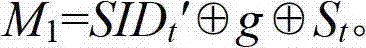An RFID secure communication method established by an ultra-lightweight RFID two-way authentication protocol
A two-way authentication, ultra-lightweight technology, applied in the field of communication, can solve the problems of security vulnerabilities such as RFID inability, achieve low communication costs, solve the problem of key synchronization, and simple operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
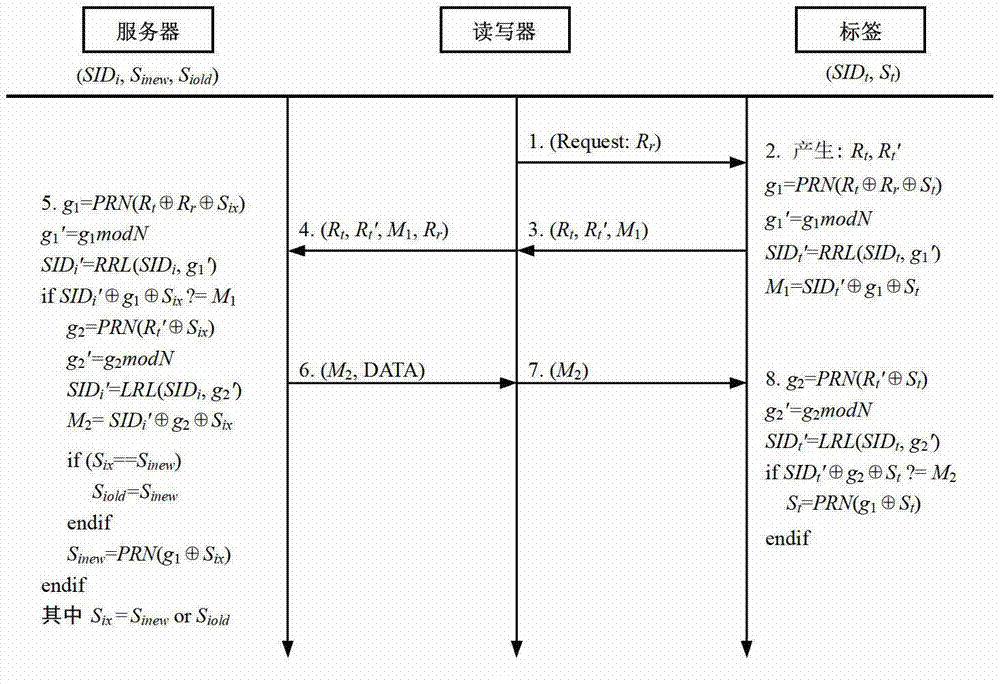
[0023] The RFID secure communication method that the ultra-lightweight RFID two-way authentication protocol that the embodiment of the present invention provides provides the following two processes:
[0024] The initialization process:
[0025] At the beginning of the RFID system, each tag is assigned a unique 1-bit security identity code SID by the server or the manufacturer or completed t and a secret value S of length l-bit t , the server sends the security identity code SID t And the relevant information of the item with the tag is stored in the tag. When the item is logged in, the server will send the information related to the tag: the security identity code SID of each tag i , the current secret value S inew And the secret value S of the last successful authentication iold stored in the backend database. Authentication process:
[0026] 1) Reader→Tag: The reader first generates a random number Rr , will (Query, R r ) to the label.
[0027] 2) Tag→Reader→Server:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com