Trust Value Management Method of Sensor Nodes in Wireless Sensor Networks Based on Tree Topology Structure of IPv6
A sensor node, wireless sensor technology, applied in wireless communication, network topology, data exchange network, etc., can solve problems such as energy consumption, low accuracy of evaluation results, and single evaluation dimension.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
[0062] The trust value management method of sensor nodes in the wireless sensor network based on the tree topology of IPv6, it comprises the following steps:
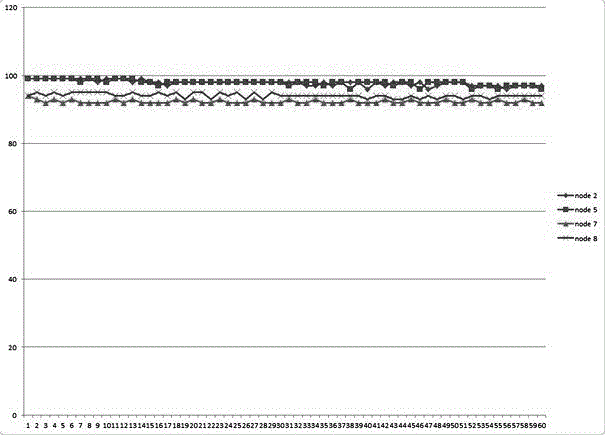
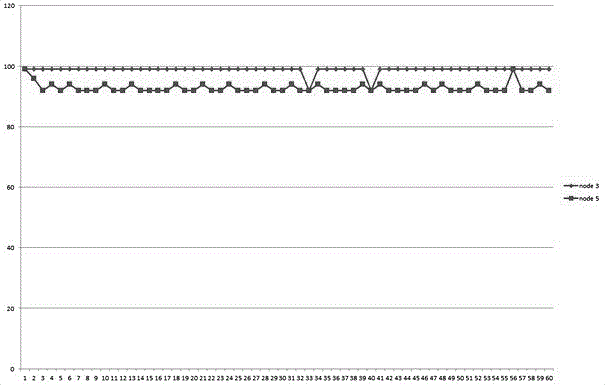
[0063] S1: The trust value evaluation is performed periodically between the sensor nodes, and the cycle length is Δt;
[0064] S2: Each sensor node reports the evaluation result of its trust value to the neighbor node to the data aggregation Sink node;
[0065] S3: The data aggregation Sink node synthesizes the trust value evaluation results of all neighbor nodes for a certain sensor node and the trust value evaluation results of the data aggregation Sink node for the sensor node according to the received trust value evaluation results;
[0066] The trust value evaluation includes a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com