Method and device for setting operation, administration and maintenance (OAM) security authentication
A technology of security authentication and identity authentication, which is applied in the field of OAM security authentication, can solve problems such as lack of security, protocol attacks, and failure to consider security, and achieve the effect of ensuring communication security and improving stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The technical solutions of the embodiments of the present invention will be clearly and completely described below in conjunction with the accompanying drawings of the present invention.
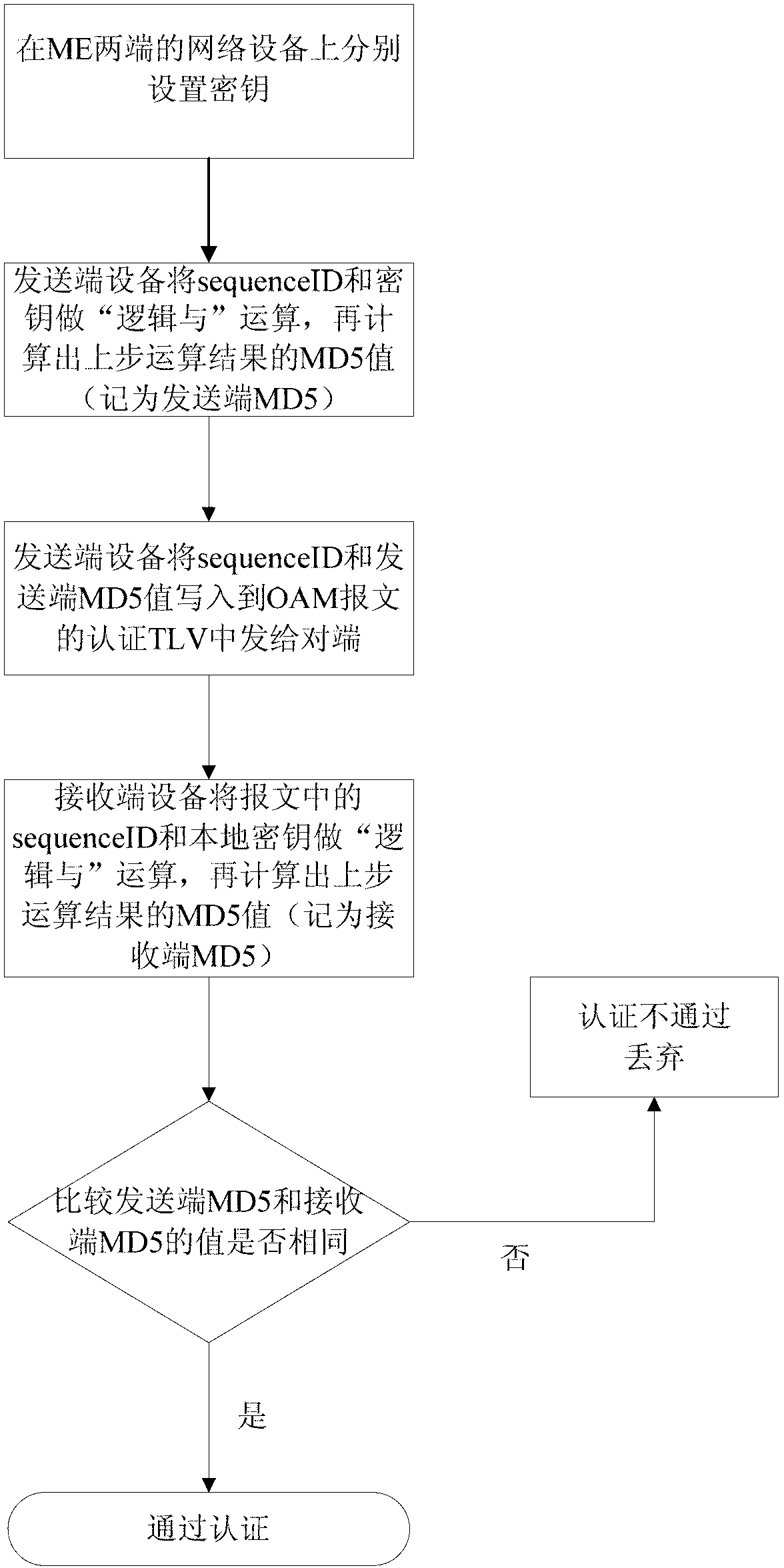
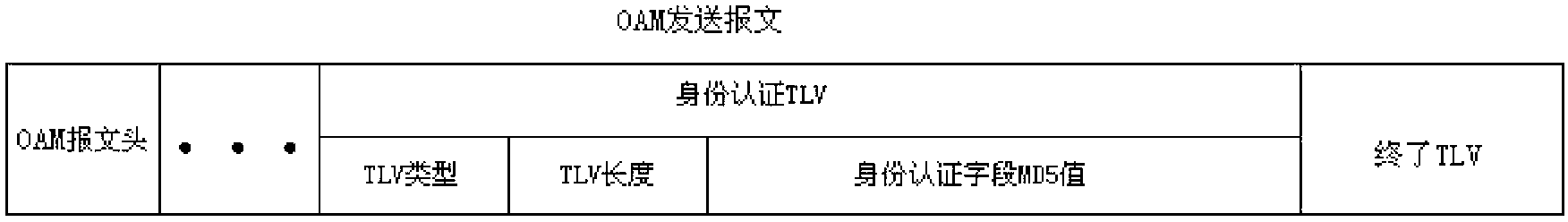
[0032] like figure 1 As shown, the method for setting OAM security authentication proposed by the present invention pre-defines a key for the network devices at both ends of the ME, and the key will not be transmitted in the network, but stored inside the device. Set an identity authentication TLV (Type Length Value) field in the OAM message sent by the network device at the ME end. The identity authentication TLV field includes an MD5 (Message-Digest Algorithm 5, information digest algorithm fifth edition ) value and sequenceID, the MD5 value is the MD5 value of the sender, which is the result of the "logical AND" operation between the sequenceID and the key in the OAM message.
[0033] When the network device at the other end of the ME receives the OAM message, it performs a "logic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com