Data security access method in cloud computing environment
A cloud computing environment and data security technology, applied in the computer field, can solve problems such as data integrity and confidentiality threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
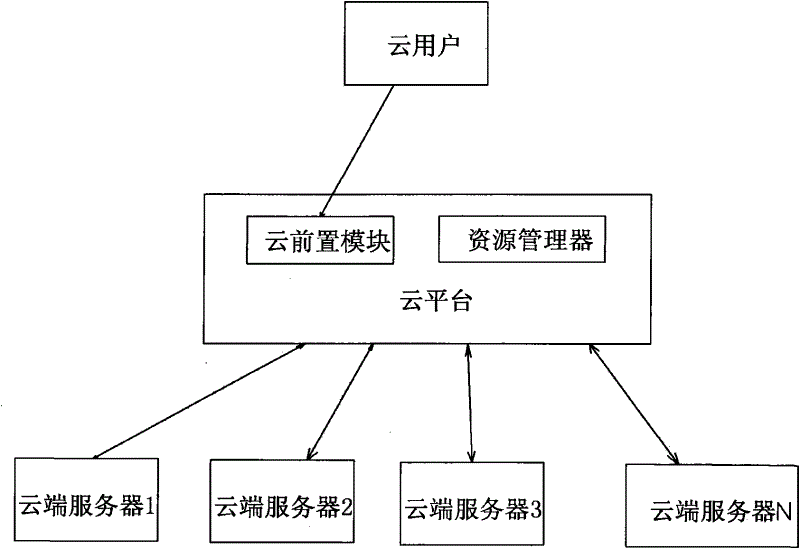
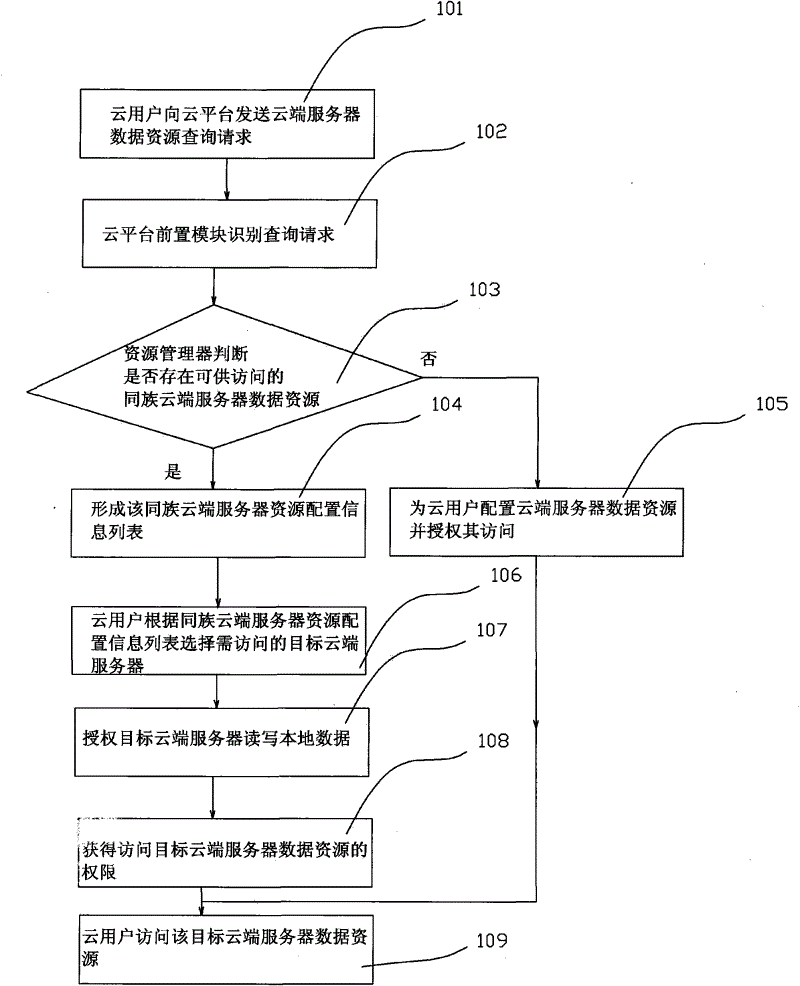
[0016] refer to figure 1 , is the cloud computing architecture of the solution of the present invention. On the whole, it includes three parts, namely cloud user (or cloud query terminal), cloud platform, and cloud server. Among them, a cloud user refers to a network requesting user or terminal for obtaining a certain computing service or data resource; a cloud platform is a central platform that provides centralized control and business management for a certain cloud computing service; a cloud server is a computer connected through the Internet , which is the constituent unit of various clouds. Regardless of whether it is a public cloud or a private cloud, it is a group of a large number of interconnected computers, and these computers can be personal computers or network servers. The figure only shows the architecture of the basic cloud environment, and specific applications may have other components. In addition, the cloud platform must have a front-end module and a reso...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap