Patents
Literature
36 results about "Shadow system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Shadow system is a term used in information services for any application relied upon for business processes that is not under the jurisdiction of a centralized information systems department. That is, the information systems department did not create it, was not aware of it, and does not support it.
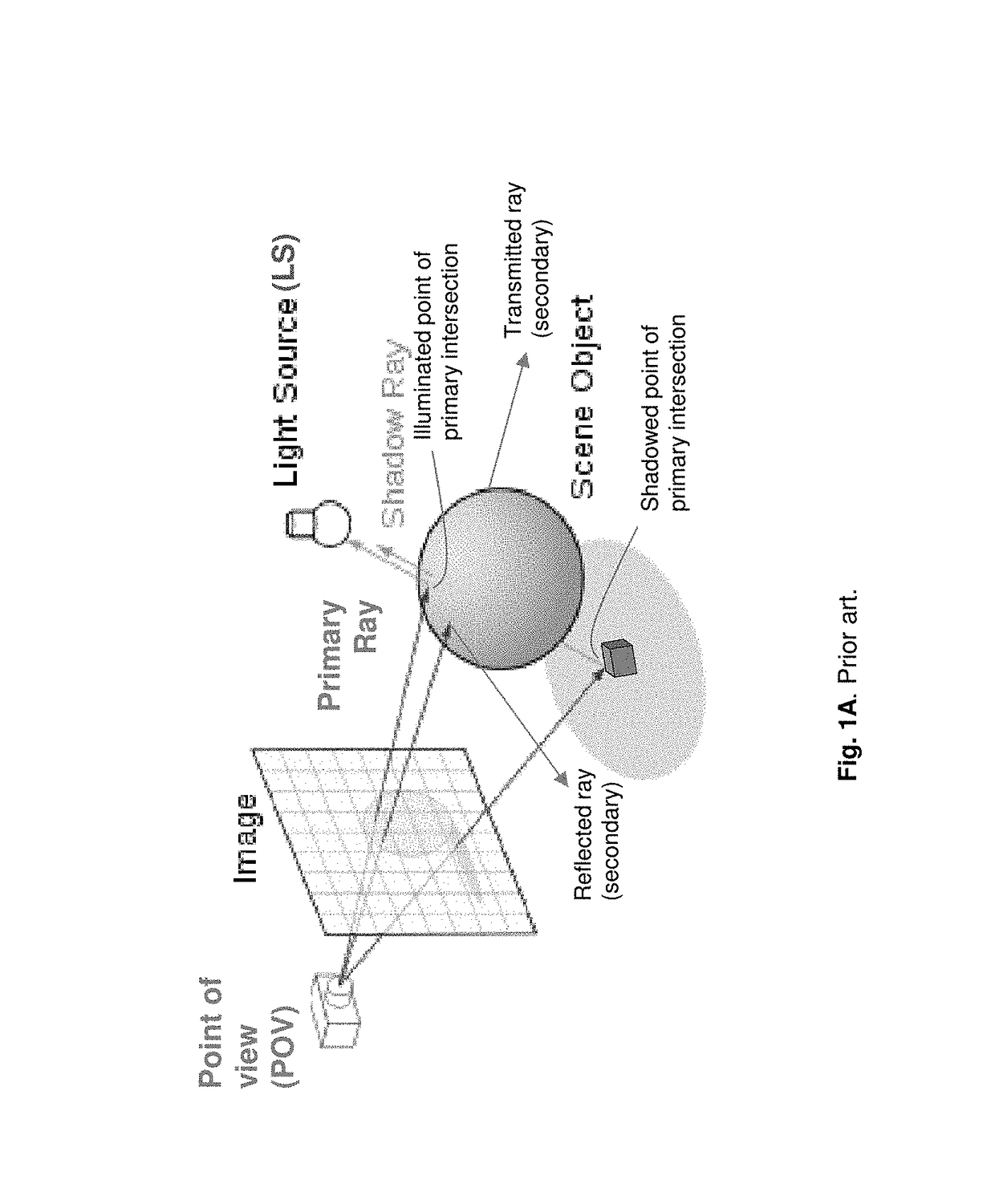
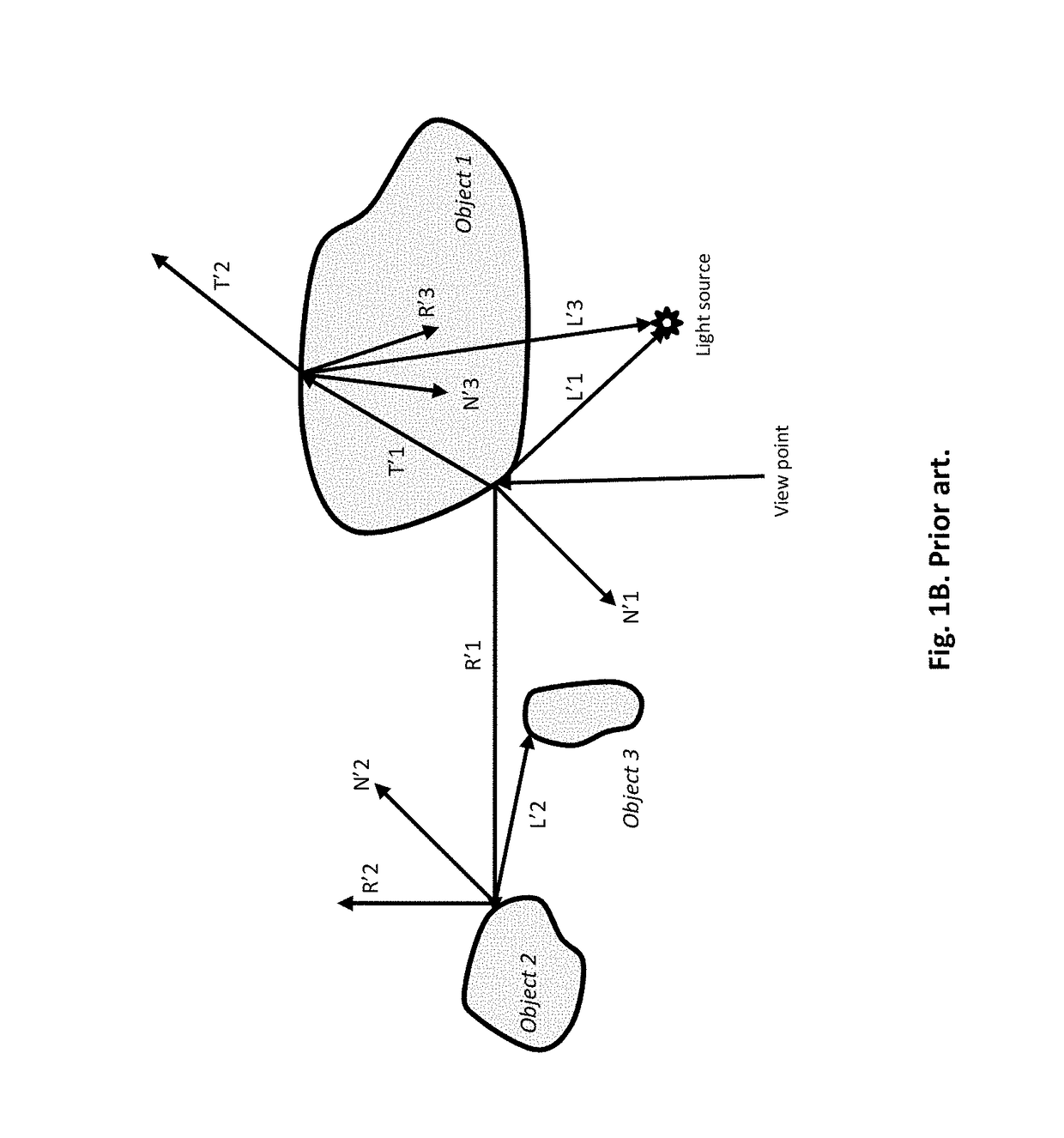
Rendering of Soft Shadows
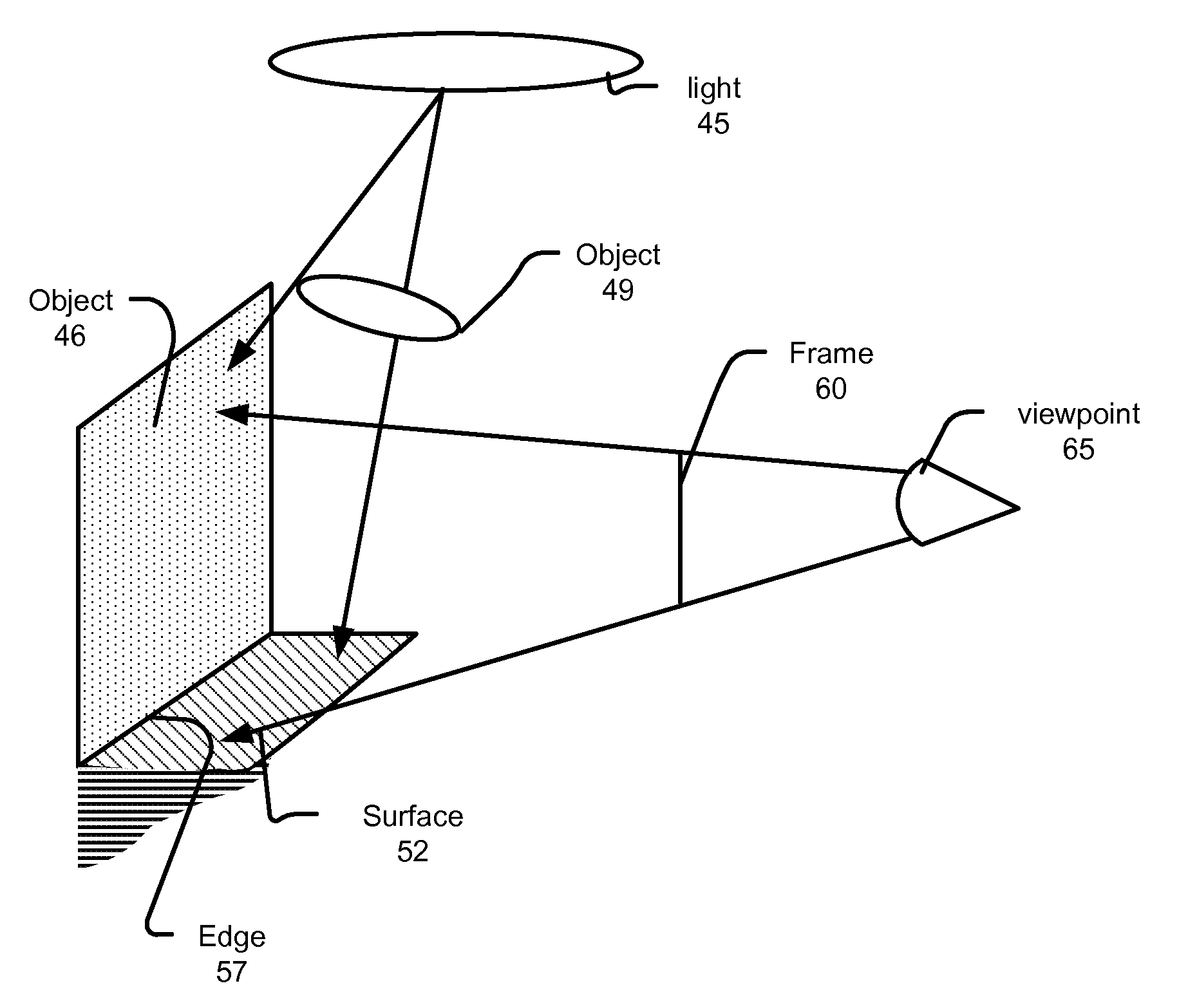
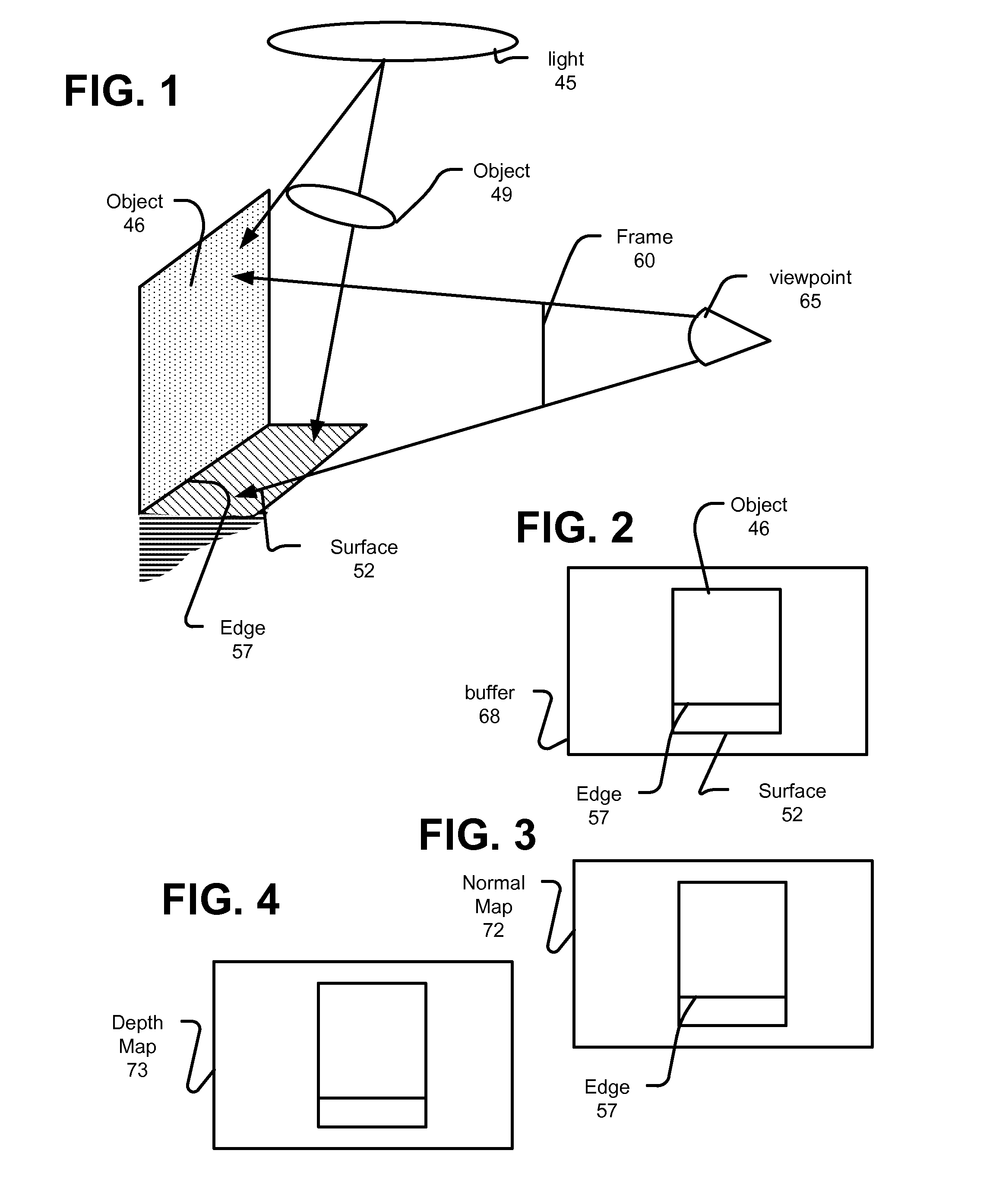
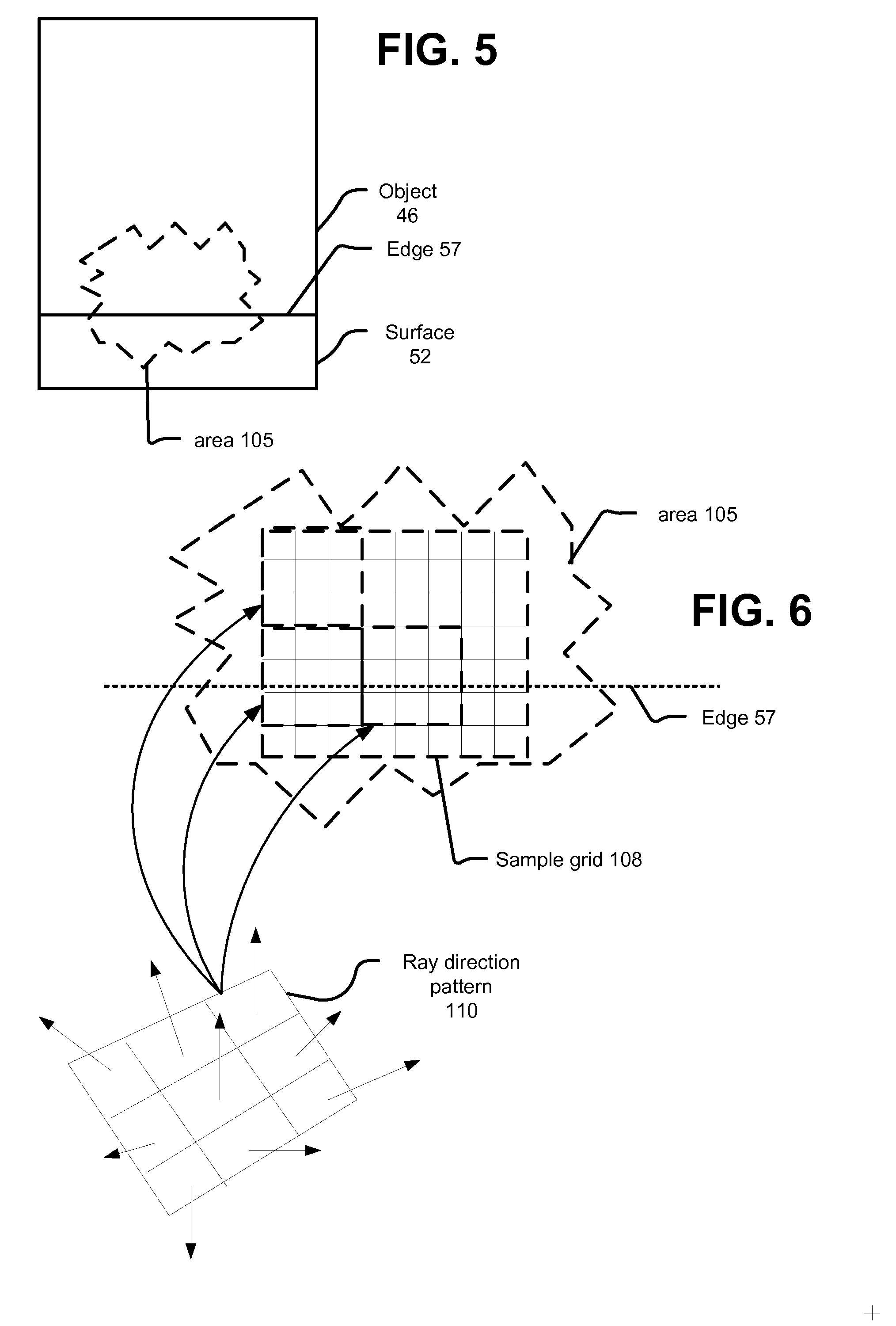
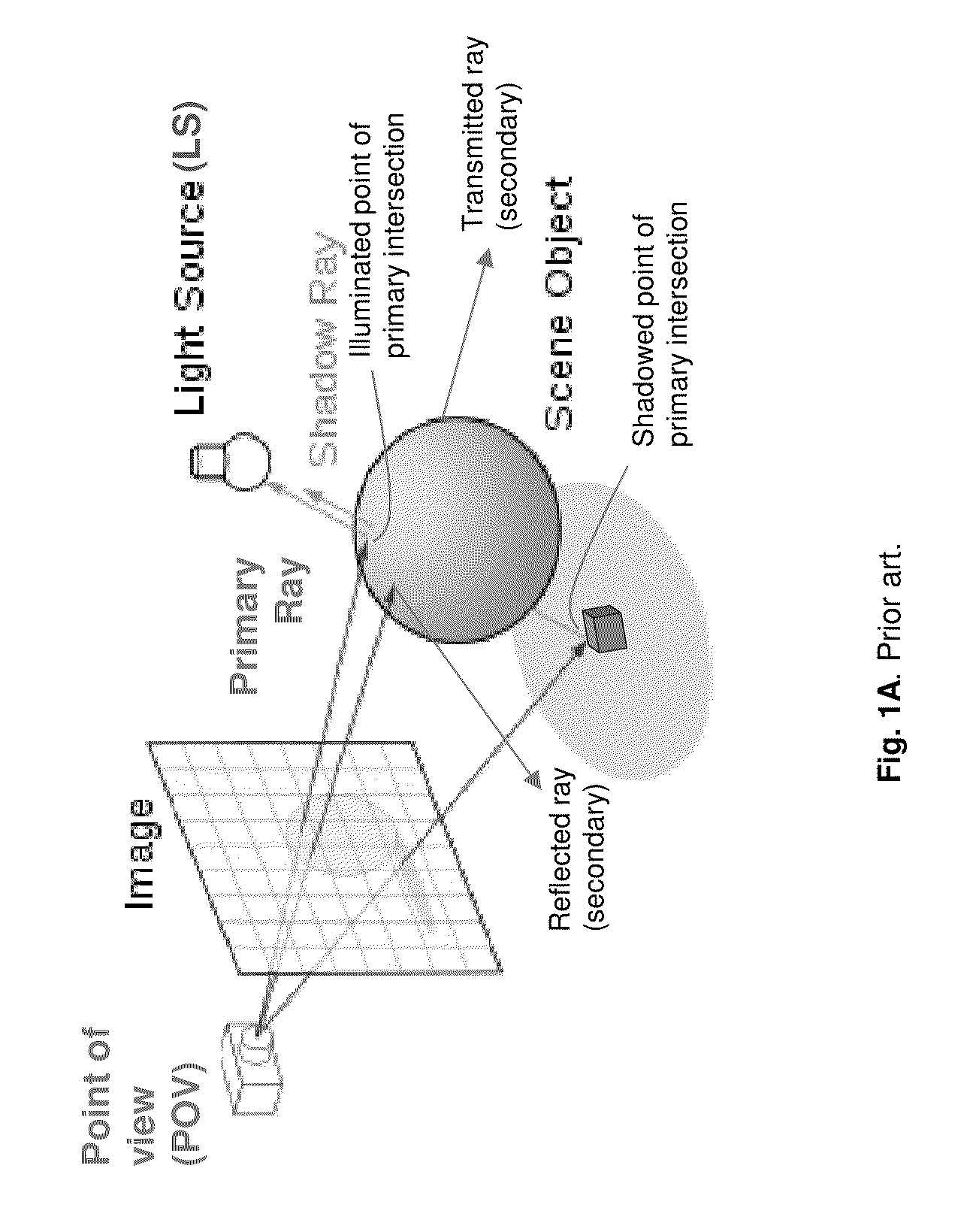
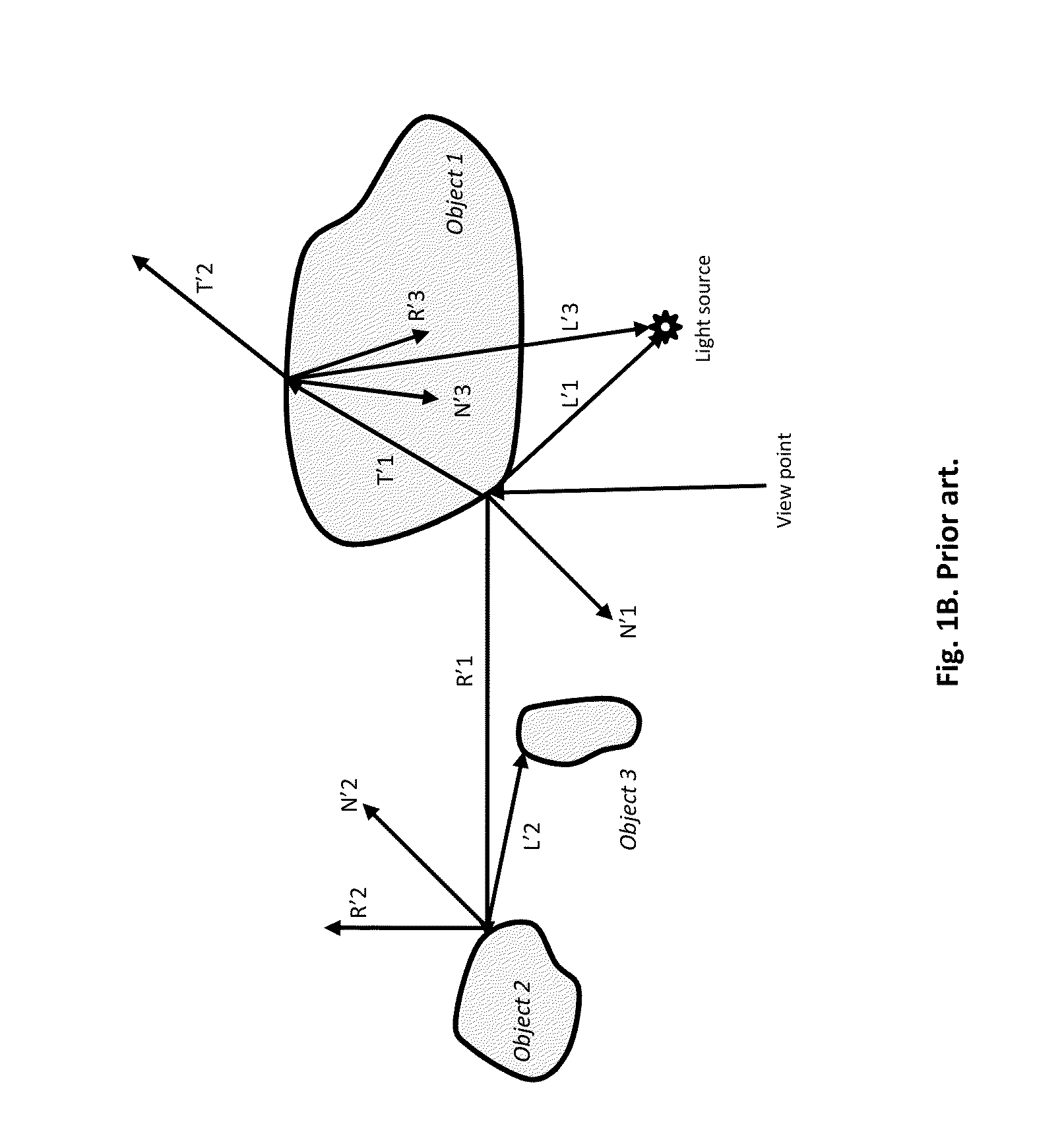
Systems can identify visible surfaces for pixels in an image (portion) to be rendered. A sampling pattern of ray directions is applied to the pixels, so that the sampling pattern of ray directions repeats, and with respect to any pixel, the same ray direction can be found in the same relative position, with respect to that pixel, as for other pixels. Rays are emitted from visible surfaces in the respective ray direction supplied from the sampling pattern. Ray intersections can cause shaders to execute and contribute results to a sample buffer. With respect to shading of a given pixel, ray results from a selected subset of the pixels are used; the subset is selected by identifying a set of pixels, collectively from which rays were traced for the ray directions in the pattern, and requiring that surfaces from which rays were traced for those pixels satisfy a similarity criteria.
Owner:IMAGINATION TECH LTD
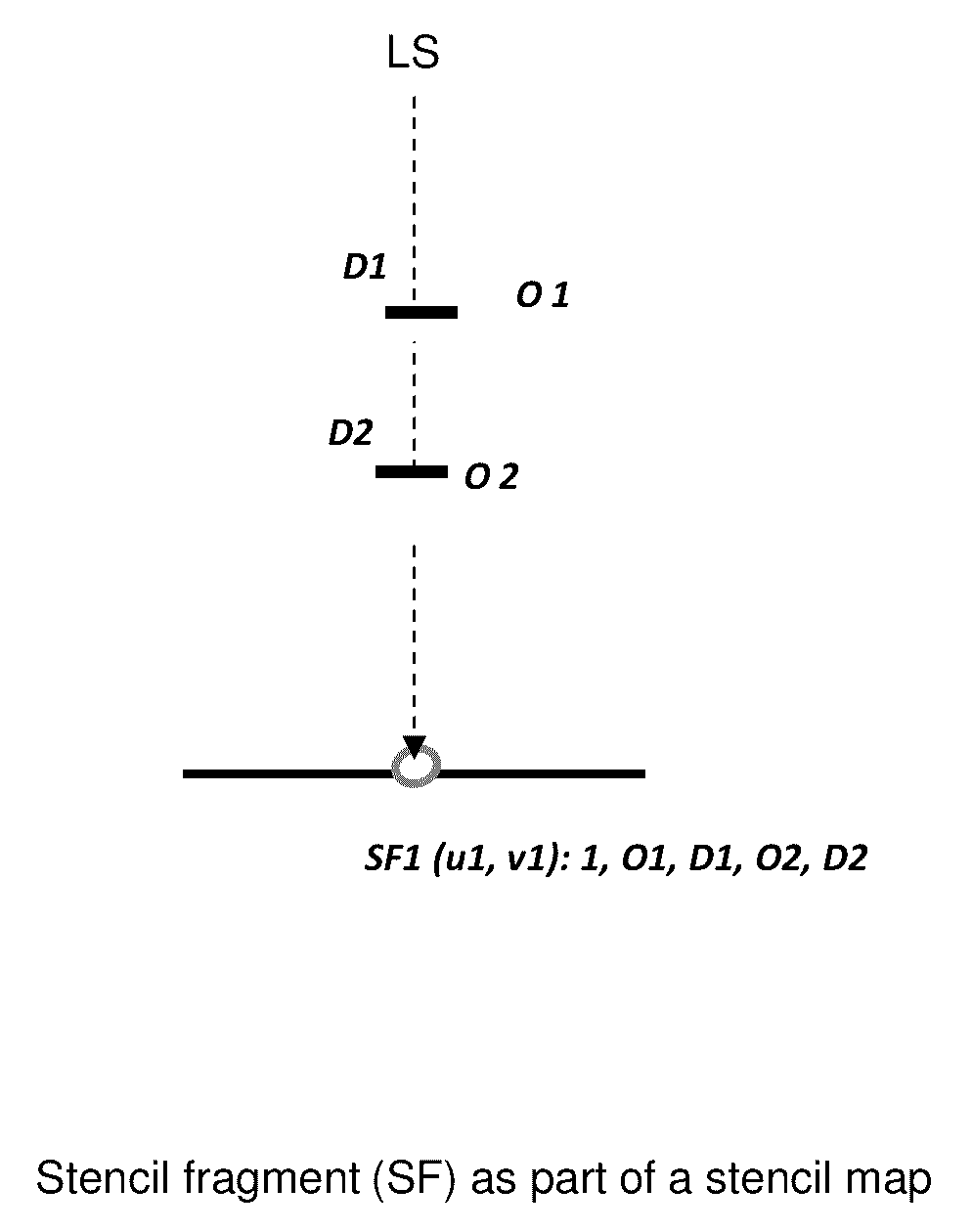
Stencil mapped shadowing system
ActiveUS20140375645A1Increase construction costsEliminate useDetails involving 3D image dataProgram controlShadowingsResource utilization
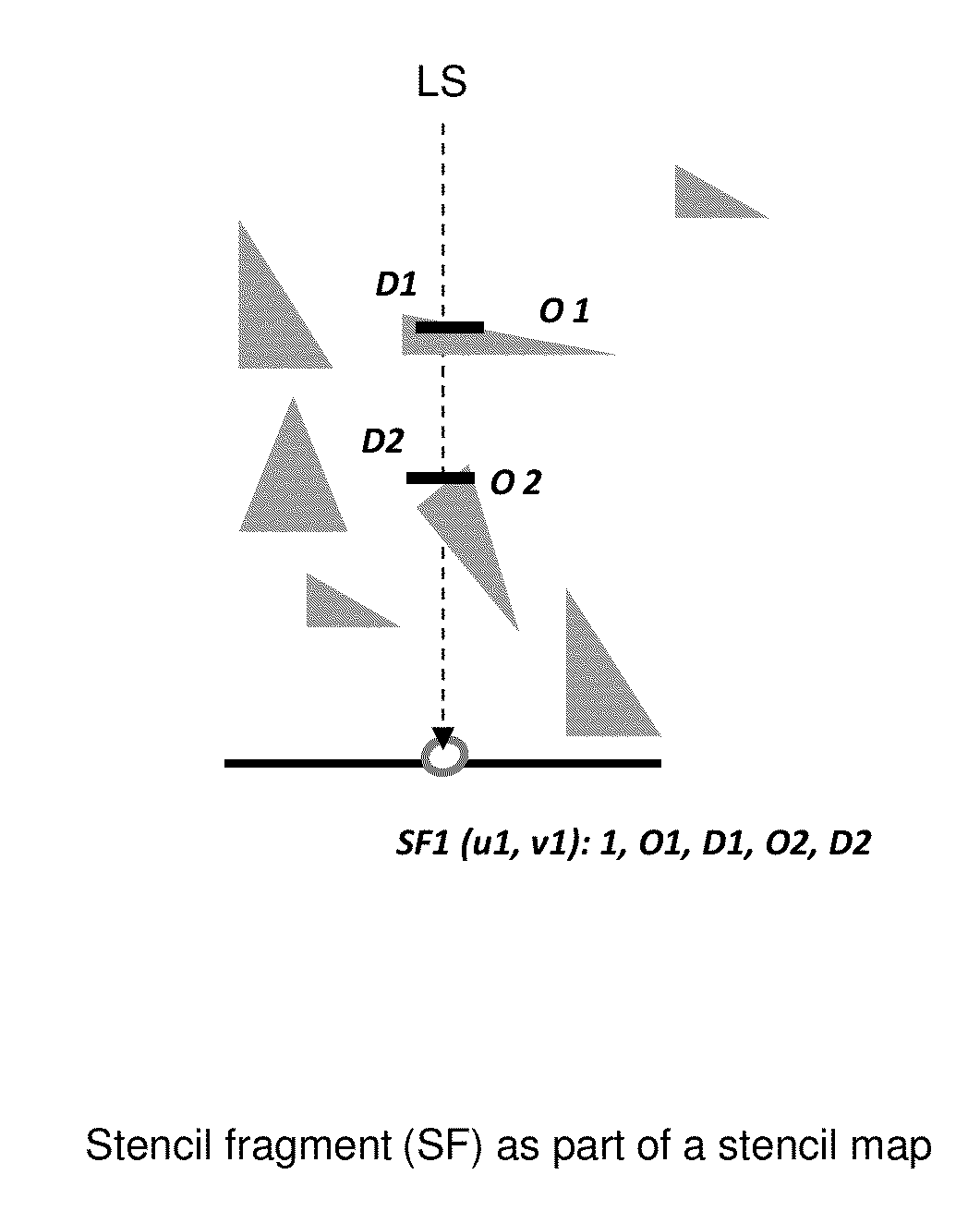
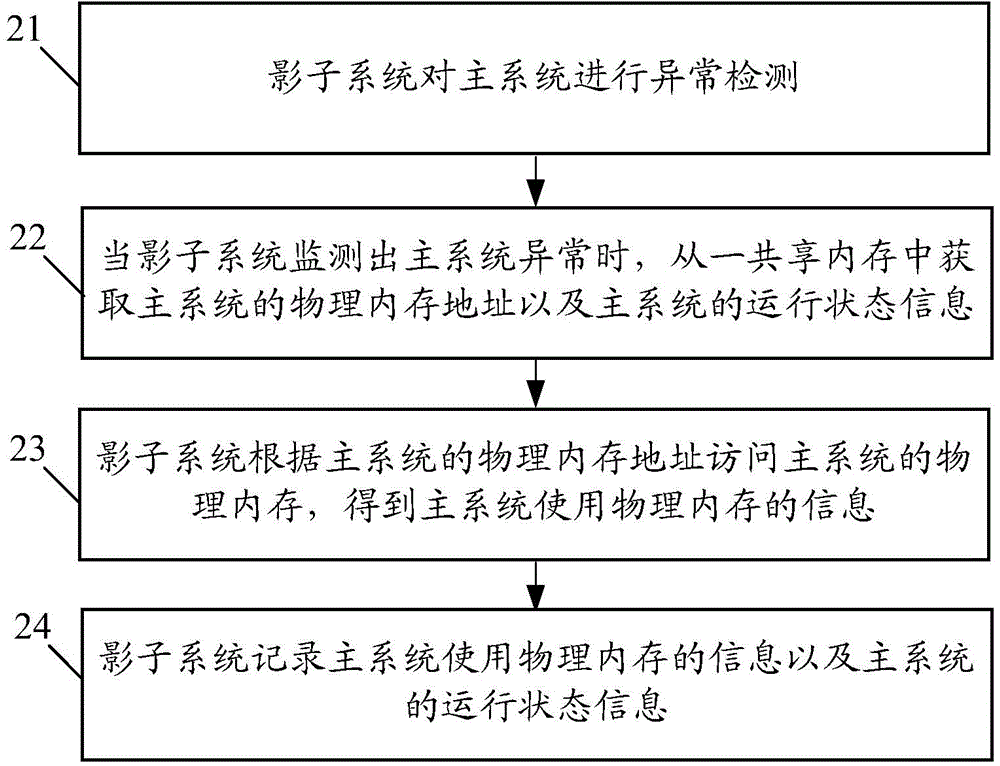
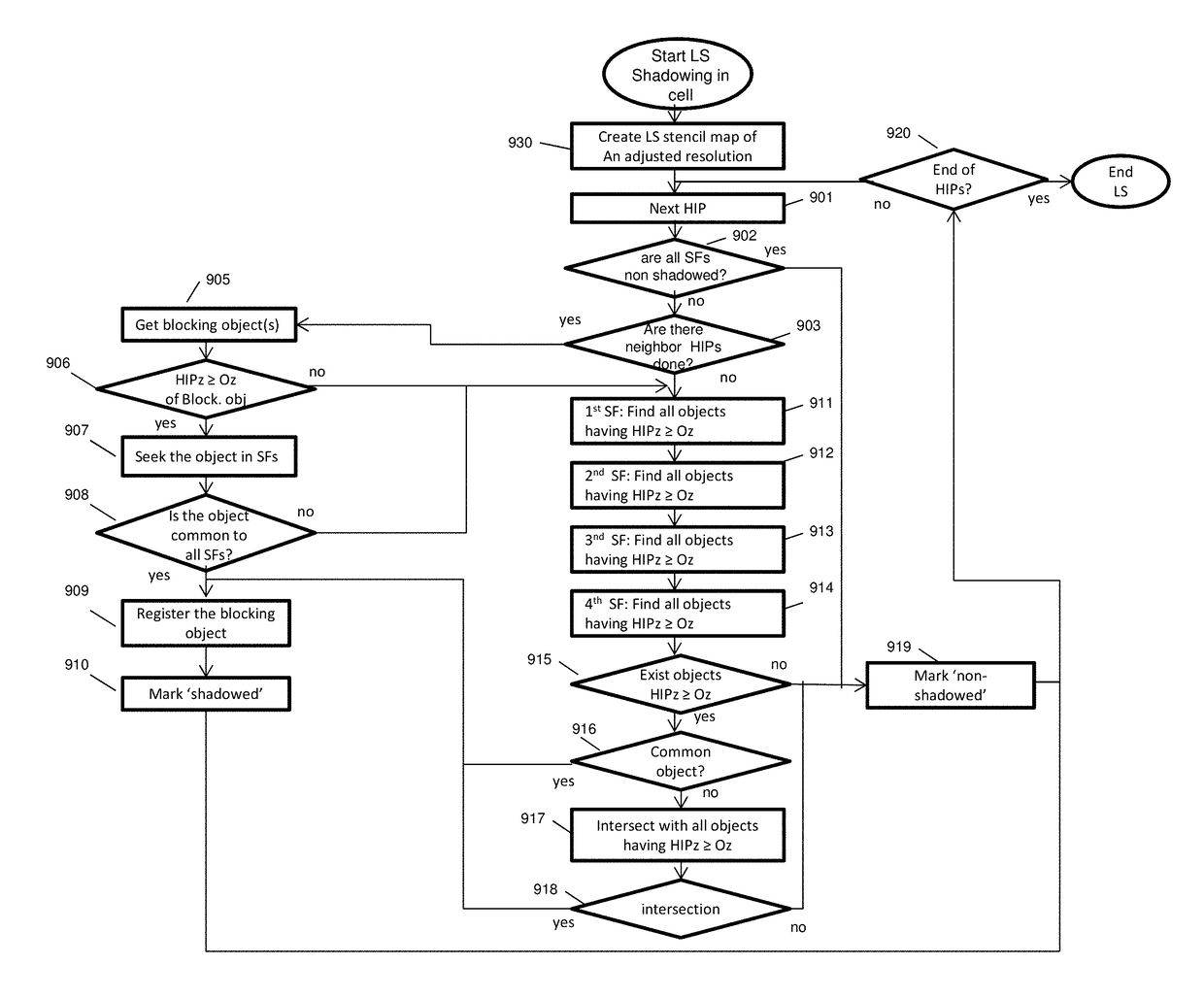
Aspects comprise shadowing system as part of ray tracing. It is based on uniform grid of cells, and on local stencils in cells. The acceleration structures are abandoned along with high traversal and construction costs of these structures. The amount of intersection tests is cut down. The stencils are generated in the preprocessing stage and utilized in runtime. The relevant part of scene data, critical for shadowing of all visible intersection points in a cell, is registered in the local stencil map, as a volumetric data. The runtime use of stencils allows a complete locality at each cell, enhanced utilization of processing resources and load balancing of parallel processing.
Owner:SNAP INC
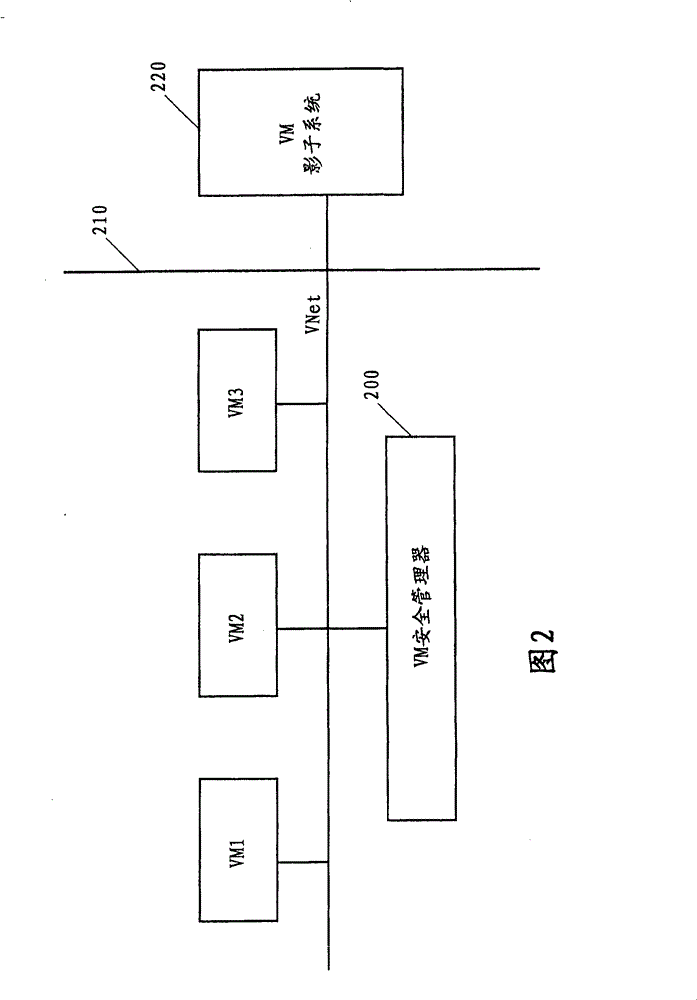
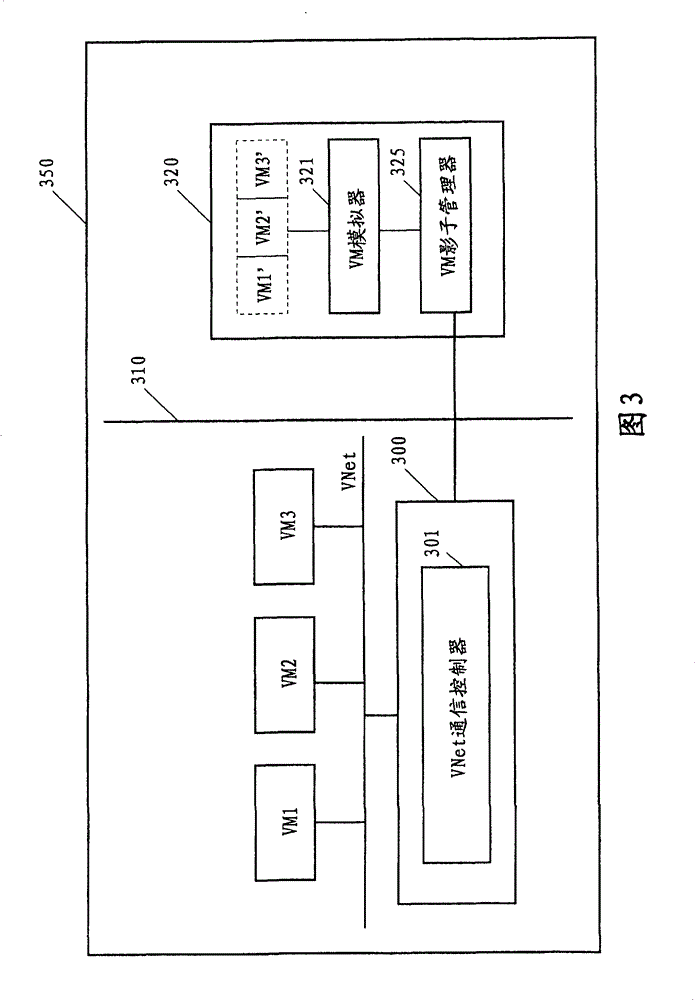
Safety enhanced virtual machine communication method and virtual machine system
InactiveCN101800730AFlexible detectionInvestment protectionSecuring communicationPhysical securityShadow system
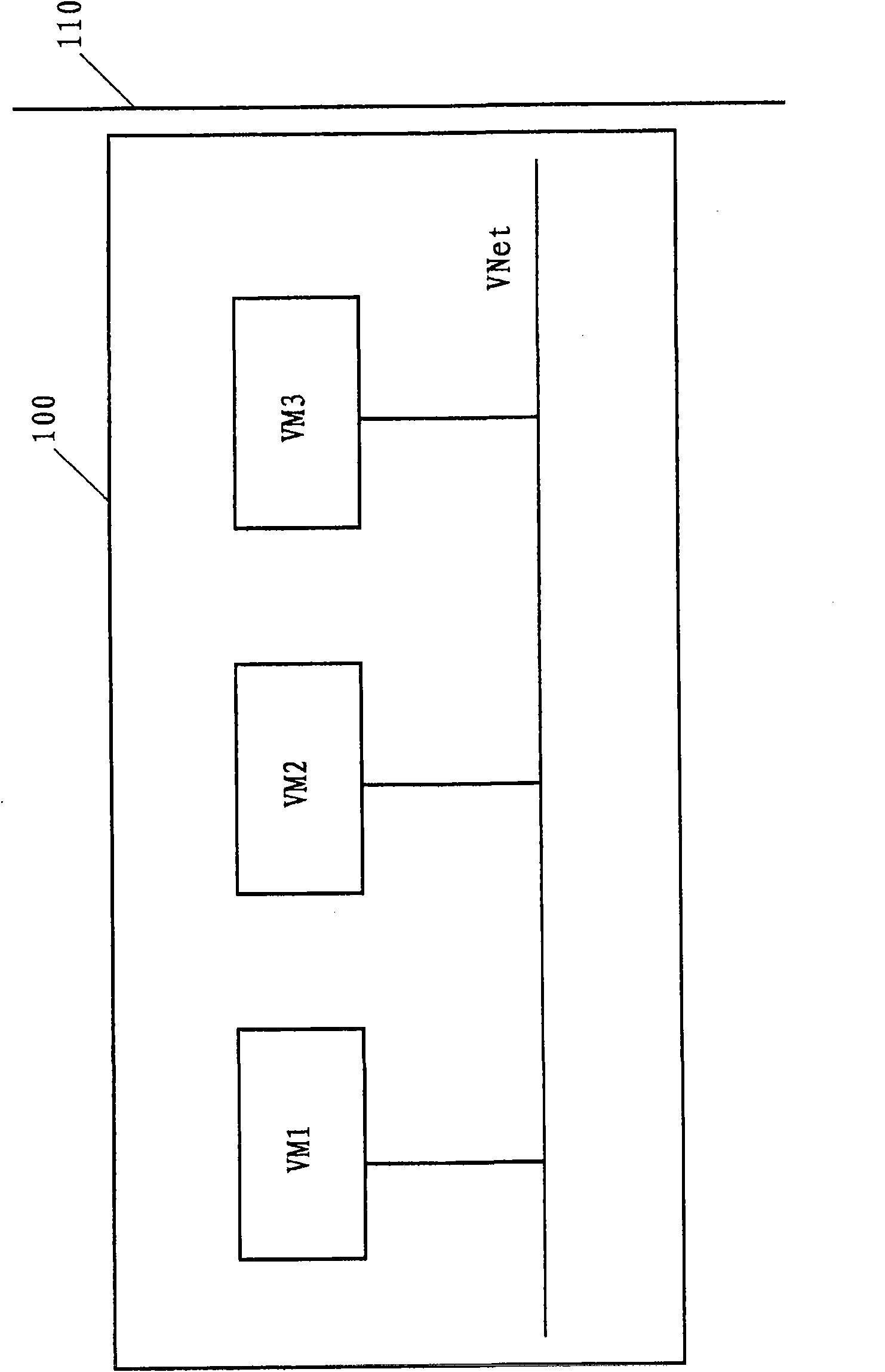
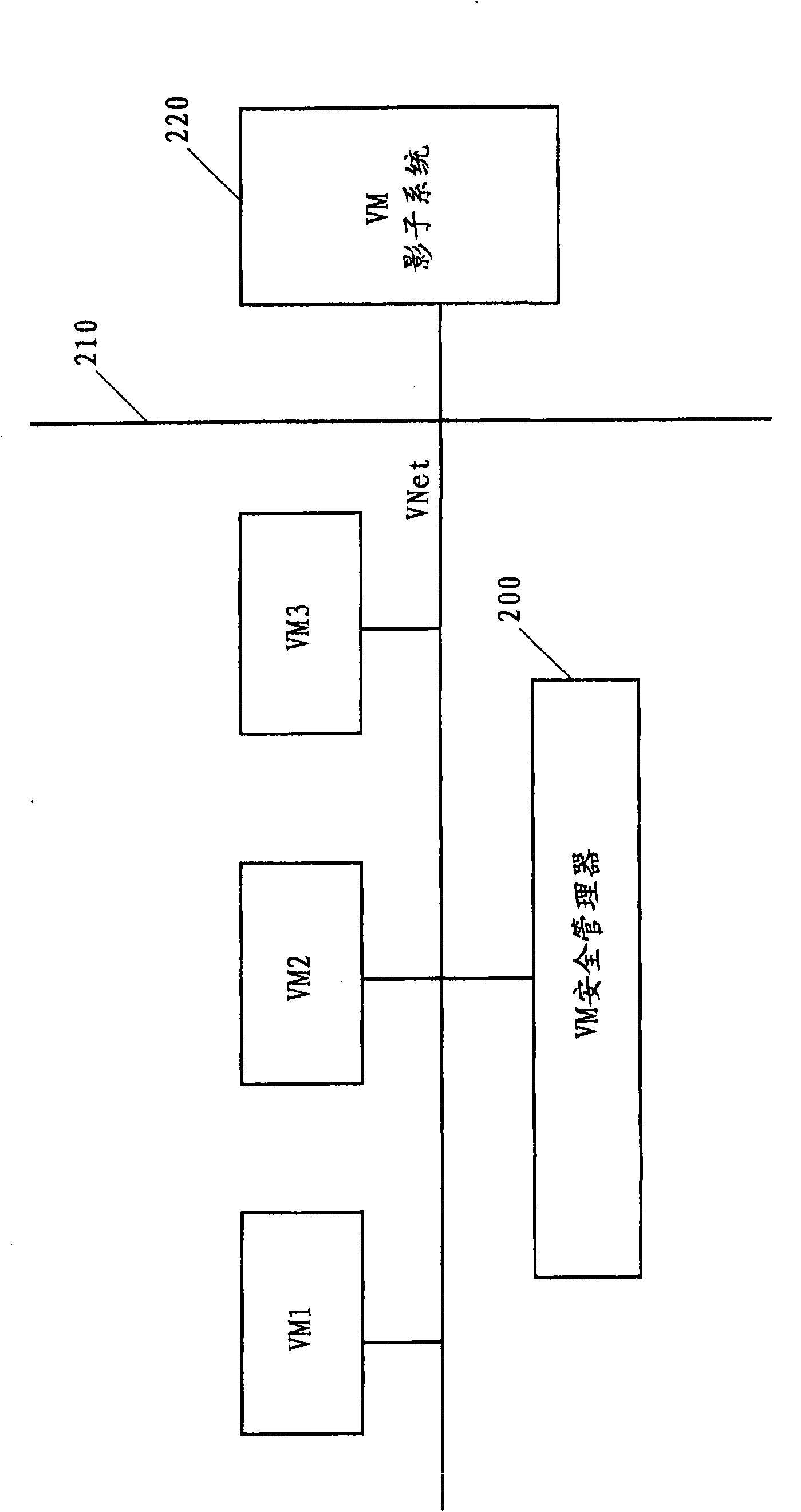
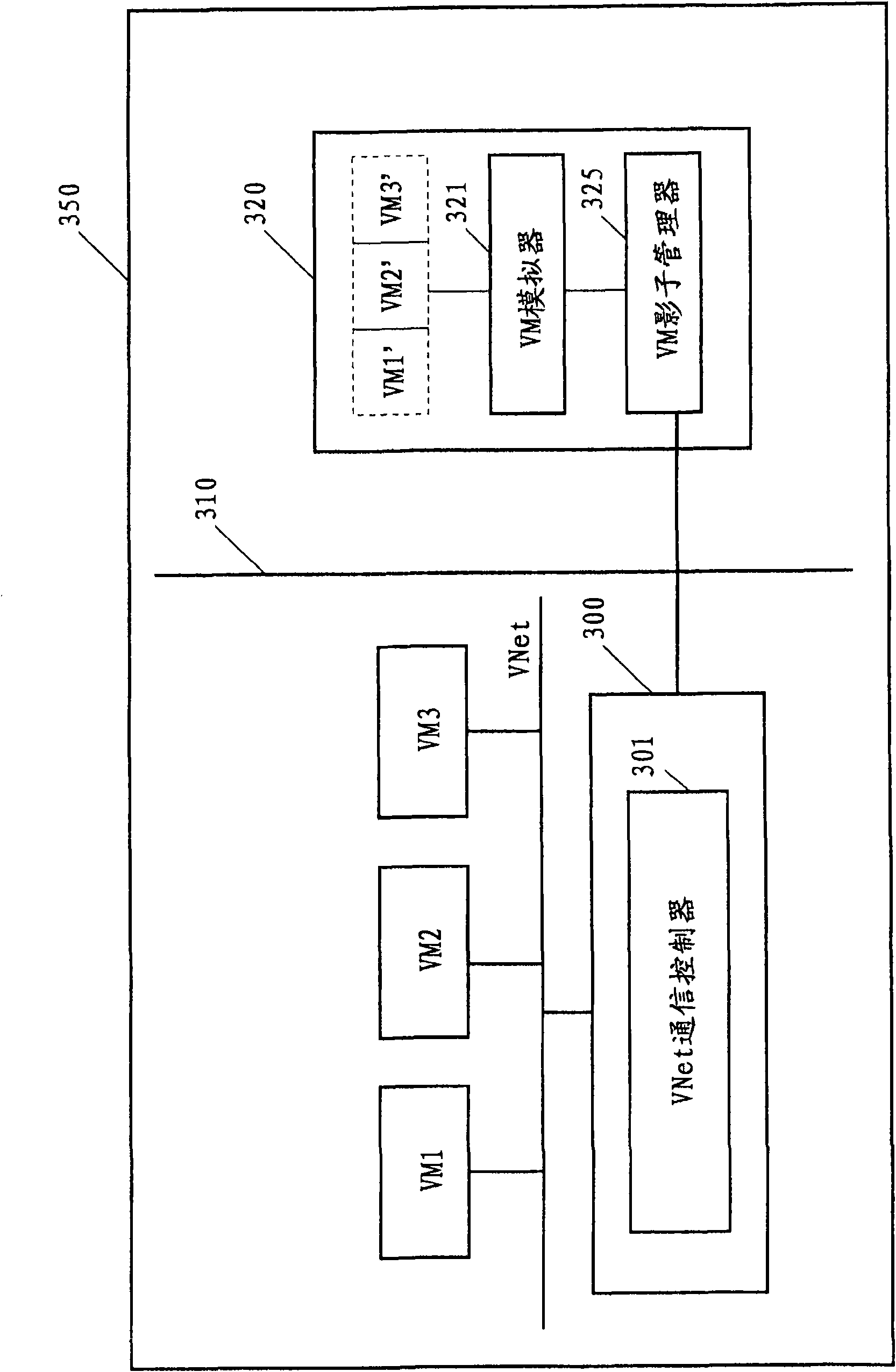
The invention discloses a safety enhanced virtual machine communication method and a virtual machine system. The safety enhanced virtual machine system according to one embodiment comprises a plurality of virtual machines positioned on a same physical machine in a virtual network. The virtual machine system comprises a virtual network safety manager coupled in the virtual network and a shadow system coupled with the virtual network safety manager, wherein the shadow system is positioned on the other physical machine different from the physical machine in which the virtual machines are positioned, the virtual network safety manager copied packets are sent among the virtual machines and the copied packets are forwarded to the shadow system through a physical safety device; the shadow systemreturns response information indicating the received packets to the virtual network safety manager; and the virtual network safety manager sends the packets among the virtual machines according to the returned response information.
Owner:IBM CN
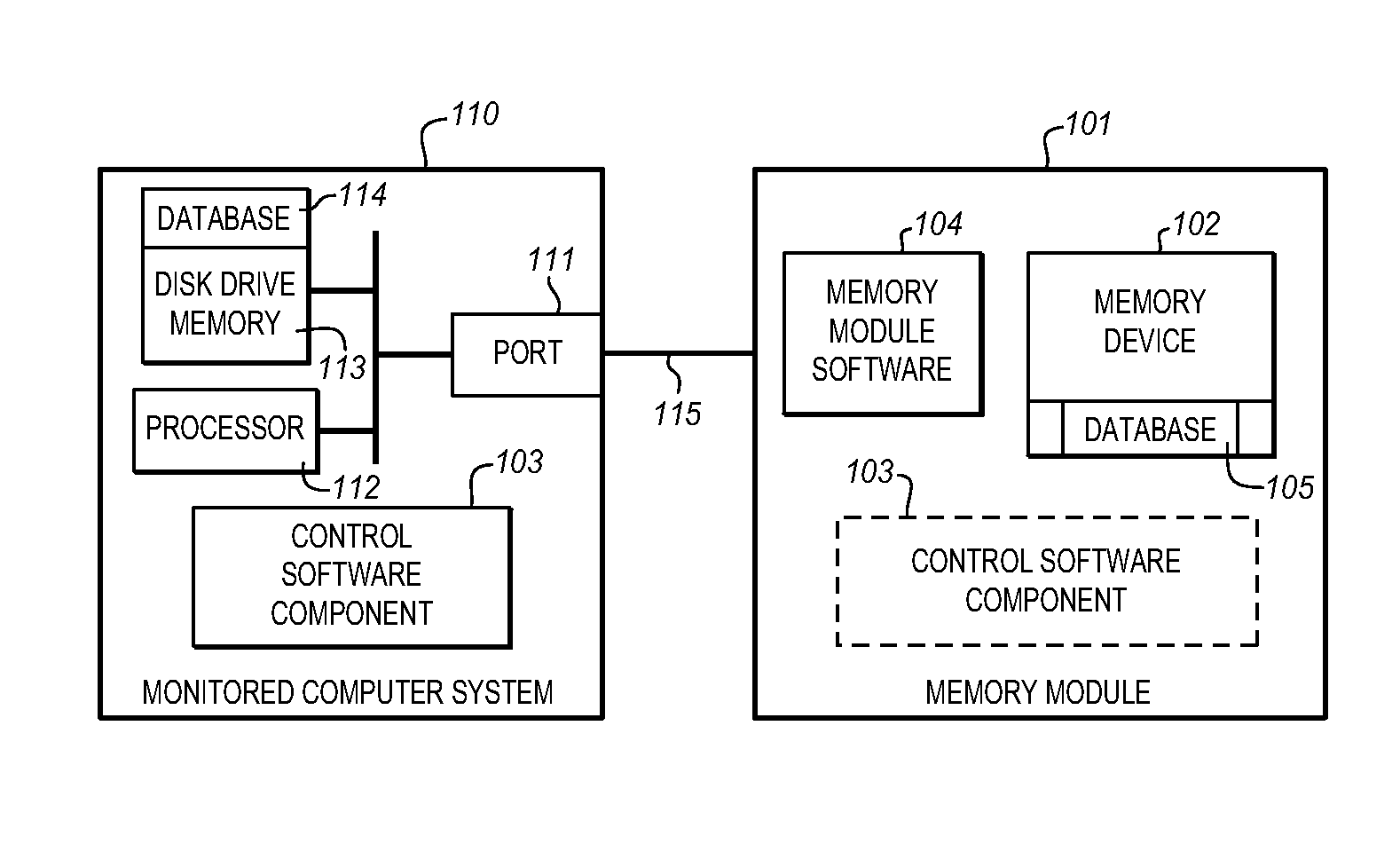
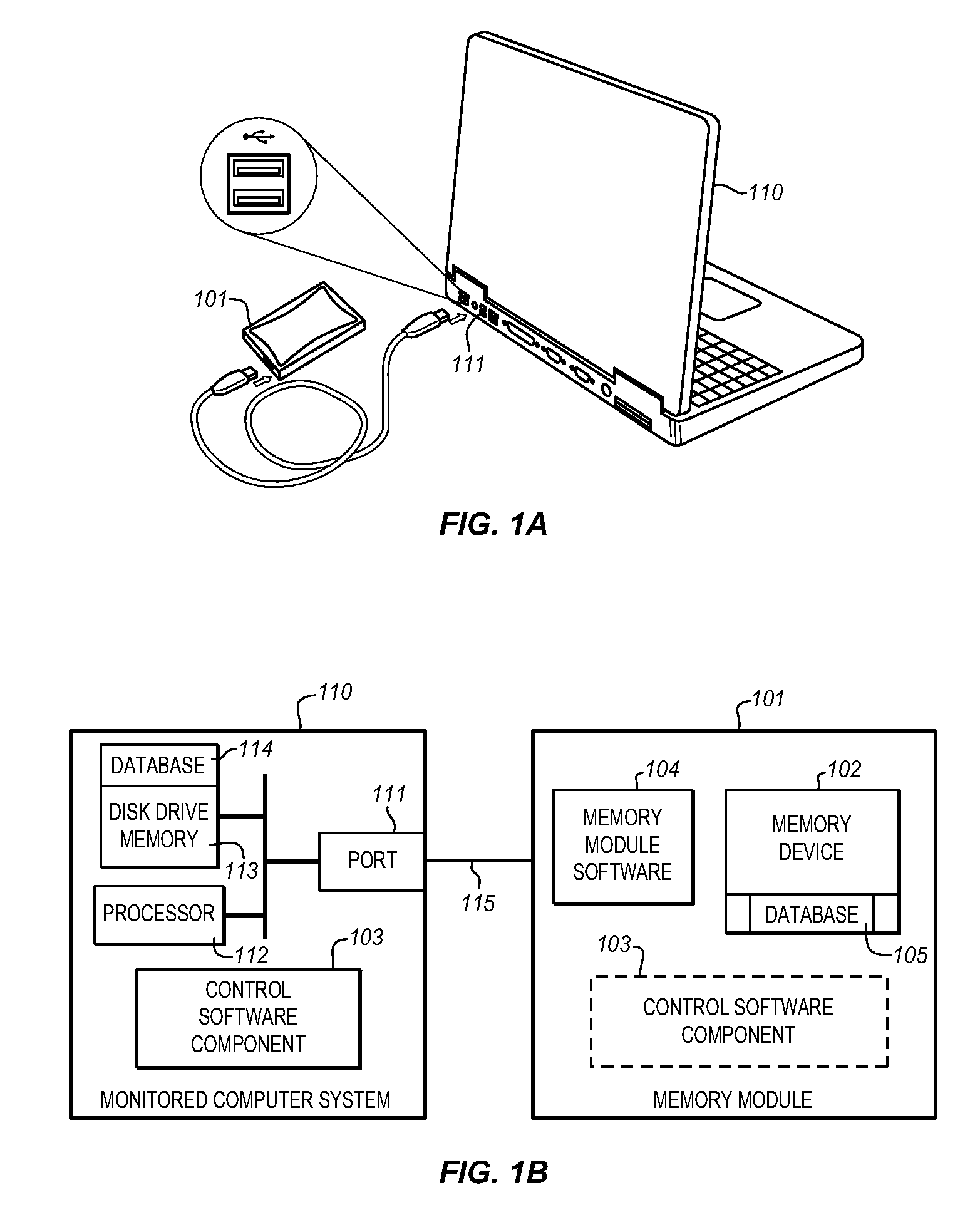
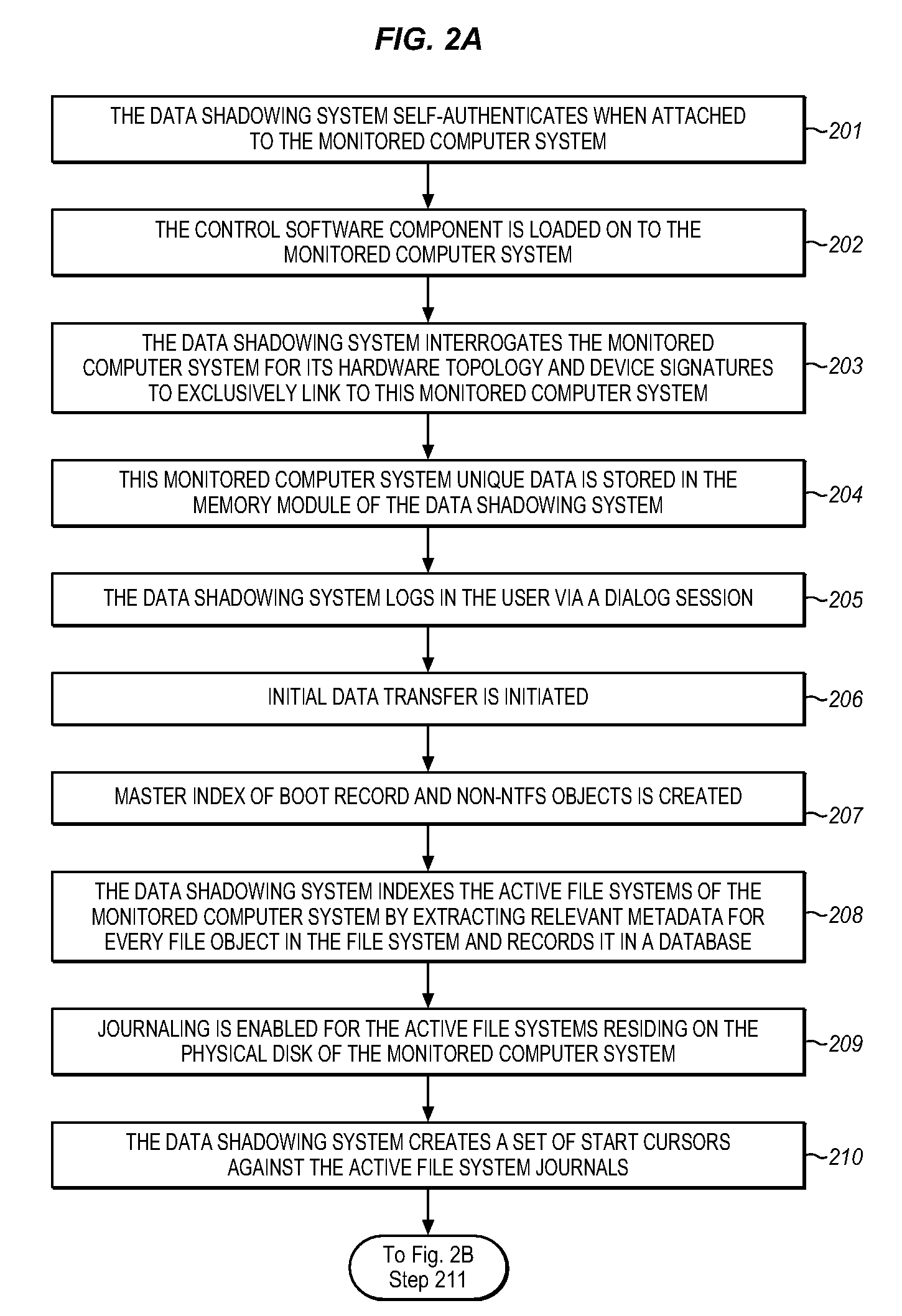
System for automatically shadowing data and file directory structures that are recorded on a computer memory
ActiveUS20080104147A1Efficiently track and storeData processing applicationsDigital data information retrievalFile systemComputerized system
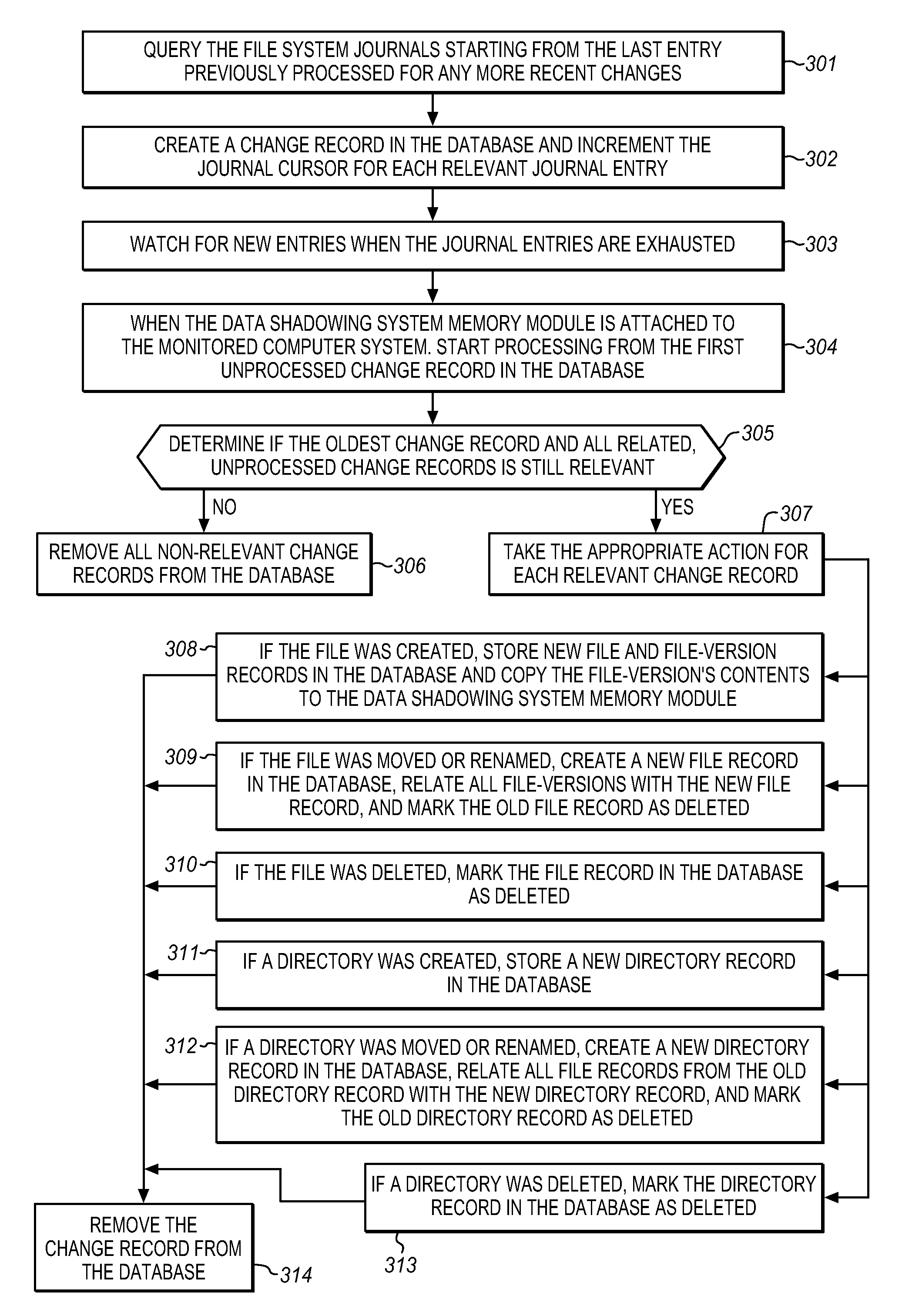
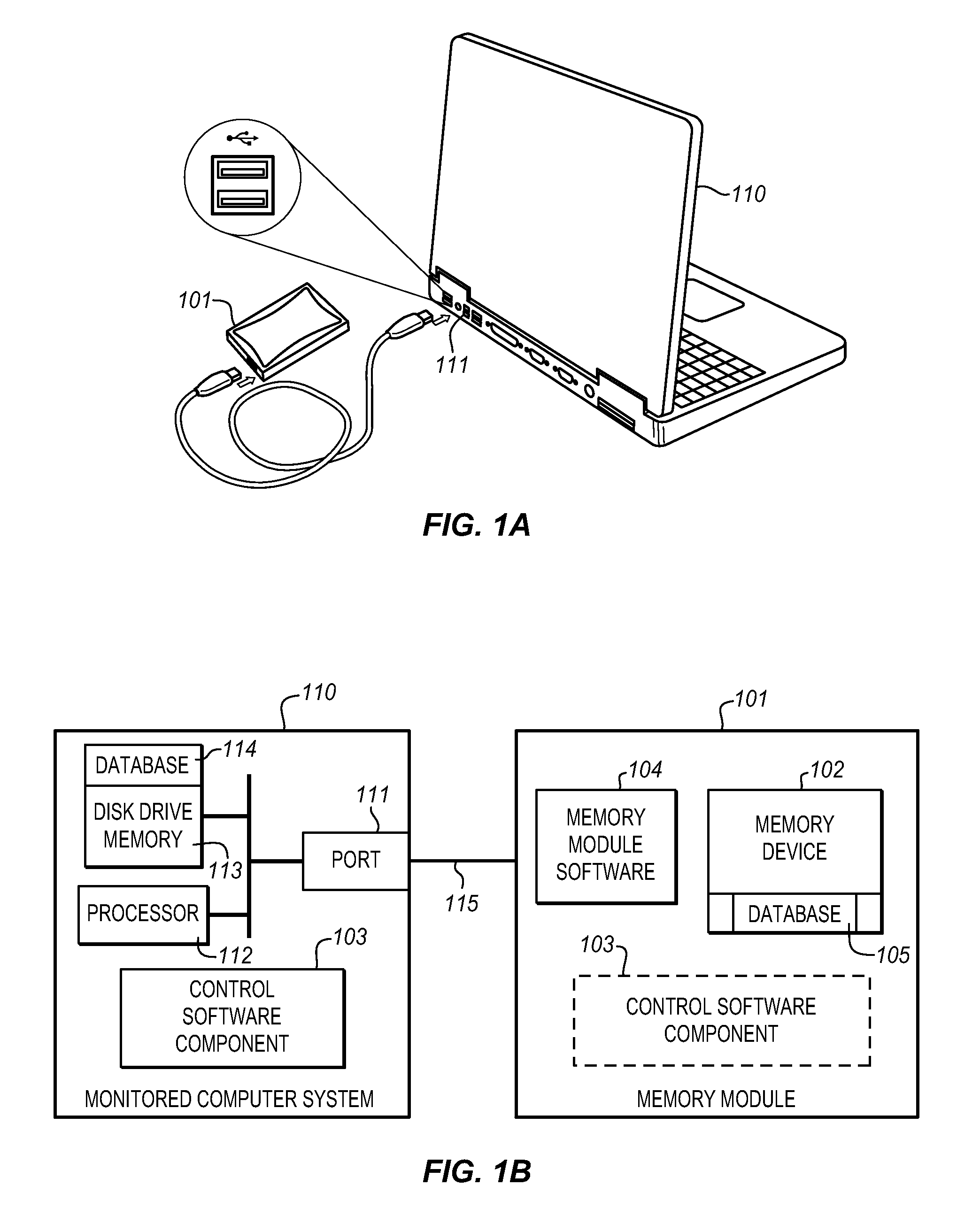
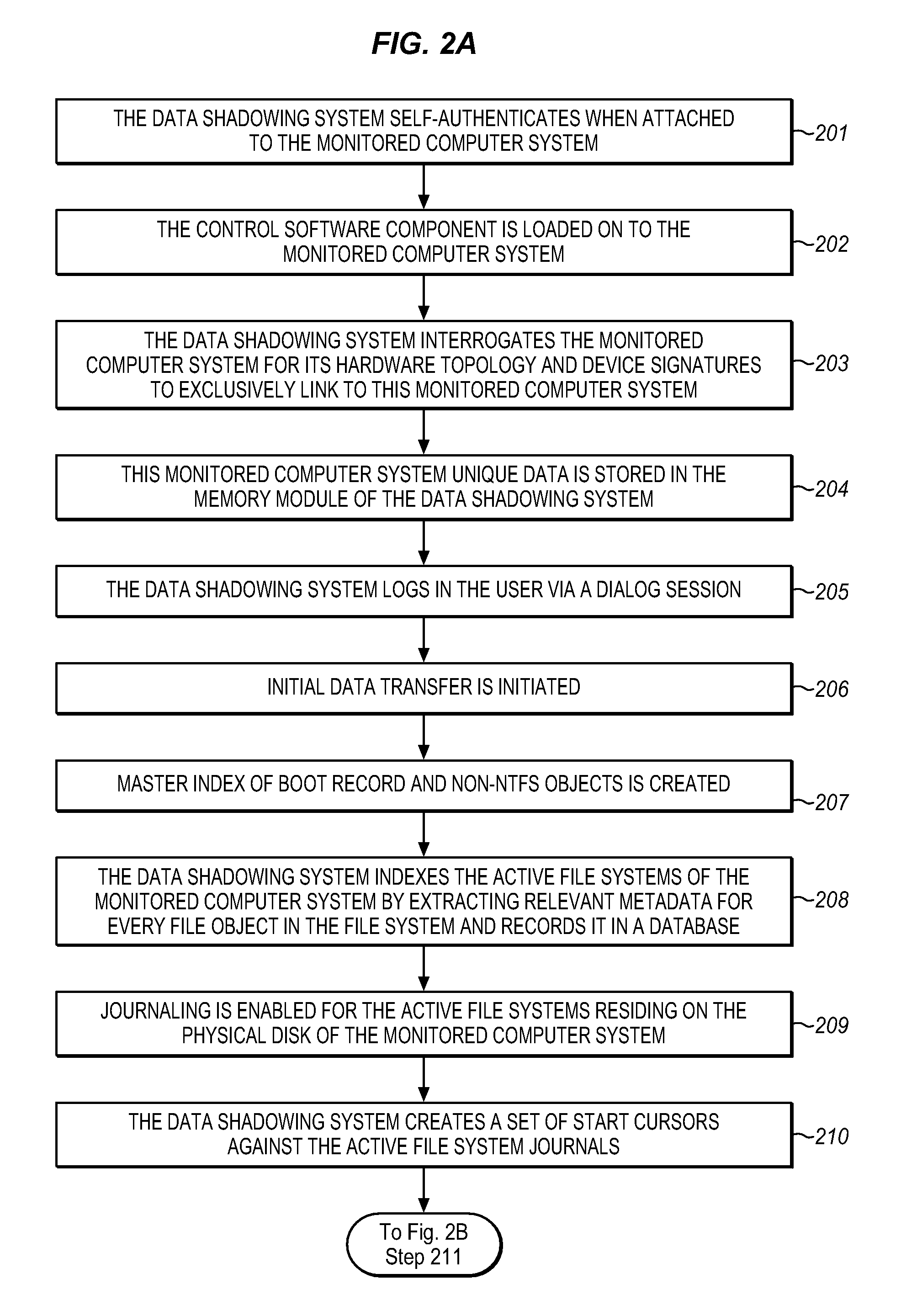
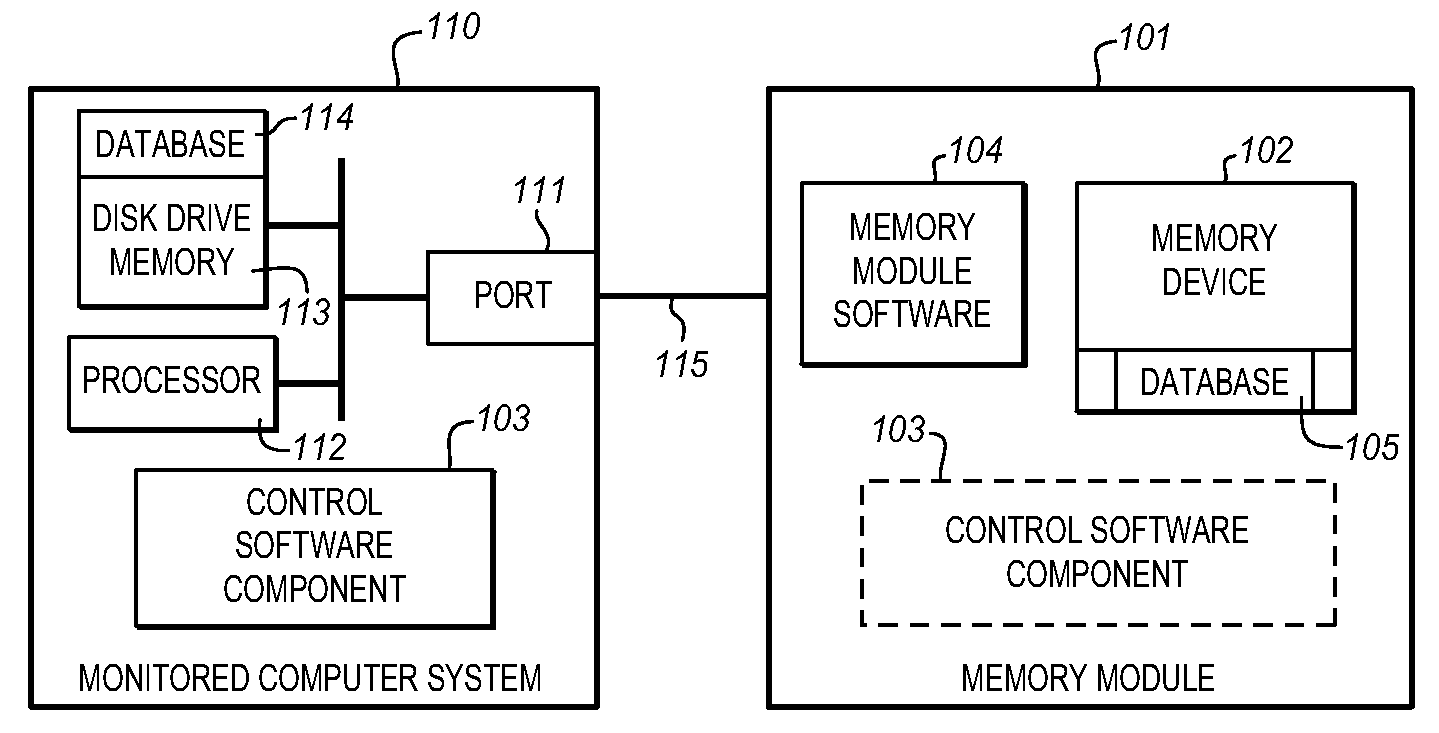
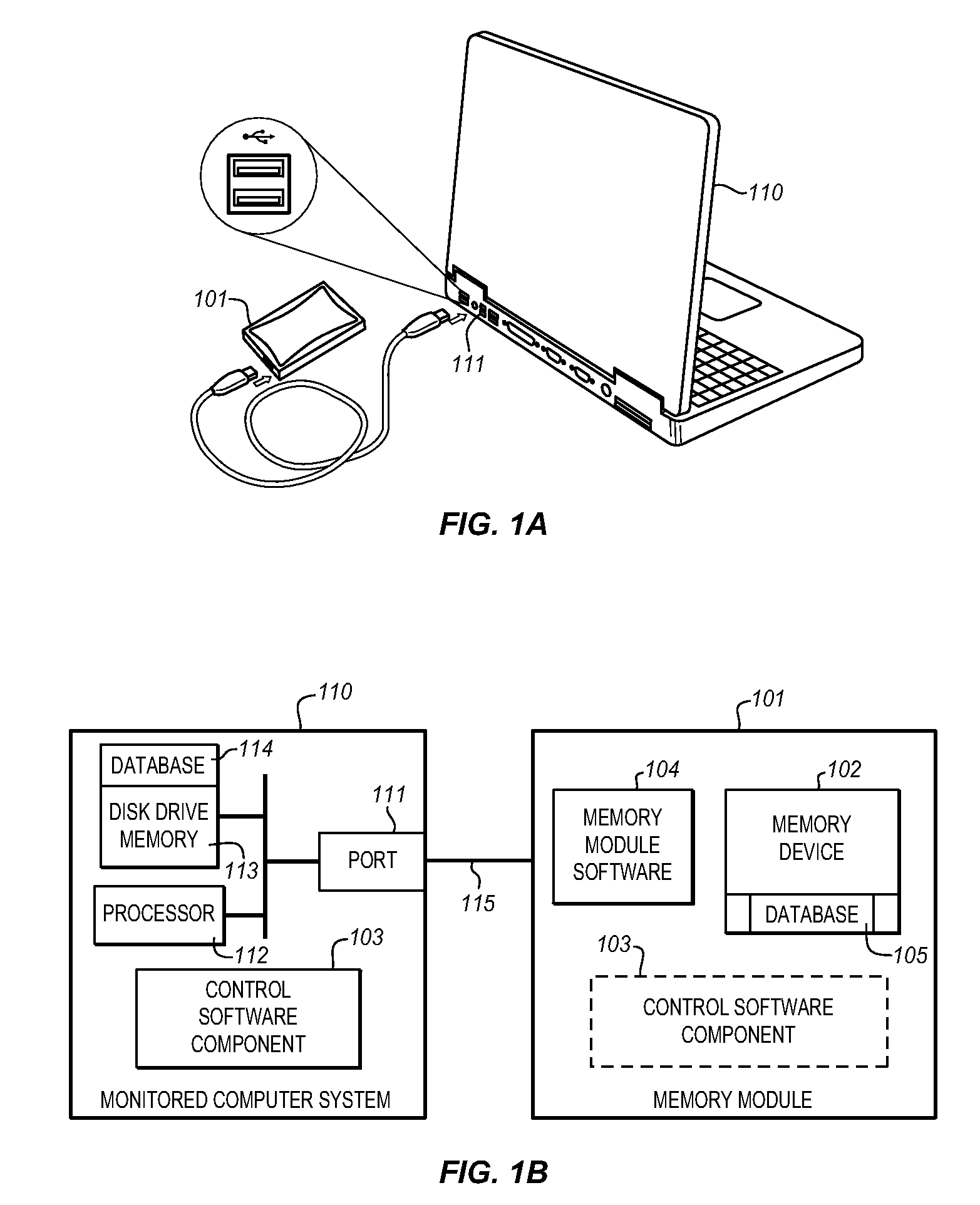
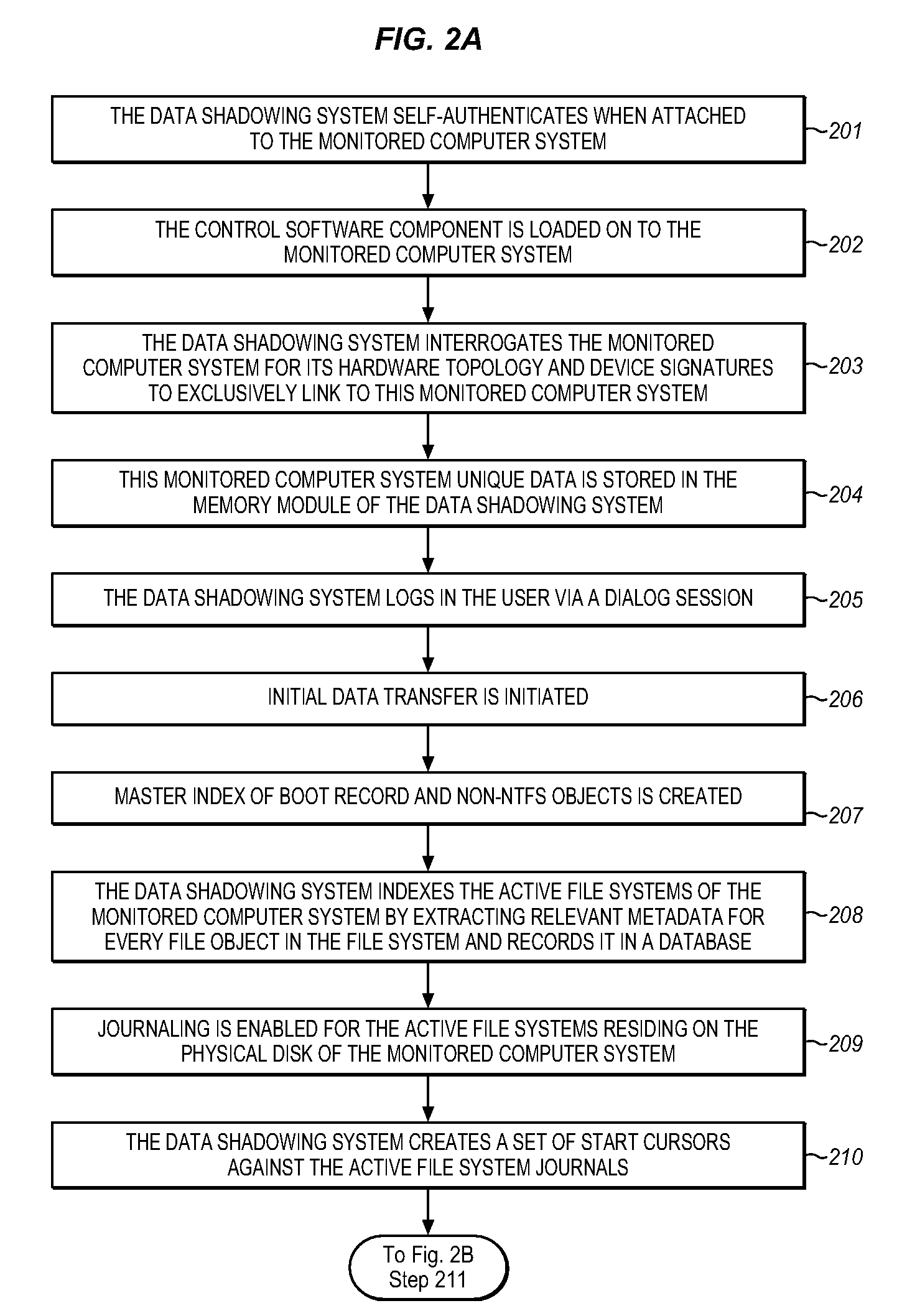
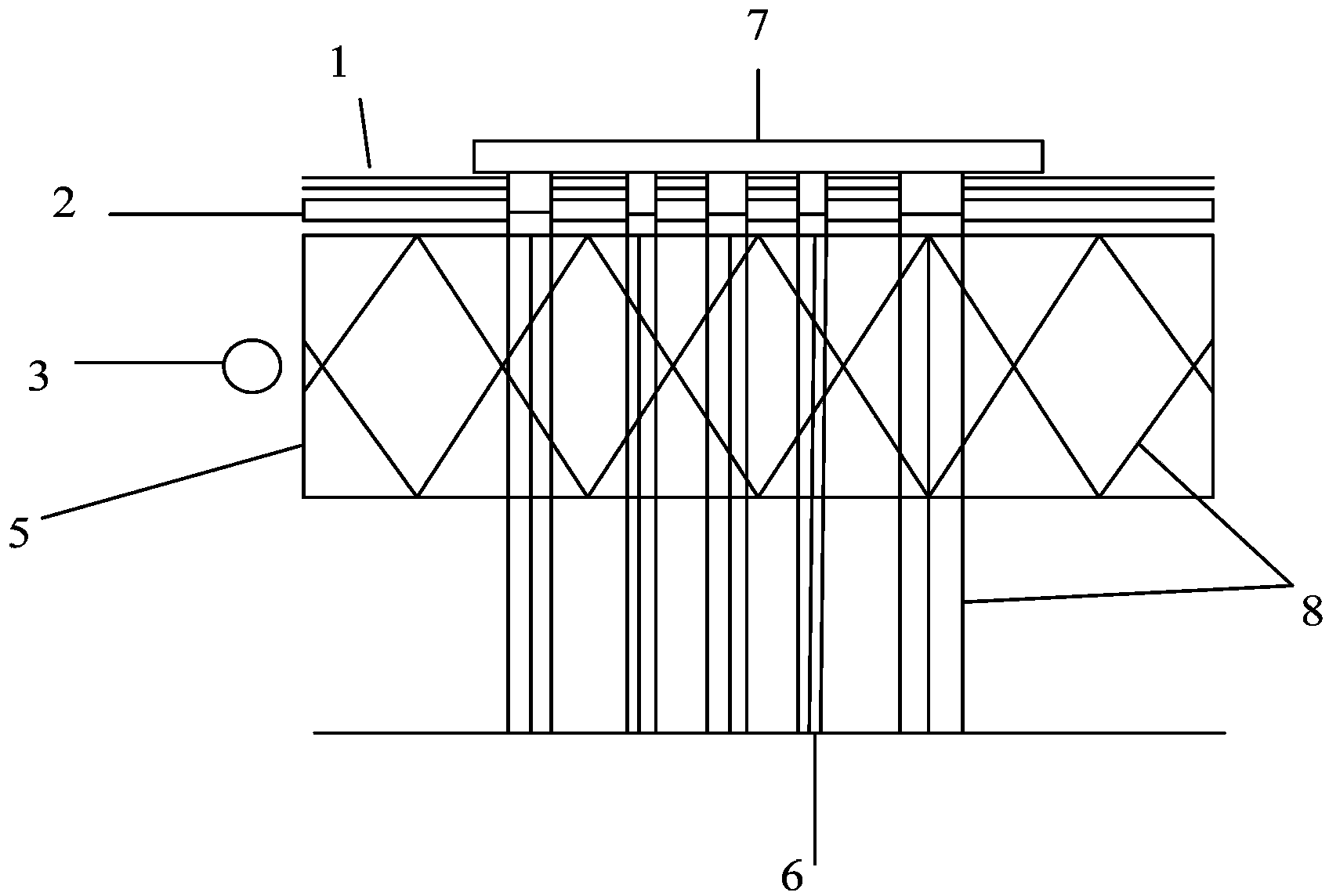
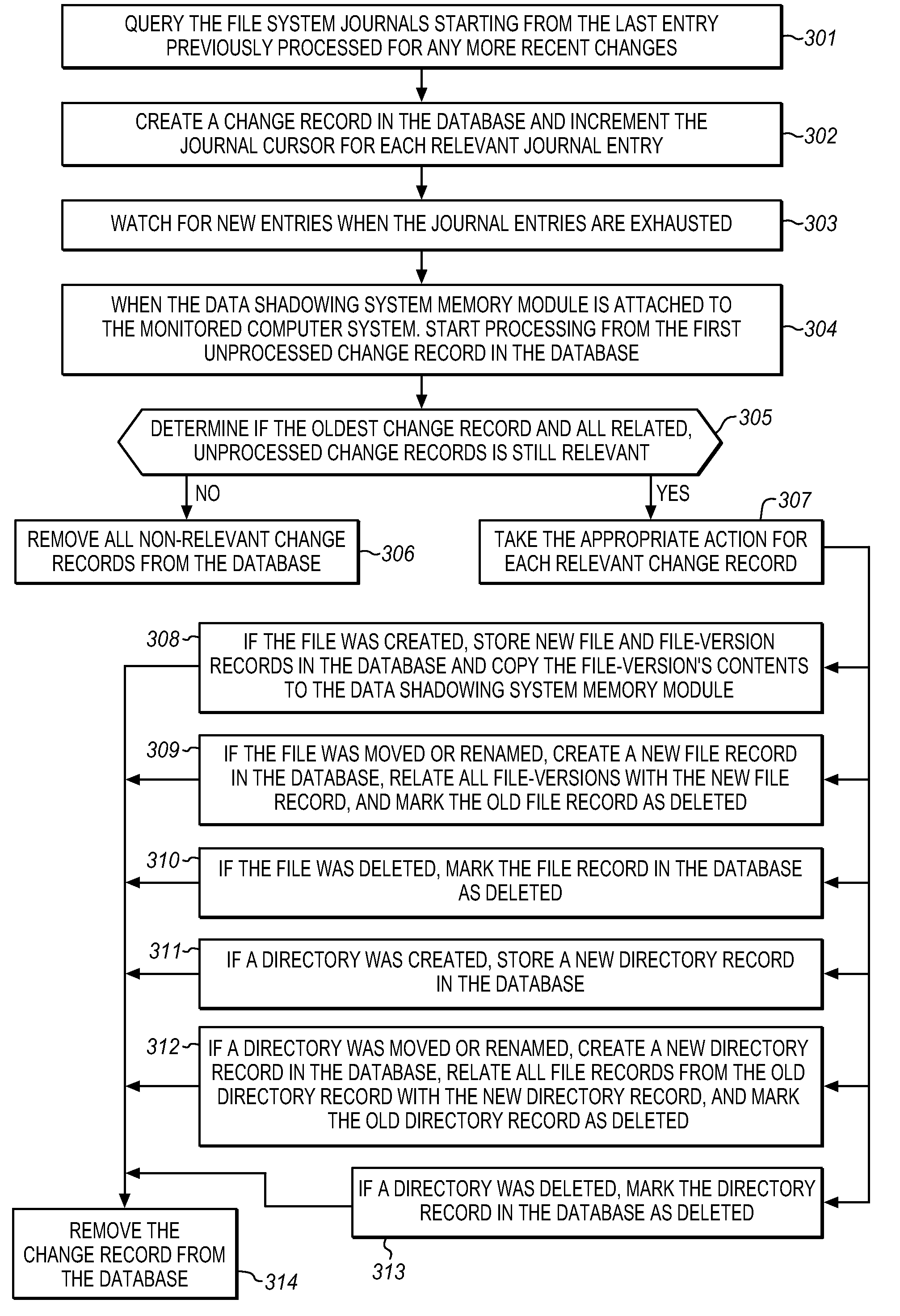
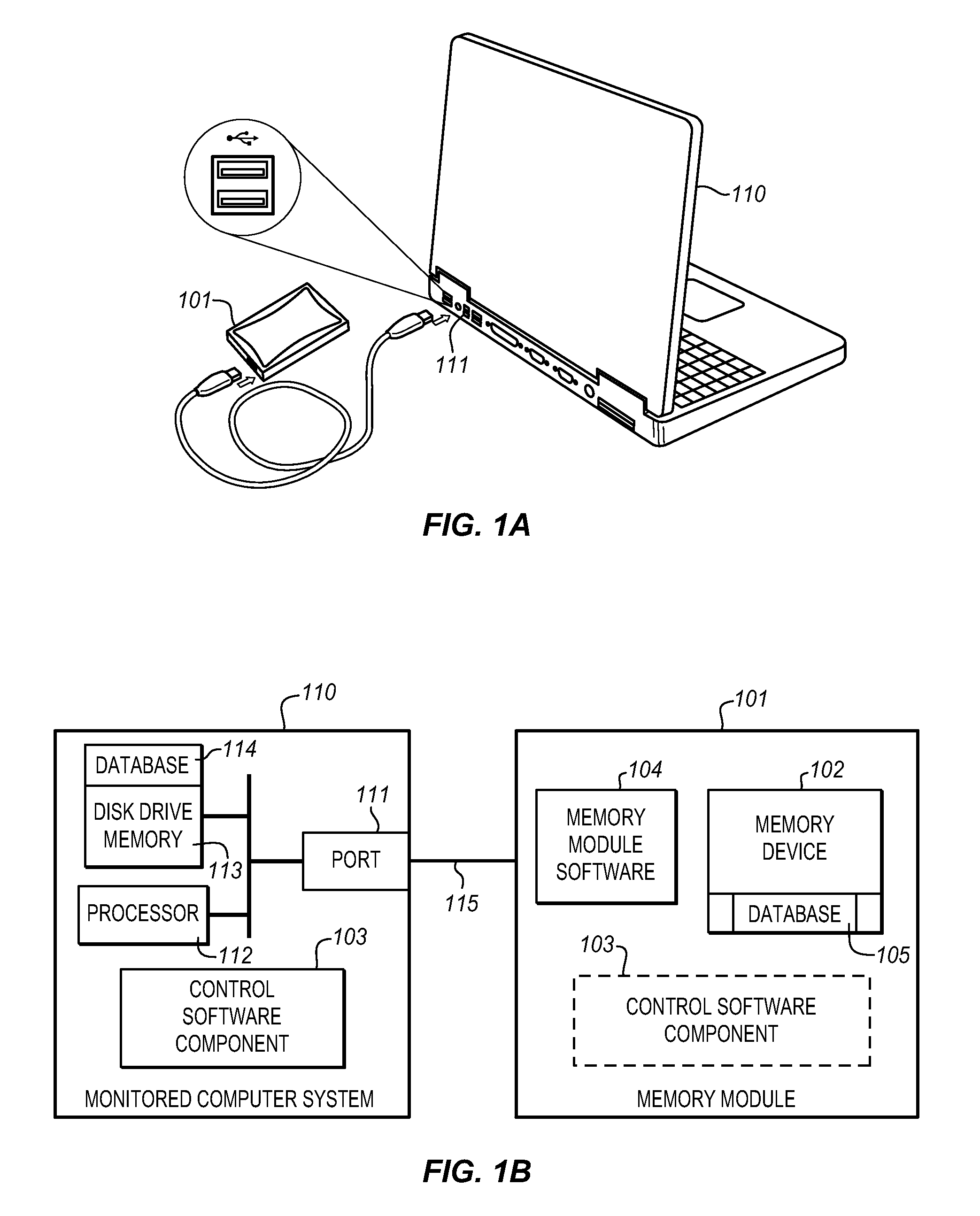
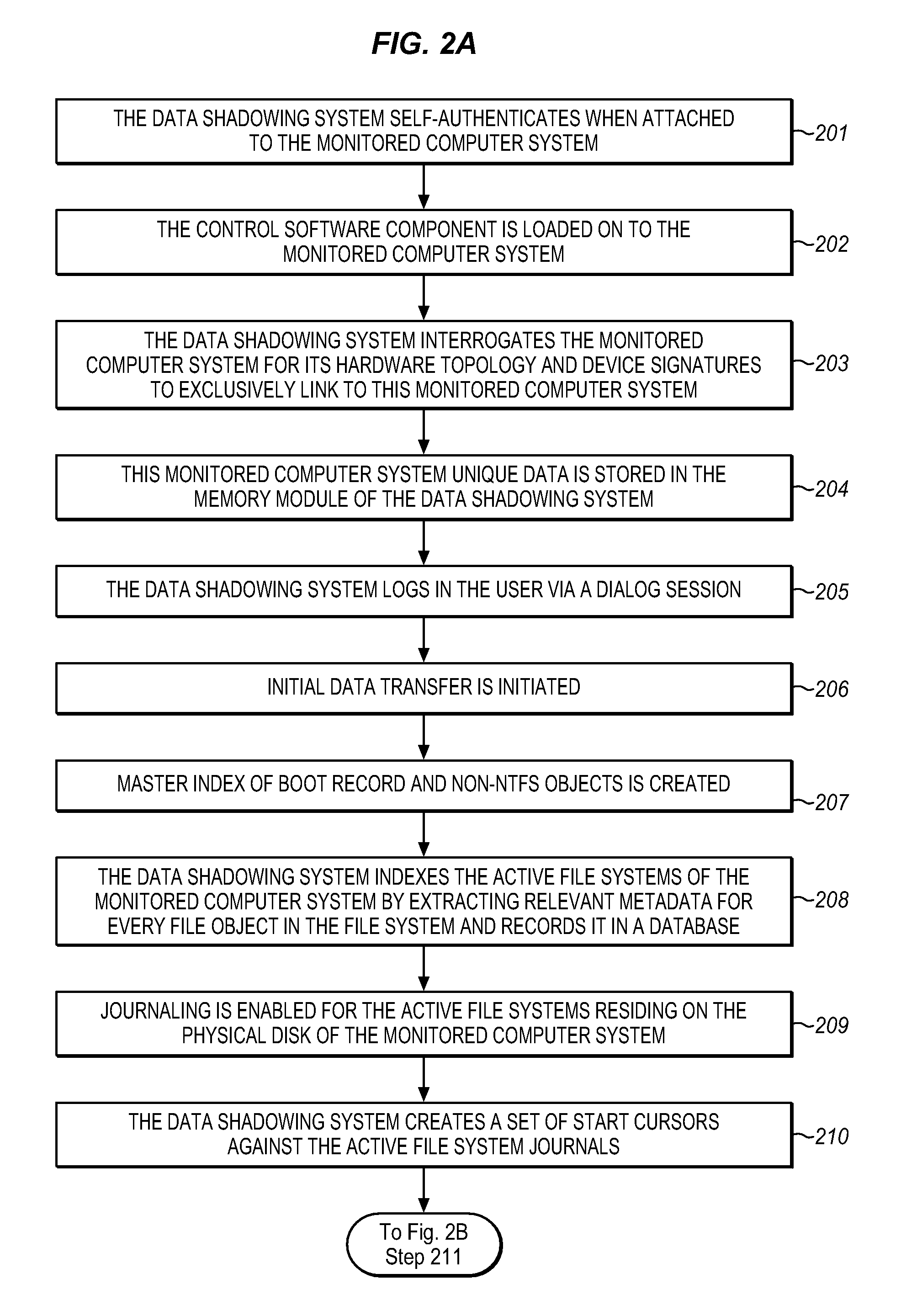
The Data Shadowing System comprises a memory module that is connected to the monitored computer system via an existing input / output port to store the shadowed data. The memory module includes a memory device for data storage as well as software, including a control software component that is automatically installed on the monitored computer system when the memory module is first connected to the monitored computer system, as well as associated module software for maintaining a record of the data stored on the memory device. The Data Shadowing System automatically stores the data on the memory module in a single format, while representing it in a data management database in two formats: disk sectors and files. The Data Shadowing System thereby efficiently tracks and stores the state of multiple file systems over time, while allowing for correct disk-level and file-level restoration to a point-in-time without storing redundant data.
Owner:CARBONITE CORP
System for automatically recovering a computer memory using shadowed data and file directory structures
ActiveUS20080104148A1Efficiently track and storeError detection/correctionDigital data processing detailsFile systemTerm memory
The Data Shadowing System comprises a memory module that is connected to the monitored computer system via an existing input / output port to store the shadowed data. The memory module includes a memory device for data storage as well as software, including a control software component that is automatically installed on the monitored computer system when the memory module is first connected to the monitored computer system, as well as associated module software for maintaining a record of the data stored on the memory device. The Data Shadowing System automatically stores the data on the memory module in a single format, while representing it in a data management database in two formats: disk sectors and files. The Data Shadowing System thereby efficiently tracks and stores the state of multiple file systems over time, while allowing for correct disk-level and file-level restoration to a point-in-time without storing redundant data.
Owner:CARBONITE CORP
System exception capturing method, main system, shadow system and intelligent equipment
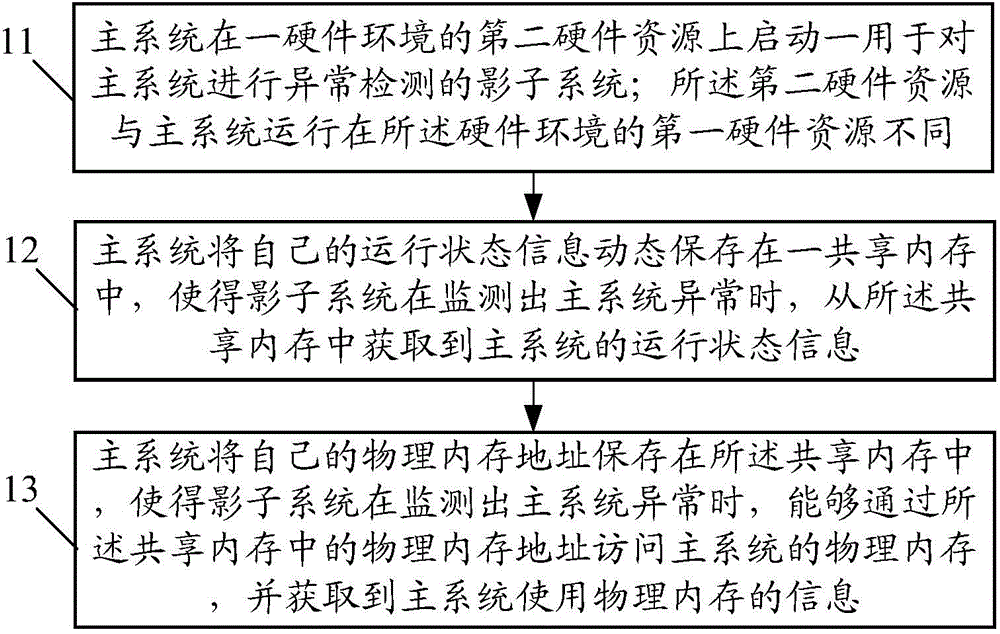
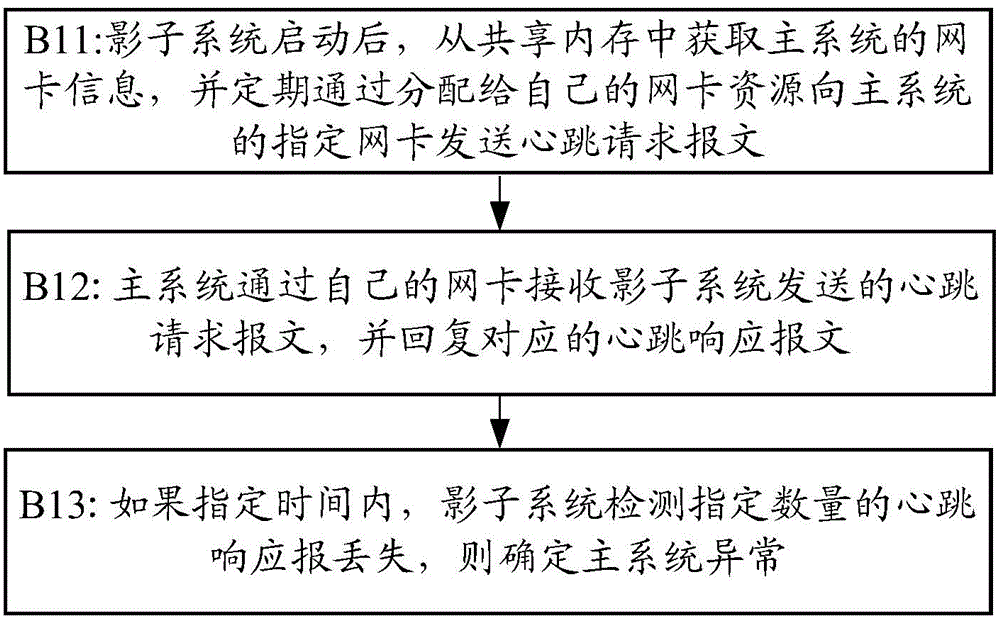
The invention provides a system exception capturing method, a main system, a shadow system and intelligent equipment. The main system side method includes the steps that the shadow system used for performing exception detection on the main system is started by the main system on a second hardware resource of a hardware environment; the second hardware resource is different from a first hardware resource, operating in the hardware environment, of the main system; own operation state information of the main system is dynamically stored in a shared memory, and when monitoring main system exceptions, the shadow system obtains the operation state information of the main system from the shared memory; own physical memory addresses of the main system are stored in the shared memory, and when monitoring main system exceptions, the shadow system can get access to a physical memory of the main system through the physical memory addresses in the shared memory and obtain the information of the physical memory used by the main system. According to the scheme, on the breakdown condition of the operation system (namely the main system), exception information can be captured.
Owner:ZTE CORP
Intelligent terminal about video image processing
InactiveCN105472358ASolve small, poor experience needsIncrease display sizePicture reproducers using projection devicesDigital output to display deviceGraphicsWireless transmission
The present invention relates to an intelligent terminal about video image processing. The intelligent terminal comprises a RGB-D imaging subsystem (100), a miniature projection subsystem (200), a control and processing unit (300), a wireless transmission subsystem (400), a battery and power subsystem (500) and a magnetic shell (600). The intelligent terminal has a three-dimensional space image detection function. Three-dimensional information can be stored and printed, and multi-screen experience can be completed. An image can be projected to any object, the arbitrary movement requirement of image display in any occasion is solved, and real and virtual border is further eliminated according to large area display. The intelligent terminal can be worn and can be used as a virtual keyboard, the requirements of arbitrarily changing a graphic, a size, a color, a background and a function according to preferences and not carrying a real keyboard of a user are satisfied, a realistic posture, a gesture and an action can be recognized as virtual information, and human-computer interaction is improved. Conversely, the realistic action can be controlled by the virtual information, and hands are liberated further.
Owner:万明 +1
Method for measuring movement velocity of high-density plasma and optical system
ActiveCN106604511AThe results are reasonably accurateThe principle is simplePlasma techniqueOptical elementsHigh densityTime delays
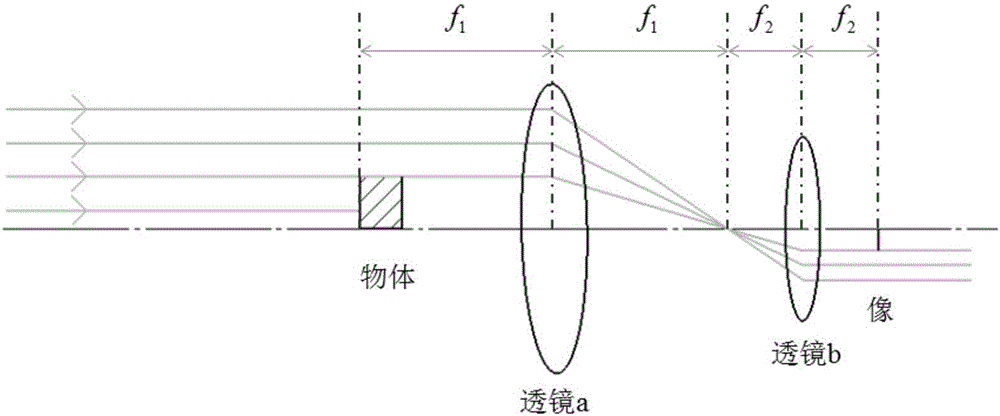
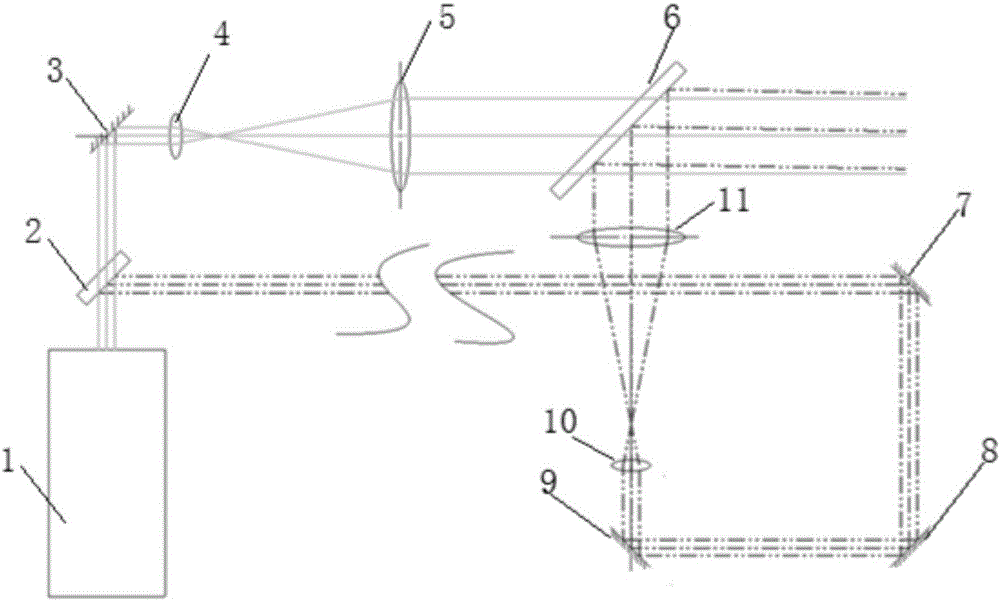
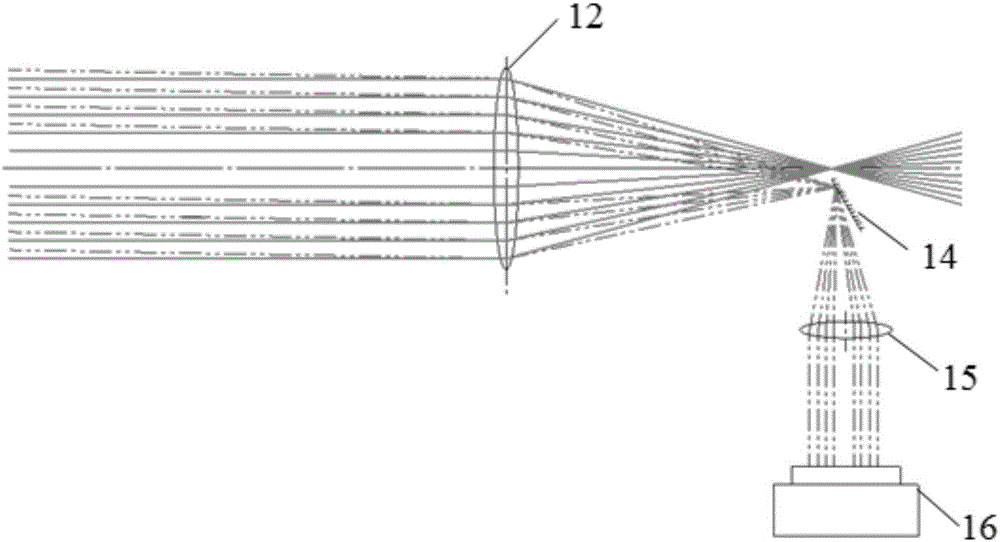
The invention provides a method for measuring movement velocity of a high-density plasma and an optical system. On the basis of a principle of light refraction occurrence at a high-density-gradient plasma boundary, an optical system is designed to generate two light beams with incidence at small angles, wherein the directions of the two light beams are perpendicular to the movement direction of the plasma boundary; and a 4f system is used for imaging and separation of the two light beams: a first light beam and a delay beam is realized at a focal point of a first lens. When velocity measurement is carried out, some light of the first light beam is deflected at the boundary of the plasma in high-speed movement and the deflected light enters the optical system where the delay beam is located; an image of the boundary of the plasma at a corresponding time is displayed at a camera; after time delay of the delay beam, the shape and location of the plasma at the corresponding time are displayed at the camera; and average movement velocity information of the plasma boundary at a corresponding time interval can be obtained in a shadow image. With a laser shadow system, the velocity of the boundary of the plasma in high-speed movement can be obtained effectively; and the result is reasonable and accurate.
Owner:NORTHWEST INST OF NUCLEAR TECH
Industrial control honeypot safety protection device and method
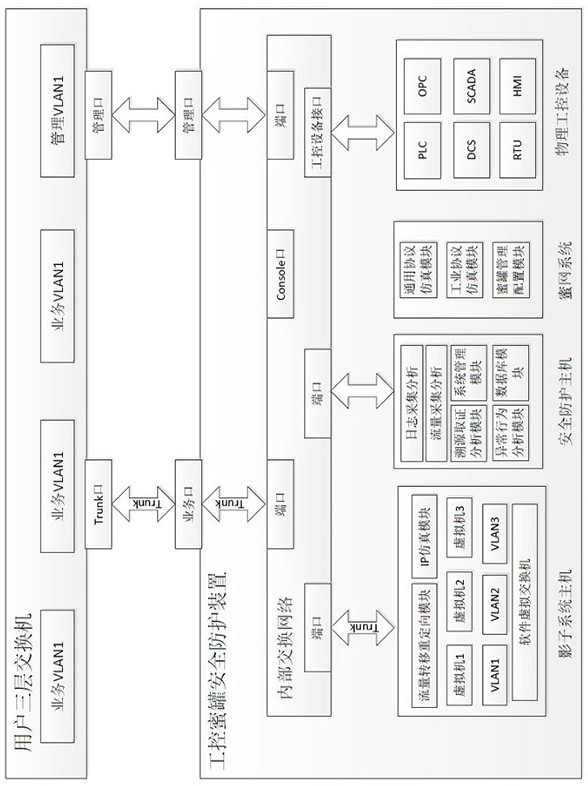
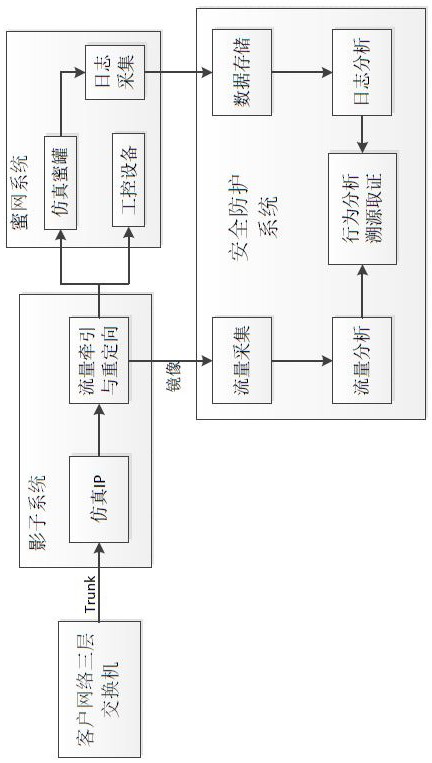
ActiveCN112578761ADoes not change the physical network structureChange structureTotal factory controlProgramme total factory controlSystems managementEmbedded system
The invention relates to the technical field of industrial safety, in particular to an industrial control honeypot safety protection device and method. A shadow system comprises an IP simulation module, a flow transfer redirection module, virtual switch software and a plurality of virtual machine systems; a honeynet system comprises a general protocol simulation module, an industrial protocol simulation module and a honeypot management configuration module; an industrial control equipment interface provides access to a PLC module, a DSC module, an RTU module, an OPC service, SCADA equipment and HMI man-machine interaction system industrial control equipment; and a safety protection system comprises a log acquisition and analysis module, a flow acquisition and analysis module, an abnormal behavior analysis module, a traceability evidence obtaining analysis module, a system management module and a system database module. The beneficial effects are that the device does not need to connecta network in series, does not need to configure a port flow mirror image in a bypass manner, does not change the physical network structure of a user, does not affect the network operation environment of the user, achieves the flexible deployment of the environment, and achieves plug-and-play.
Owner:山东云天安全技术有限公司
Electronic beam focusing equipment and electronic beam projection micro shadow system using the same equipment
InactiveCN1527358ALess bendingUniform electric/magnetic fieldRadiation/particle handlingElectric discharge tubesLower poleShadow system
An electron beam focusing apparatus and an electron beam projection lithography system employing the apparatus are provided, to allow a uniform electromagnetic field to be formed between a wafer and an electron beam emitter and to minimize the bending of an electron beam path due to the vibration of a vacuum chamber. The electron beam focusing apparatus comprises upper and lower magnets which are arranged in the upper and lower exterior parts of a vacuum chamber surrounding the space where a wafer is mounted, respectively, and form a magnetic field inside the vacuum chamber; upper and lower pole pieceswhich penetrate the ceiling wall and bottom wall of the vacuum chamber, respectively and are magnetically contact with the upper and lower magnets, respectively; and upper and lower projection parts which are projected in a ring-shape in the mutual corresponding faces of the upper and lower pole pieces. Preferably rubber plates containing a ferromagnetic material are inserted between the upper and lower magnets and the upper and lower pole pieces, respectively.
Owner:SAMSUNG ELECTRONICS CO LTD
Rendering system and method for webpage graphic images
InactiveCN106709041AReduce overheadImprove standardizationAnimationSpecial data processing applicationsImaging processingAnimation
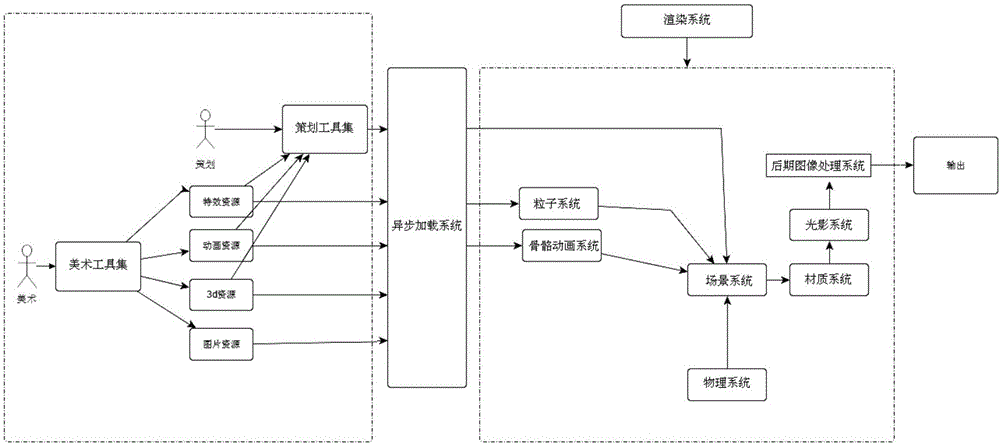
The invention relates to the technical field of graphic rendering, in particular to a rendering system and method for webpage graphic images. The rendering system for the webpage graphic images comprises an art and / or planning tool set, an asynchronous loading system, a particle effect system, a skeletal animation system, a scene system, a physical system, a texture system, a light and shadow system, a later image processing system and a rendering system. The asynchronous loading system is used for processing data processed by the planning tool set or directly processing data output by the art tool set; the scene system adopts the data of the asynchronous loading system, particle data and animation data, the data is introduced into the physical system, and operation is carried out; the physical system processes data of the scene system; the texture system processes the data of the scene system; the light and shadow system processes data of the texture system, and rendered targets are generated; the later image processing system processes data rendered into the rendered targets, and final images are generated.
Owner:深圳岂凡网络有限公司
Wireless router protection method and system based on cloud shadow system
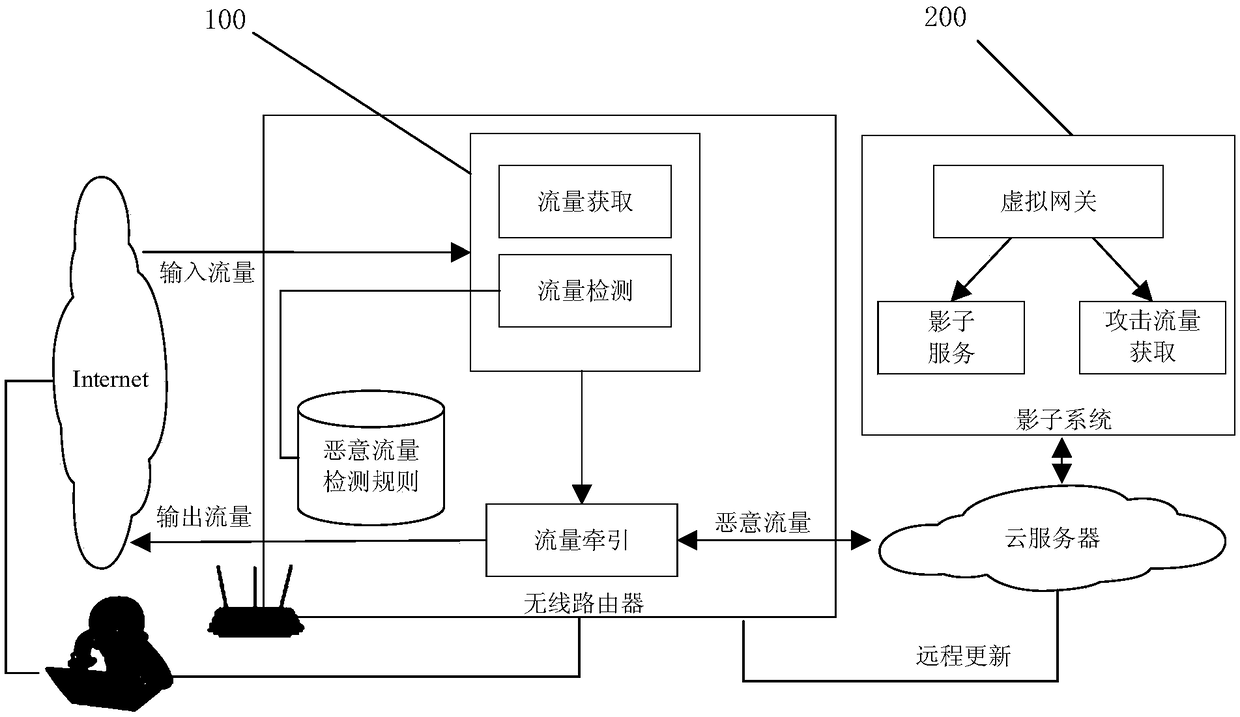
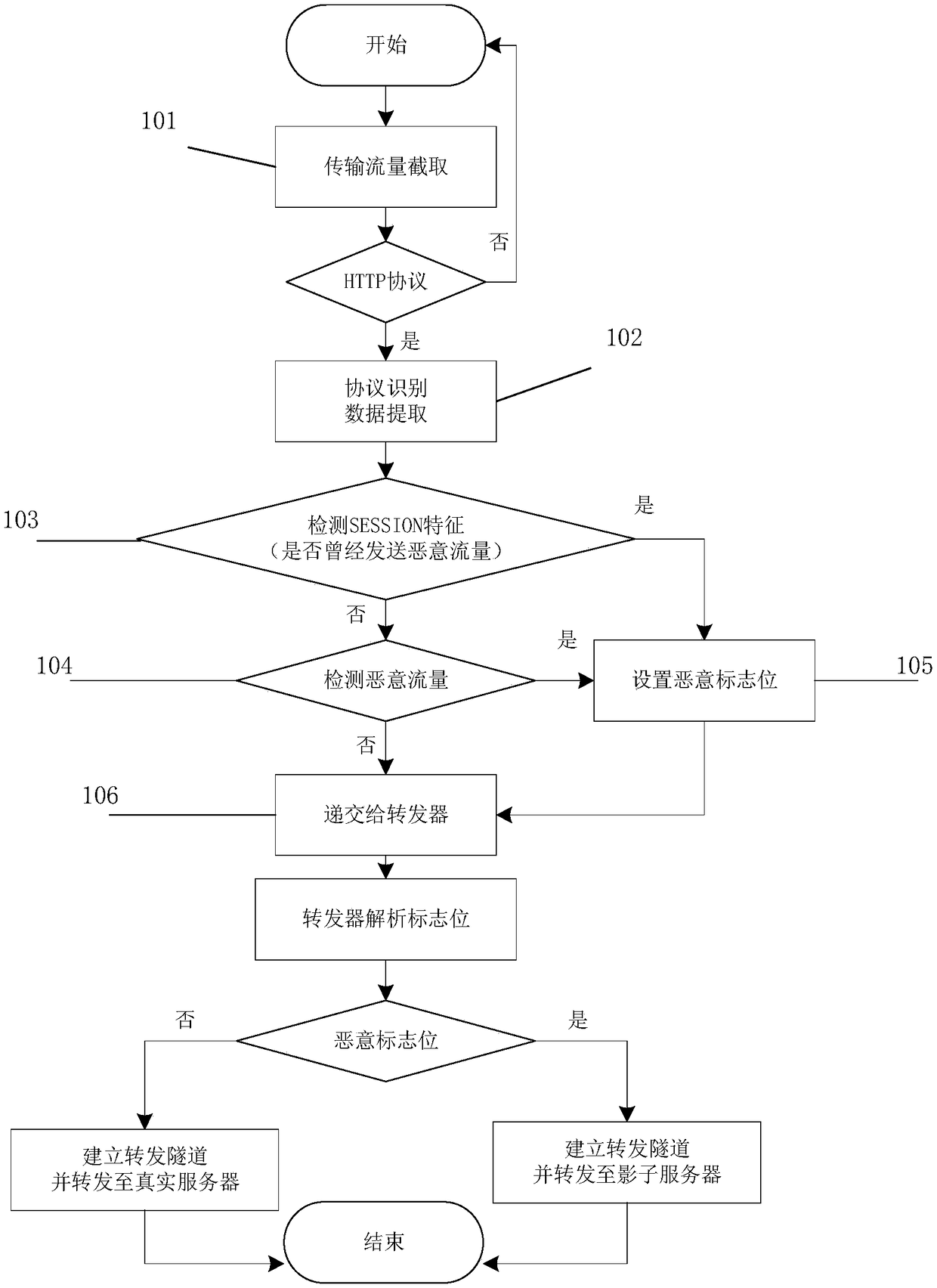
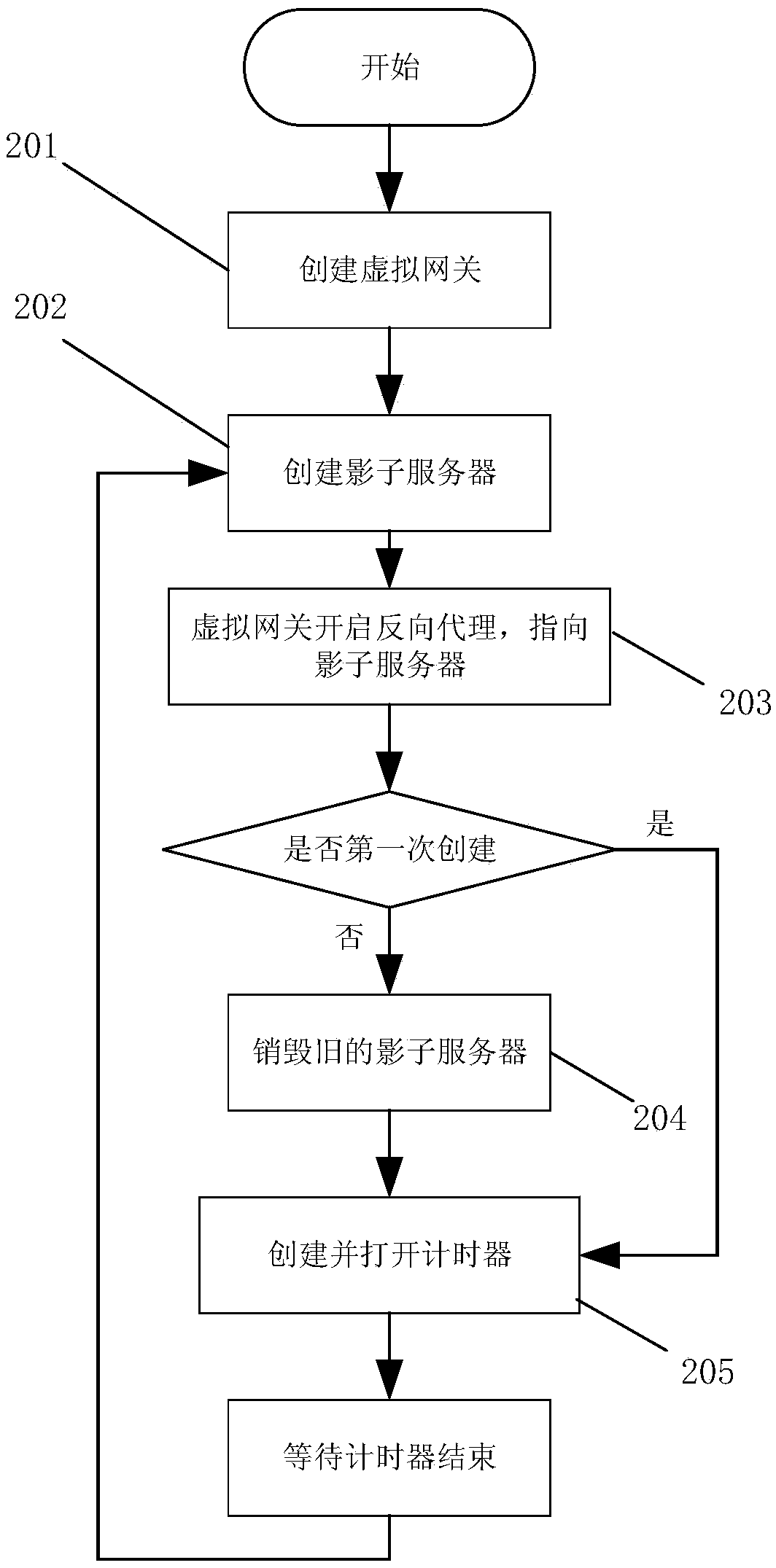
ActiveCN108809950AUnderstand the means of attackValid responseData switching networksTraffic capacityWireless router
The invention relates to a wireless router protection method and system based on a cloud shadow system. The method comprises the following steps: 1) detecting a network traffic data packet passing through a wireless router to judge whether the network traffic data packet is a malicious traffic data packet; and 2) forwarding the detected malicious traffic data packet to the cloud shadow system, thereby implementing the protection of the wireless router. The system comprises the wireless router and a cloud server, wherein the wireless router comprises a traffic acquisition module, a traffic detection module and a traffic traction module, and the cloud server comprises the cloud shadow system. According to the wireless router protection method and system provided by the invention, an attackeris introduced into a cloud shadow system that is completely the same as a user wireless router system, the wireless router protection method is a wireless router lightweight protection scheme based on the cloud shadow system, and a security worker can further understand the attack means of the attacker conveniently and make more effective response according to the attack means of the attacker.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Network security protection method and network security protection system
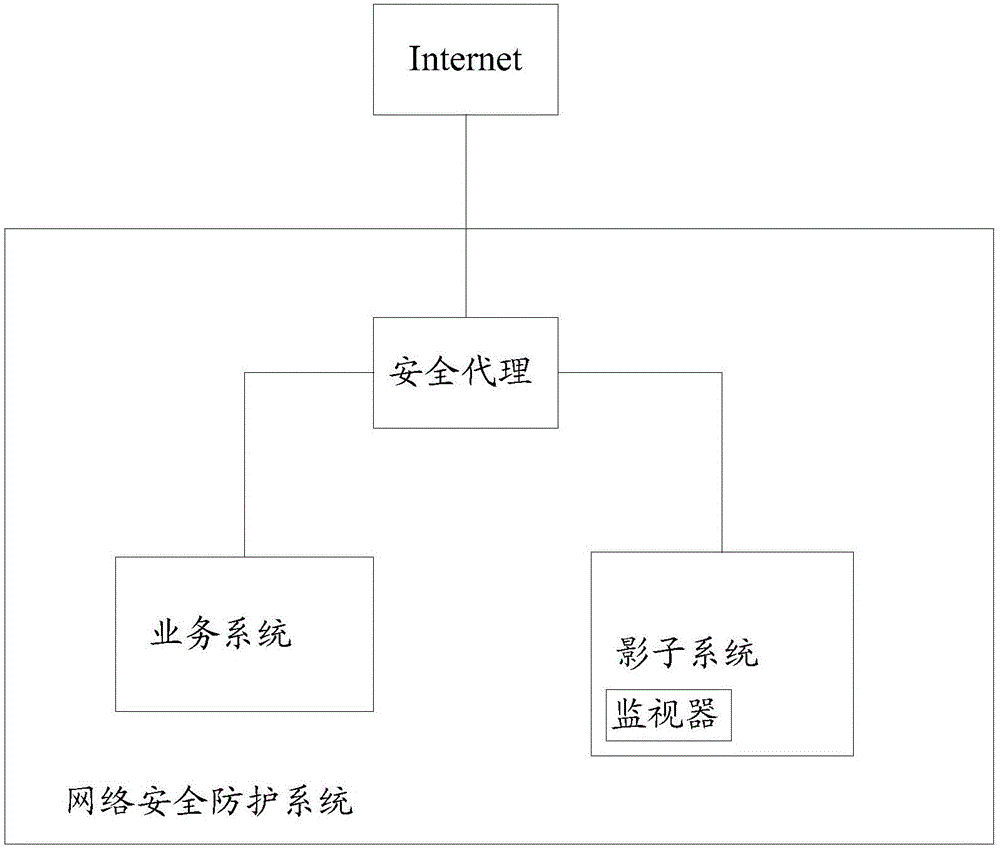
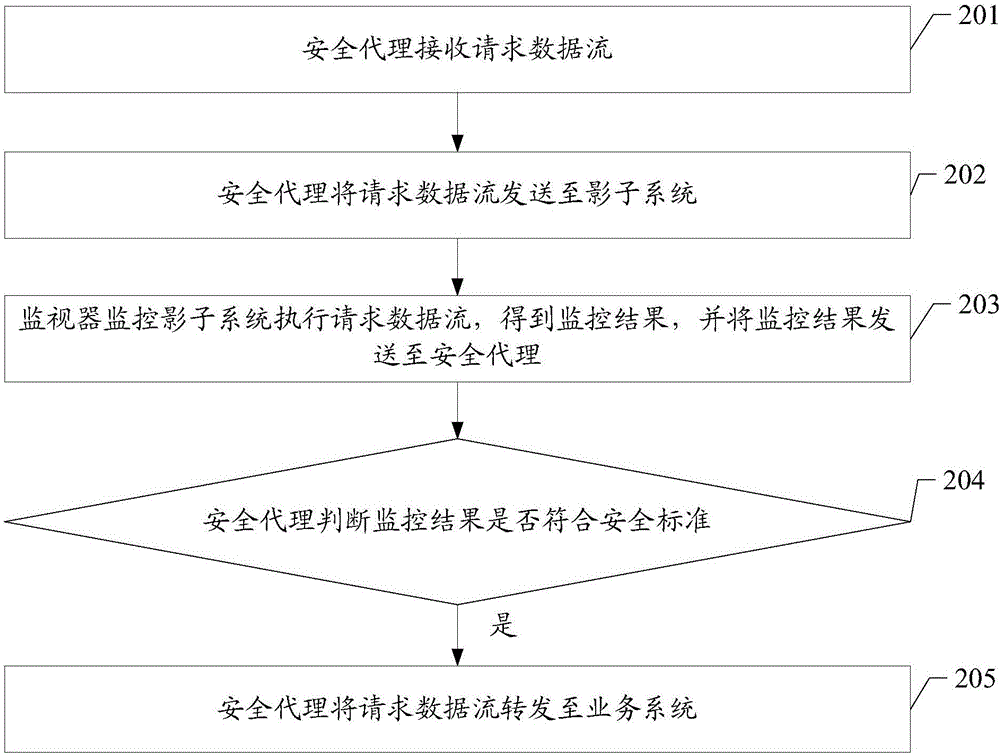
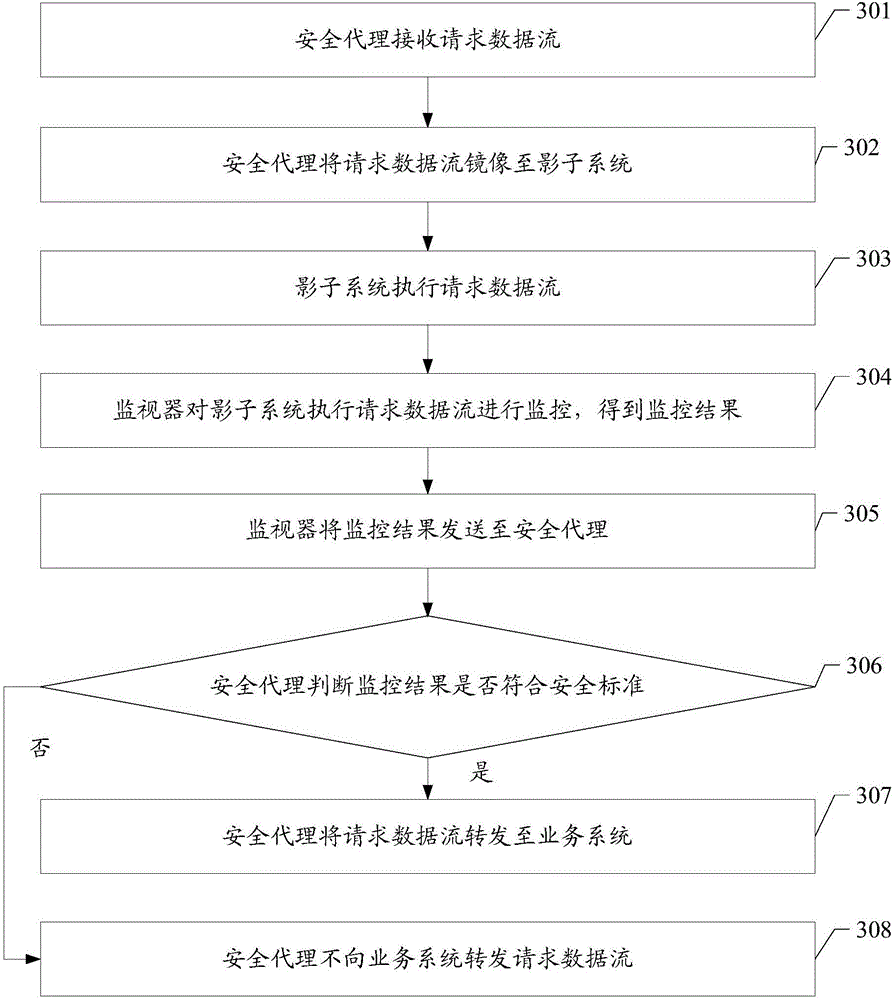
The invention discloses a network security protection method and a network security protection system and is used for improving protection of an unknown attack mode and judgment of a malicious attack, and enabling a service system to be more secure. The method provided by the embodiment of the invention comprises the steps that a security agent receives a request data stream; the security agent sends the request data stream to a shadow system; a monitor monitors performance of the request data stream carried out by the shadow system, thereby obtaining a monitoring result, and sends the monitoring request to the security agent; the security agent judges whether the monitoring result satisfies a security standard or not; and the security agent forwards the request data stream to the service system if the monitoring result satisfies the security standard.
Owner:SANGFOR TECH INC
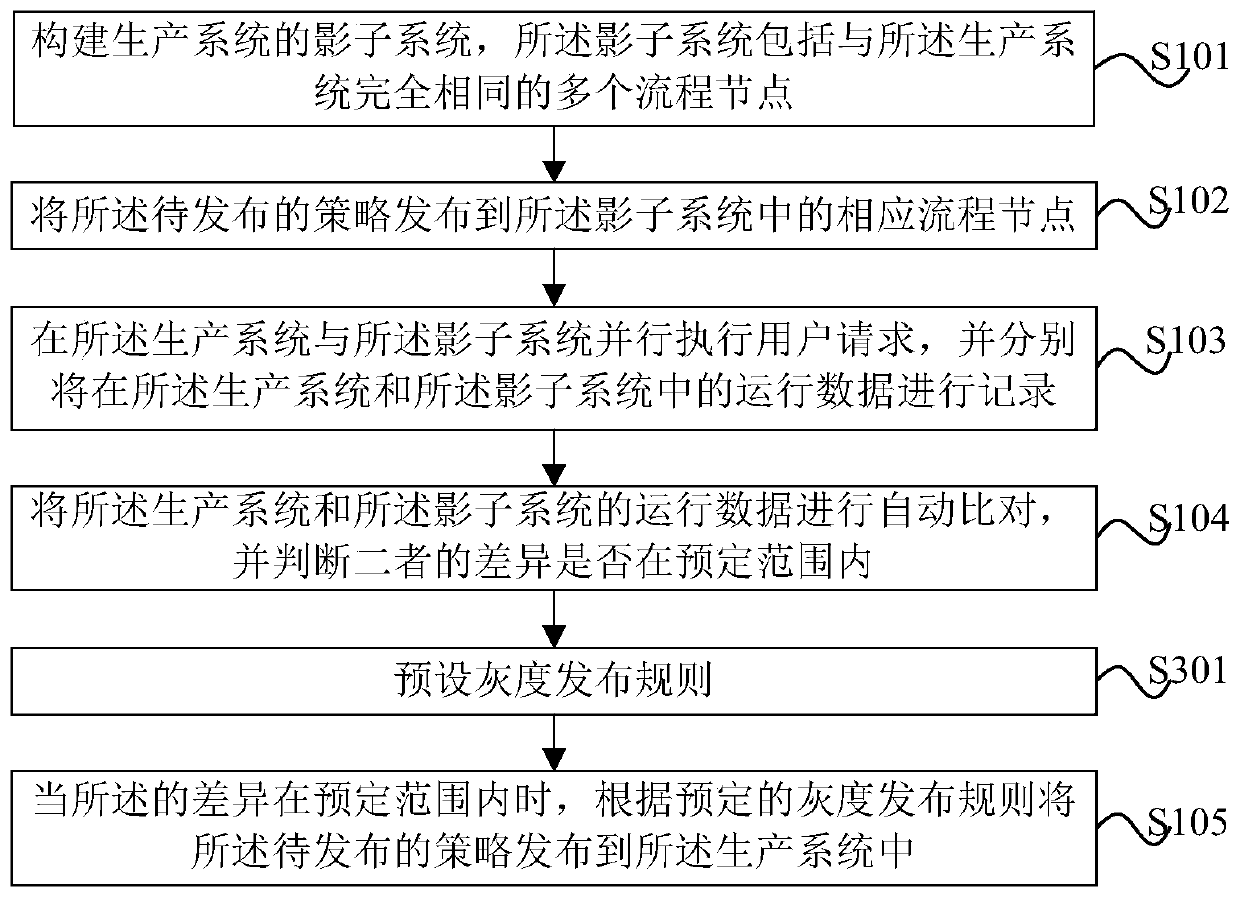
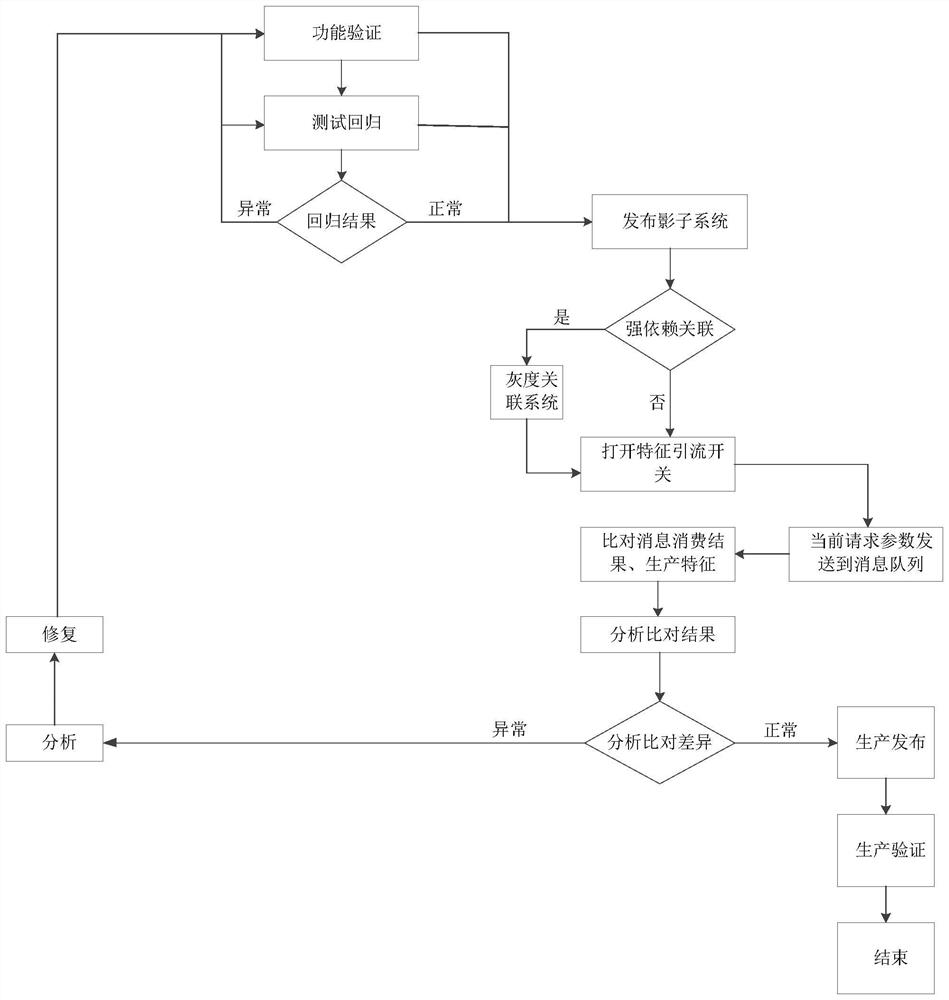
Strategy release method and system based on whole-process gray release and electronic equipment
PendingCN111580855ASolving difficult-to-evaluate problemsGuaranteed stabilityFinanceVersion controlProcess engineeringShadow system
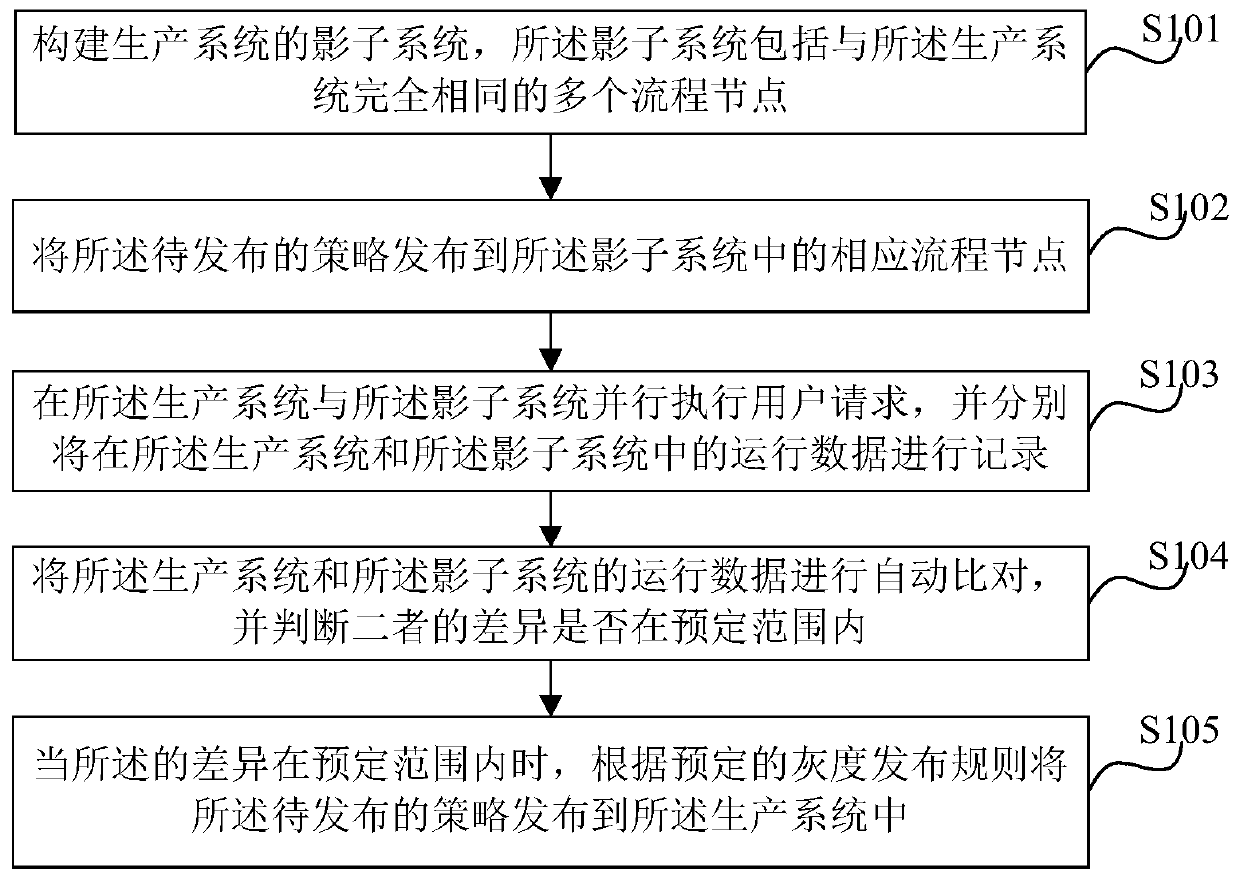
The invention provides a strategy publishing method based on full-process gray release, which is used for automatically publishing a strategy to be published in a production system in a gray release manner, and comprises the following steps: constructing a shadow system of the production system, the shadow system comprising a plurality of process nodes which are completely the same as those of theproduction system; publishing the strategy to be published to a corresponding process node in the shadow system; executing the user request in parallel in the production system and the shadow system,and respectively recording the operation data in the production system and the shadow system; automatically comparing the operation data of the production system and the shadow system, and judging whether the difference between the operation data is within a preset range or not; and when the difference is within a predetermined range, publishing the to-be-published strategy to the production system according to a predetermined gray publishing rule. According to the method, potential production problems can be eliminated, the release risk of a production system is reduced, and the strategy release efficiency is improved.
Owner:上海淇毓信息科技有限公司
System for automatically recovering a computer memory using shadowed data and file directory structures
ActiveUS8126851B2Efficiently track and storeDigital data processing detailsError detection/correctionFile systemTerm memory
The Data Shadowing System comprises a memory module that is connected to the monitored computer system via an existing input / output port to store the shadowed data. The memory module includes a memory device for data storage as well as software, including a control software component that is automatically installed on the monitored computer system when the memory module is first connected to the monitored computer system, as well as associated module software for maintaining a record of the data stored on the memory device. The Data Shadowing System automatically stores the data on the memory module in a single format, while representing it in a data management database in two formats: disk sectors and files. The Data Shadowing System thereby efficiently tracks and stores the state of multiple file systems over time, while allowing for correct disk-level and file-level restoration to a point-in-time without storing redundant data.
Owner:OPEN TEXT CORPORATION
Network security protection method and system
InactiveCN114268452AProtect the safety of useAggressive Behavior AccurateSecuring communicationInternet trafficAttack
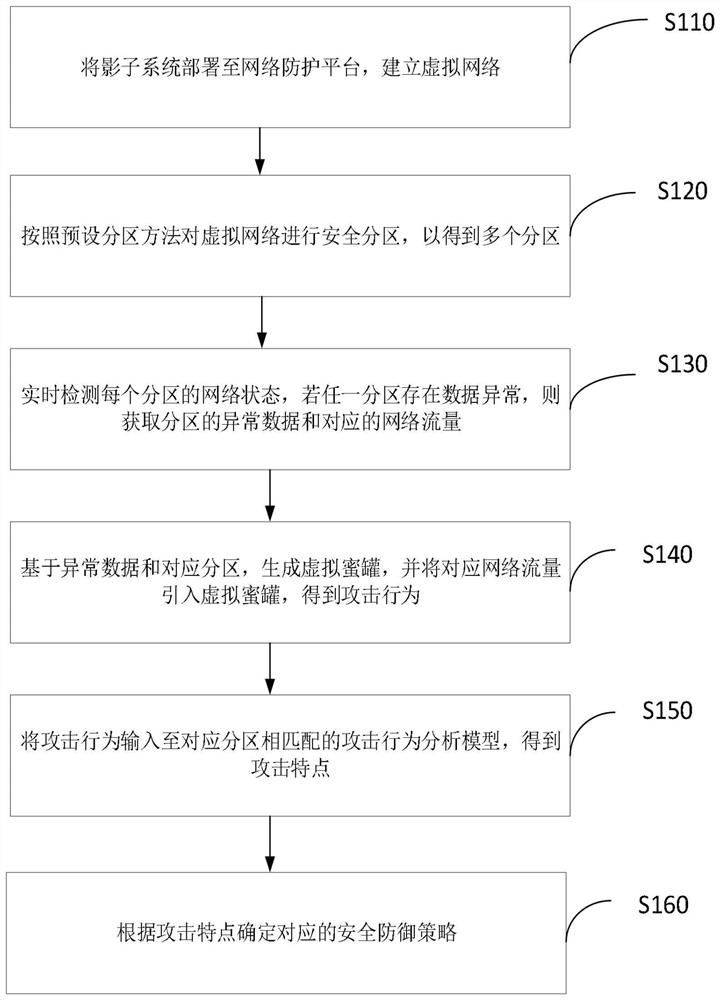
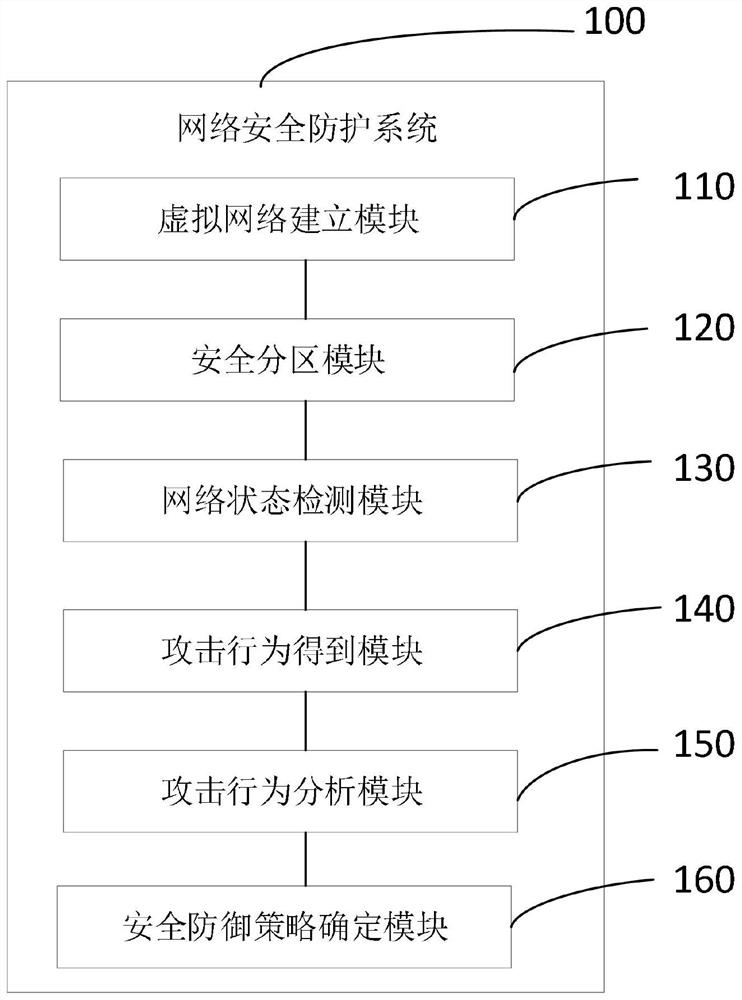
The invention provides a network security protection method and system, and relates to the technical field of network security. The method comprises the following steps: deploying a shadow system to a network protection platform, and establishing a virtual network; and performing secure partitioning on the virtual network according to a preset partitioning method to obtain a plurality of partitions. And detecting the network state of each partition in real time, and if any partition has data exception, obtaining the exceptional data of the partition and the corresponding network flow. And generating a virtual honeypot based on the abnormal data and the corresponding partition, and introducing the corresponding network traffic into the virtual honeypot to obtain an attack behavior. And inputting the attack behaviors into the attack behavior analysis models matched with the corresponding partitions to obtain attack characteristics. And determining a corresponding security defense strategy according to the attack characteristics. Therefore, the security defense strategy is determined according to the attack characteristics of different partition attack behaviors, so that the security defense strategy is more adaptive to the attack behaviors, the protection resources are configured as required according to different attack characteristics, and a better protection effect is achieved.
Owner:杨磊
Pressure sensing light and shadow imaging system and imaging method thereof
The invention provides a pressure sensing light and shadow imaging system and an imaging method thereof. The pressure sensing light and shadow imaging system comprises bearing media, a sensing surface, light and shadow media, a light pool, a light and shadow system and an imaging surface. The bearing media are arranged at the uppermost end of the pressure sensing light and shadow imaging system. The lower portion of the bearing media makes contact with the sensing surface. The lower portion of the sensing surface is closely combined with the upper surface of the light pool provided with the light and shadow media. The imaging surface is arranged below the light pool. Textured substances to be imaged are placed on the upper surface of the bearing media. The bearing media transmit borne pressure to the sensing surface. The sensing surface senses pressure distribution of the textured substances. Light rays in the light pool are reflected by the sensing surface to reflect out the contact tightness between the sensing surface and the bearing media and to generate a pressure distribution image of the textured substances. The sensing surface projects the generated pressure distribution image of the textured substances to the imaging surface. The pressure sensing light and shadow imaging system can be used for forming the contact pressure image of the textured substances and enabling the formed image to be capable of reflecting out the contact pressure distribution, the image of the textured substances and the pressed sequence.
Owner:DALIAN EVERSPRY SCI & TECH
System for automatically shadowing data and file directory structures that are recorded on a computer memory
ActiveUS7640280B2Efficiently track and storeData processing applicationsDigital data information retrievalFile systemComputerized system
The Data Shadowing System comprises a memory module that is connected to the monitored computer system via an existing input / output port to store the shadowed data. The memory module includes a memory device for data storage as well as software, including a control software component that is automatically installed on the monitored computer system when the memory module is first connected to the monitored computer system, as well as associated module software for maintaining a record of the data stored on the memory device. The Data Shadowing System automatically stores the data on the memory module in a single format, while representing it in a data management database in two formats: disk sectors and files. The Data Shadowing System thereby efficiently tracks and stores the state of multiple file systems over time, while allowing for correct disk-level and file-level restoration to a point-in-time without storing redundant data.
Owner:OPEN TEXT CORPORATION
Icon safe operation method under voice screen mouse check
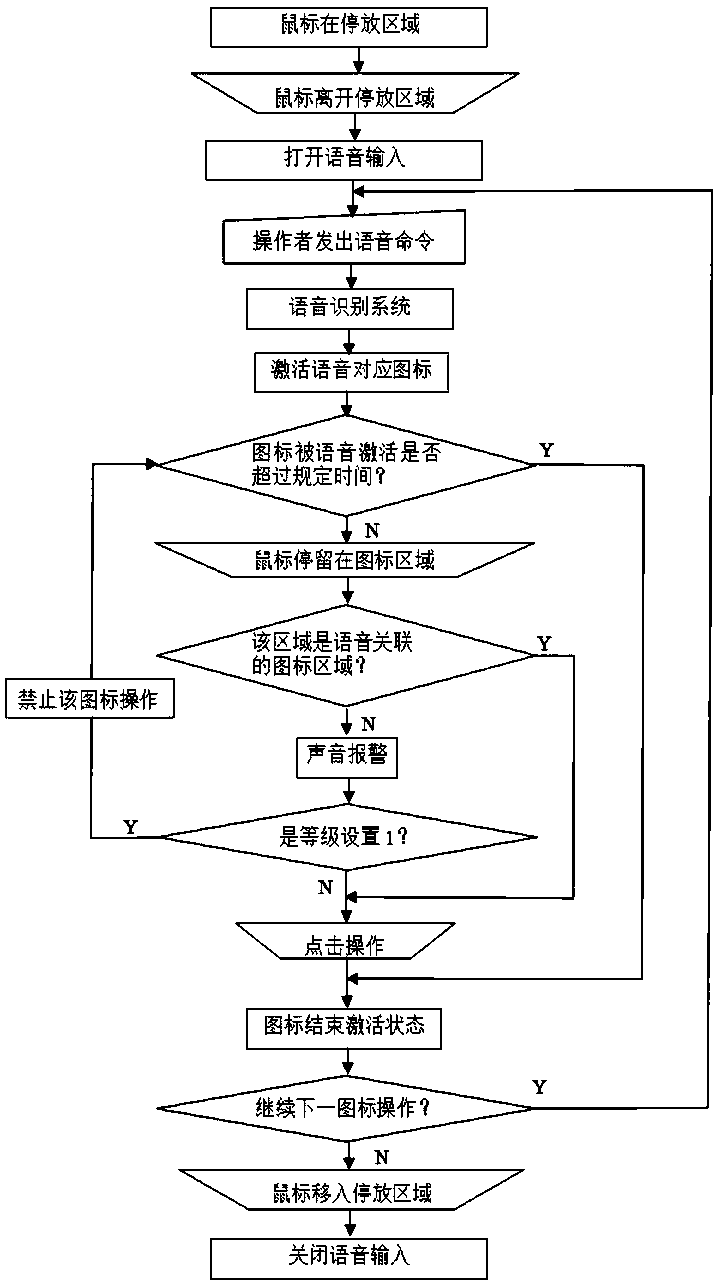
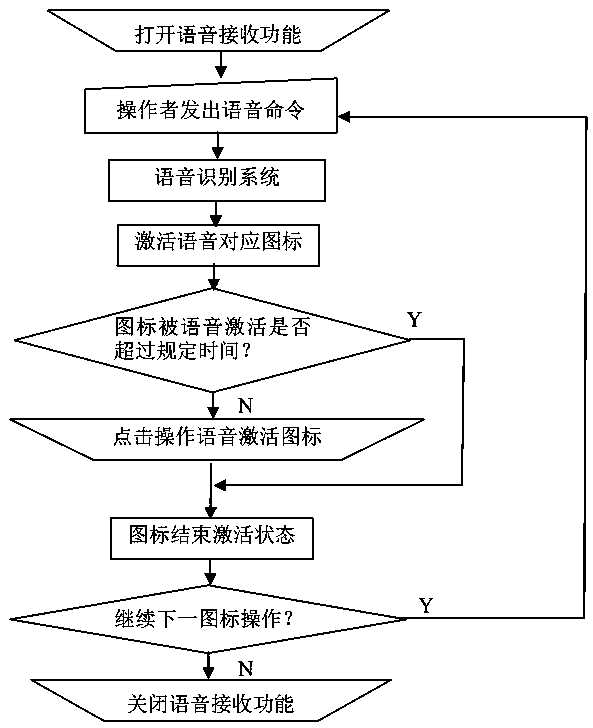
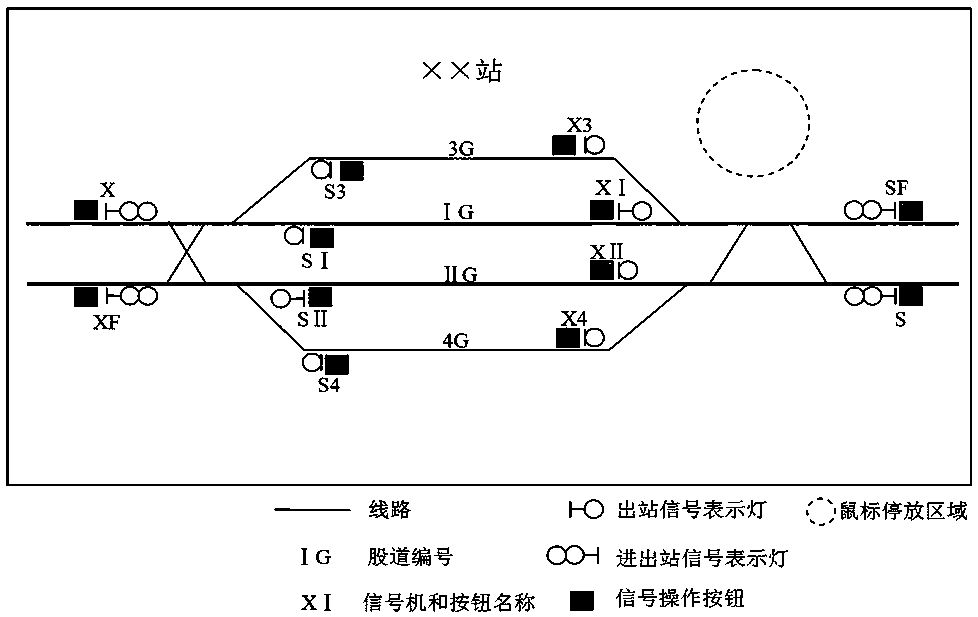
ActiveCN109189280AReduce misuseAccurate operationRailway traffic control systemsAlarmsComputer terminalFacial recognition system
Provided is an icon safe operation method under the voice screen mouse check. An operator utters a voice associated icon, an icon used to specify the operation and displayed on the screen and an iconpointed to when the mouse stops moving are checked and compared, and operation authority and warning of operation are given by a system. The basic features of the method are that the association between the specific voice and the icon is established, the associated icon is activated through the voice input of the voice recognition system, and the associated icon and the icon pointed out when the mouse stops moving are checked and compared. For touchscreen computers and mobile terminals, the icons associated with the voice emitted by the operator are displayed on the screen for binary verification, and the system gives the right to operate. In addition, shadow systems can be protected against existing systems. The invention utilizes the modern speech recognition tool to check the behavior of a person through a computer system to ensure the correct operation to the maximum extent and avoid accidents.
Owner:NANJING INST OF RAILWAY TECH
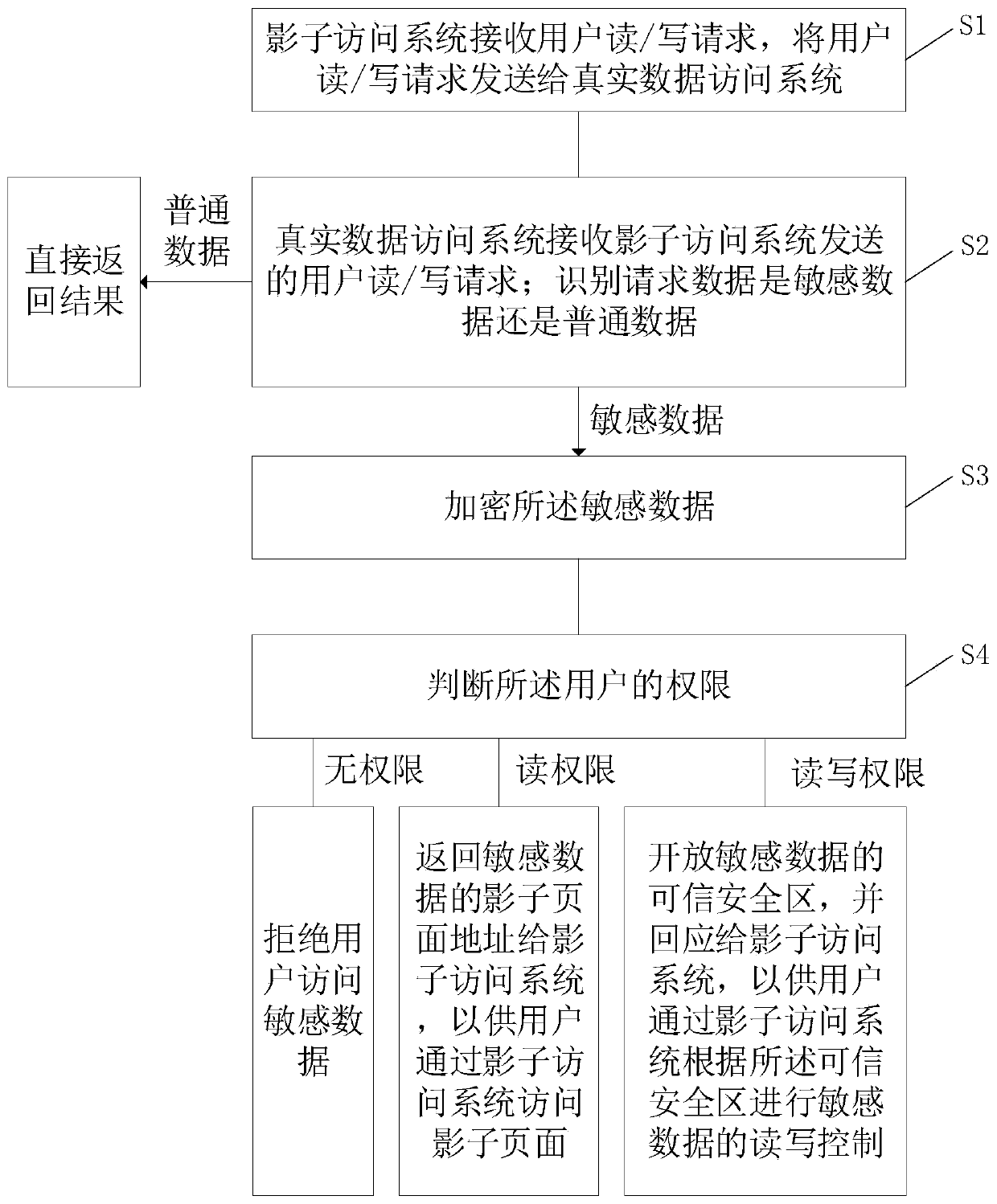
Sensitive data security protection method and system based on shadow system
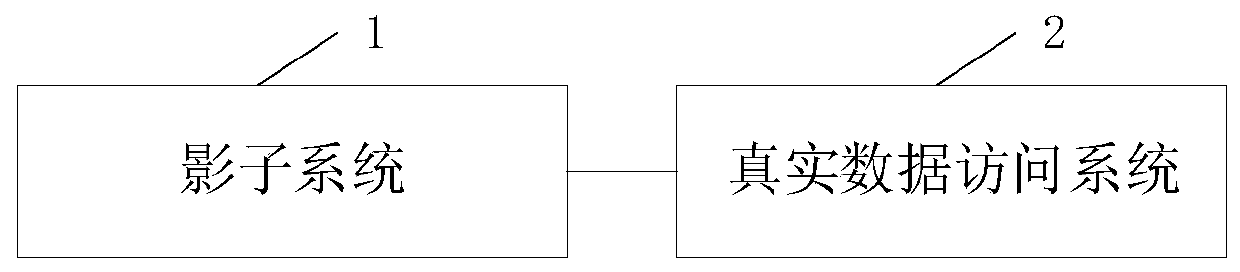
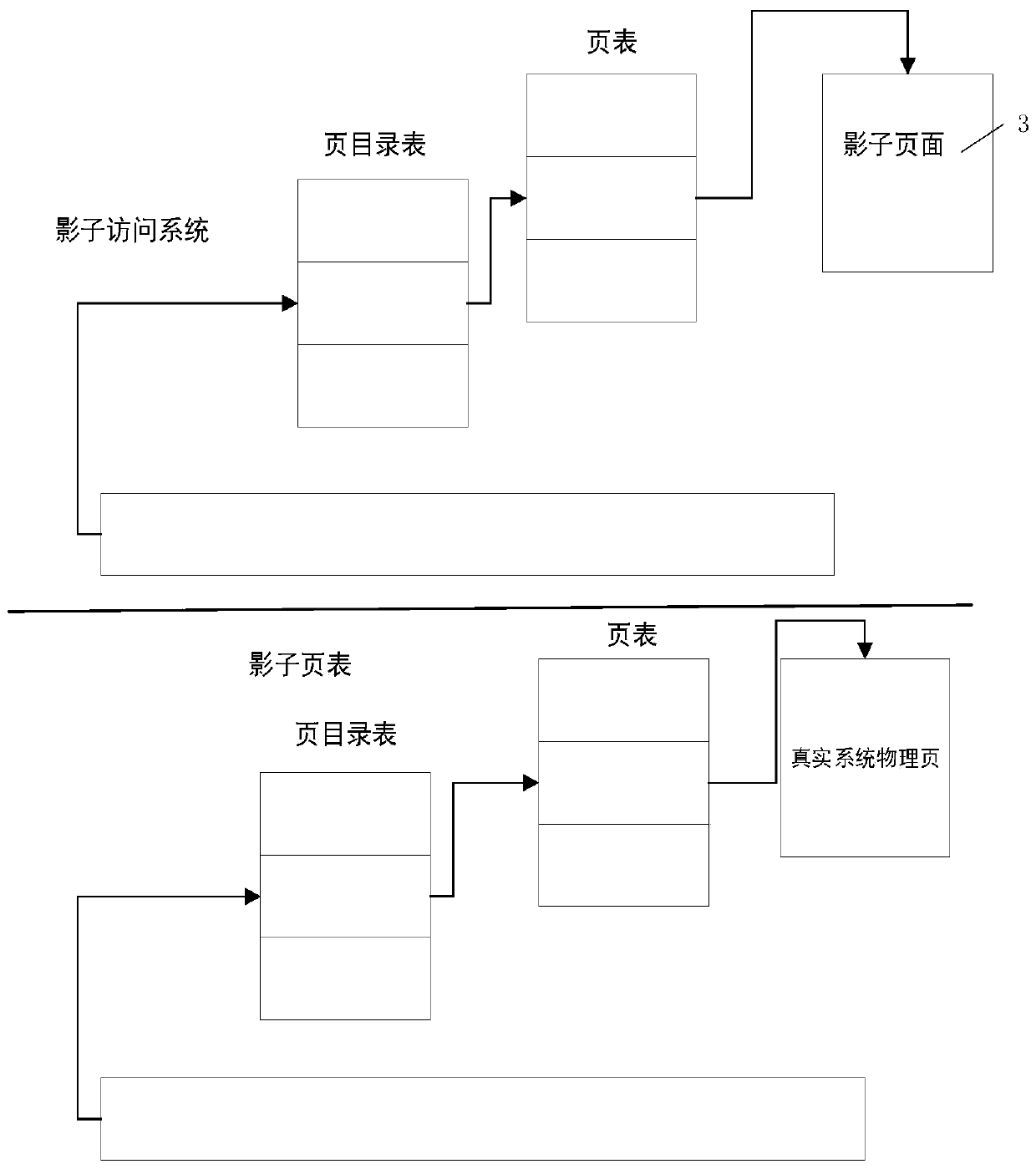
ActiveCN111563269ASecurity securityData storage securityDigital data protectionDigital data authenticationInternet privacyData access
The invention discloses a sensitive data security protection method and system based on a shadow system. The sensitive data security protection method comprises the steps: transmitting a shadow systemuser read / write request o a real data access system; by the real data access system, identifting whether the request data is sensitive data or common data; for common data, directly returning a result; for the sensitive data, encrypting the sensitive data, and determining the permission of the user; if the sensitive data access permission does not exist, refusing the user to access the sensitivedata; if only the sensitive data reading permission exists, returning a shadow page address of the sensitive data to the shadow system; and if the sensitive data read-write permission exists, openinga trusted security area of the sensitive data, and responding to the shadow system. The invention further discloses a response system. According to the technical scheme, the security of the sensitivedata is improved based on the shadow system.
Owner:NINGBO TRANSMISSION & DISTRIBUTION CONSTR +4
Intelligent interactive light and shadow stone backlight device
PendingCN113500876ALow costRealize stitching effectSpecial ornamental structuresLight effect designsStone carvingEngineering
The invention relates to the technical field of stone equipment, in particular to an intelligent interactive light and shadow stone backlight device. Compared with the prior art, the intelligent interactive light and shadow stone backlight device adopts a four-layer structural design; the uppermost layer is a light-transmitting stone carving layer; a composite material bonding layer is arranged at the bottom end of the light-transmitting stone carving layer; the lower end of the composite material bonding layer is a light and shadow system layer; the bottommost layer is a reinforced protection layer; the composite material bonding layer is made of a light-transmitting material and is in a light-transmitting state; the light and shadow system layer adopts a programmable light and shadow system; light and shadow images are designed and programmed according to natural lines or engraved patterns of the light-transmitting stone carving layer; a dynamic background light and shadow effect is achieved in cooperation with front and back patterns; an intelligent control module and a touch sensor can be arranged in the light and shadow system layer; a terminal is used for controlling interaction programs and patterns of stone products; the stone products can be achieved through cooperation with the touch sensor; many application scenes are added; and more design and imagination space is achieved.
Owner:王江
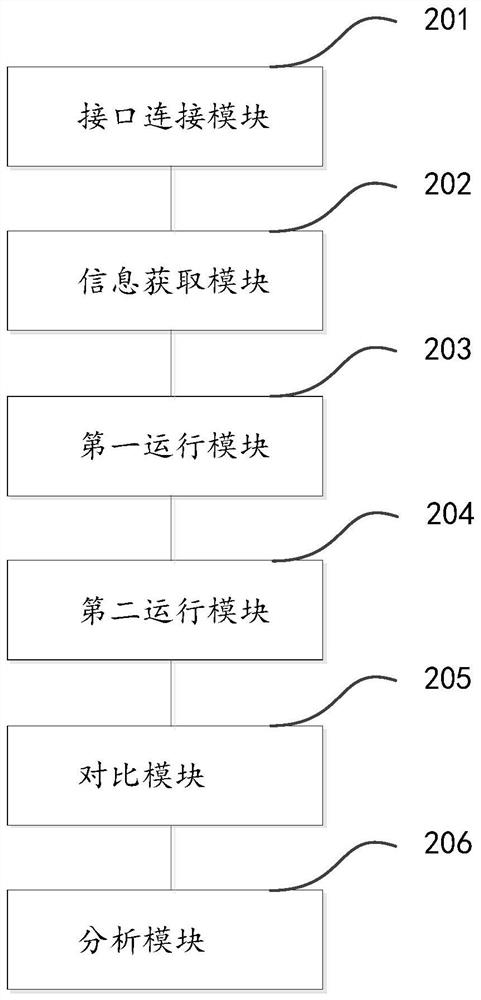
Characteristic comparison method and device based on shadow system and electronic equipment
PendingCN114253600AEnhanced authenticationImprove efficiencyVersion controlSoftware testing/debuggingOnline businessProcess engineering
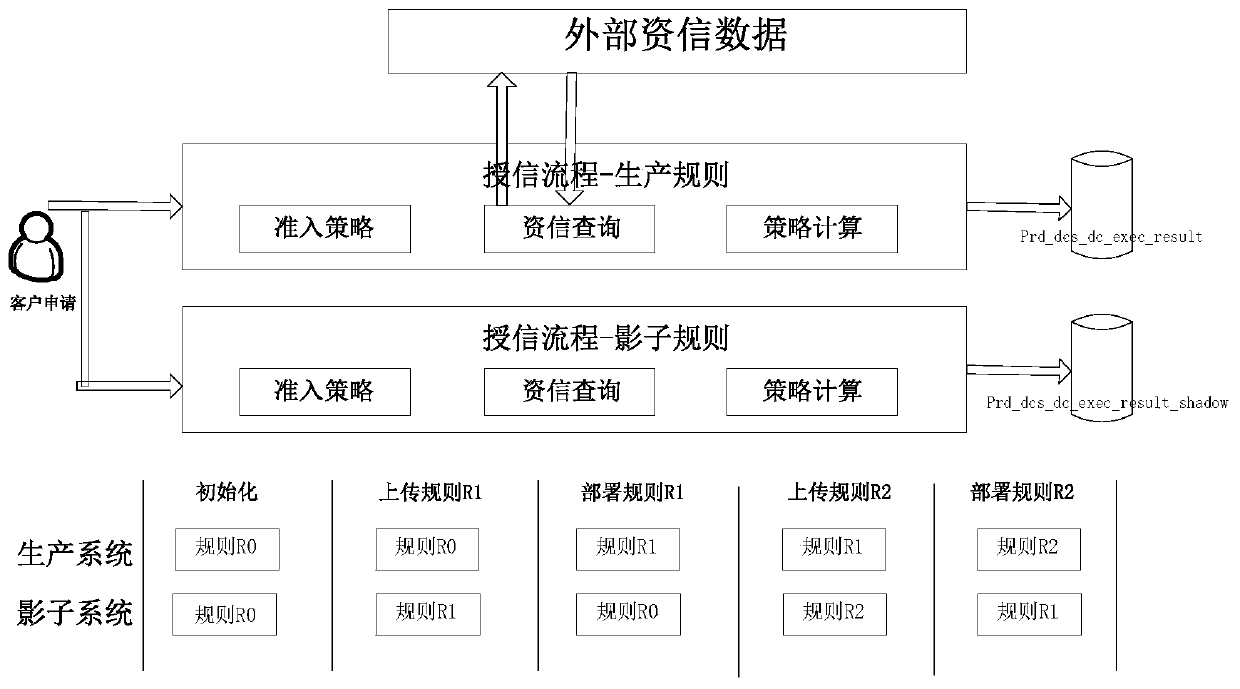
The invention relates to the technical field of computers, in particular to a feature comparison method and device based on a shadow system and electronic equipment, and the method comprises the steps: obtaining the production features of a pre-published business production version, the business production data of an online business production version, and the production features of the online business production version; operating an online business production version and the shadow system to obtain second business result data; comparing the first business result data with the second business result data, and comparing the production characteristics of the pre-published business production version with the production characteristics of the online business production system; and performing difference analysis on the comparison result, and processing the pre-published service production version according to the difference analysis result. According to the method, the shadow system is utilized to quickly discover the influence of the production version of the pre-published service on the production characteristics in the historical version, and the situation that verification discovery cannot be covered due to the influence on the calculation of the production characteristics in the historical version is avoided, so that production accidents are avoided.
Owner:SHANGHAI QIYUE INFORMATION TECH CO LTD
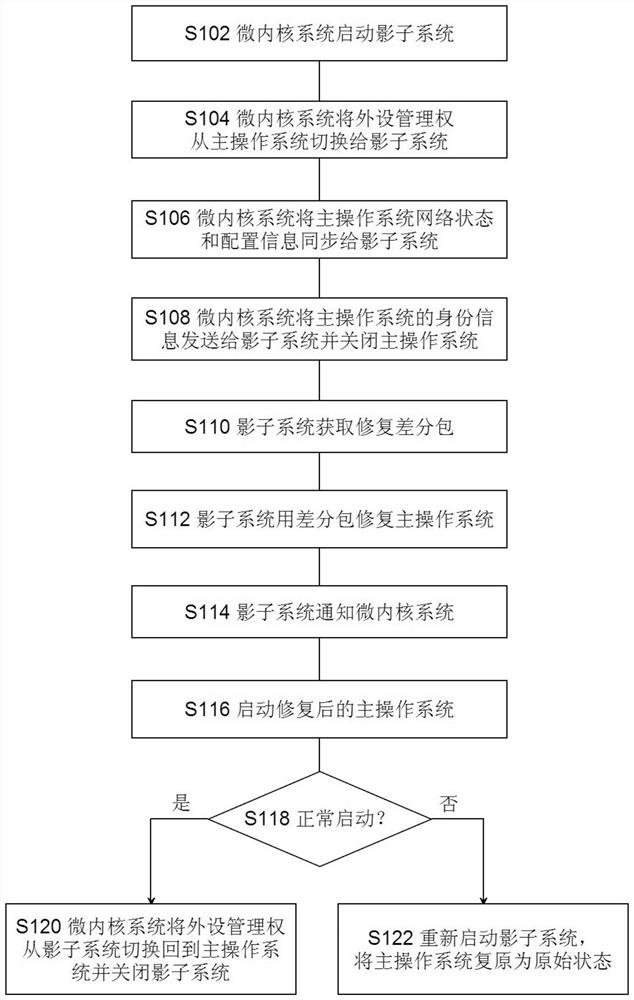
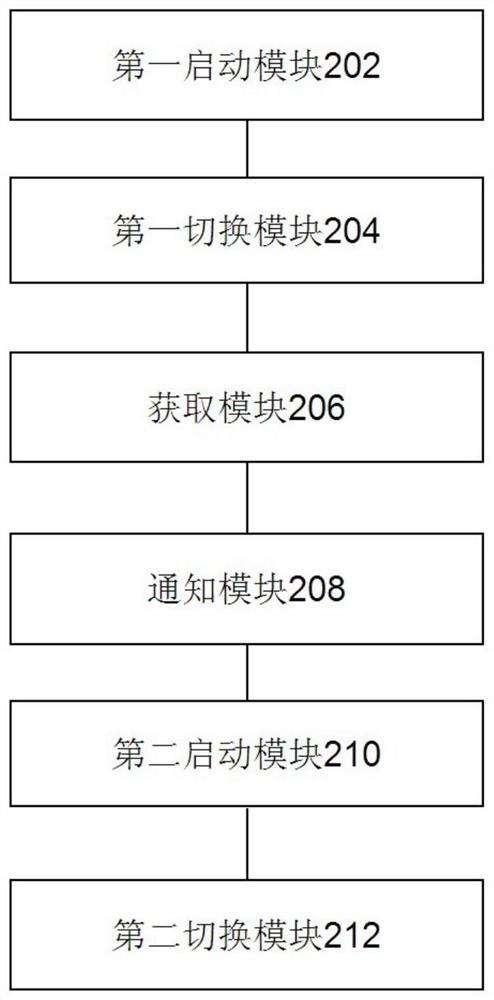
Operating system repairing method and system, corresponding equipment and storage medium
InactiveCN111813595AGuaranteed continuous availabilityAvoid the possible risks of repairing yourselfRedundant operation error correctionComputer hardwareCore function
The invention discloses an operating system repairing method and system, corresponding equipment and a storage medium. According to the method, a shadow system is arranged in a terminal; the shadow system is provided with a terminal peripheral driving program and core applications such as a telephone and a short message. When the operating system is repaired, the microkernel enables the peripheralmanagement right to be smoothly switched between the main operating system and the shadow system, and the started shadow system is used for repairing the main operating system, so that the peripheralalways keeps normal work in the whole repairing process, and the core function of the terminal is ensured to be continuously available.
Owner:BEIJING YUANXIN SCI & TECH
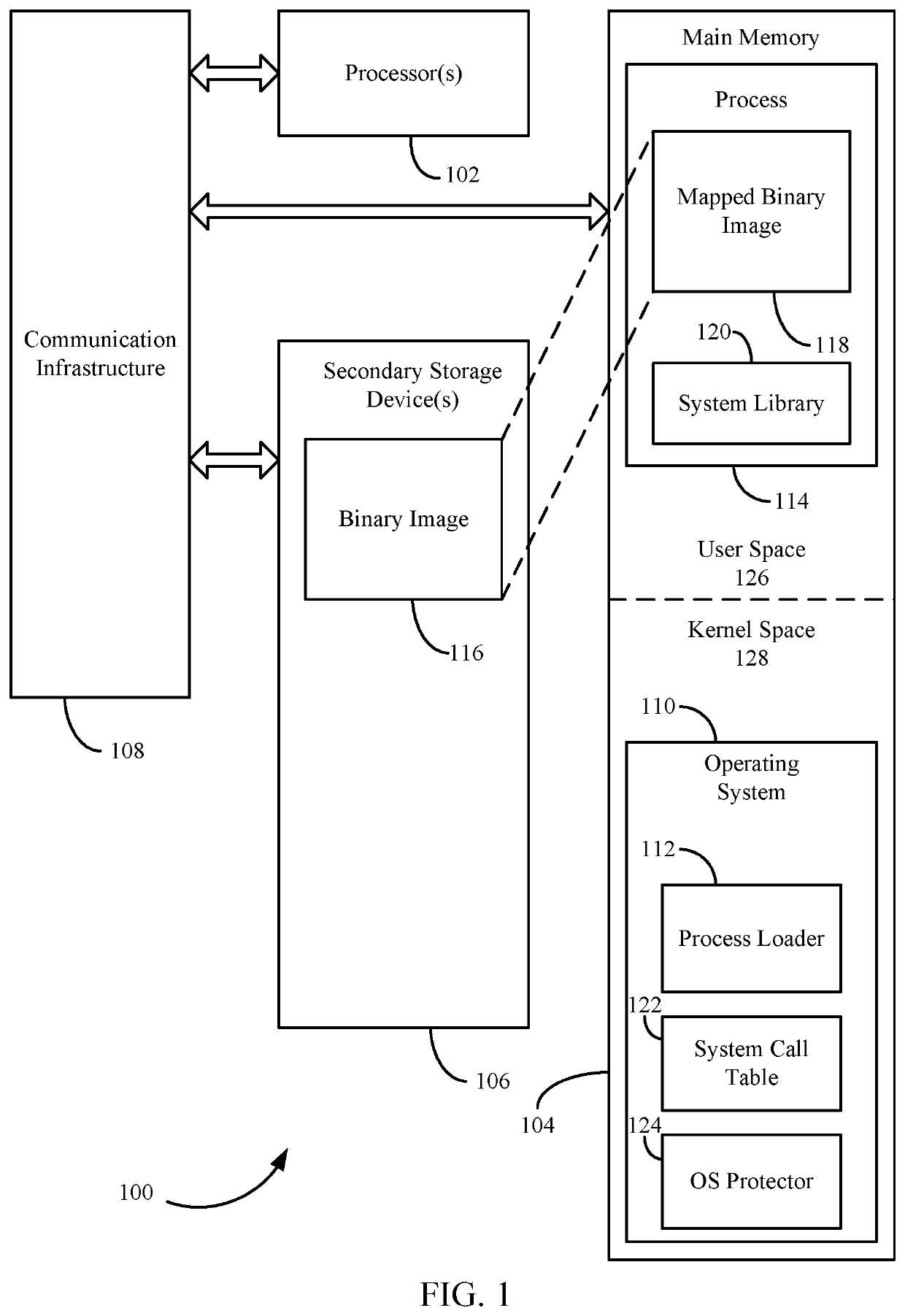
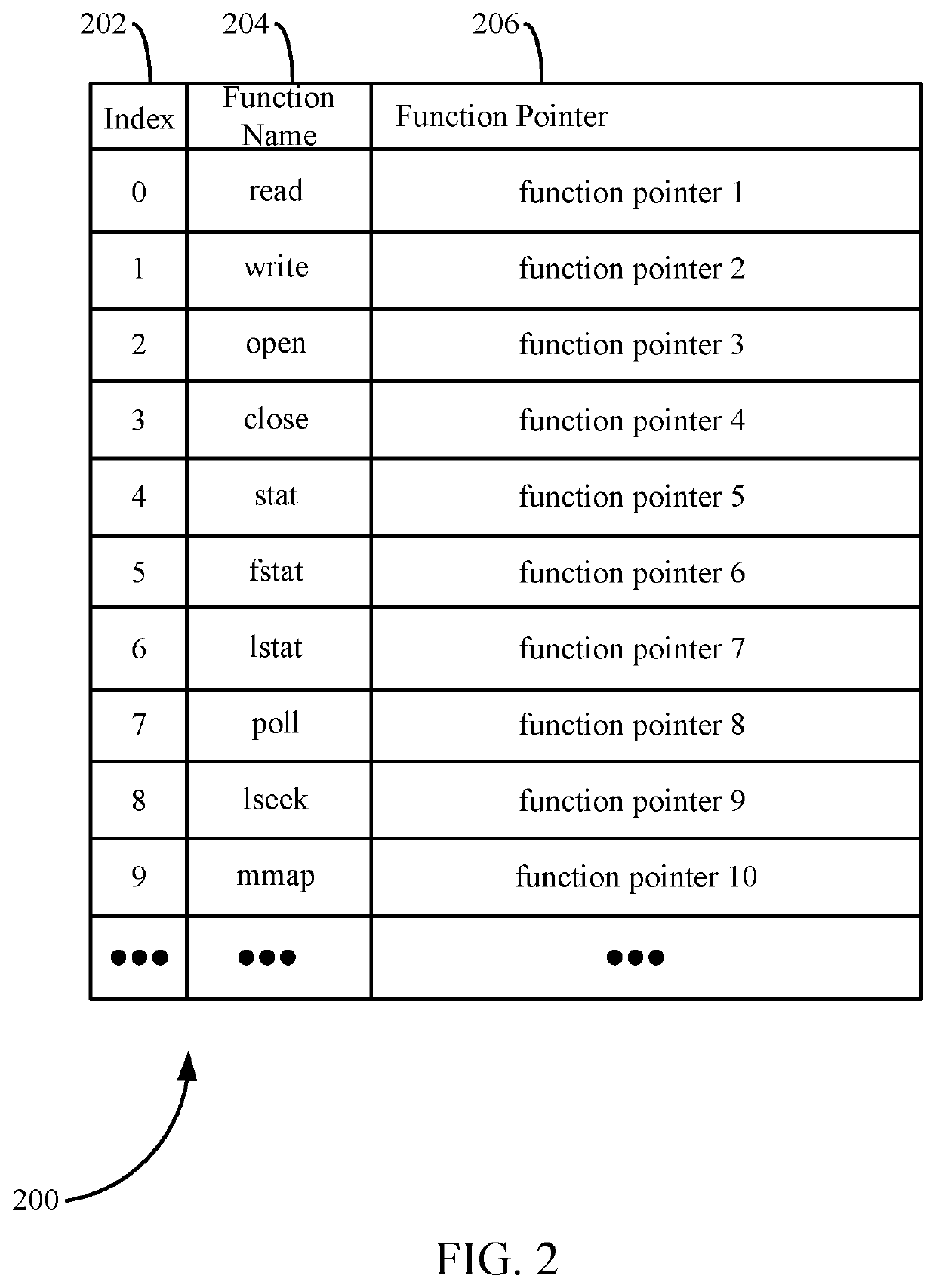
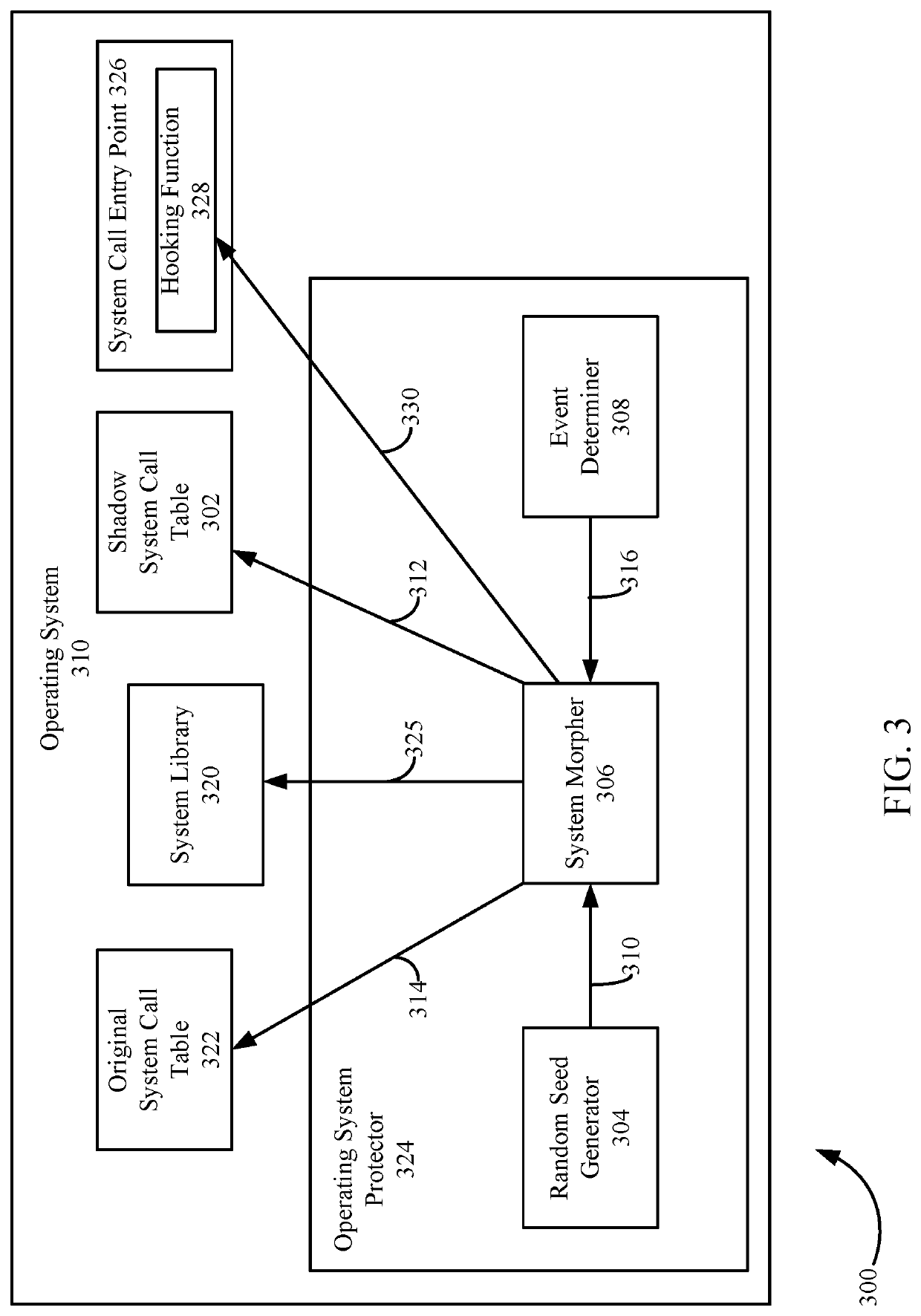
Malicious code protection for computer systems based on system call table modification and runtime application patching
Techniques are provided for neutralizing attacks by malicious code on a computer system. In an embodiment, this is achieved by modifying certain aspects of an operating system. For example, a system call table storing pointers to system functions is duplicated to create a shadow system call table. The original table is modified with traps resulting the neutralization of processes that access the table, whereas processes that access the shadow system call table are enabled to execute properly. In order for valid applications to operate with the shadow system call table, index numbers corresponding to the different system function calls are randomized in a system library that maintains function calls to such system functions. Valid applications may be patched in order to reference such randomized index numbers, whereas malicious processes continue to reference the original non-randomized index numbers.
Owner:MORPHISEC INFORMATION SECURITY 2014
Stencil mapped shadowing system utilizing GPU
InactiveUS20180308279A1Increase construction costsEliminate useImage renderingImage generationShadowingsResource utilization
Aspects comprise shadowing system as part of ray tracing. It is based on uniform grid of cells, and on local stencils in cells. The acceleration structures are abandoned along with high traversal and construction costs of these structures. The amount of intersection tests is cut down. The stencils are generated in the preprocessing stage and utilized in runtime. The relevant part of scene data, critical for shadowing of all visible intersection points in a cell, is registered in the local stencil map, as a volumetric data. The runtime use of stencils allows a complete locality at each cell, enhanced utilization of processing resources and load balancing of parallel processing.
Owner:BAKALASH REUVEN +1
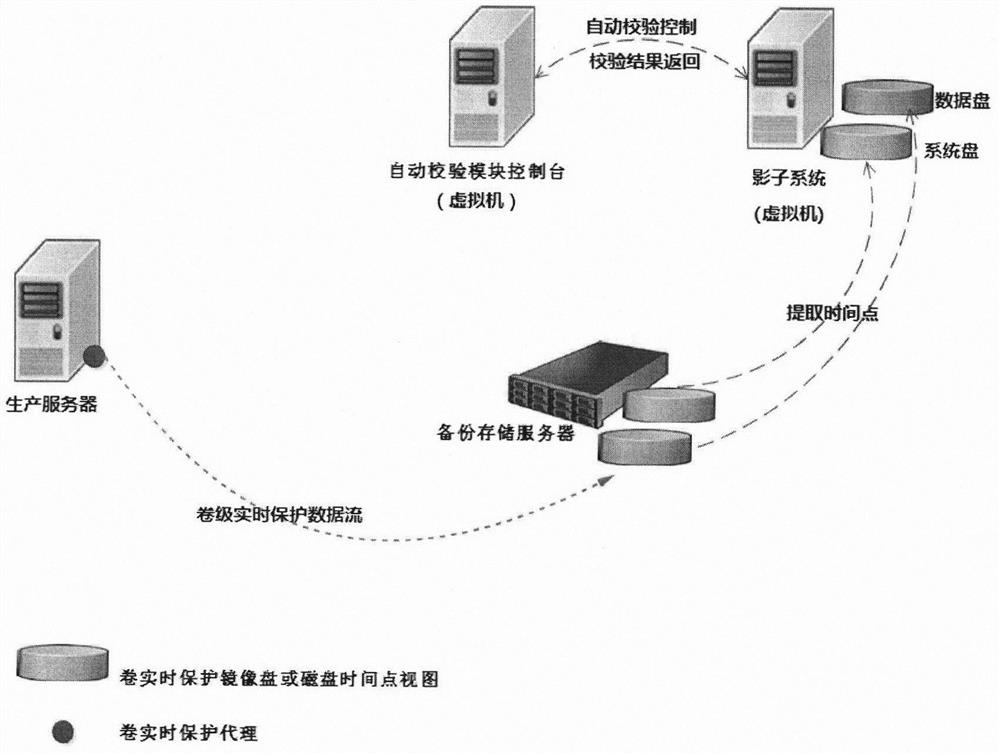
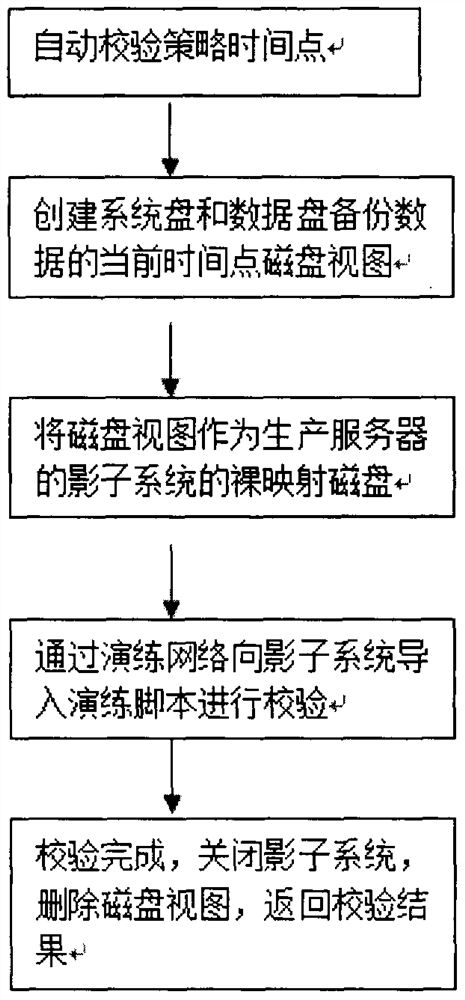
An automatic verification method for volume real-time protection data
ActiveCN108804248BLow technical requirementsReduce labor costsRedundant operation error correctionDatabase querySource Data Verification
Owner:航天壹进制(江苏)信息科技有限公司
Stencil mapped shadowing system
ActiveUS9633467B2Eliminate useIncrease construction costsResource allocationImage generationShadowingsResource utilization
Aspects comprise shadowing system as part of ray tracing. It is based on uniform grid of cells, and on local stencils in cells. The acceleration structures are abandoned along with high traversal and construction costs of these structures. The amount of intersection tests is cut down. The stencils are generated in the preprocessing stage and utilized in runtime. The relevant part of scene data, critical for shadowing of all visible intersection points in a cell, is registered in the local stencil map, as a volumetric data. The runtime use of stencils allows a complete locality at each cell, enhanced utilization of processing resources and load balancing of parallel processing.
Owner:SNAP INC
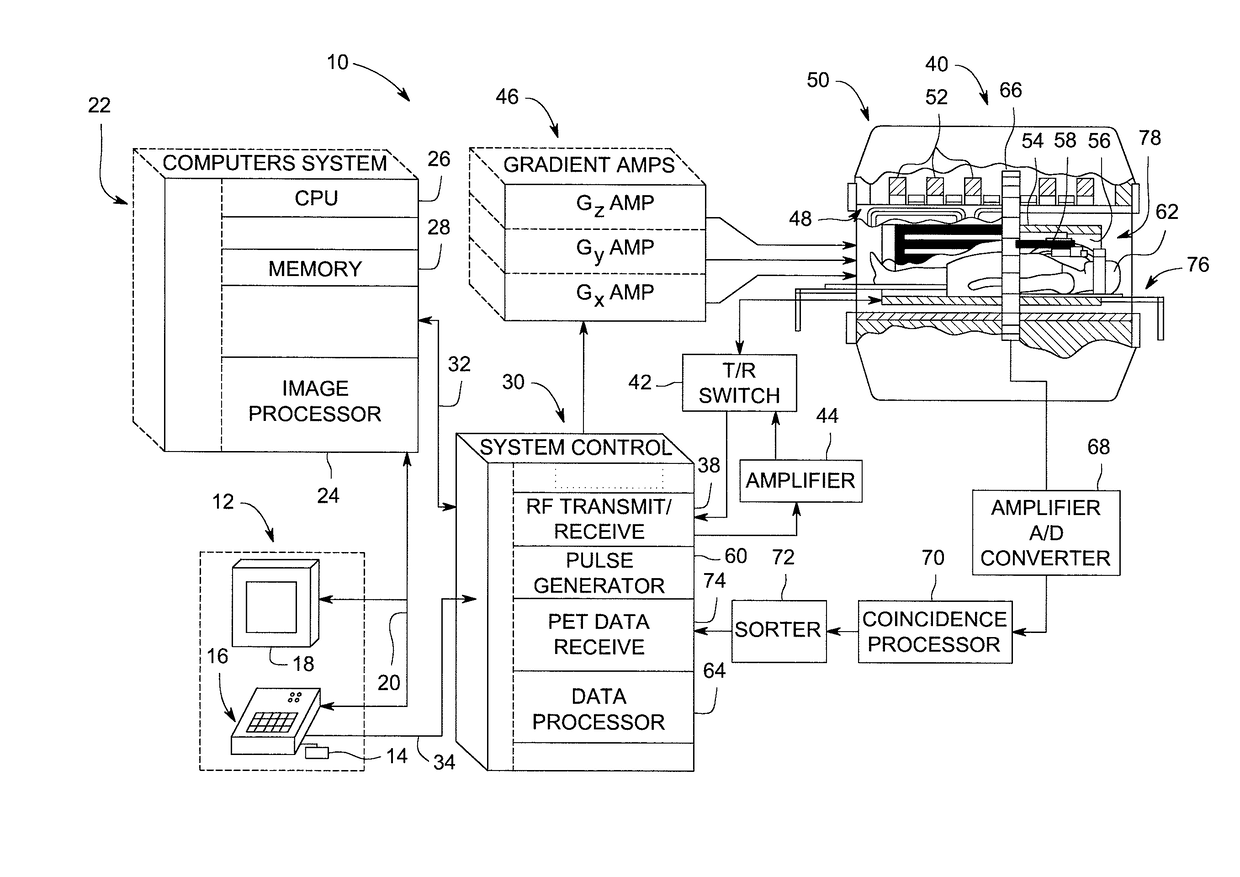
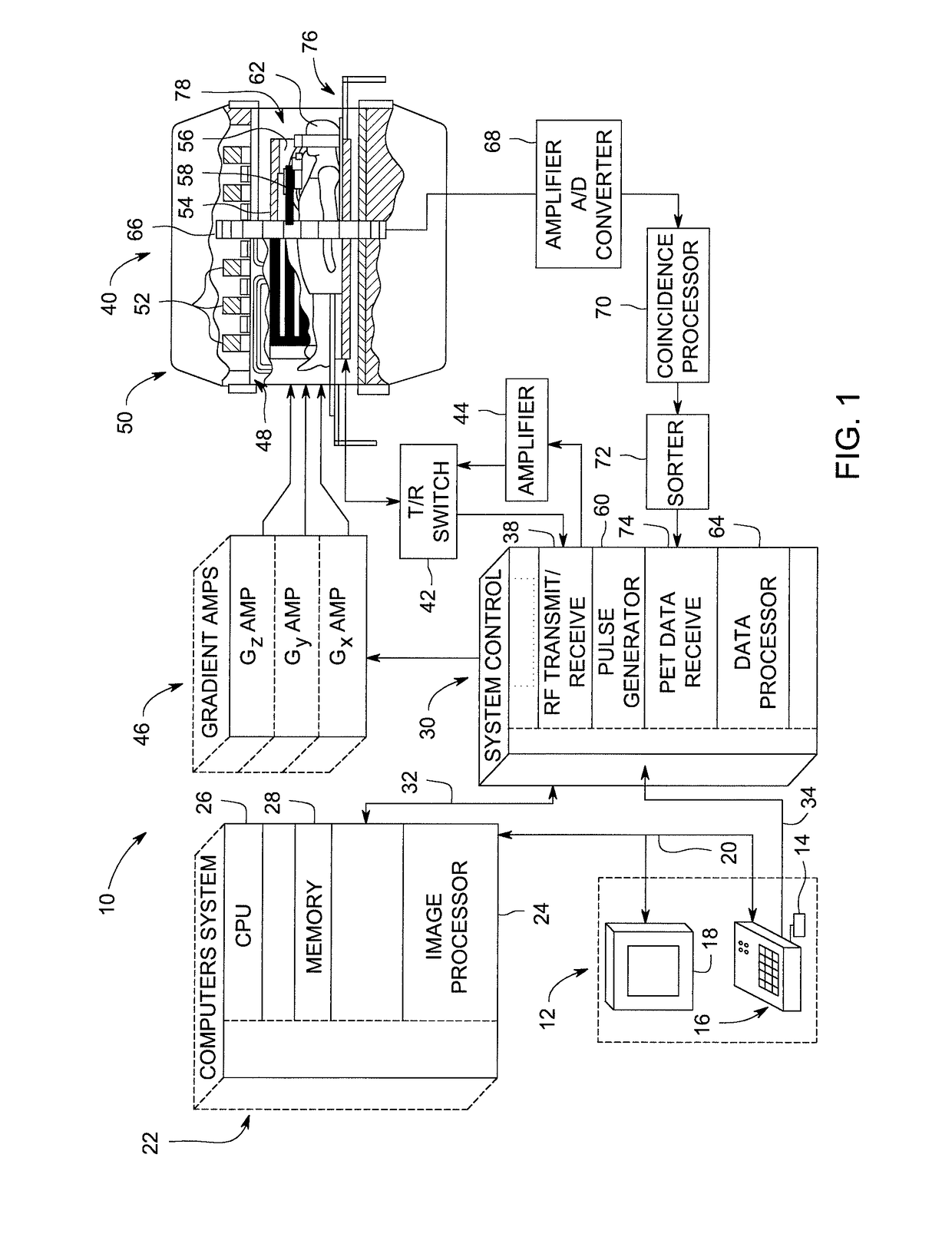
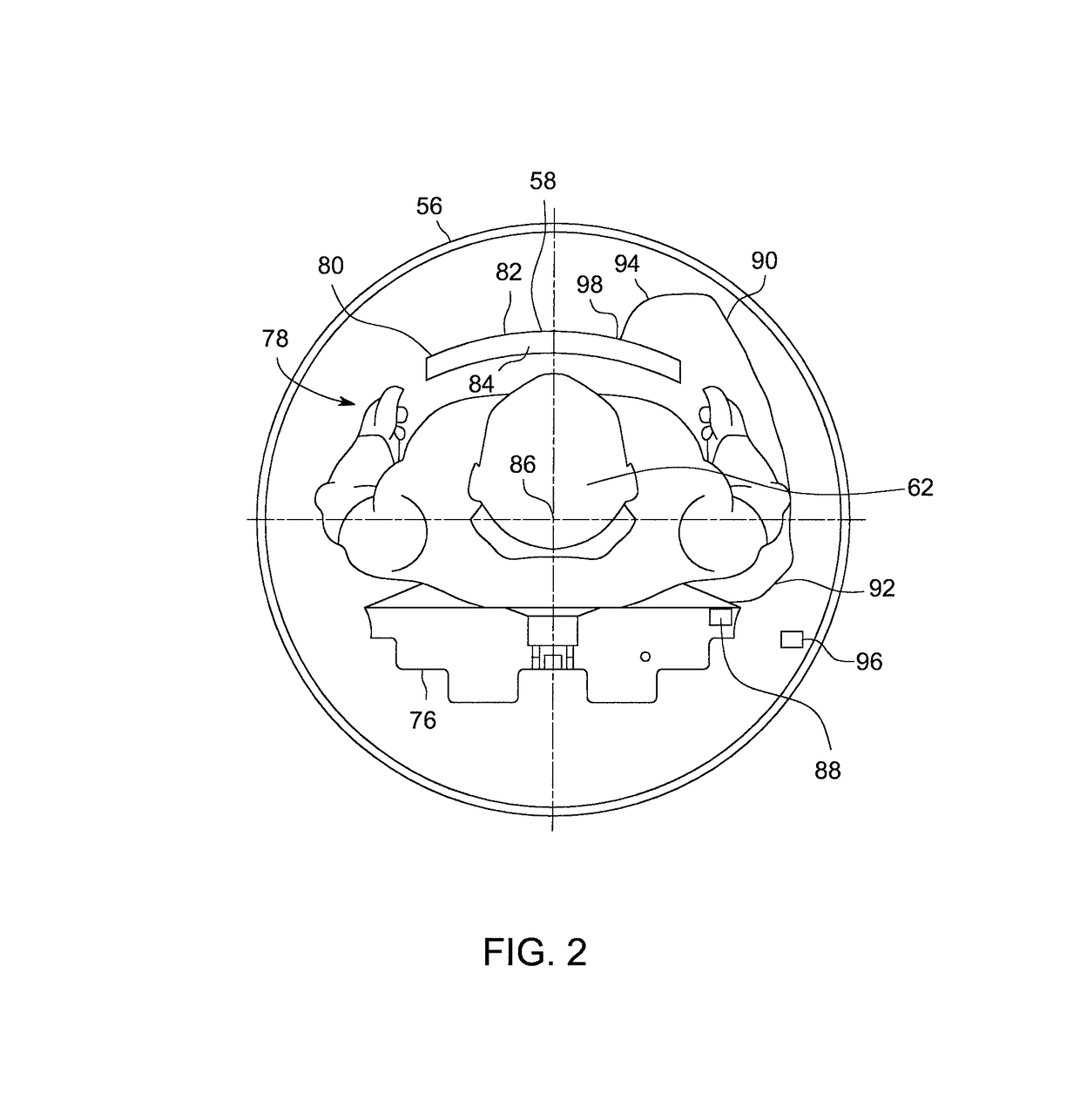
System and method for attenuation correction of a surface coil in a PET-MRI system
ActiveUS10132891B2Computerised tomographsMeasurements using NMR imaging systemsUltrasound attenuationSurface coil
A PET-MRI system for imaging an object is provided. The PET-MRI system includes a magnetic resonance imaging sub-system, a positron emission tomography sub-system, an optical sensor, and a data processing controller. The magnetic resonance imaging sub-system includes a surface coil that acquires magnetic resonance signals from the object. The positron emission tomography sub-system acquires PET emissions from the object. The optical sensor detects at least one of a spatial location and a shape of the surface coil. The data processing controller communicates with the magnetic resonance imaging sub-system, the positron emission tomography sub-system, and the optical sensor, and utilizes at least one of the detected spatial location and the detected shape of the surface coil to correct the acquired PET emissions for attenuation.
Owner:GENERAL ELECTRIC CO
Safety enhanced virtual machine communication method and virtual machine system
InactiveCN101800730BFlexible detectionInvestment protectionSecuring communicationPhysical securityShadow system
The invention discloses a safety enhanced virtual machine communication method and a virtual machine system. The safety enhanced virtual machine system according to one embodiment comprises a plurality of virtual machines positioned on a same physical machine in a virtual network. The virtual machine system comprises a virtual network safety manager coupled in the virtual network and a shadow system coupled with the virtual network safety manager, wherein the shadow system is positioned on the other physical machine different from the physical machine in which the virtual machines are positioned, the virtual network safety manager copied packets are sent among the virtual machines and the copied packets are forwarded to the shadow system through a physical safety device; the shadow system returns response information indicating the received packets to the virtual network safety manager; and the virtual network safety manager sends the packets among the virtual machines according to the returned response information.
Owner:IBM CN
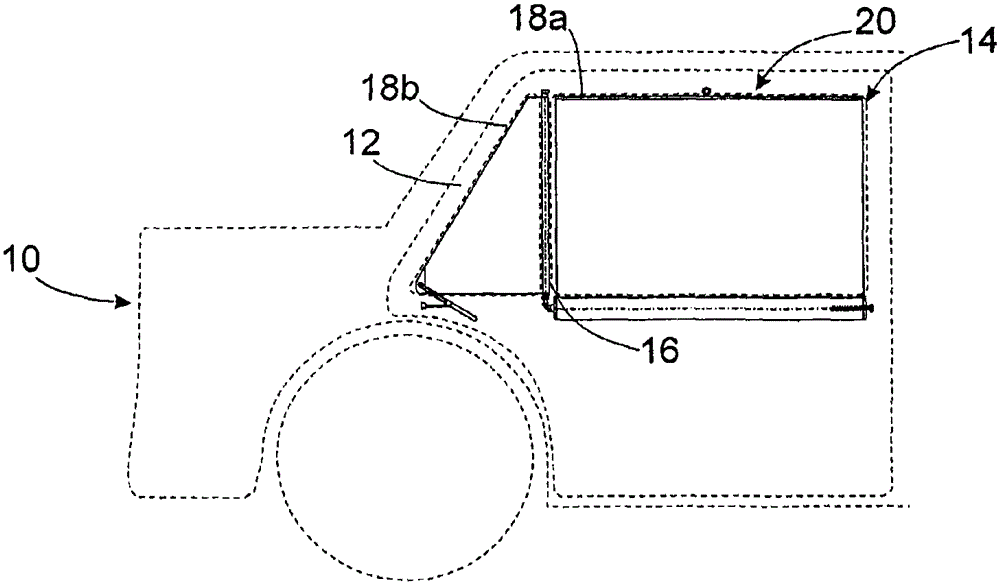
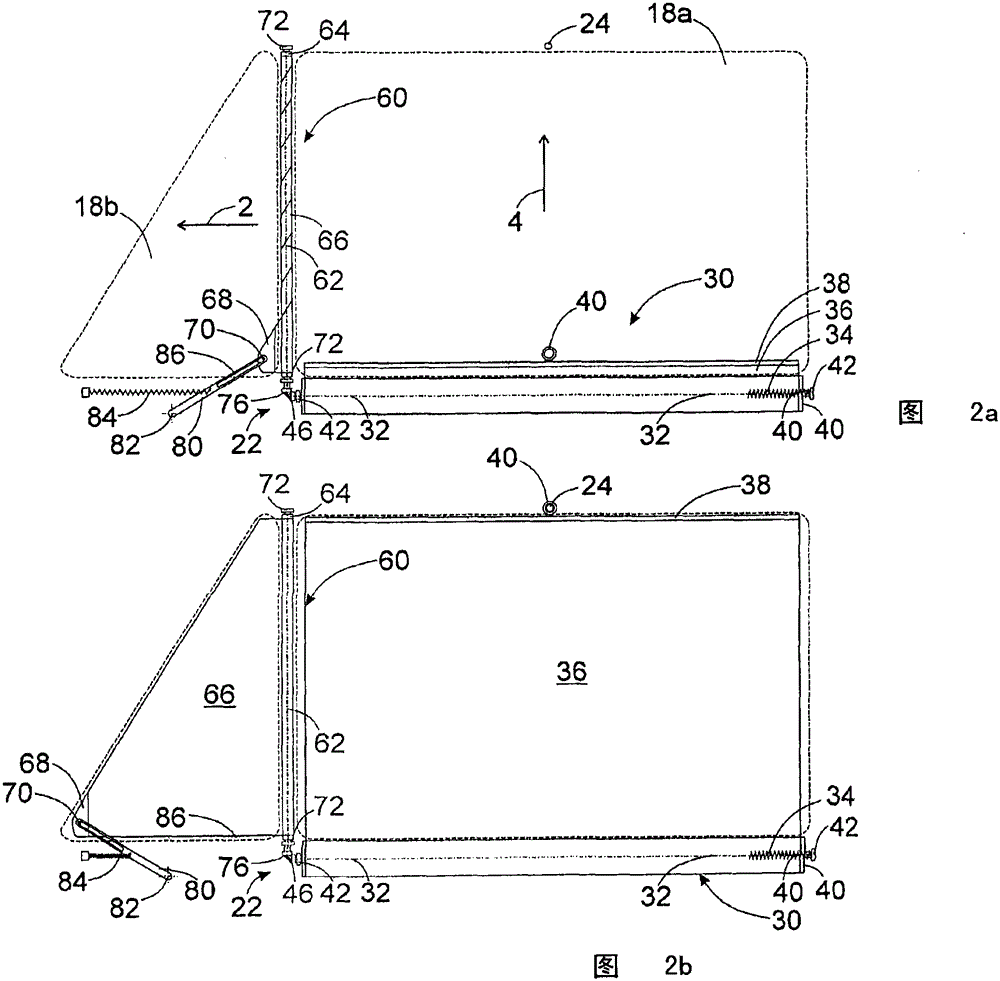
Shading system and roller unit therefor
Roller units are known for covering triangular windows of two-part side windows of vehicles, which have a flexible planar formation and a winding shaft rotatable about a vertical axis, wherein the planar formation is wound up in the stored state On the winding shaft, and in the functional state, it is unwound from the first winding shaft in a horizontal pull-out direction, and wherein a pull-out spring device is arranged, which acts on the distal end of the planar formation, and in the functional state The direction of causes a force loading on the planar structure. It is proposed that the pull-out spring device (80, 84) has a lever (80) pivotable about a pivot axis (82), which lever is loaded with a moment via the lever spring (84) for the pull-out direction (2) A force is applied to the planar structure ( 66 ), whose distal end ( 86 ) facing away from the pivot axis ( 82 ) is arranged on the distal end ( 68 , 70 ) of the planar structure ( 66 ). In particular, positively coupled roller units are used for the screening system.
Owner:BOS AUTOMOTIVE SYST (TAICANG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com