Secure Transaction Authentication
A technology for safe transactions and transactions, applied in security devices, user identity/authority verification, instruments, etc., can solve problems such as input, abuse, and security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
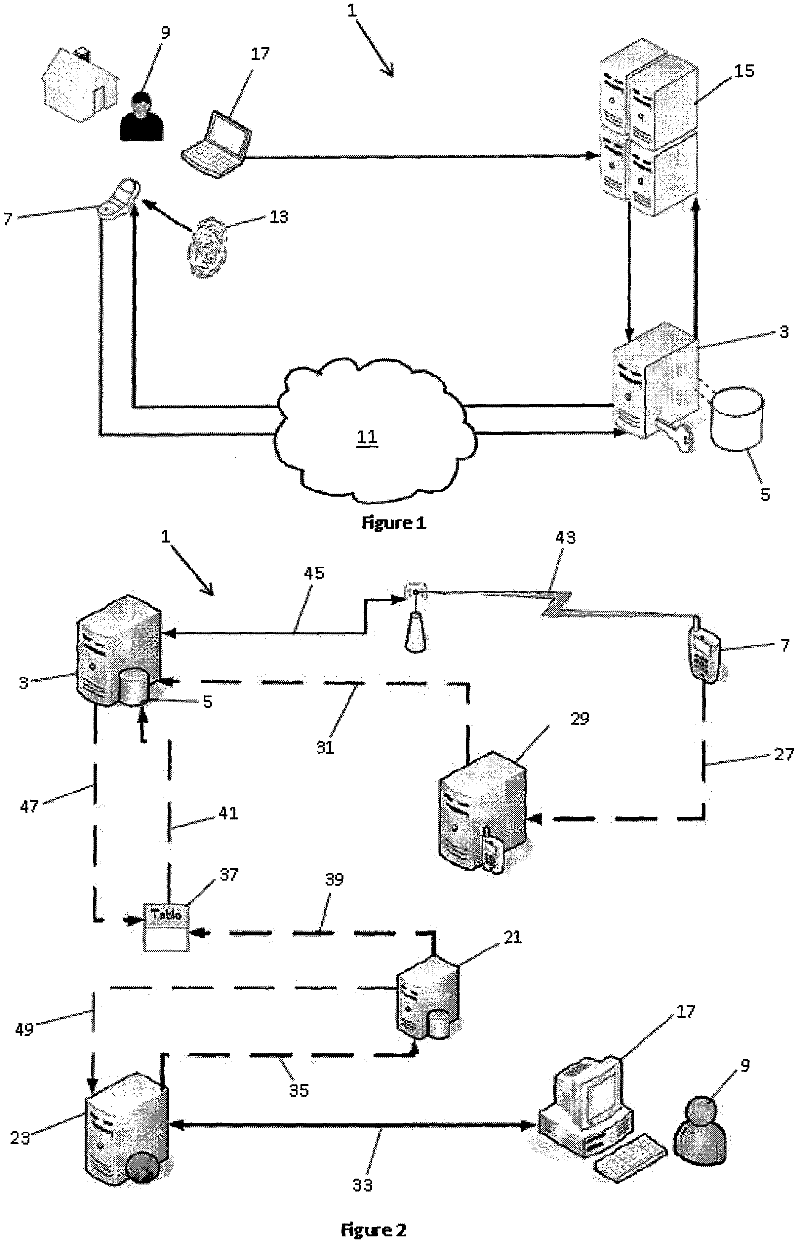
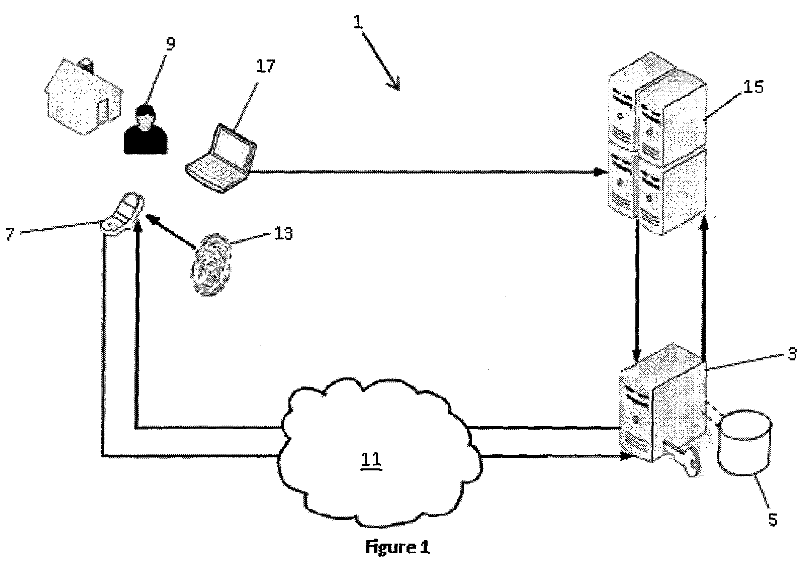
[0026] In the simplest arrangement, as shown in Figure 1, a secure transaction authentication system (1) includes an authentication server (3), an authentication server (5) and a mobile communication device application software (not shown). The application software is configured to be installed on a mobile communication device (7), which in most cases is a mobile phone of a user (9). It should be understood that the server (3), database (5) and application software are implemented, operated and maintained by authorized service providers, and provide an authentication platform on which authentication operations can be performed.
[0027] In order to utilize the authentication system (1), the user (9) must be registered with an authentication service provider. Registration can be completed after the user (9) downloads the application software to his / her mobile phone (7) and installs it on the mobile phone through the mobile phone Internet browser software on the mobile phone (7)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com