System exception capturing method, main system, shadow system and intelligent equipment
A main system and shadow technology, applied in the field of system exception capture and intelligent equipment, can solve problems such as unable to capture valid information, PCI bus hangs, other tasks cannot be scheduled, etc., to achieve the effect of enhancing maintainability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
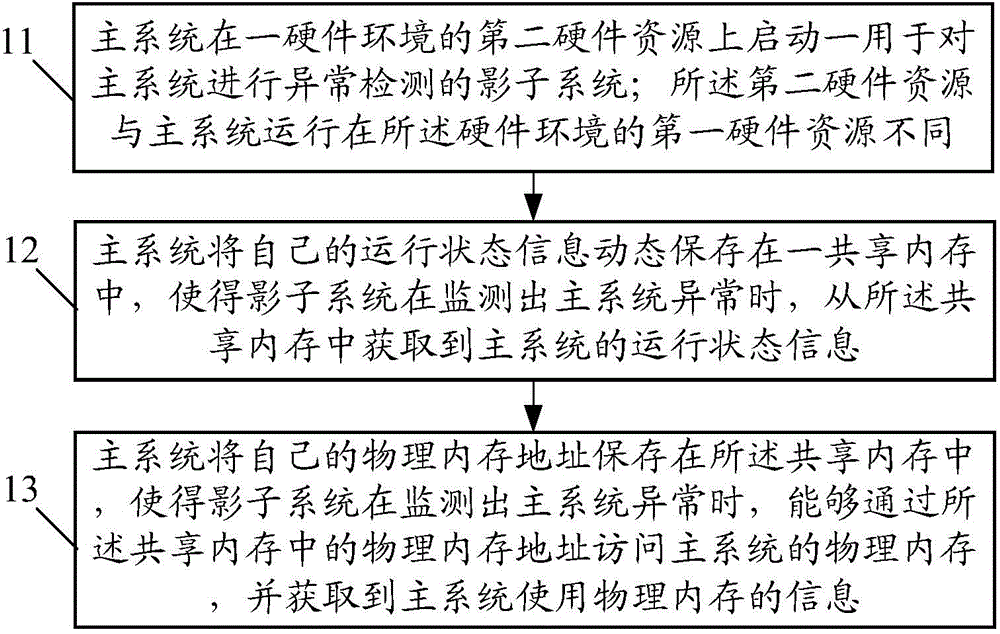
Examples
Embodiment 1
[0118] Step A11, the shadow system detects and reads the physical CPU information used by the main system from the shared memory. The physical CPU information is saved in the shared memory by the main system.
[0119] Step A12, the shadow system stops running by sending interrupt requests to all CPUs used by the main system.
[0120] Step A13, if the main system can still respond to the interrupt request at this time, the main system stops running, stops accessing the memory, and synchronizes the states among the CPUs. Wherein, if the main system cannot respond to the interrupt request at this time (has hung up), then skip this step.
[0121] Step A14, the shadow system reads the physical memory address previously saved by the main system from the shared memory.
[0122] Step A15, the shadow system uses the physical memory address of the main system as a startup parameter of the query kernel, and then loads the query kernel. This way, the shadow system can access the physic...
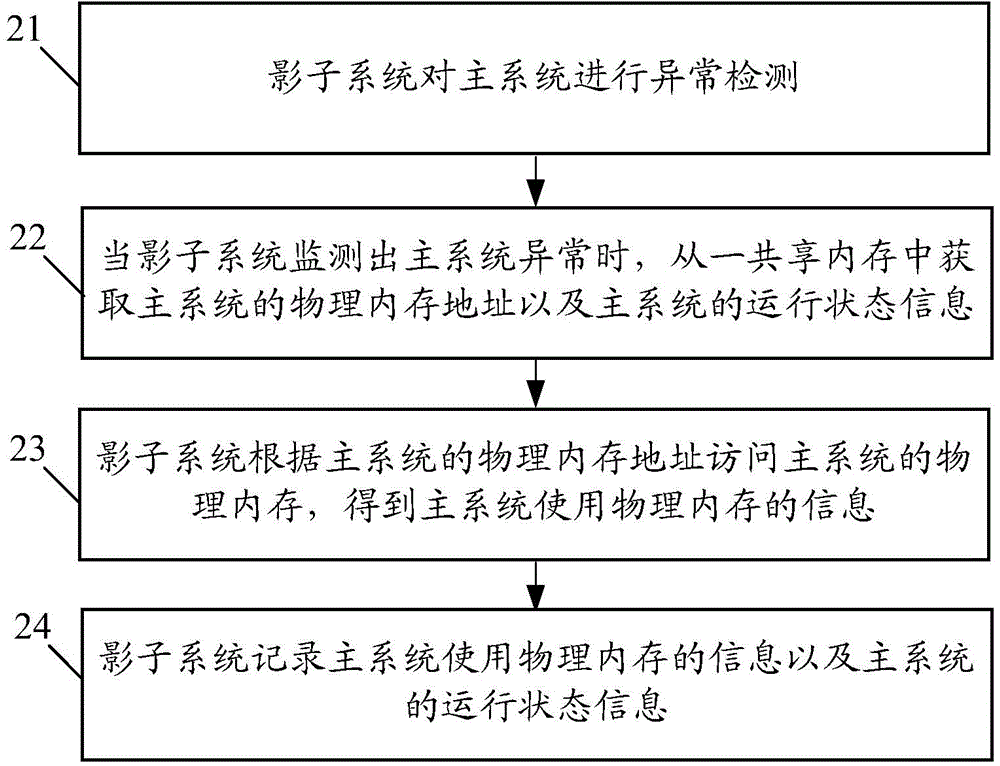
Embodiment 2
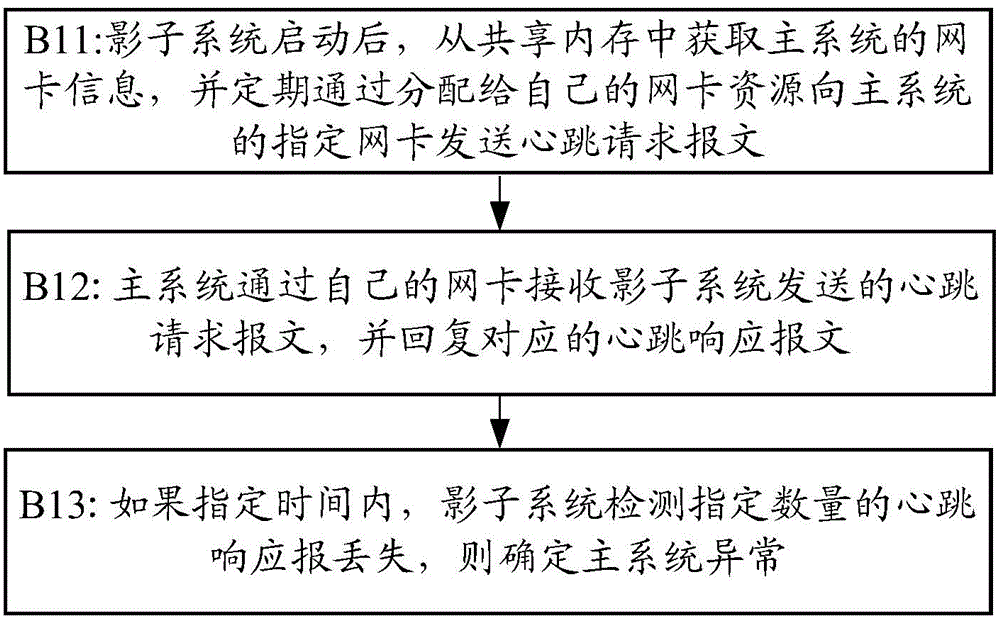
[0131] In the second embodiment, the shadow system performs anomaly monitoring according to the status of network card resources occupied by the main system, specifically including: image 3 Steps shown:
[0132] Step B11, after the shadow system is started, it obtains the network card information of the main system from the shared memory, and periodically sends a heartbeat request message to the designated network card of the main system through the network card resources allocated to itself. Due to the same hardware environment, if the main system has network card resources, then the shadow system can also be allocated network card resources.
[0133] Step B12, the main system receives the heartbeat request message sent by the shadow system through its own network card, and replies with a corresponding heartbeat response message.
[0134] Step B13, if the shadow system detects that a specified number of heartbeat responses are lost within a specified time, then it is determ...
Embodiment 3
[0136] In the third embodiment, the shadow system performs abnormal capture on the CPU resources occupied by the main system, specifically including: Figure 4 Steps shown:
[0137] In step C11, after the shadow system is started, the CPU resource information used by the main system is read from the shared memory.
[0138] Step C12, the shadow system periodically sends an inter-core interrupt to the CPU used by the main system as a heartbeat request message; this step is applicable to a multi-core CPU chip, and the shadow system and the main system can run on different CPUs.
[0139] Step C13: After receiving the inter-core interrupt from the shadow system through the shared memory, the main system replies to the CPU used by the shadow system with an inter-core interrupt response, that is, a heartbeat response message. It should be noted that after the CPU processes the received core information, it will continue to run normally, and the interrupt processing is very fast, whi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com