Novel fuzzy vault method based on fingerprint characteristic data and matching algorithm
A technology that fuzzes the characteristics of vaults and fingerprints. It is applied in the fields of pattern recognition and cryptography, and can solve problems such as staying in theoretical demonstrations, unclear explanations, and lack of experimental conditions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
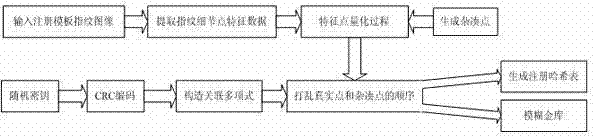
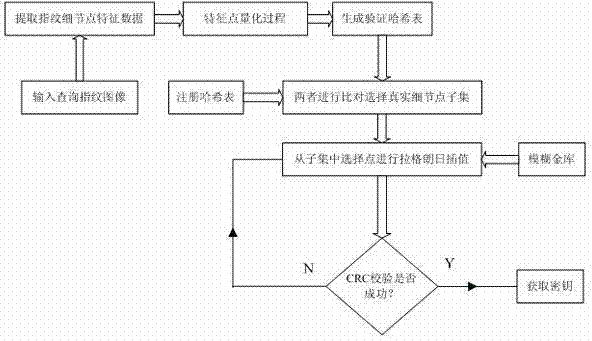
[0043] The present invention will be further described below in conjunction with accompanying drawing.
[0044] 1. Detailed process of system locking (Locking) process:
[0045] 1.1. If figure 1 As shown, a random key with a length of 128 bits is generated by the system as the start of the system, and the random key with a length of 128 bits is used as a coefficient of the polynomial every 16 bits, and the coefficients of the 1st order to the 8th order are assigned to the coefficients of the order to generate an 8th degree polynomial , and the constant term of the polynomial is composed of CRC check code. In this way, we associate the key with the polynomial and add the CRC check code. The generator polynomial of the CRC check code selects CRC16_IBM: .
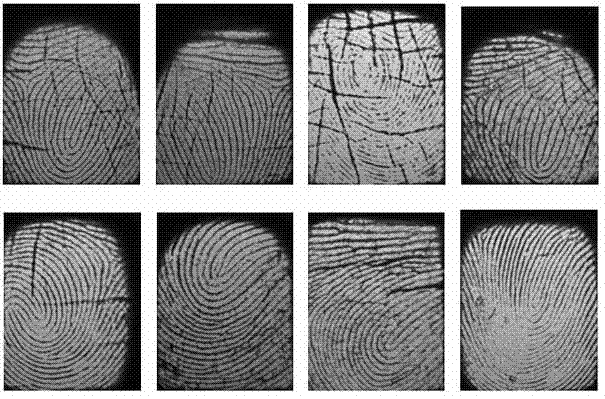
[0046] 1.2. Input a fingerprint image ( image 3 is a part of the image in the fingerprint database), and perform the following operations on this fingerprint image:
[0047] A series of preprocessing operations such ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com