Data monitoring method and device
A data monitoring method and data technology, applied in the network field to achieve the effect of flexible monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
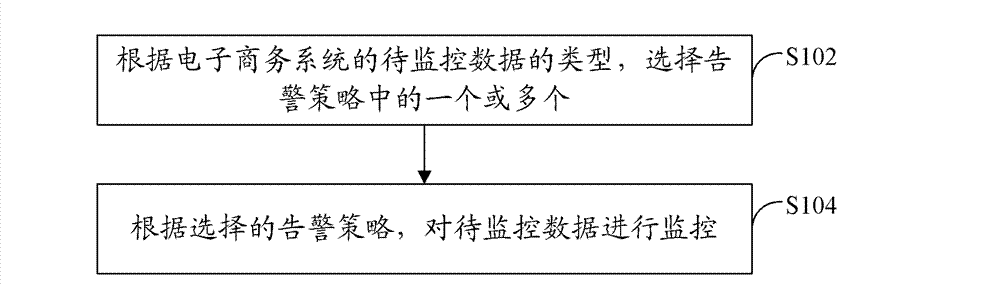
[0028] refer to figure 1 , which shows a flowchart of steps of a data monitoring method according to Embodiment 1 of the present application.
[0029] The data monitoring method of the present embodiment includes the following steps:
[0030] Step S102: According to the type of data to be monitored in the e-commerce system, select one or more of the warning strategies.
[0031] Among them, the warning strategy includes: a fixed value warning strategy, a baseline warning strategy and a fluctuating warning strategy. Among the above alarm strategies, the fixed value alarm strategy is used to give an alarm when the data to be monitored exceeds the set threshold; the baseline alarm strategy is used to compare the data to be monitored with the set The alarm is issued when the range is exceeded; the fluctuation alarm strategy is used to issue an alarm when the data to be monitored is compared with the set data and exceeds the set range.
[0032] The data types of the e-commerce syst...
Embodiment 2
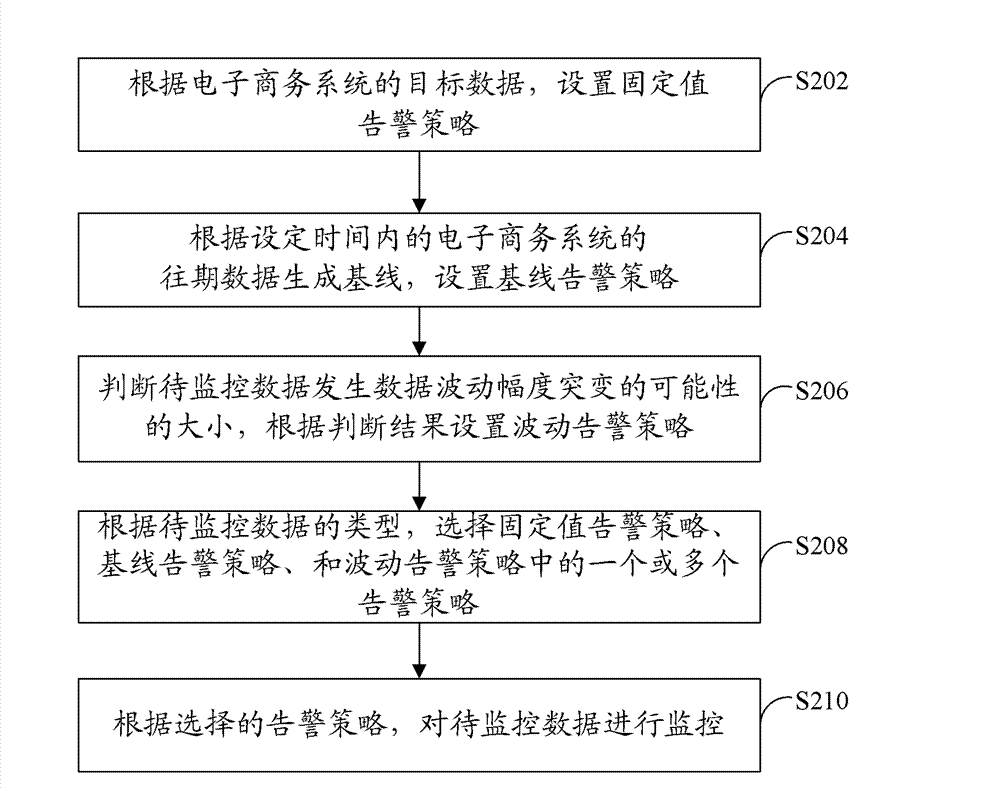
[0038] refer to figure 2 , which shows a flowchart of steps of a data monitoring method according to Embodiment 2 of the present application.
[0039] The data monitoring method of the present embodiment includes the following steps:
[0040] Step S202: According to the target data of the e-commerce system, set a fixed-value alarm strategy.
[0041] In this step, the fixed-value alarm strategy can adopt an existing setting method, including setting a maximum threshold and a minimum threshold. The fixed-value alarm strategy is usually applicable to monitoring indicators that exceed the threshold at different time periods every day and can be alarmed, and the trend is relatively flat and has little correlation with users. For example: the number of abnormalities in application-level data, the number of database connections / database cache hit rate in basic service-level data, and the monitoring and alarming of disk space in system-level data.
[0042] Step S204: Generate a ba...
Embodiment 3
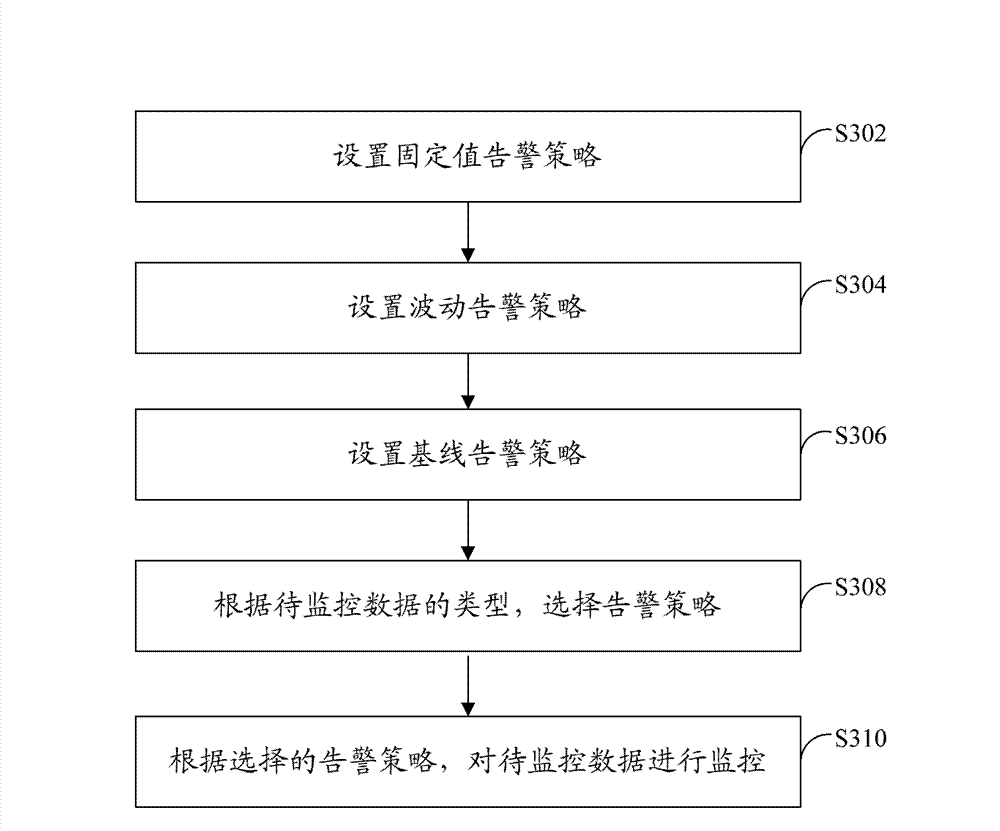
[0064] refer to image 3 , which shows a flowchart of steps of a data monitoring method according to Embodiment 3 of the present application.
[0065] The data monitoring method of the present embodiment includes the following steps:
[0066] Step S302: Set a fixed-value alarm strategy.
[0067]That is, a threshold is set, the data to be monitored in the e-commerce system is compared with the set threshold, and an alarm is issued when the threshold is exceeded. The type of the threshold value can be numeric or character string, and the comparison conditions include "=", "!=", ">", ">=", "<", "<=", "contains", "does not contains" etc.
[0068] Step S304: Set a fluctuation warning policy.
[0069] That is, obtain the past data of the e-commerce system at a set time point or time period, compare the data to be monitored with the obtained past data, and issue an alarm when it exceeds a certain range.
[0070] In this embodiment, the set fluctuation alarm strategy includes: co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com