User identification method and device
A user identification and user identification technology, applied in the network field, can solve problems such as inability to accurately identify users, achieve the effects of reducing information interaction costs and information interaction volume, accurately identifying users, and improving access experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
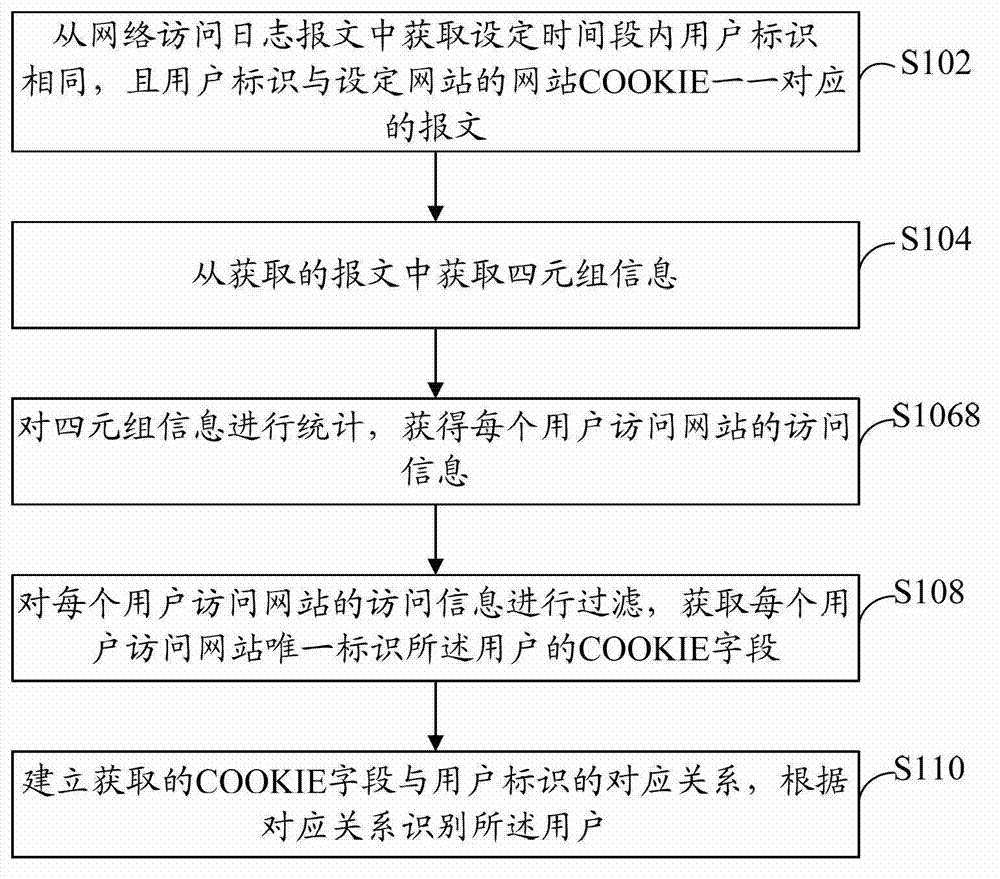
[0030] refer to figure 1 , shows a flow chart of steps of a user identification method according to Embodiment 1 of the present invention.
[0031] The user identification method in this embodiment includes the following steps:
[0032] Step S102: Obtain from the network access log messages the messages in which the user IDs are the same within a set period of time, and the user IDs correspond to the website cookies of the set website one by one.
[0033] Wherein, the set time period can be appropriately set by those skilled in the art according to the actual situation, such as one day or several hours or several days, which is not limited in the present invention. It is set that websites are usually visited by a large number of users and those websites whose COOKIE field can identify the user's identity can be obtained through statistical analysis methods, such as Baidu, Google, Taobao, etc. These websites have well-known and unique COOKIE , it can be determined whether the...
Embodiment 2
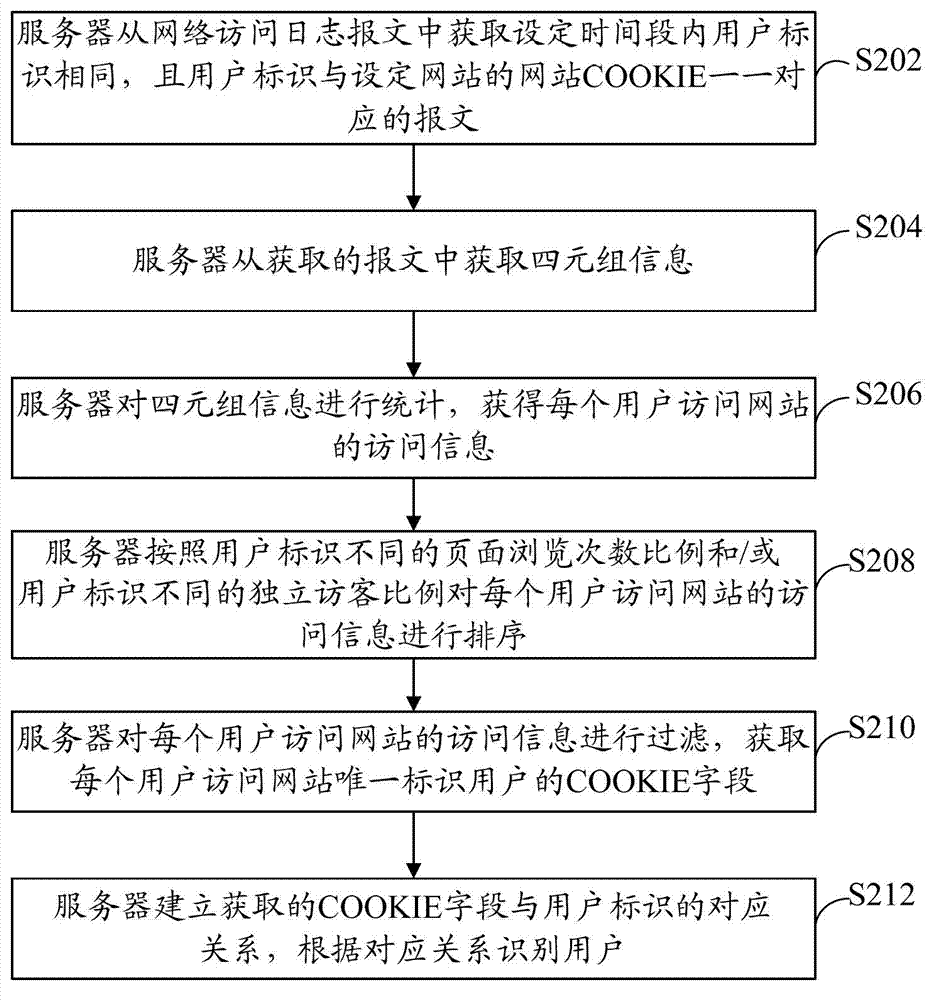
[0045] refer to figure 2 , shows a flow chart of steps of a user identification method according to Embodiment 2 of the present invention.
[0046] The user identification method in this embodiment includes the following steps:
[0047] Step S202: The server obtains from the network access log messages the messages in which the user IDs are the same within a set period of time, and the user IDs correspond to the website cookies of the set website one-to-one.
[0048] In this embodiment, the user identifier includes a user account and a browser version number. User accounts include but are not limited to Internet accounts such as ADSL accounts or ADSL accounts + UA, user mailboxes, and so on.
[0049] Taking a user ID as an example, assuming that the user ID is ADSL1+UA1, the server obtains all packets whose user ID is ADSL1+UA1 from network access log messages. Of course, the user account is not limited to the ADSL account, and other user accounts are also applicable.
[...
Embodiment 3
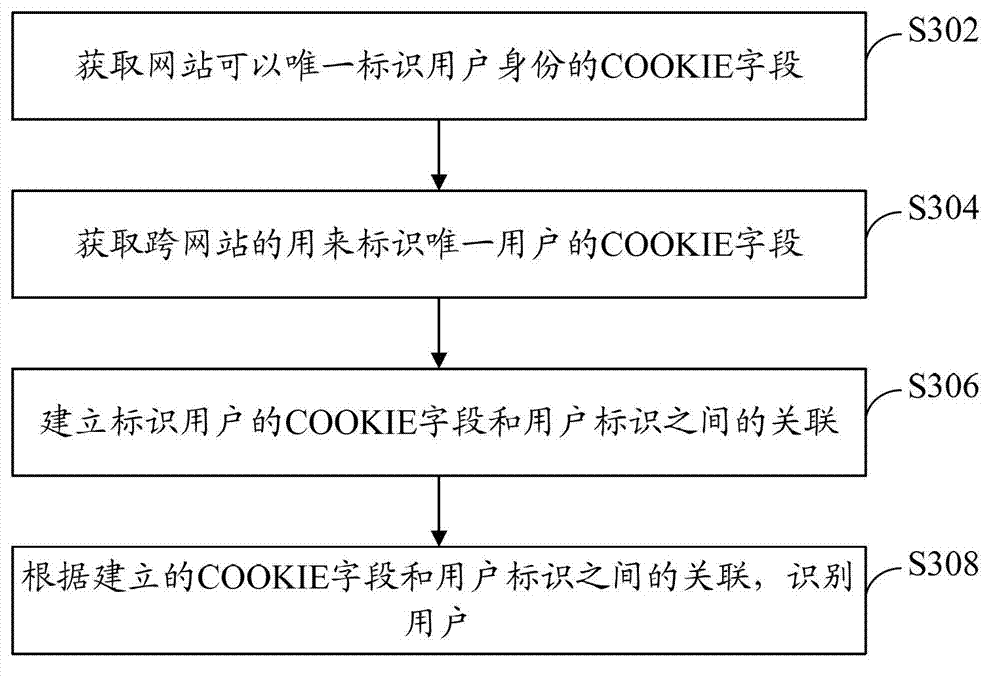
[0065] refer to image 3 , shows a flow chart of steps of a user identification method according to Embodiment 3 of the present invention.
[0066] The user identification method in this embodiment includes the following steps:
[0067] Step S302: Obtain the COOKIE field that can uniquely identify the user identity of the website.
[0068]The cookie information contains a large number of unmarked cookie field information, such as: YYID=D4A741CDC23704C21D8E99150E94F9C4; SUID=96F7B43C26420A0A4EA94973000407AE, etc. These fields can be used as identity information. Through this step, these fields can be automatically parsed from the cookie, and then it can be determined which cookie fields in each website can uniquely identify the user.
[0069] This step specifically includes:
[0070] Step S3022: Obtain a day's original ptu logs (logs that generate messages), and mark the ADSL ID of each log (log) through the online and offline information.
[0071] Step S3024: Select all si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com