An identity-based end-to-end key authentication negotiation method and system
A technology of identity identification and key authentication, which is applied in the field of information security and can solve problems such as denial of service attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
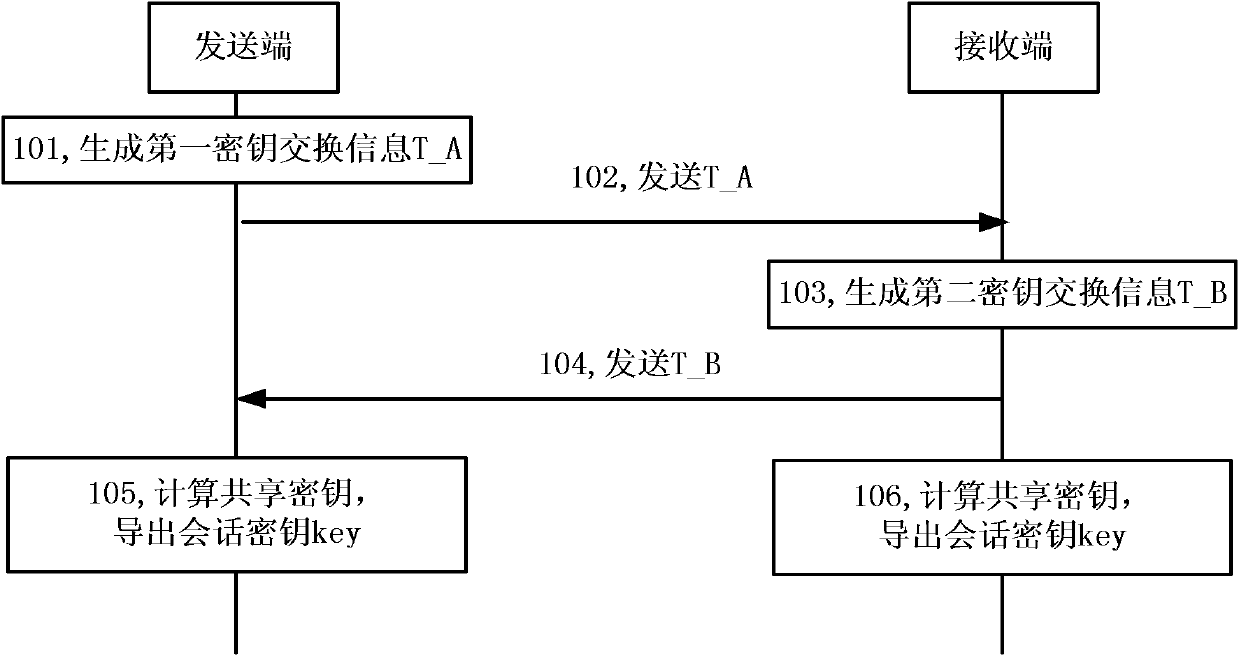
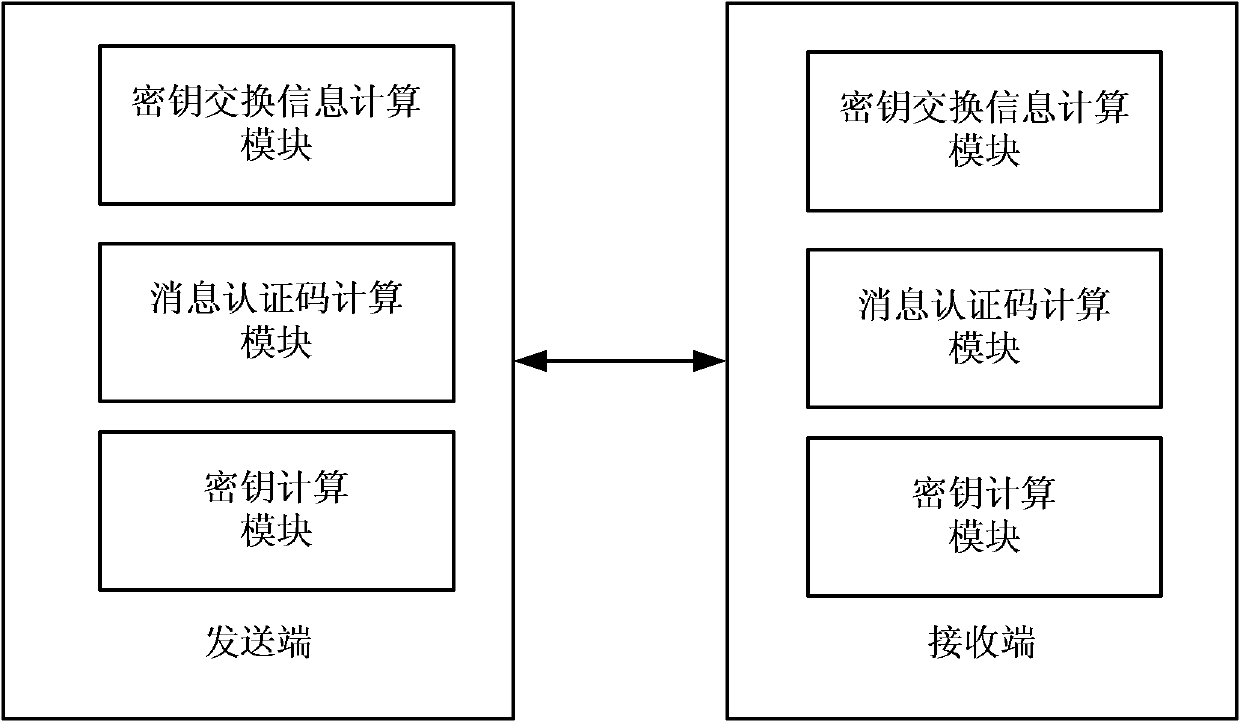
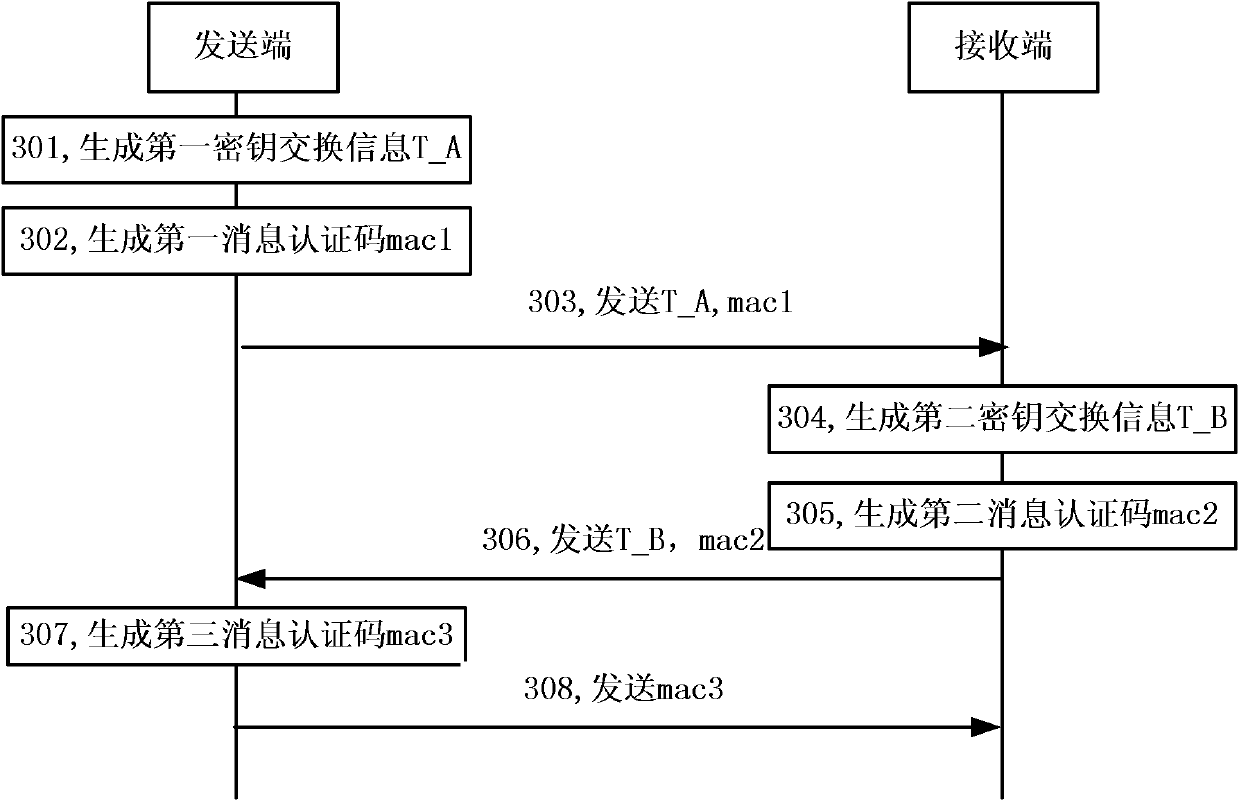
[0082] The sending-end message authentication code calculation module is further configured to generate a first key according to the sending-end private key, the receiving-end identity identifier, and first key exchange-related information when generating the first message authentication code, from the first Deriving the first authentication key from a key, using the first authentication key as the input key of the first message authentication code algorithm, and calculating the first message authentication code; When the second message authentication code is received by the end, a second key is generated according to the private key of the sending end, the identity of the receiving end, the second key exchange information, and the first key exchange related information, and the second key is obtained from the second key The second authentication key is derived from the key, and the second authentication key is used as the input key of the second message authentication code alg...
Embodiment approach 2
[0085] The sending-end message authentication code calculation module is further configured to generate a first key according to the sending-end private key, the receiving-end identity identifier, and first key exchange-related information when generating the first message authentication code, from the first Deriving the first authentication key from a key, using the first authentication key as the input key of the first message authentication code algorithm, and calculating the first message authentication code; When the second message authentication code is received by the end, a second key is generated according to the private key of the sending end, the identity of the receiving end, the second key exchange information, and the first key exchange related information, and the second key is obtained from the second key The second authentication key is derived from the key, and the second authentication key is used as the input key of the second message authentication code alg...
Embodiment approach 3
[0088] The sending-end message authentication code calculation module is further configured to generate a first key according to the sending-end private key, the receiving-end identity identifier, and first key exchange-related information when generating the first message authentication code, from the first Deriving the first authentication key from a key, using the first authentication key as the input key of the first message authentication code algorithm, and calculating the first message authentication code; When the second message authentication code is received by the end, a second key is generated according to the private key of the sending end, the identity of the receiving end, the second key exchange information, and the first key exchange related information, and the second key is obtained from the second key The second authentication key is derived from the key, the session key is derived from the second authentication key, and the session key is used as the input ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com