Safety enhanced virtual machine communication method and virtual machine system
A communication method and virtual machine technology, applied in the direction of secure communication devices, transmission systems, digital transmission systems, etc., can solve the problems of VM1 infection and no security protection mechanism, and achieve the effect of reducing costs and protecting investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
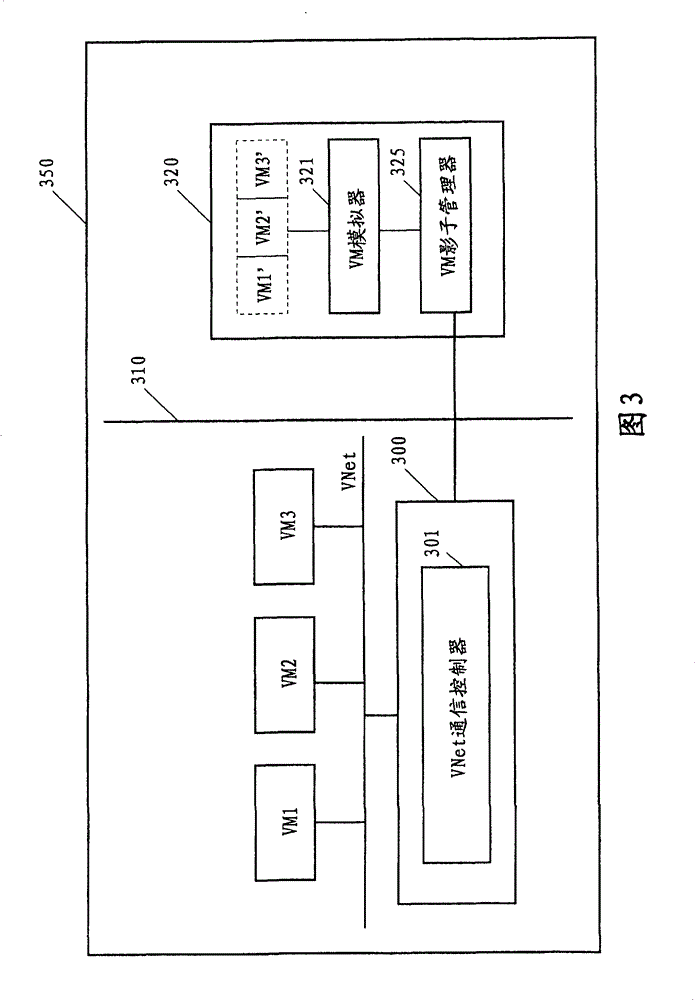
[0030] image 3 A schematic block diagram of a security-enhanced virtual machine system according to this embodiment is shown.
[0031] As shown in the figure, the virtual machine system 350 according to this embodiment includes multiple virtual machines, such as VM1, VM2 and VM3. Please note that although this embodiment uses three virtual machines as an example for illustration, those skilled in the art can understand that this is only for convenience of explanation, not limitation. You can actually include as many virtual machines as you want. In this embodiment, these virtual machines are located on the same physical machine (such as server, mainframe, workstation, etc.).
[0032] The virtual machine system 350 also includes a virtual network (VNet) security manager 300 and a VM shadow system 320 coupled thereto. The VM shadow system 320 is located on another physical machine different from the physical machine where the virtual machines VM1, VM2, and VM3 are located. ...
Embodiment 2
[0045] Figure 4 It is a schematic block diagram showing a security-enhanced virtual machine system according to another embodiment of the present invention. exist Figure 4 , using the same notation as the image 3 The same device, and its detailed description is omitted.
[0046] The difference between the virtual machine system 350' of this embodiment and the virtual machine system 350 of Embodiment 1 is that the VNet security manager 300' also includes a VNet division controller 305.
[0047] The VNet partition controller 305 is coupled to the VNet communication controller 301 . If the VNet communication controller 301 does not receive the response information returned from the VM shadow system 320 within the specified time, it will notify the VNet division controller 305 to adjust the VNet. The VNet division controller 305 adjusts the VNet to divide the virtual machine VM3 sending packets into a virtual subnetwork (not shown) separate from other virtual machines, and ...
Embodiment 3
[0050] Figure 5 A flowchart showing a security-enhanced virtual machine communication method according to yet another embodiment of the present invention.
[0051] The virtual machine communication method according to this embodiment can be implemented on the virtual machine system described in Embodiment 1. Such as Figure 5 As shown, firstly, at step 501, the VNet communication controller detects, for example, a packet sent from a virtual machine VM3 located on the same physical machine to VM1.
[0052] Then, at step 510, the detected packet is maintained in shared memory and the packet is copied.
[0053] Next, at step 520, the retained package may be tagged with a universally unique identifier UUID.
[0054] Then, at step 530, the copied packet and UUID are forwarded to the VM shadow system through, for example, a firewall. The shadow system is located on another physical machine than the physical machine where the virtual machine is located.
[0055] Afterwards, in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com