Mobile terminal and starting-up method thereof
A mobile terminal and power-on password technology, which is applied in the field of communication, can solve problems such as the interruption of the boot process of legitimate users, and achieve the effect of ensuring unaffected, good privacy, and solving the interruption of the boot process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0026] DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENTS The present invention will be described in detail below with reference to the accompanying drawings and examples. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
[0027] The embodiment of the present invention considers that in order to enhance the security of starting up the existing mobile terminal, the user needs to enter the correct power-on password to complete the power-on process during the power-on process. The service provides a method for starting up a mobile terminal and the mobile terminal, wherein the mobile terminal here generally refers to a user equipment (UE, User Equipment) such as a mobile phone, and the technology will be described below.
[0028] figure 1 It is a flowchart of a booting method of a mobile terminal according to an embodiment of the present invention, such as figure 1 ...
Embodiment 1
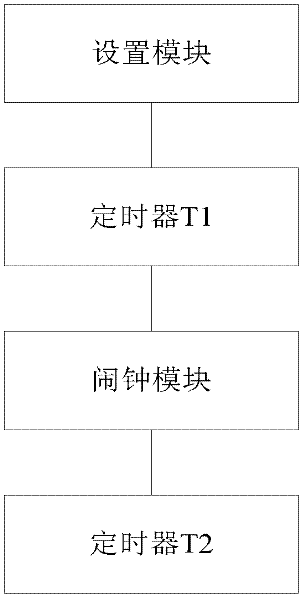
[0042] In this embodiment, when the password protection is enabled by the user, the user is reminded when the password is turned on. In order to help the user avoid the problem that the mobile phone cannot be turned on normally due to forgetting to enter the password. In this embodiment, an alarm clock is used as an example for illustration, see figure 2 The schematic structural diagram of the mobile terminal shown, the mobile terminal includes the following modules:
[0043] 1. The setting module is used for the user to choose to enable and disable the password protection function, and the time S1 to activate the reminder function, and notify the UE of the user's choice.
[0044] 2. Timer T1, the user calculates the time from when the UE pops up the password input interface to when the user enters the password operation. If the time exceeds the preset time S1, a notification will be sent to the UE.
[0045] 3. Alarm clock module: When the user does not perform a password o...
Embodiment 2
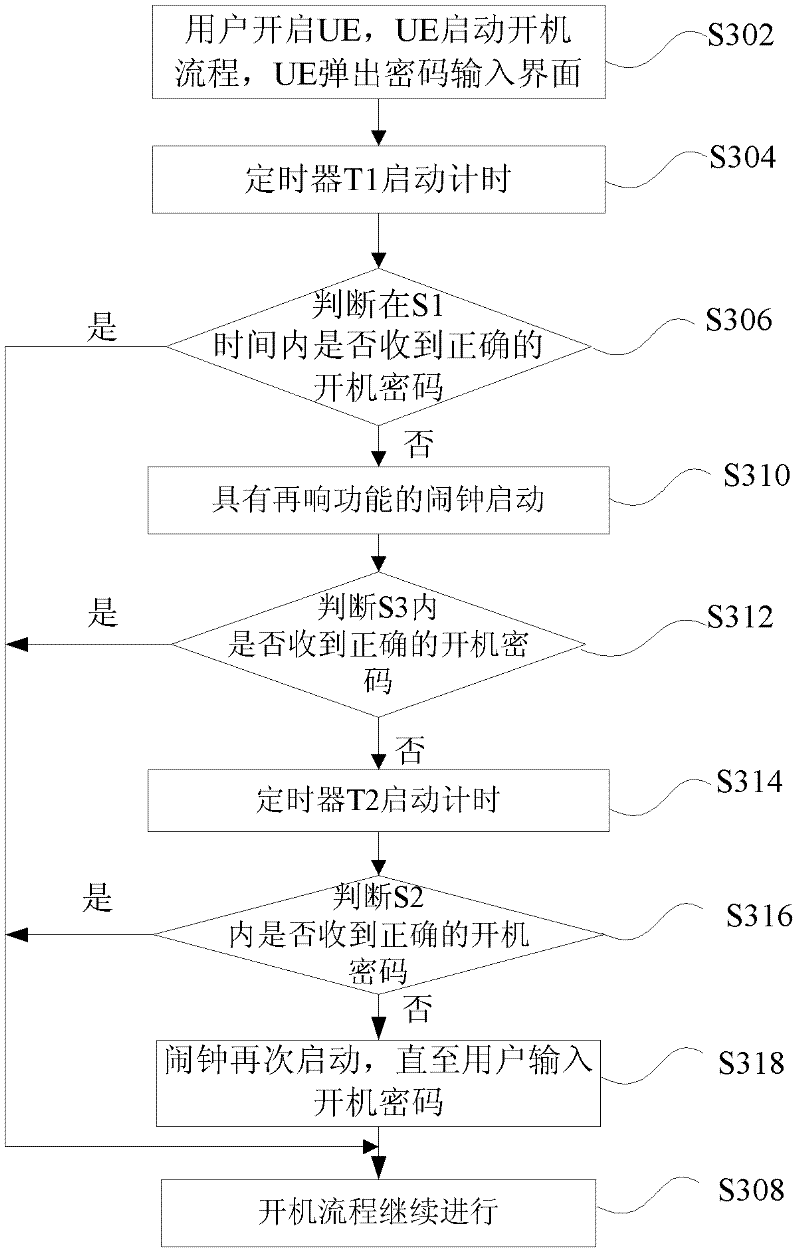
[0063] At present, there are many password protection methods for mobile terminal equipment. This embodiment takes the most commonly used PIN code protection method as an example to introduce the power-on method of the mobile terminal (ie UE) based on setting the power-on password. The UE in this embodiment is set. the above figure 2 For each module shown, before the start-up method is performed, the user enters the setting module and selects the function of "requiring a PIN code when using a mobile phone" to be enabled; the setting option "set alarm clock reminder time" is S1. Then, the user enters the alarm clock module, sets the option "alarm clock ringing duration" as S3; sets "alarm clock re-ring time" as S2. After completing these settings, the boot process of the UE is as follows:
[0064] Step 1: the user turns on the UE when the UE is turned off. The UE executes the power-on process, and a PIN code input interface pops up. At the same time, the timer T1 starts tim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com