Method, device and browser for protecting webpage against malicious attack
A malicious attack, webpage technology, applied in the field of browsers, can solve problems such as webpage Trojan attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
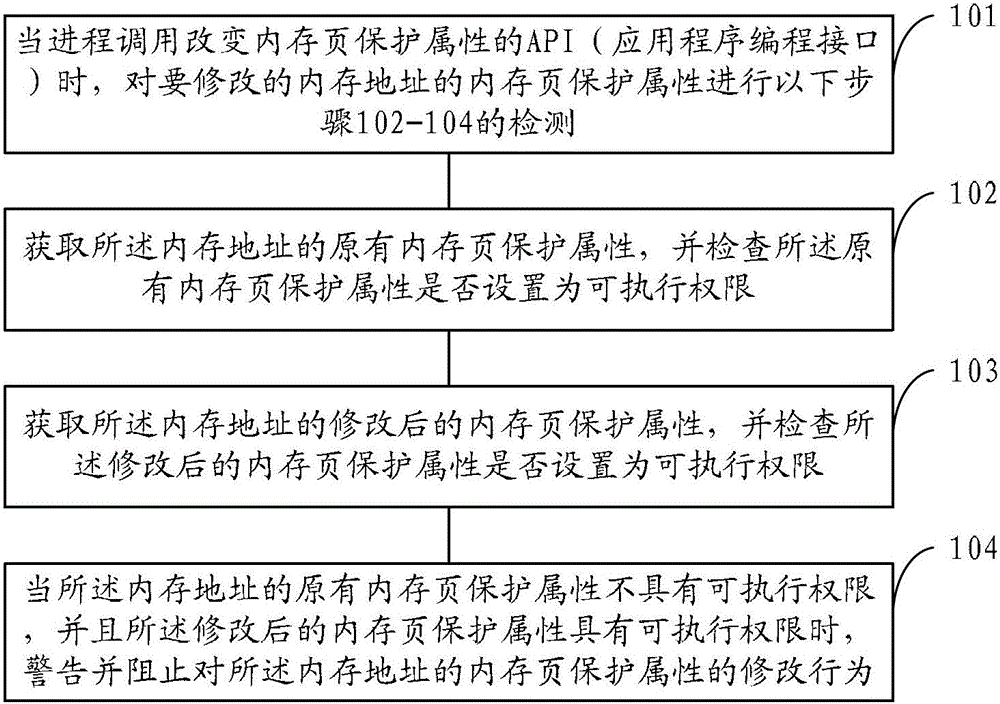
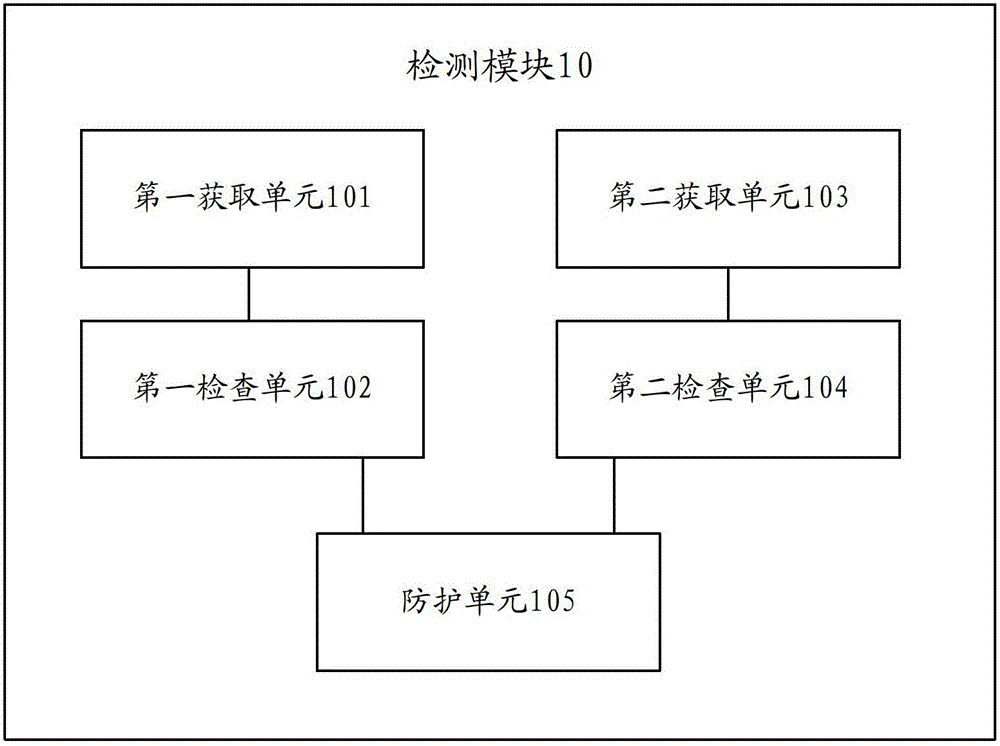
[0040] In order to solve the problem that attackers use ROP technology (return-oriented programming technology) to bypass DEP (Data Execution Protection) to carry out webpage Trojan horse attacks, the application first analyzes the process of using ROP technology to carry out malicious attacks, as follows.
[0041] As described in the prior art, DEP (Data Execution Protection) cannot completely and effectively protect the system security, and new attack methods are still emerging one after another. The attacker can modify the memory of the memory address where the malicious code shellcode is located through the ROP technology (Return Oriented Programming Technology) The page protection attribute enables d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com