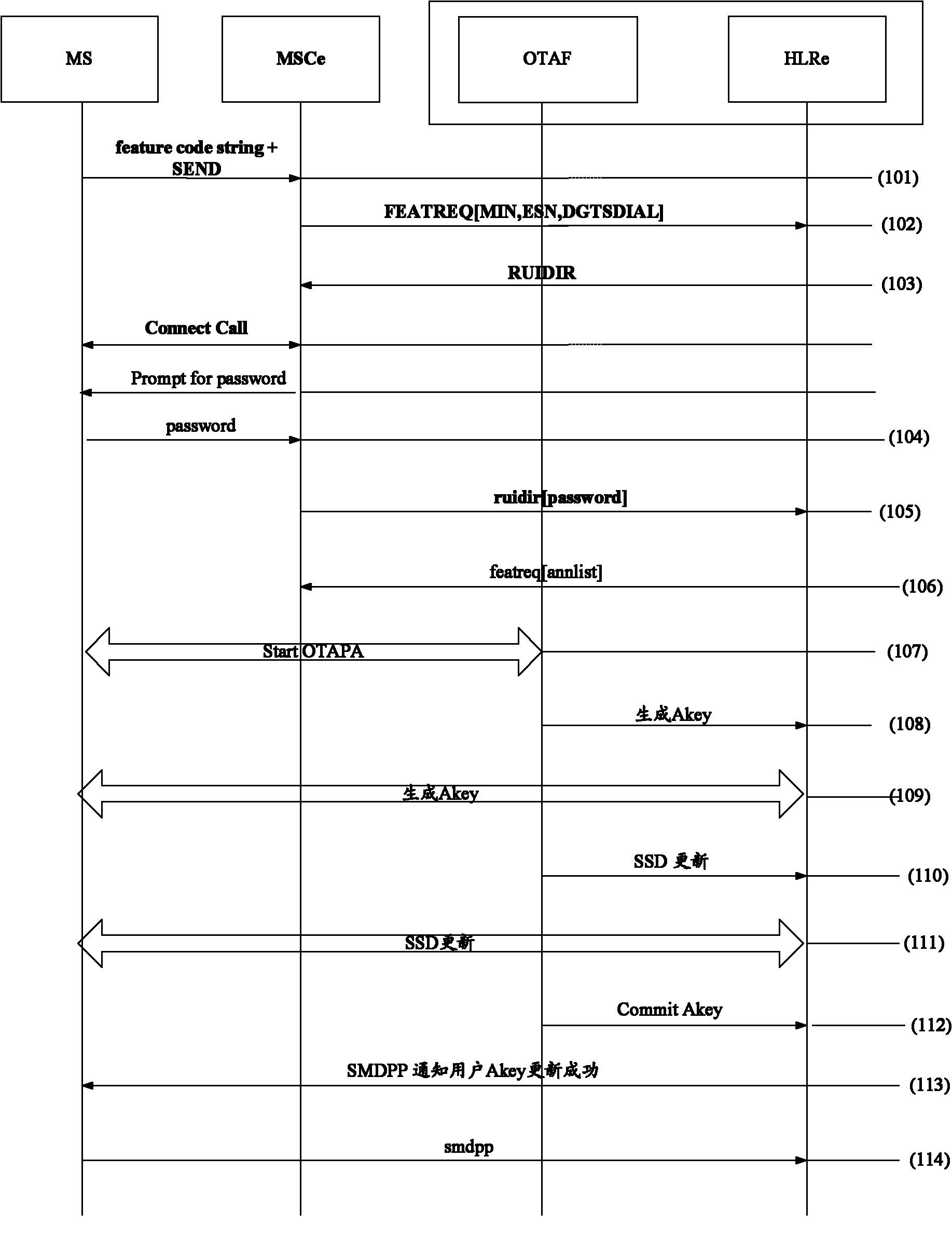
[0061] In this example, the user initiates an Akey update through a supplementary service. figure 1 It is a flowchart of a method for updating an authentication code of a user equipment according to Embodiment 1 of the present invention, as shown in figure 1 As shown, the method for updating the user equipment authentication code in this example specifically includes the following steps:
[0062] In step 101, an Akey update process is initiated through a supplementary service operation of the UE.
[0063] In the present invention, the so-called supplementary service operation is a newly added service specially used for initiating an Akey update request for UE; this service can be provided as user's subscription data, or as a value-added service provided by an operator. Those skilled in the art should understand that it is easy to make the UE initiate a certain service request.
[0064] In the present invention, the UE sends an Akey update request to a Mobile Switching Center...
Embodiment 2
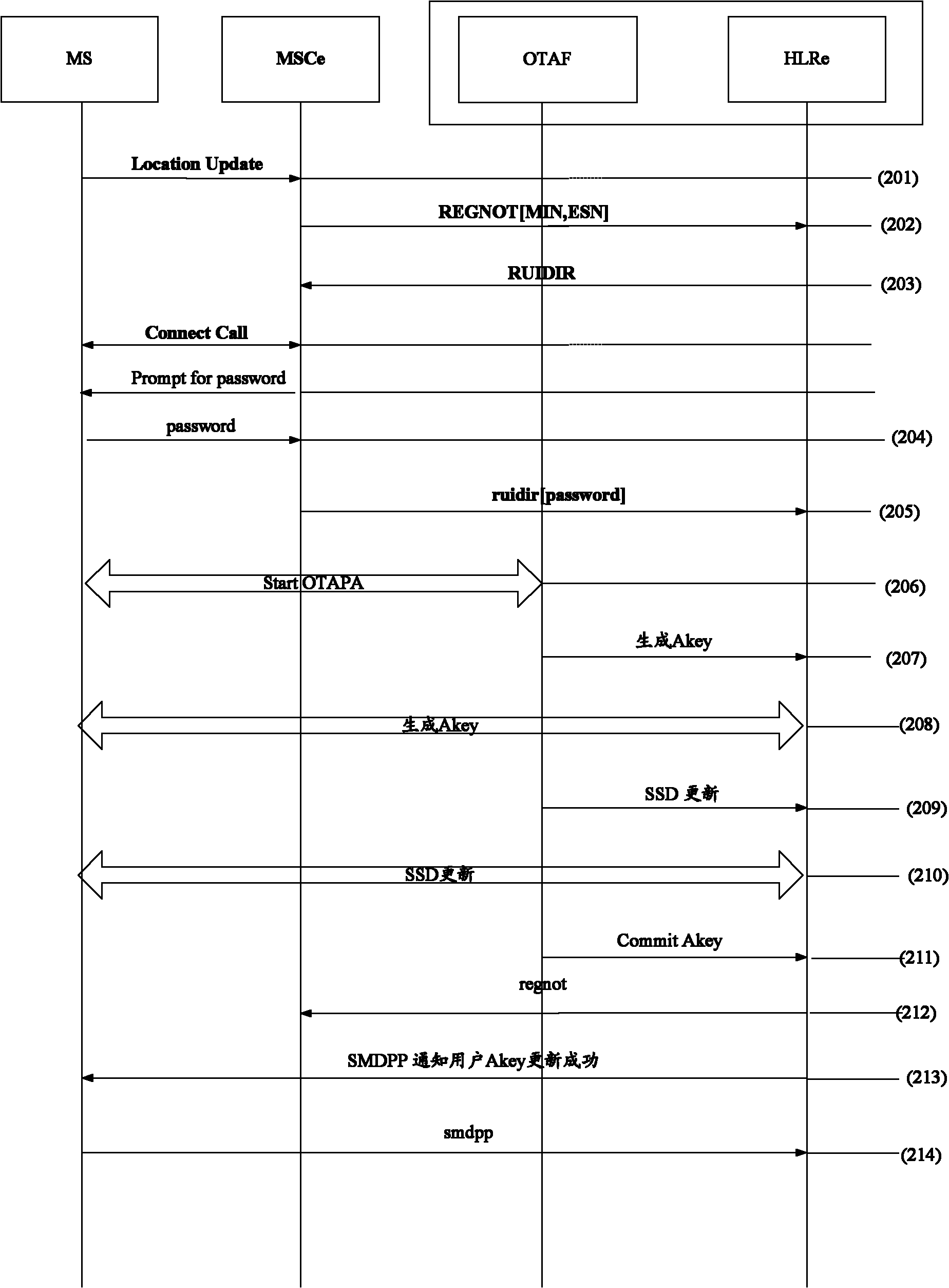
[0080] In this example, the operator updates the Akey periodically. figure 2 It is a flow chart of the method for updating the user equipment authentication code in Embodiment 2 of the present invention, as shown in figure 2 As shown, the method for updating the user equipment authentication code in this example specifically includes the following steps:
[0081] Step 201, the user initiates a location update.
[0082] Step 202, MSCe triggers a registration message to HLRe.
[0083] Step 203, HLRe determines whether the user has the authority to update the Akey, and determines whether the update time threshold set by the operator has been reached. If the time threshold for updating the Akey has been reached, the HLRe instructs the MSCe to initiate a RUIDIR operation.
[0084] In step 204, the MSCe initiates a RUIDIR operation, instructing the user to input the service operation password.
[0085] Step 205, MSCe collects the service operation password and sends it to HLRe...
Embodiment 3
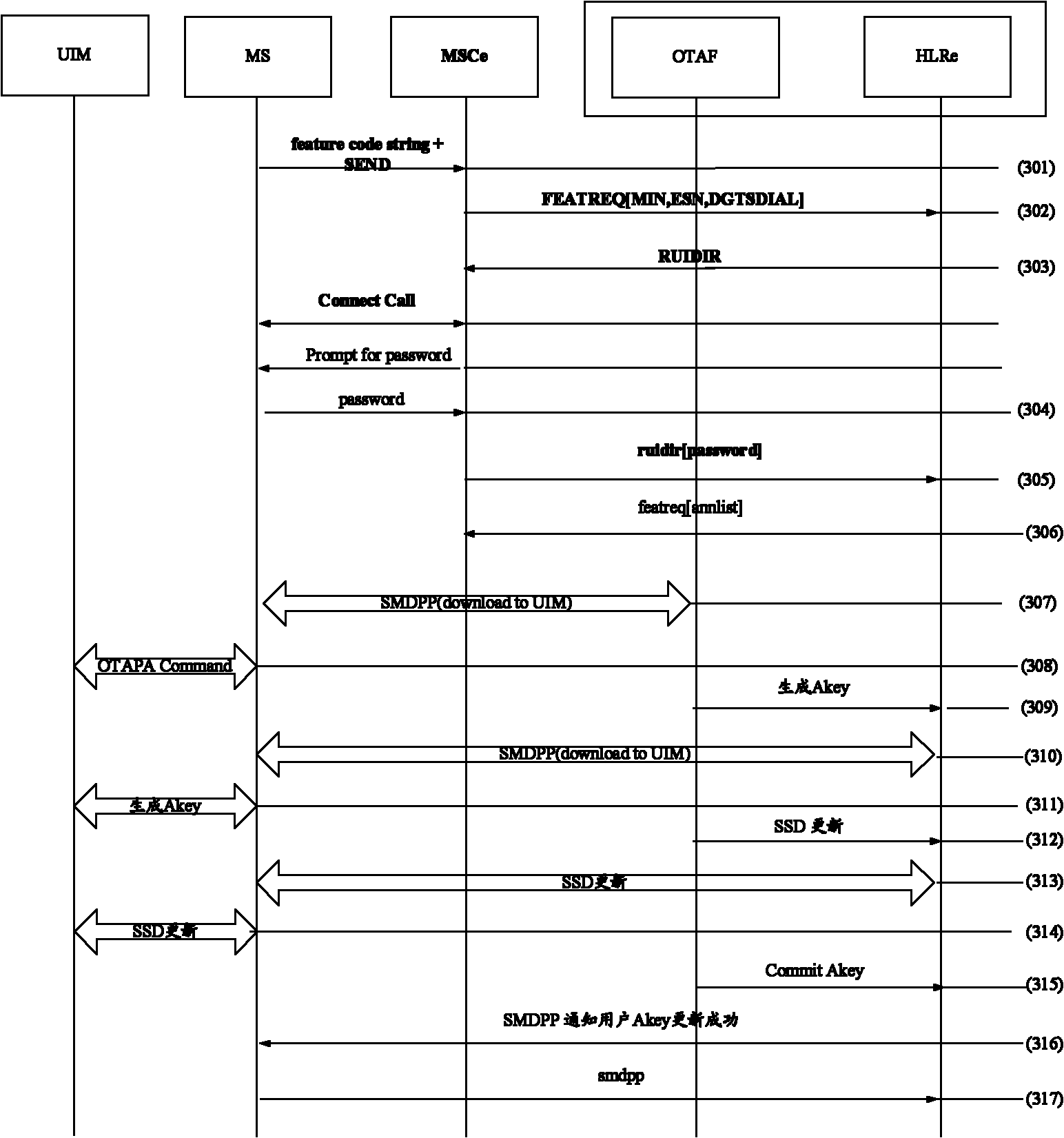
[0093] In this example, the user initiates a UIM card Akey update through a supplementary service. image 3 It is a flowchart of a method for updating an authentication code of a user equipment according to Embodiment 3 of the present invention, as shown in image 3 As shown, the method for updating the user equipment authentication code in this example specifically includes the following steps:
[0094] In step 301, the user initiates an Akey update process through a supplementary service operation.
[0095] In step 302, the MSCe initiates a FEATREQ to the HLRe, carrying parameters such as the user's MIN, ESN, and supplementary service code.
[0096] In step 303, the HLRe determines whether the user has the authority to update the Akey, and instructs the MSCe to initiate a RUIDIR operation.
[0097] In step 304, the MSCe initiates a RUIDIR operation, instructing the user to input the service operation password.
[0098] Step 305, MSCe collects the service operation passwor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com