Data secure transmission method among multilevel information systems
An information system and data security technology, applied in the field of high-level protection, can solve the problems of unspecified safety marks, incompatibility, poor flexibility, etc., to eliminate information islands, promote information sharing, and improve efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be described below in conjunction with the accompanying drawings and specific embodiments.
[0053] basic concept
[0054] Before describing the specific implementation of the present invention in detail, some concepts involved in the present invention will be described uniformly.
[0055] (1), subject (Subject)
[0056] The subject in this application refers to the requester who initiates access to a certain type of resource or the initiator of the communication between the two parties. For example, users, hosts, subnets, address ranges, user groups, subnet groups, and address groups can all be defined as subjects.
[0057] (2), object (Object)
[0058] The object is a concept opposite to the subject, and it refers to the resources accessed by the subject. For example, files, databases, web services, ftp services, subnets, hosts, address ranges, address groups, etc., can all be defined as objects.
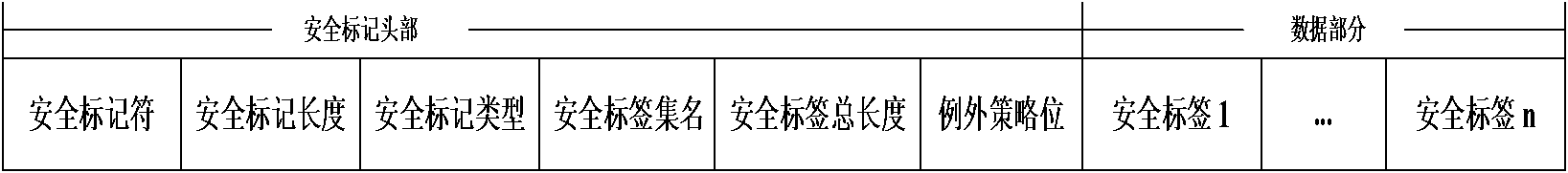
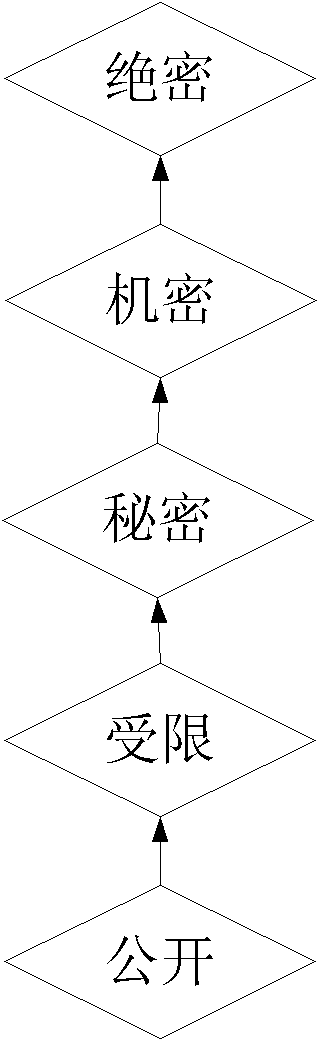
[0059] (3), Secure Label
[0060] The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com