Method and system for isolating computing environment
A computing environment and trusted computing technology, applied in computing, computer security devices, protection of internal/peripheral computer components, etc., can solve problems such as inability to apply application software
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
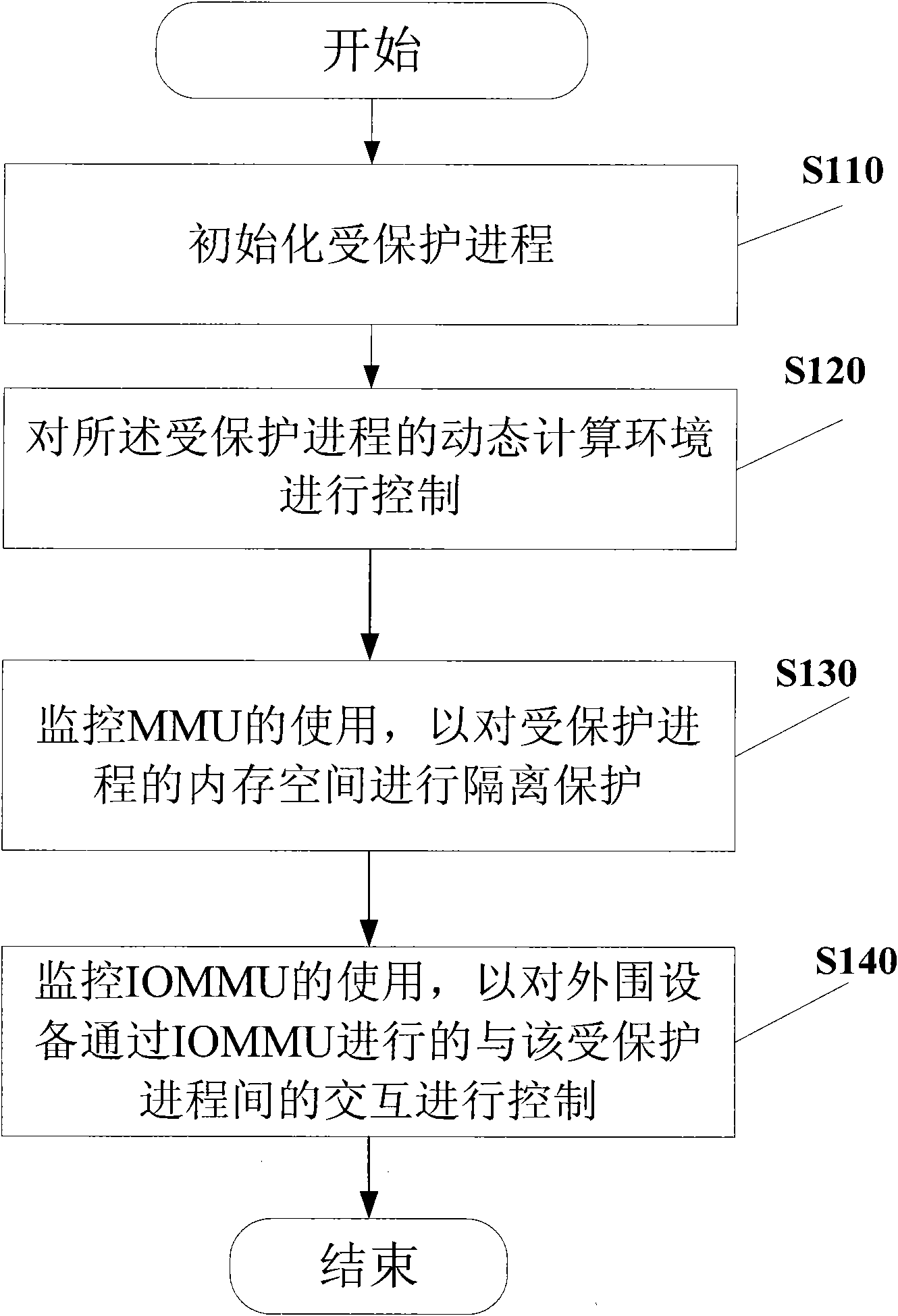
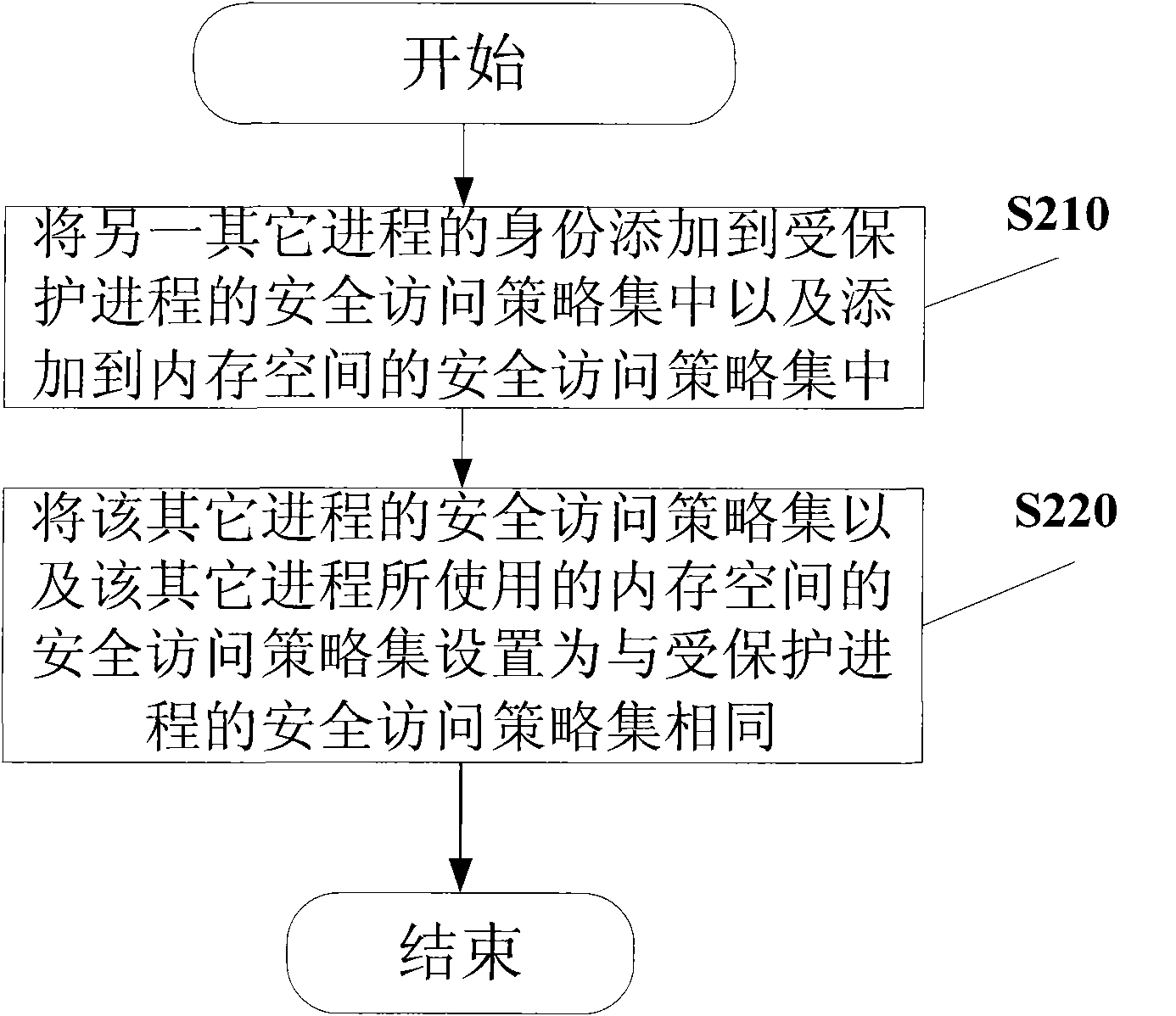
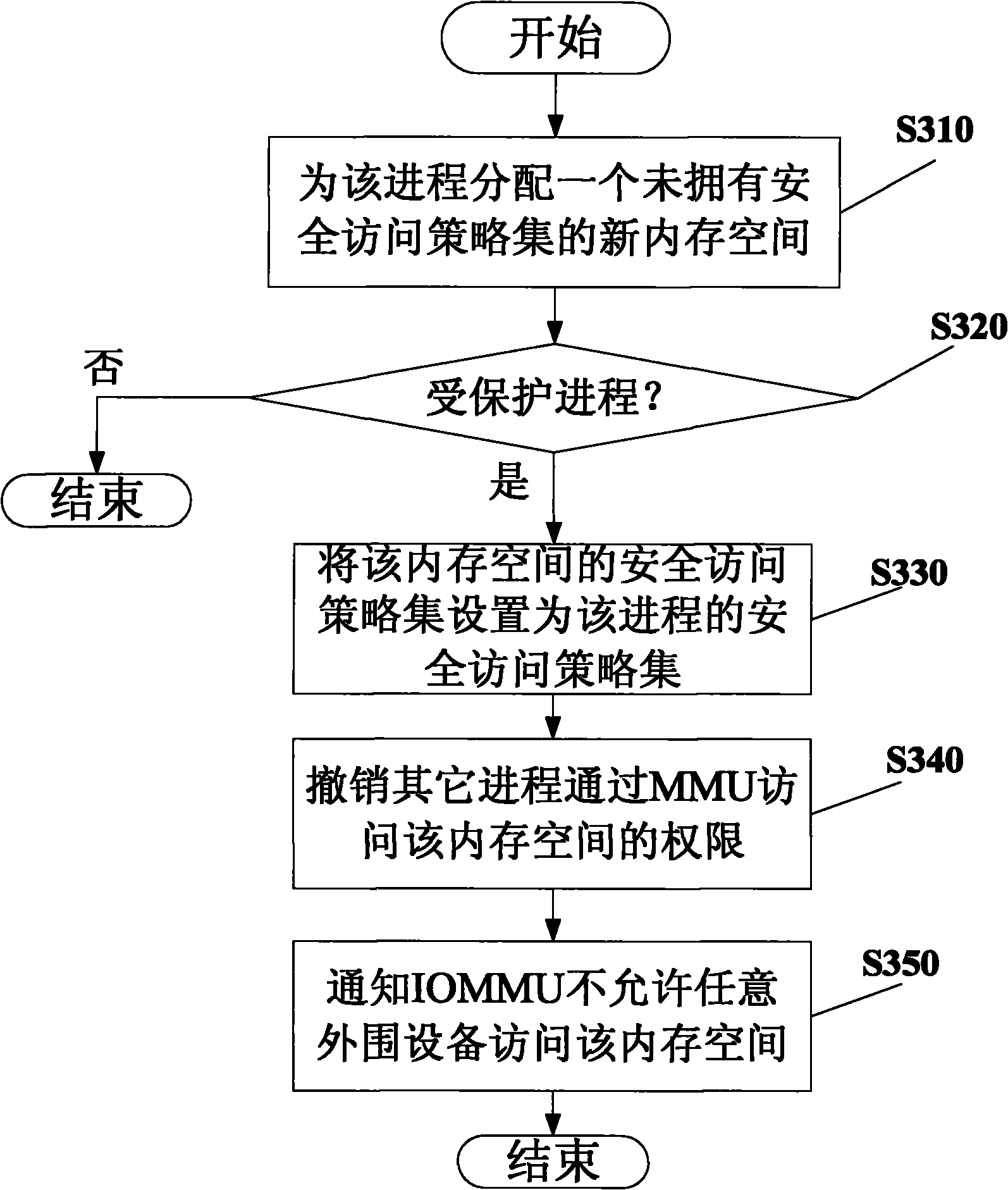
[0052] Firstly, the computing environment according to the present invention is introduced. The computing environment according to the present invention generally includes computing hardware with an open architecture (such as but not limited to, Intel X86 architecture) and a software stack.
[0053] Generally, the hardware architecture includes a Trusted Platform Module (TPM), a Program Control Unit (PCU), a Memory Management Unit (MMU) and an Input / Output Memory Management Unit (IOMMU).
[0054] When starting the software stack of the computing platform, the trusted platform module can measure the Root Trusted Computing Base (RTCB, Root Trusted Computing Base), and store the measurement result in the trusted platform module for future verification. The method and device for measuring, storing and verifying the RTCB by the trusted platform module are common techniques in the art and will not be described here. See, eg, US Patent Application filed by the present applicant (Atto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com