Method for detecting crossing use of mobile storage equipment
A technology of a mobile storage device and a detection method, which is applied in the detection field of mobile storage devices, can solve the problem of not realizing the cross-use detection of mobile storage media, etc., and achieve the effect of avoiding file loss.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
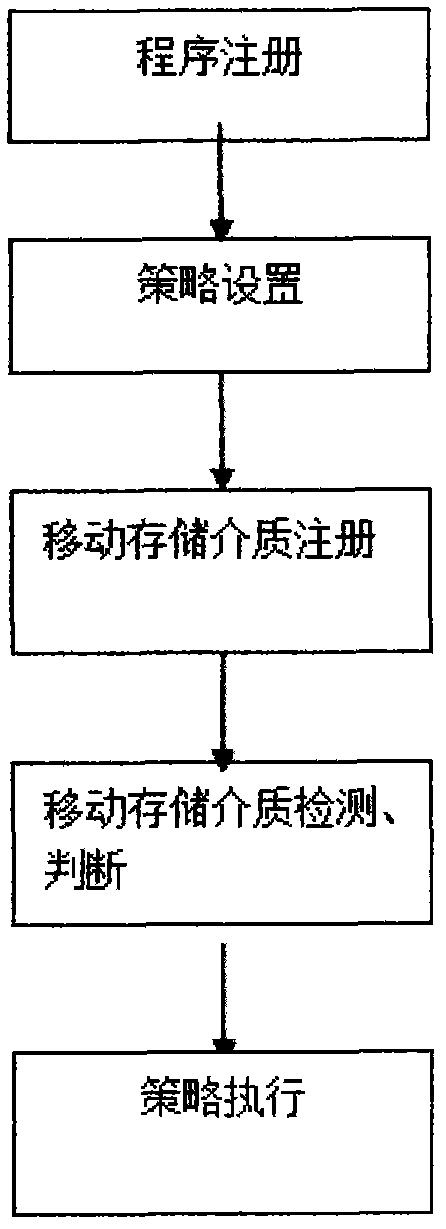
[0023] The detection method for cross-use of mobile storage devices of the present invention operates under the stand-alone version, and the steps are as follows:
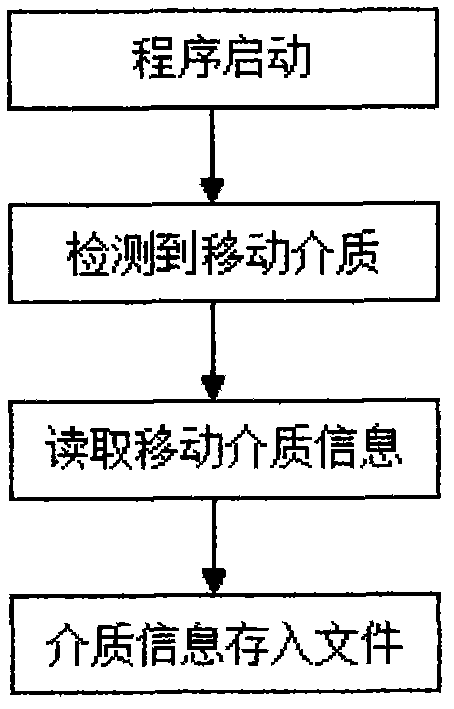
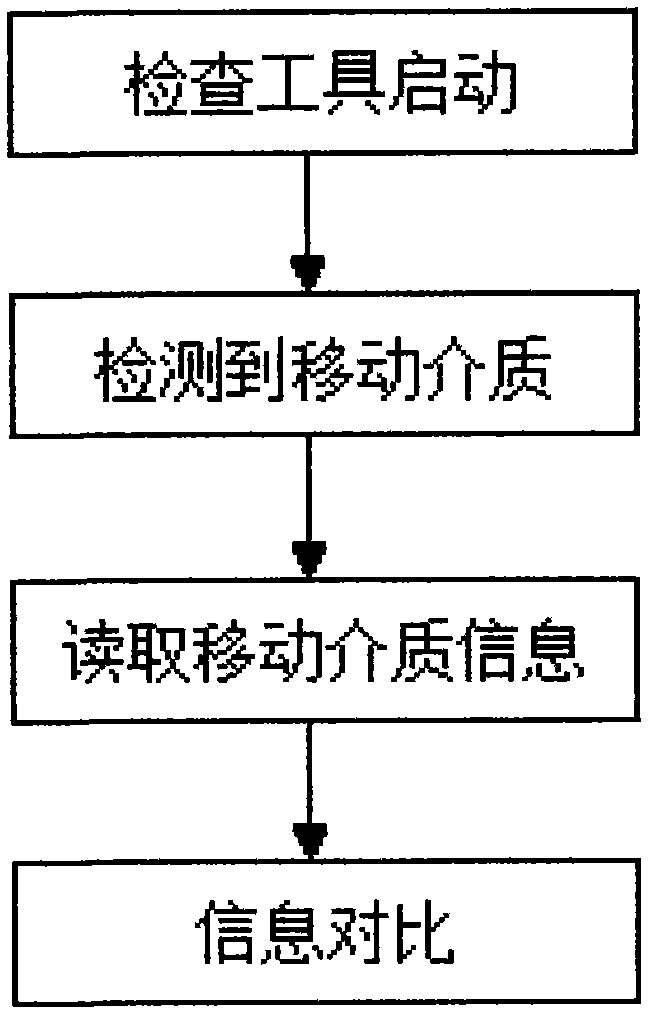
[0024] Such as figure 1 As shown, when the program runs on the computer for the first time, the program registration is performed, that is, the program is automatically copied to the system directory for operating the computer, and registers itself as an interrupt operation mode; when the mobile storage medium is found to have cross-use behavior, It is determined through the policy setting that the mobile storage medium is processed in a mode that prohibits reading and writing or read-only; the mobile storage medium registration module is responsible for obtaining its relevant information when the mobile storage medium is inserted, and storing it in a fixed location; when the insertion of the mobile storage medium is detected again When the system is running, read and compare the existing information of the mobile ...
Embodiment 2
[0032] The detection method for cross-use of mobile storage devices of the present invention runs under the network version, and the steps are as follows:
[0033] This solution can be used in the network. It adds an authentication server on the basis of the stand-alone version, uploads the registration information of the mobile storage medium to the server, and adds a step of limiting the range of cross-use, that is, the mobile storage Modifications within the scope of use are not considered cross-use, and only use outside the limited scope of cross-use is considered cross-use.
[0034] In the network model, it includes a plurality of computers 1-n, and a server for saving the authentication database. The general process of this program is as follows Figure 5 As shown, all computers in the network, such as computers 1-n, run the authentication program independently, and the authentication program is similar to the program registration function in the above-mentioned stand-a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com