Quantum key distribution system for resisting blinding attack
A technology of quantum key distribution and blinding attack, which is applied in key distribution, can solve problems such as pseudo-state attack and time-shift attack, and achieve the effect of resisting blinding attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
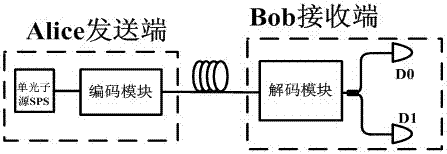
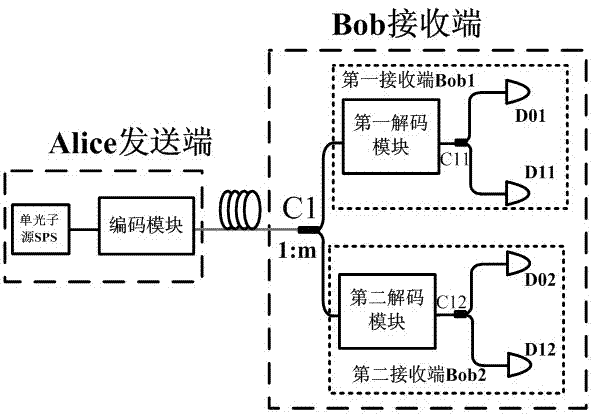
[0023] Such as figure 2 As shown, a quantum key distribution system against blinding attacks includes an Alice sending end and a Bob receiving end. The Alice sending end includes a single photon source SPS and an encoding module that generates photons, and the photon information sent by the single photon source is passed through Coding module encoding; the Bob receiving end includes a unequal arm coupler C1, a first receiving end Bob1 and a second receiving end Bob2, and the encoded photons in the Alice sending end are respectively sent to the second receiving end through an unequal arm coupler C1 A receiving end Bob1 and a second receiving end Bob2. That is, the output end of the single photon source SPS is connected to the input end of the encoding module; the output end of the encoding module is connected to the input end of the unequal arm coupler C1, and an output end of the unequal arm coupler C1 is connected to the first receiving end Bob1 The input end is connected, ...
Embodiment 2
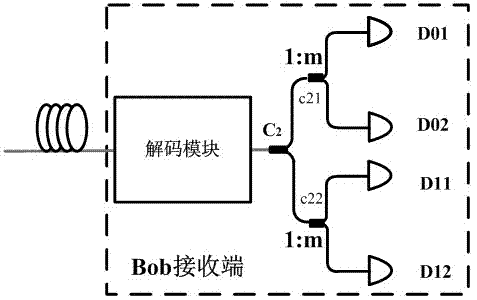
[0049] Such as image 3 As shown, a quantum key distribution system against blinding attacks includes a sending end and a receiving end, the sending end includes a single photon source and an encoding module that generates photons, and the photons emitted by the single photon source are encoded by the encoding module; The receiving end includes a decoding module, an equal ratio coupler C2, a first unequal arm coupler C21, a second unequal arm coupler C22, detectors D01, D11, D02, D12; the output end of the decoding module is coupled with an equal ratio The input end of the proportional coupler C2 is connected, and an output end of the proportional coupler C2 is connected with the input end of the first unequal arm coupler C21, and the other output end of the proportional coupler C2 is connected with the second unequal arm coupler C22. The input ends are connected, the first unequal arm coupler C21 is connected to the detectors D01 and D11 respectively; the second unequal arm c...
Embodiment 3
[0052] Such as Figure 4 As shown, a quantum key distribution system against blinding attacks includes a sending end and a receiving end. The sending end includes a single photon source that generates photons and an encoding module. The photons emitted by the single photon source are encoded by the encoding module; the receiving end includes The unequal arm coupler C3, the first decoding module, the second decoding module, the first delay line DL1, the second delay line DL2, the detector D0 and the detector D1, and the sending end uses the unequal arm coupler C3 to separate the photon information Send to the first decoding module and the second decoding module; the output end of the first decoding module is connected to the first delay line DL1 through the equi-arm coupler, and then connected to the detector D1; the output end of the second decoding module is connected through the equi-arm coupler The coupler is connected to the second delay line DL2, which in turn is connecte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com