Method for hiding running coding of confidential information
A technology of secret information and encoding, which is applied in the field of information hiding and can solve problems such as visual distortion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
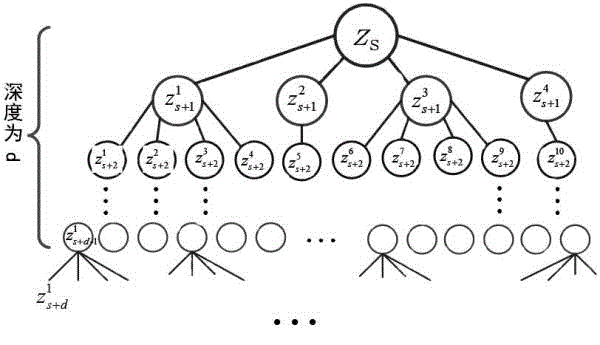
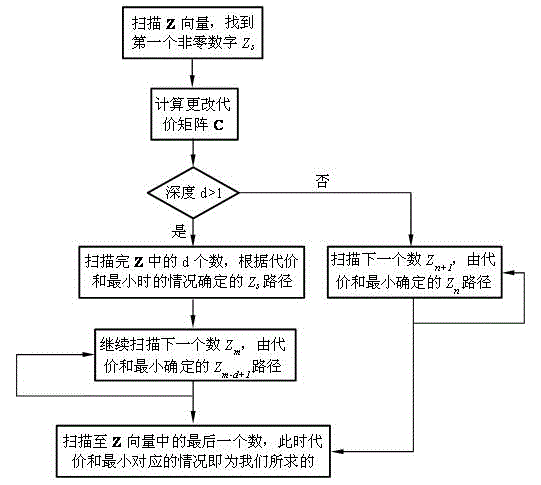
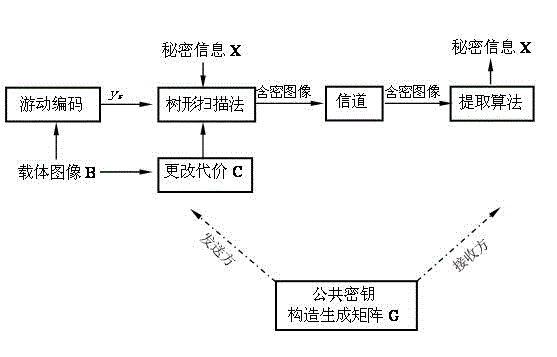
[0050] Embodiment one: see figure 1 , figure 2 and image 3 , the mobile code hiding method of confidential information is characterized in that: one is the secret information embedding process of the sender, and the other is the secret information extraction process of the receiver. The specific operation steps are as follows:
[0051] 1. Embedding process of recipient’s secret information:
[0052] a. Define the transmission rate of the system k , k = the number of lowest bits of the carrier / the number of bits of secret information, and it is considered to be a positive integer, and it is always greater than 1.
[0053] assume existing L The secret information to be embedded is expressed as: X = [x 1 , x 2 ,...,x L ],vector X is a binary sequence, namely x i ∈{0,1}, i =1,2,..., L .
[0054] Express the lowest bit of the carrier pixel that can be embedded with secret data as:
[0055] ,
[0056] here, b i,j The value of is 0 or 1, indicating the lowest b...
Embodiment 2
[0073] Embodiment 2: This embodiment is basically the same as Embodiment 1, and an example is described in conjunction with the accompanying drawings. The operating steps of the mobile code hiding method for this confidential information are as follows:
[0074] 1. Embedding process of recipient’s secret information:
[0075] 1. The original carrier image is usually relatively large. In order to illustrate the working principle of this embodiment, the Figure 4 An image block with a size of 10×6 in the upper left corner (for the pixel values of the image block, see Figure 5 ), here in order to facilitate the calculation of the change cost value of each pixel, we take the 8×4 block in the middle of the image block as the carrier space (actually, for the pixels located on the edge of the image, when calculating the change cost value, the points are correspondingly reduced counts). Figure 6 It is the LSB bit value of the 8×4 pixel block, that is, the carrier space B,
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com