Link time delay detection method, source terminal, destination terminal and system
A detection method and technology of a detection system, applied in the field of communication, can solve problems such as failure to send business messages normally, failure of detected links to work normally, and high labor costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0070] The embodiment of the present invention provides a link delay detection method, such as figure 1 As shown, the method includes:
[0071] 101. Write the first time stamp and the detection message identification information into the detection message to obtain the first detection message, and send the first detection message to the sink end, and the first time stamp is sent by the source end The time value T1 of the first detection message.
[0072] 102. Receive the packet returned by the sink, and determine whether the packet returned by the sink is a second detection packet, where the second detection packet includes the detection packet identification information and a first timestamp , a second time stamp and a third time stamp, the second time stamp is the time value T2 when the first detection message arrives at the sink, and the third time stamp is the time when the sink sends the second The time value T3 of detecting the packet.
[0073] 103. When it is determi...
Embodiment 2
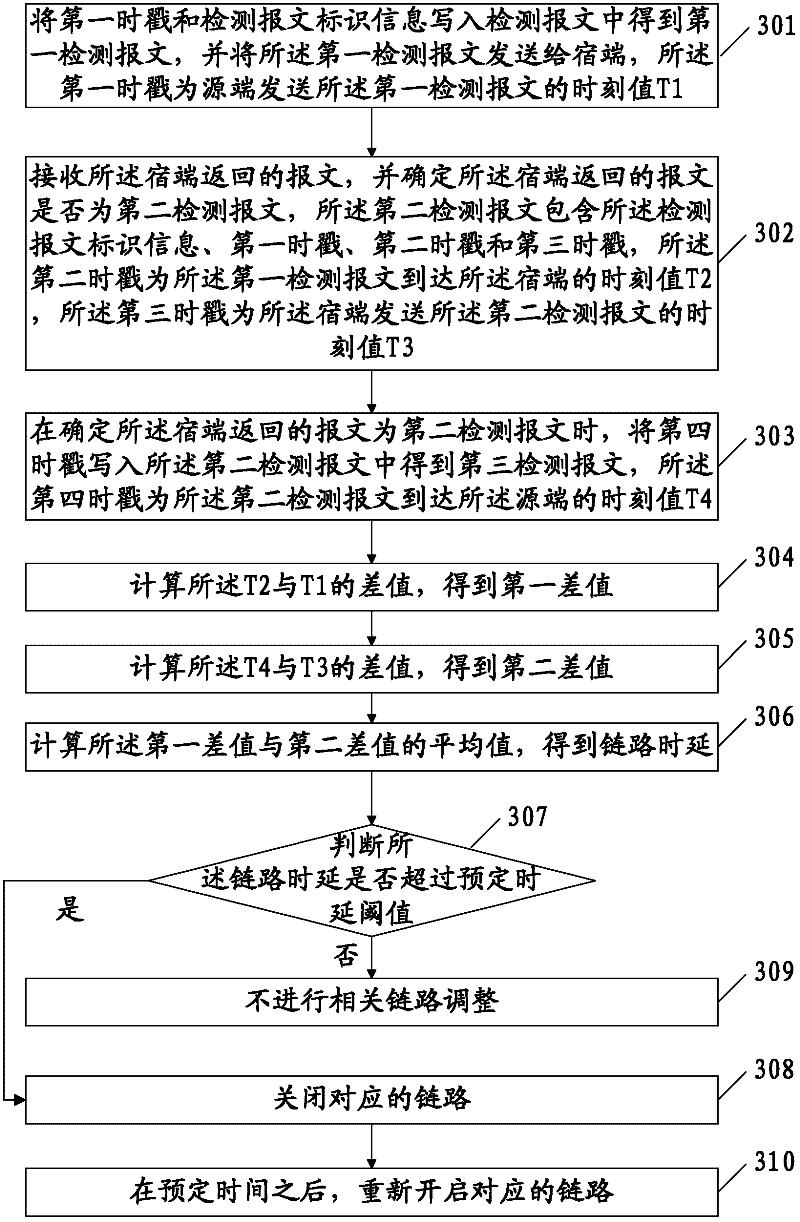
[0082] An embodiment of the present invention provides a link delay detection method, such as image 3 shown, including:
[0083] 301. Write the first time stamp and detection message identification information into the detection message to obtain the first detection message, and send the first detection message to the sink, and the first time stamp is sent by the source The time value T1 of the first detection message.
[0084] Wherein, the first timestamp is the time value T1 at which the source sends the first detection message, which is written into the message field of the detection message, for example, as shown in Table 1, it is a complete PPP message, Write T1 to the first 4 bytes of the message field. The address and control fields in the PPP message occupy 1 byte respectively, the protocol field occupies 2 bytes, the first 16 bytes of the message field are used to store 4 timestamp information, and the remaining 33 bytes in the message field It may not be used in ...
Embodiment 3
[0123] An embodiment of the present invention provides a source, such as Figure 5 As shown, it includes: a first time stamp unit 51 , a source determination unit 52 , a fourth time stamp unit 53 , and a calculation unit 54 .
[0124] The first time stamp unit 51 is configured to write the first time stamp and the detection message identification information into the detection message to obtain the first detection message, and send the first detection message to the sink end, the first detection message A timestamp is the time T1 when the source sends the first detection message.
[0125] The source determining unit 52 is configured to receive the message returned by the sink, and determine whether the message returned by the sink is a second detection message, and the second detection message includes the detection message identifier information, a first timestamp, a second timestamp, and a third timestamp; the second timestamp is the time value T2 when the first detection m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com