Method for realizing software authorization by using dual power supply system device independent of host computer in real time
A software authorization and power supply system technology, applied in computer security devices, electrical digital data processing, instruments, etc., can solve problems that cannot be solved fundamentally, wrong time information of software protection devices, and inability to obtain software usage time, etc. Achieve the effect of timely and reliable system time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail by giving examples below.
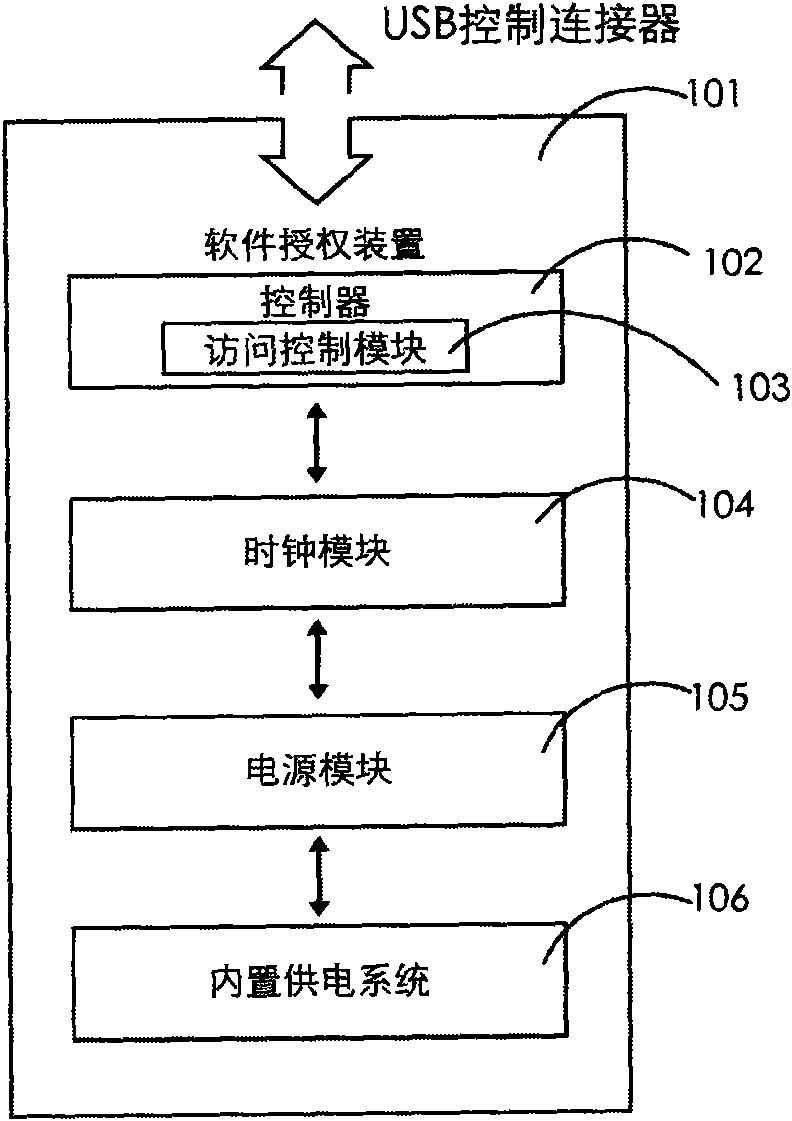
[0030] figure 1 It is a schematic structural diagram of the software authorization device of the present invention, such as figure 1 As shown, the software authorization device (101) involved in the present invention includes an access controller (102), a clock module (104), a power supply module (105), and a built-in power supply system (106). in:
[0031] The access controller (102) includes an access control module (103) for realizing the dialogue between the PC client and the software protection device: specifically: parsing the instructions from the PC client, and realizing the software developer setting the permission for the software to be accessed .
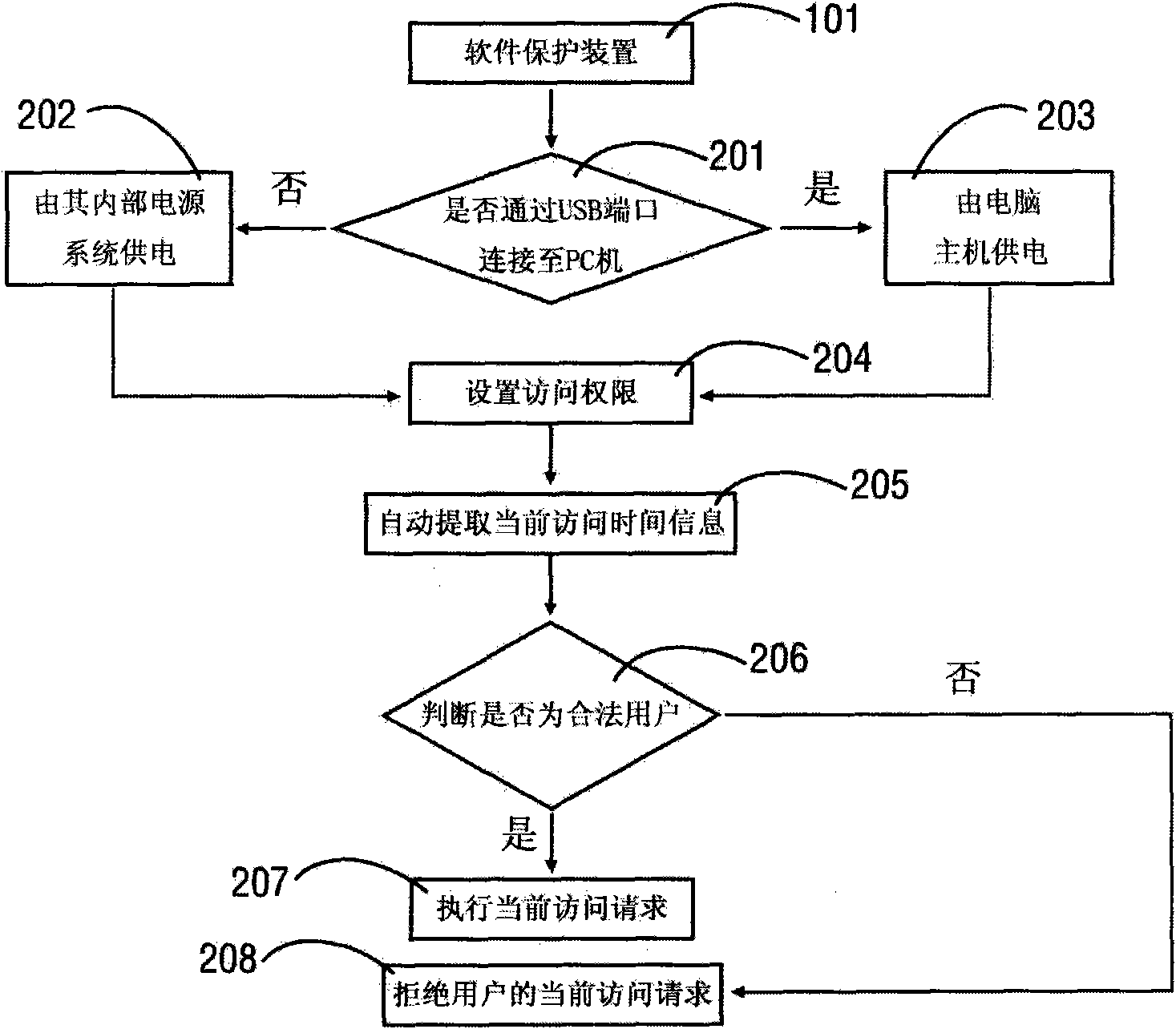
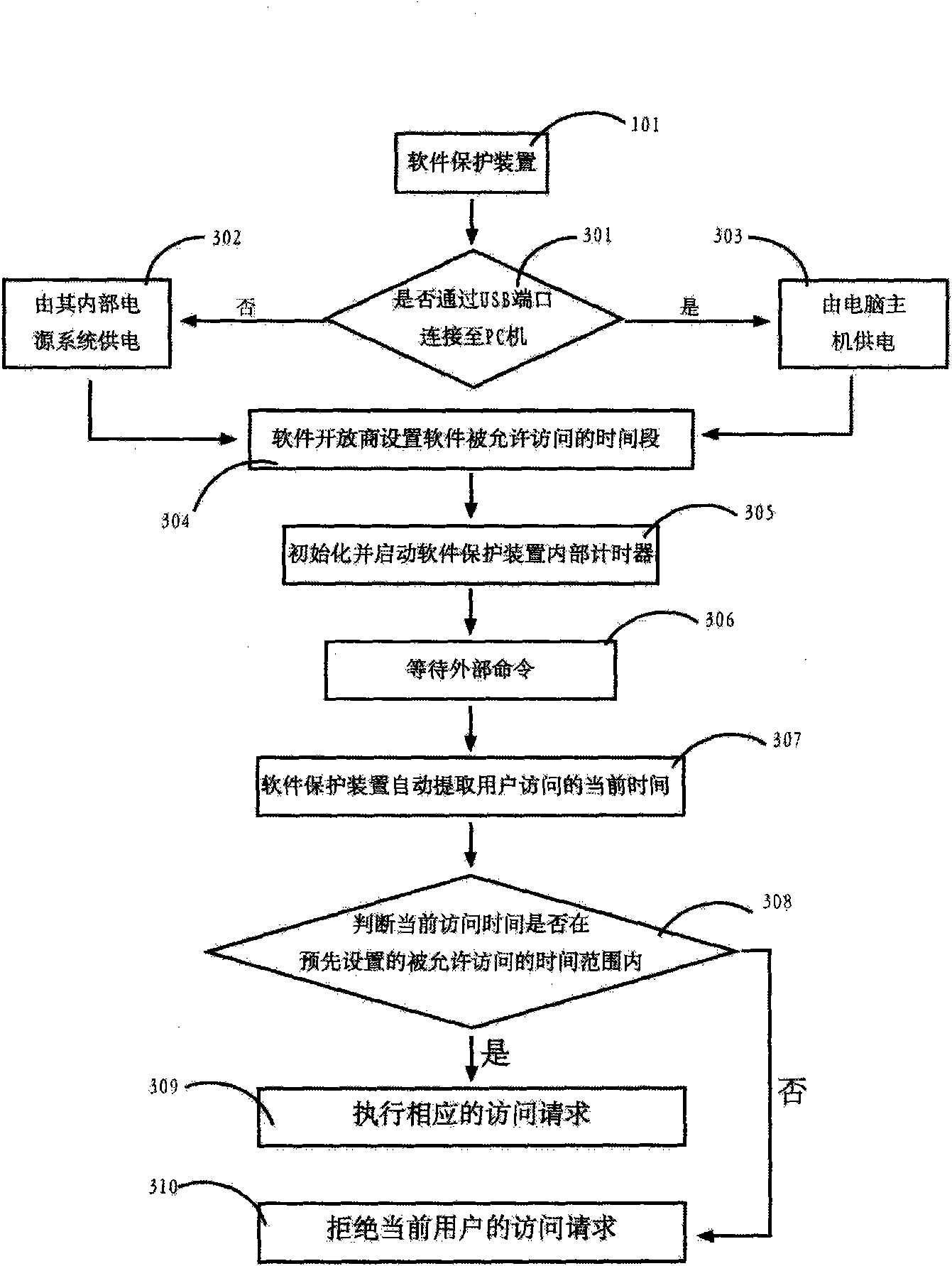
[0032] The clock module (104), which is the timing function of the software authorization device, keeps timing continuously, and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com