Network security protection method and system
A network security and network technology, applied in the field of network security, can solve problems such as poor network security protection effect, inability to configure protection resources, and inability to achieve protection effects, and achieve good protection effects and safe use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
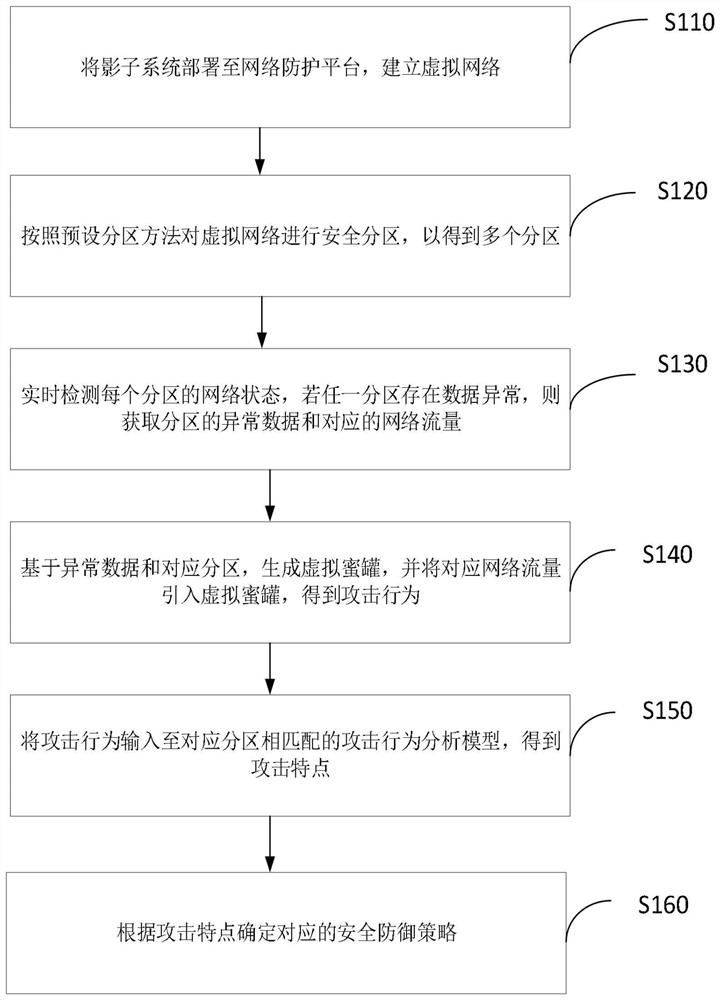
[0037] Please refer to figure 1 , figure 1 A flow chart of a network security method according to an embodiment of the present application is shown. A network security method is applied to a network protection platform, which includes the following steps:
[0038] S110: Deploy the shadow system to the network protection platform to establish a virtual network;
[0039] Among them, the shadow system is to isolate the Windows operating system while creating a virtual imaging system as the real operating system. After entering the shadow system, all operations are virtual, all viruses and rogue software are unable to infect the real operating system.
[0040] Specifically, a virtual network that deploys shadow systems to a network protection platform can effectively protect the use of real operating systems.
[0041] S120: Safety partitions for virtual networks in accordance with the preset partition method to get multiple partitions;
[0042] Specifically, on the basis of the virtua...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com