Method for improving safety performance of computers on basis of safety sandbox
A computer security and security technology, applied in computer security devices, computing, platform integrity maintenance, etc., can solve problems such as risks, affect software execution efficiency, increase software development costs, etc., to ensure clean, safe, and easy to use. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
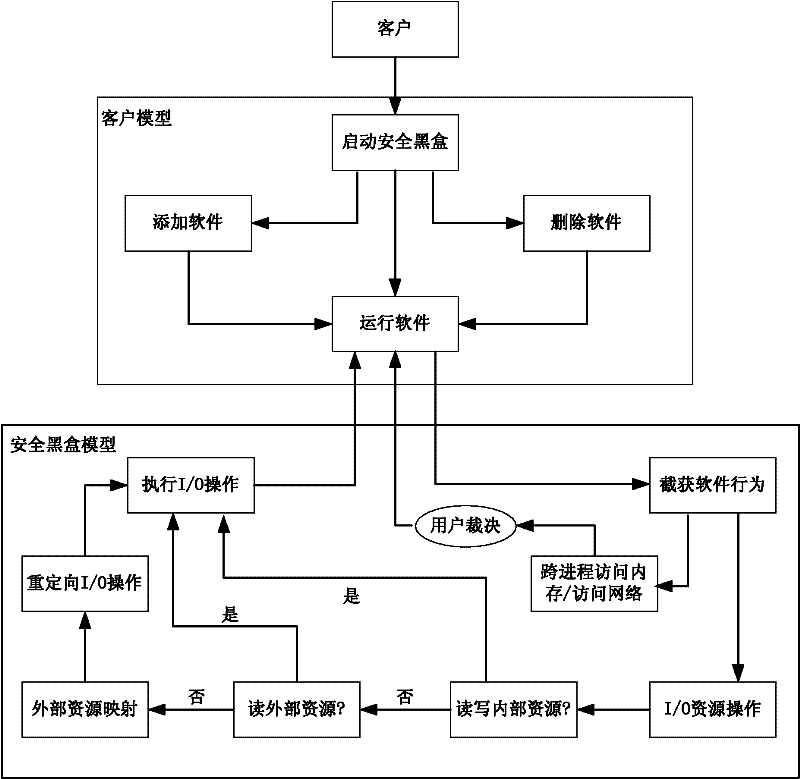
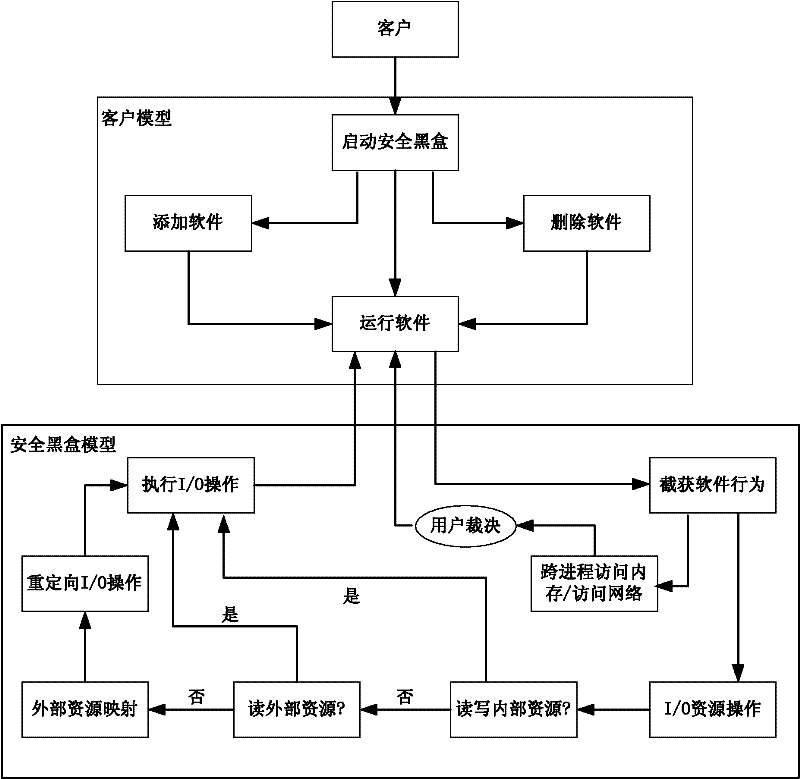
[0018] The invention adopts the method of closing the software running environment and monitoring the running state of the software. Specifically, by intercepting software running behaviors, including cross-process memory access, underlying I / O request operations, accessing the network, etc., when intercepting software behaviors, if the software requests cross-process access to memory or access to the network, it is up to the user to decide whether to run the software . If the software sends an I / O request, the security black box will add the request to the request queue after receiving the request; if the security black box analyzes the intercepted I / O request and redirects it to the inside of the security black box to achieve closed software operation environmental purpose. When requesting access to an external system device file, and the requested permission is insufficient, the security black box tries to generate a device image file inside the security black box for the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com