Attack protection method and system
A protection system and statistical table technology, applied in the transmission system, electrical components, etc., can solve the problem that the number of top posts cannot be limited, and achieve the effect of improving experience and improving operation response
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
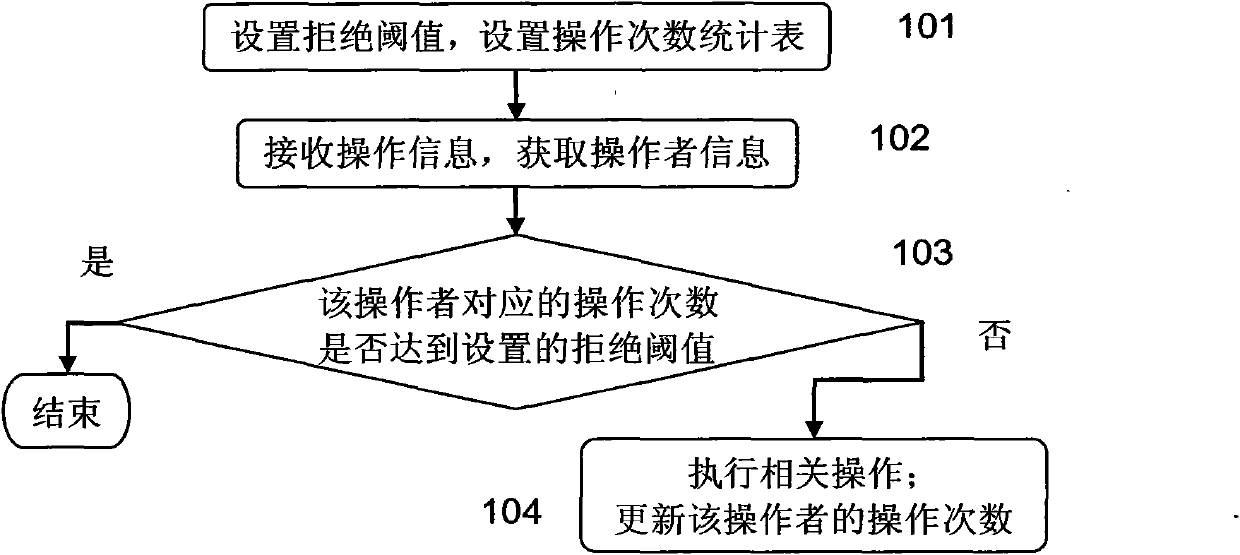
[0058] Such as figure 1 Shown is the flow chart of the first embodiment of the present invention, in this embodiment:
[0059] Firstly, in step 101, a rejection threshold is set, and an operation count table is set to record the operator's operation count.
[0060] Here, the rejection threshold can be set separately according to different operators; or only one common rejection threshold can be set for all operators. To simplify the description, in this embodiment, the rejection threshold is set for all operators.
[0061] Here, the operation times statistics table includes an operator field and an operation times field, as shown in Table 1.
[0062] According to different applications, the setting method of the number of operations statistics table may be different. For example, for the prevention and control of the problem of top posting irrigation in the website community, the setting operation count table can add a statistical field in the netizen registration data tabl...
no. 1 example
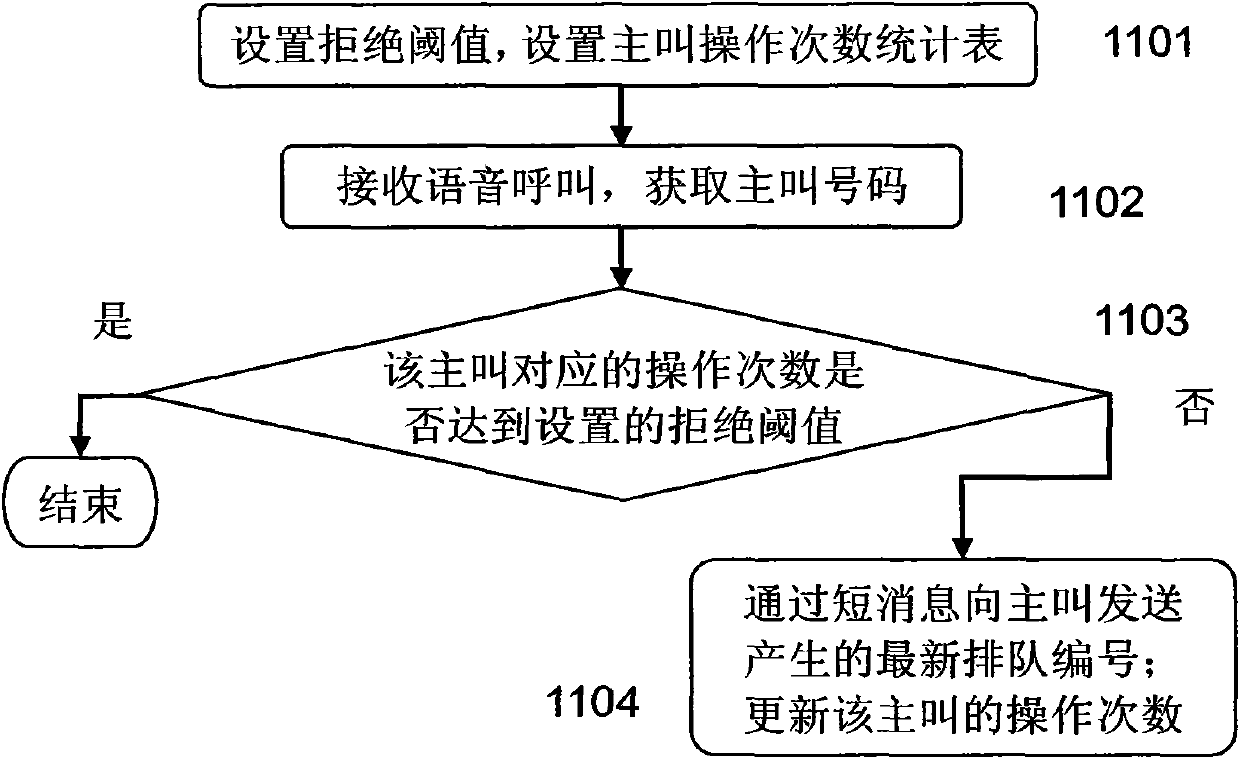
[0080] Such as Figure 1A Shown is the flowchart of the first embodiment of the first embodiment of the present invention, in this embodiment:
[0081] Firstly, in step 1101, a rejection threshold is set, and a statistical table of calling operation times is set, as shown in Table 2.
[0082] Step 1102, receiving a voice call, and obtaining a calling number.
[0083] Step 1103, according to the calling number and the calling number statistics table, judge whether the number of operations corresponding to the calling party reaches the set rejection threshold, if yes, end the process; otherwise, execute step 1104.
[0084] Here, according to the calling number, the corresponding record is searched from the statistics table of the number of calling operations. If found, the number of operations corresponding to the calling can be obtained; if not found, the corresponding operation of the calling The number of times is 0, that is, no queue number has been applied for.
[0085] ...
no. 2 example
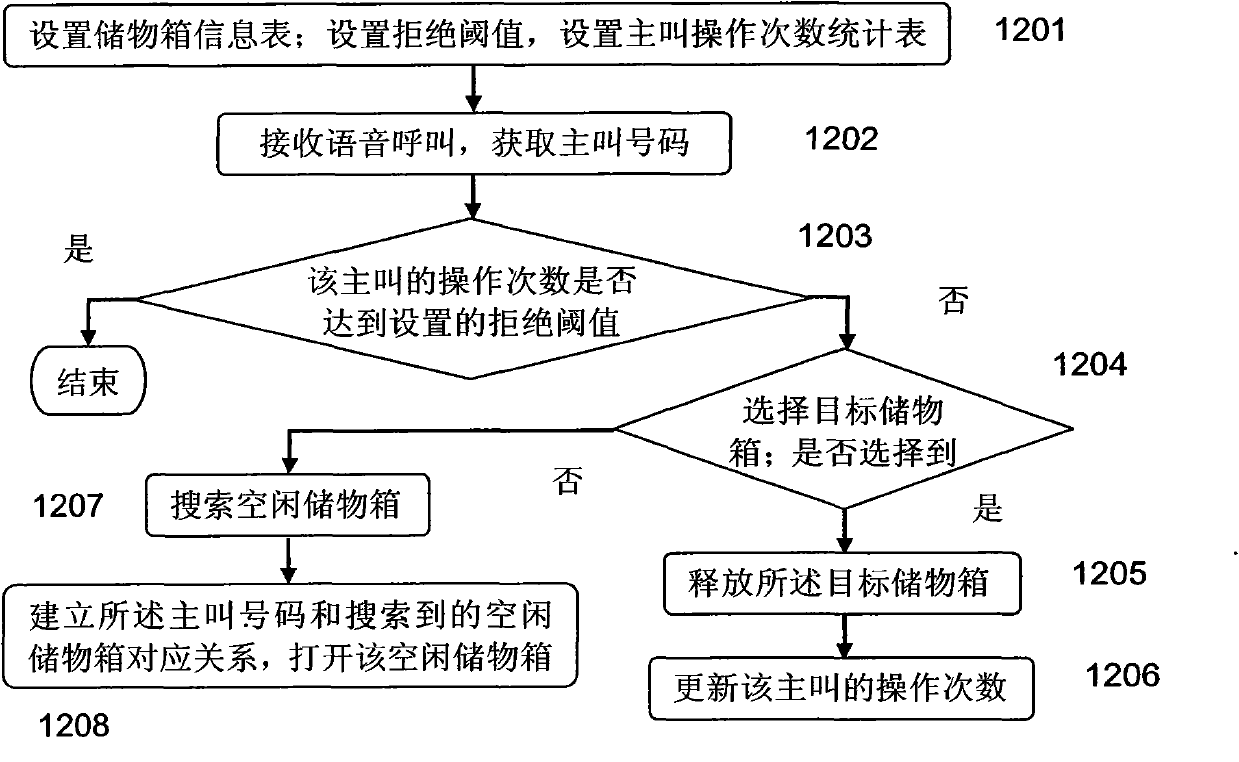
[0093] Such as Figure 1B Shown is the flowchart of the second embodiment of the first embodiment of the present invention, in this embodiment:
[0094] First in step 1201, set the storage box information table, as shown in Table 3, establish the corresponding relationship between the communication number and the storage box through this table; set the rejection threshold, and set the statistics table of calling operation times, as shown in Table 2.
[0095] Step 1202, receive a voice call, and obtain a calling number.
[0096] Step 1203, according to the calling number and the calling number of operations statistics table, judge whether the number of operations of the calling party reaches the set rejection threshold, if yes, end the process; otherwise, execute step 1204.
[0097] Here, according to the calling number, the corresponding record is searched from the statistics table of the number of calling operations. If found, the number of operations corresponding to the ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com