Access control method and equipment
A technology of access control and access control strategy, which is applied in the field of network communication, can solve the problems of intercommunication and failure of site network C, and achieve the effect of access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
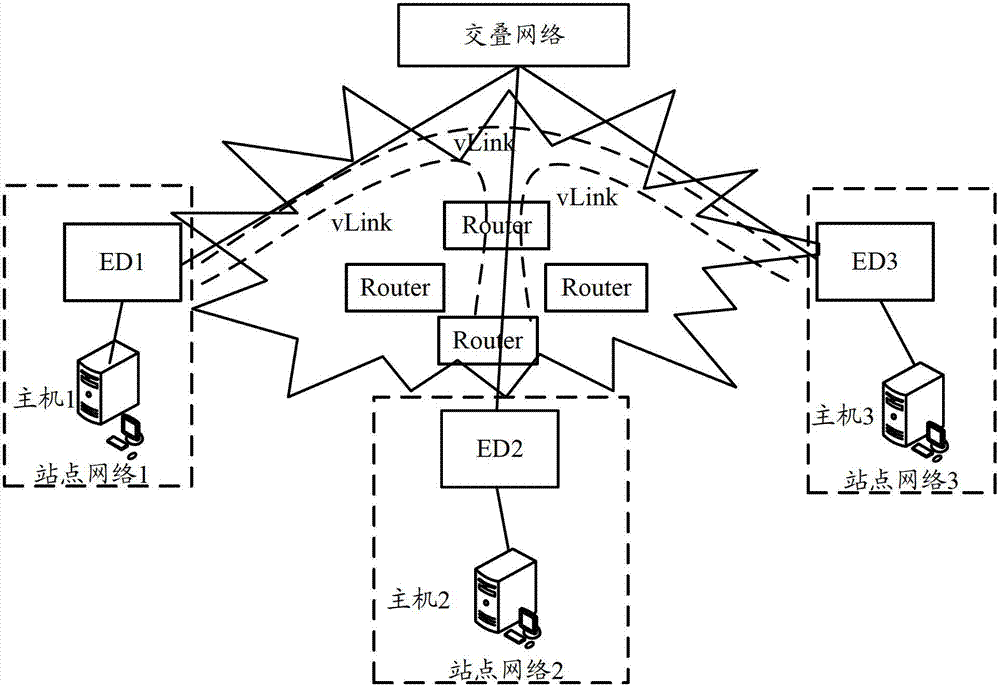
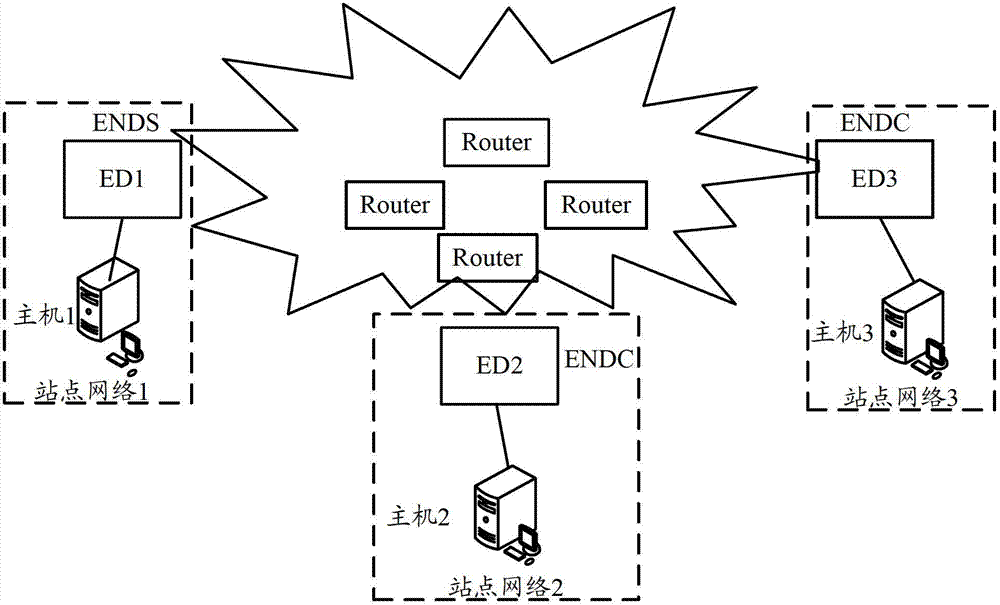
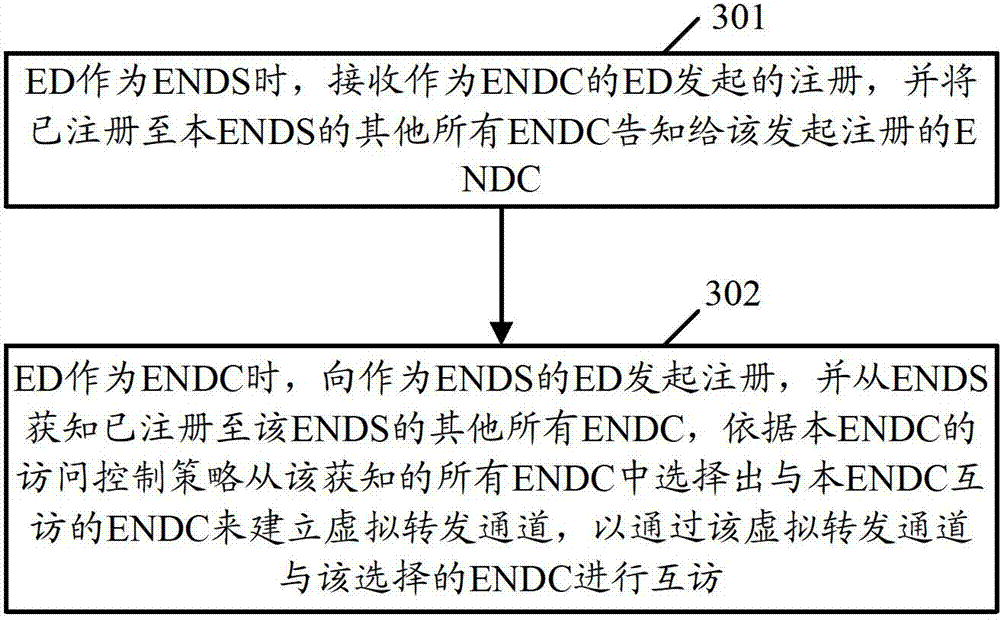
[0030] The method provided by the present invention is applied to the ED in the site network, for example, figure 1 Any ED shown from ED1 to ED3. Among them, in order to provide access control for specific data center networking requirements, the present invention needs to deploy the roles of EDs in each site network in the networking according to the actual application of the networking. Among them, the roles of EDs are mainly divided into two types: one is neighbor Discovery Server (ENDS), and the other is Neighbor Discovery Client (ENDC). In the networking, the number of ENDS is relatively small, generally 1 or 2, while the number of ENDCs is relatively large. figure 2 It shows the networking in which EDs in site network 1 serve as ENDS, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com