Security element, and value document comprising such a security element
一种防伪元件、有价文件的技术,应用在光学元件、制造工具、特种图样等方向,能够解决防伪元件难以仿造、微光学构造难仿制或复制等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
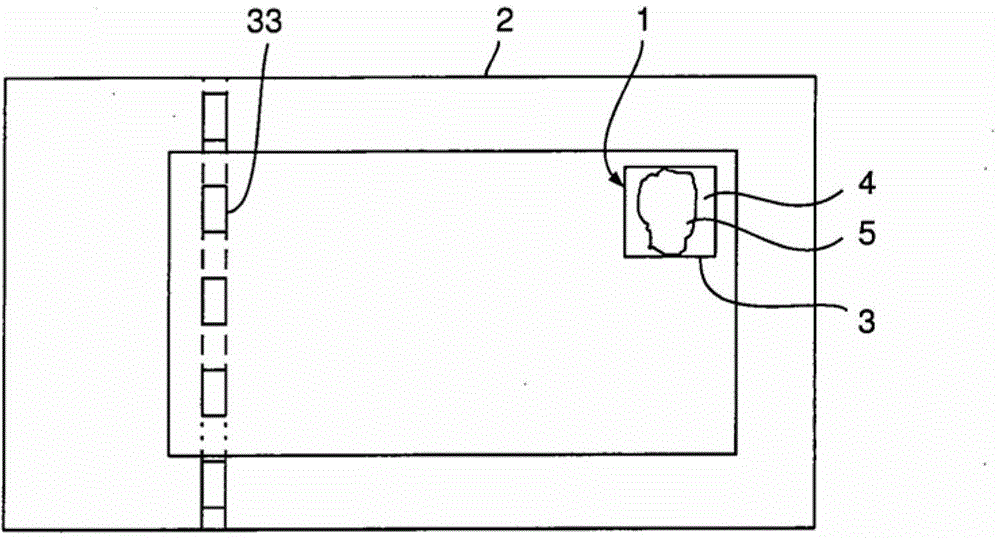
[0059] exist figure 1 In the shown embodiment, the security element 1 according to the invention is integrated in the banknote 2, so that it can be obtained from figure 1 The security element 1 is seen on the front side of the banknote 2 shown in .
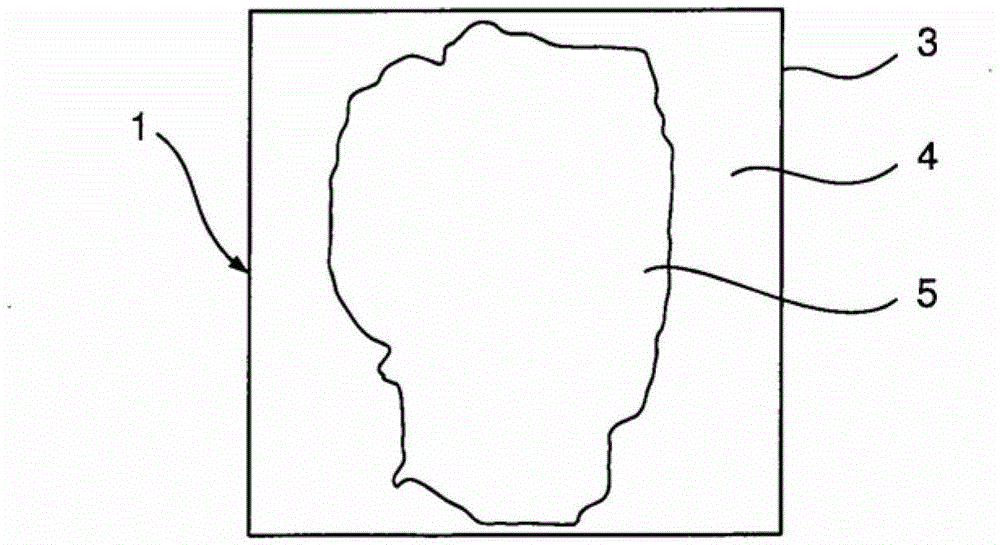
[0060] The security element 1 is designed as a reflective security element 1 with a rectangular graphic area 3 which is divided into a first graphic section 4 and a second graphic section 5 .
[0061] Here, the first graphic part 4 surrounds the second graphic part 5, just as from figure 2 As inferred from the enlarged illustration in .
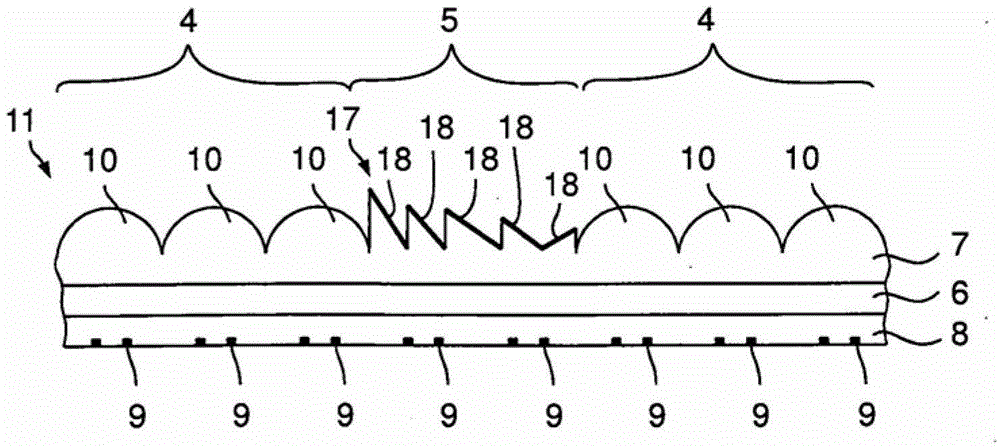
[0062] especially if image 3 As shown in the schematic sectional view of the graphic area 3 in , the graphic area 3 has a carrier foil 6 (which can be, for example, a PET foil) and an upper 7 and a lower embossing varnish layer 8 . In the lower embossing varnish layer 8, the microstructures 9 are arranged in a grid with a fixed geometry (here, for example, a hexagonal grid) perpendicular to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com