Method for realizing trusted computing platform in embedded device
An embedded device and trusted computing technology, applied in the field of information security, to achieve the effect of reliable security guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
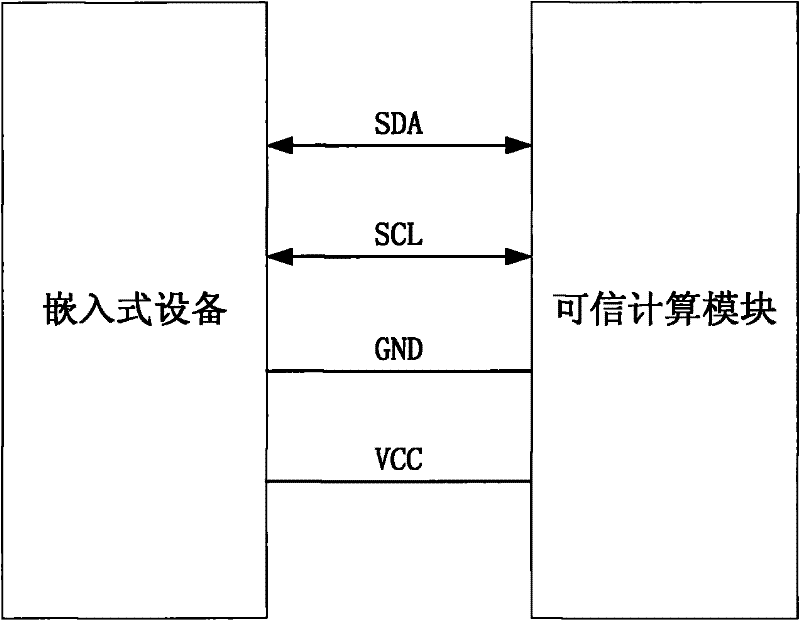
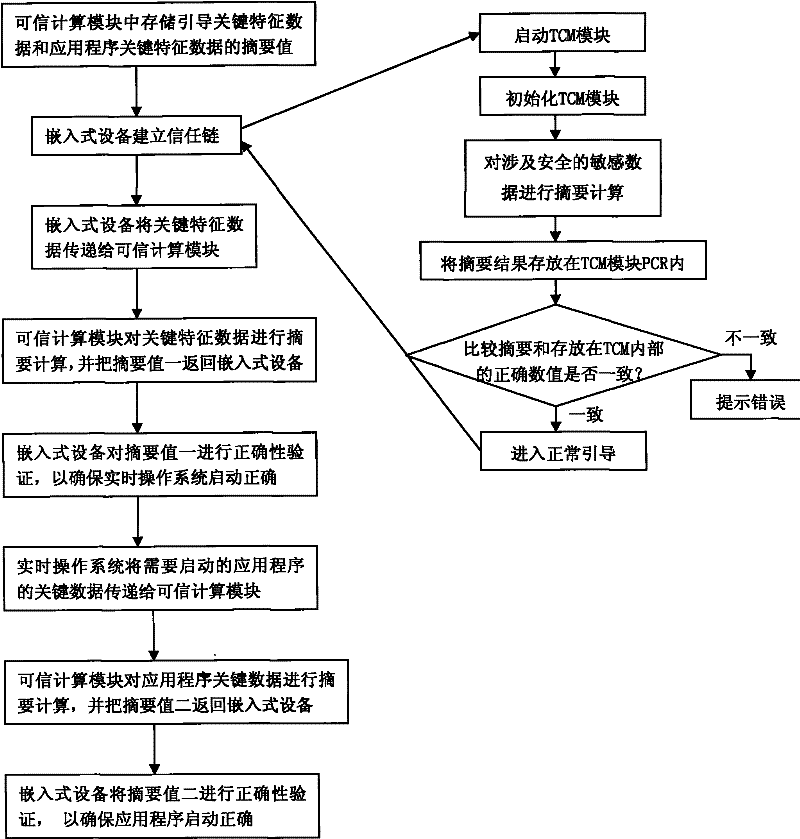
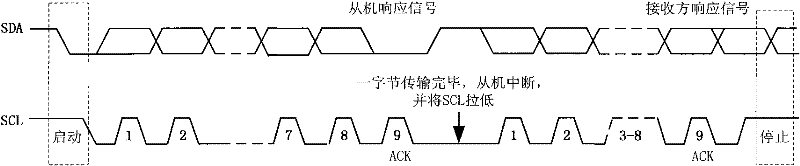
[0038] see figure 1 and figure 2 , the present invention realizes the method step of trustworthy computing platform in embedded device as:
[0039] 1) Connect the embedded device containing the real-time operating system to the trusted computing module through the serial interface;
[0040] 2) Store the summary value of boot key feature data and application program key feature data in the trusted computing module.
[0041] 3) The embedded device establishes a chain of trust during the boot phase, and the method for establishing the chain of trust is:
[0042] a) Start the trusted computing module and initialize it;
[0043] b) Send the security-related sensitive data to the trusted computing module for summary calculation;
[0044] c) store the result of the digest calculation in the platform configuration register of the trusted computing module;
[0045] d) Compare the summary calculation result with the summary value stored in the non-volatile storage area inside the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com