A method of providing security protection for item identification and its analysis service
A technology for parsing service and item identification, applied in the field of Internet of Things information systems, and can solve problems such as limited coding space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The present invention will be described in further detail below in conjunction with the examples.
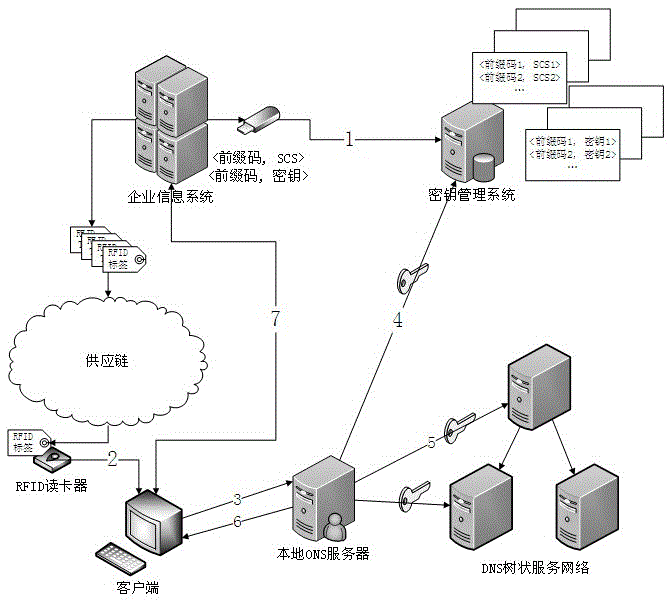
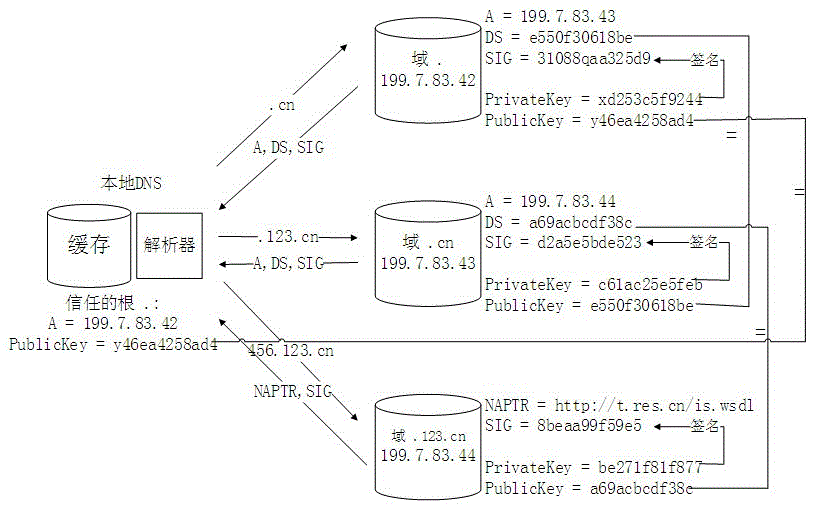
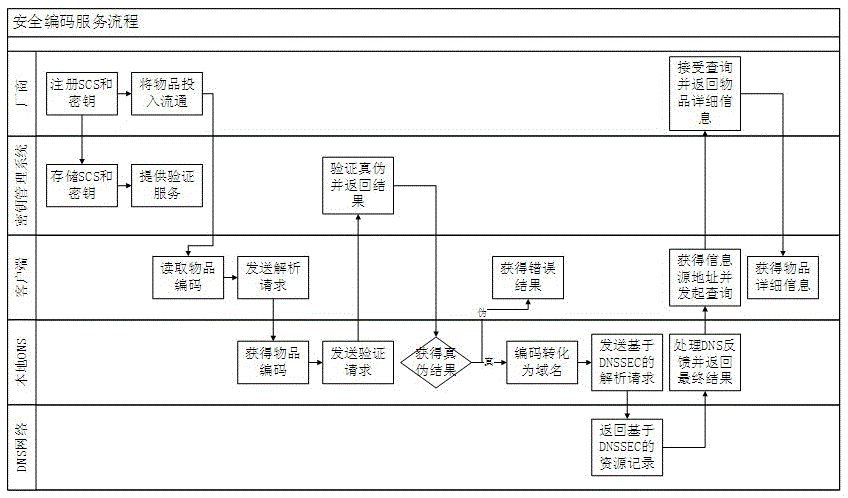
[0055] figure 1 Shown is the security item identification analysis service process completed by the cooperation of enterprise information system, key management system, local ONS server, DNS tree service network supporting DNSSEC and client. image 3 Swimlane flowchart for secure coding services.
[0056] An example is given below to specifically illustrate the whole process of security item code from generation to analysis. Assume that a manufacturer uses the Serialized Global Trade Identification Number (SGTIN-96) to mark items, which has a length of 96 bits. The first 58 bits have a fixed meaning and are used to indicate the category of the product, and the last 38 bits are freely defined by the manufacturer. For cost considerations, the RFID tag capacity selected by the manufacturer is 96 bits, and a space-sensitive 8-bit verification code is selected to provide se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com