Method for activating token equipment
A token and device technology, applied in the field of information security, can solve the problem of low key security, and achieve the effect of improving security and ensuring the security of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
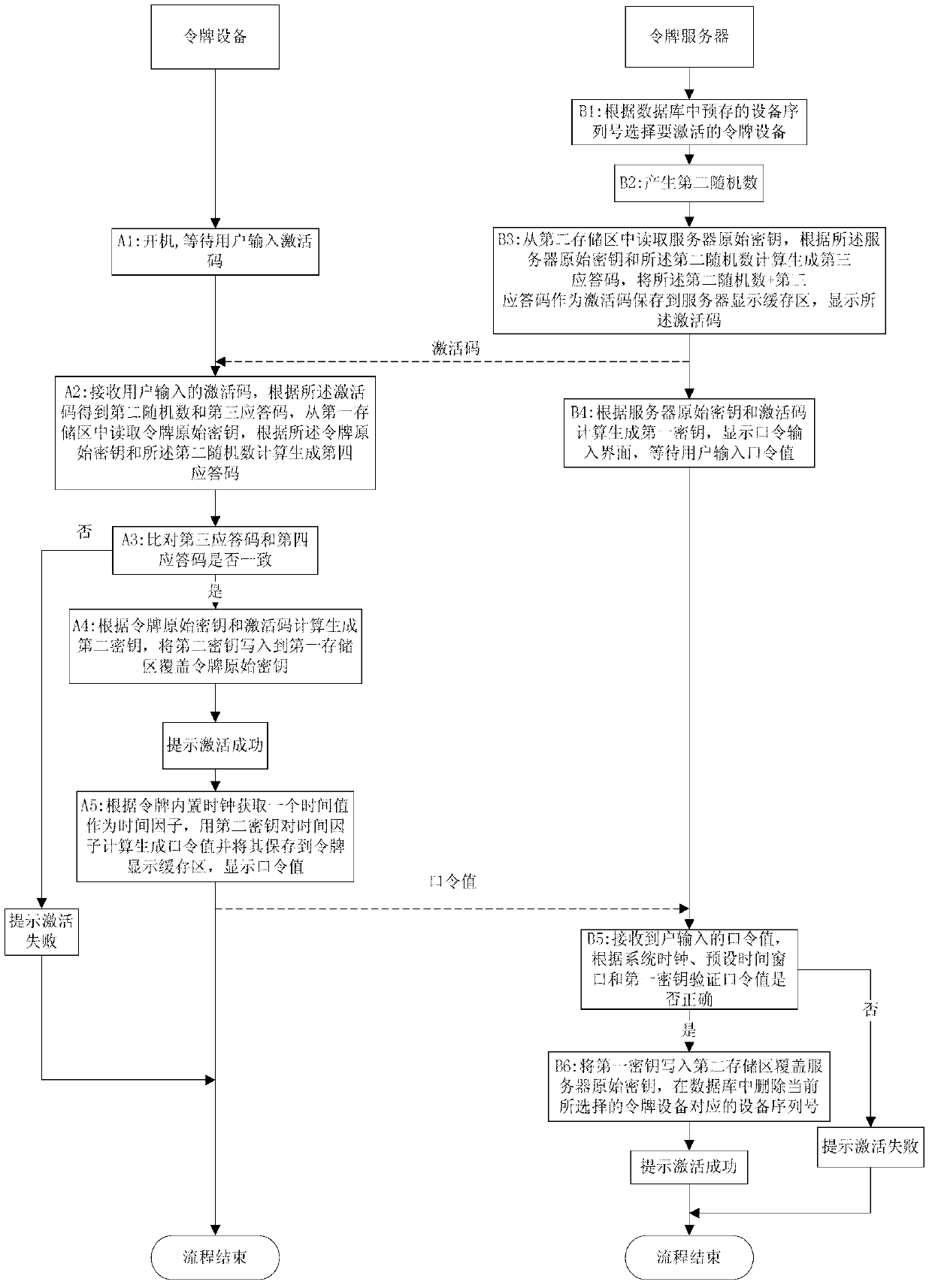
[0031] The method for activating a token device proposed in Embodiment 1 includes steps A1-A5 performed by the token device and steps B1-B6 performed by the token server. The specific process is as follows figure 1 Shown:
[0032] Step A1: Turn on the token device and wait for the user to input the activation code;
[0033] Specifically, the token device is turned on to check whether it has been activated, and if so, it will display the token normal working interface and enter the normal work flow; otherwise, it will display the activation interface, wait for the user to input the activation code, and continue to step A2.
[0034] Step A2: The token device receives the activation code input by the user, obtains the second random number and the third response code according to the activation code, reads the original key of the token from the first storage area, and obtains the original key of the token according to the original key of the token. key and the second random numbe...
Embodiment 2
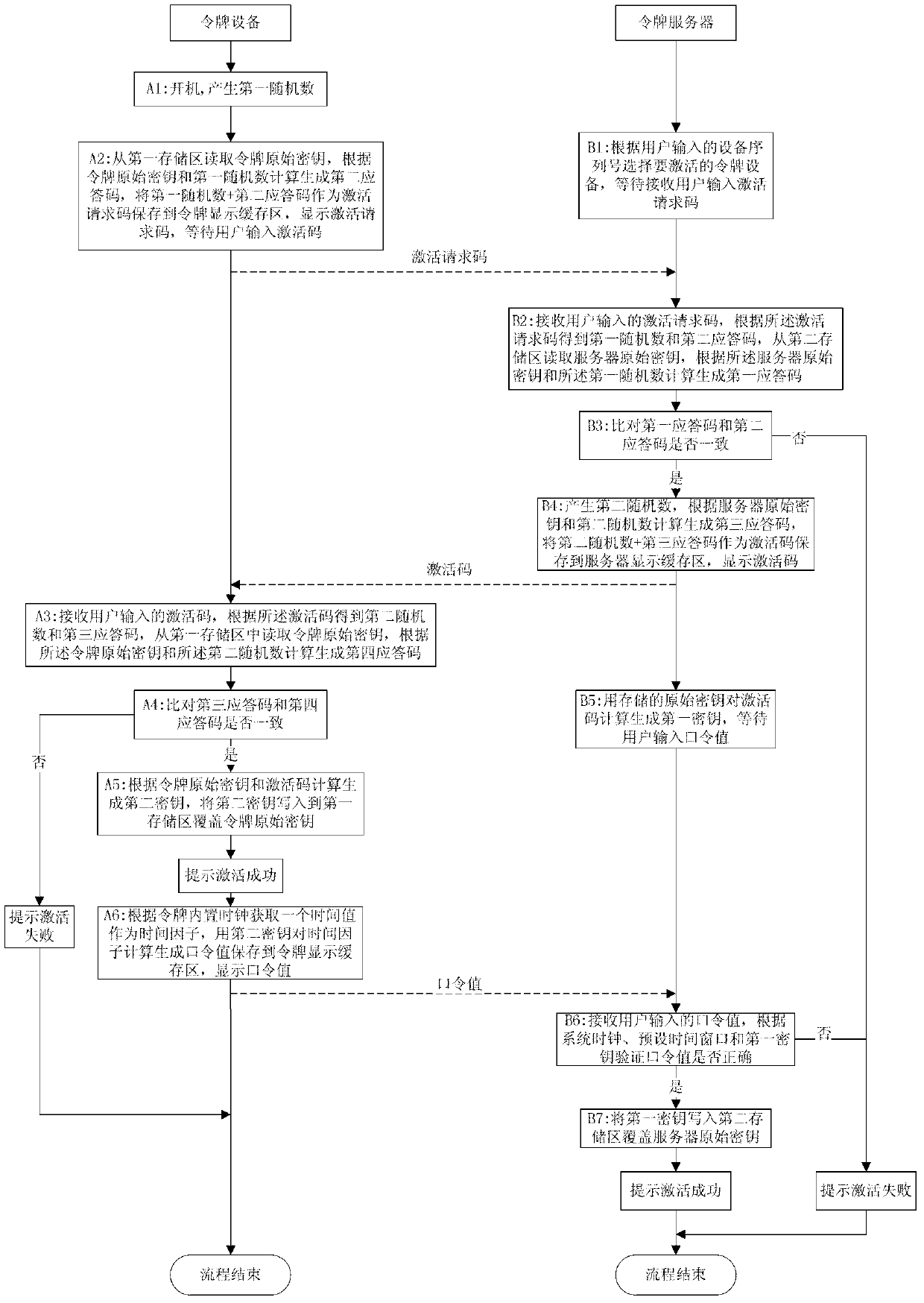
[0066] The method for activating a token device proposed in Embodiment 2 includes steps A1-A5 performed by the token device and steps B1-B6 performed by the token server. The specific process is as follows figure 2 Shown:
[0067] Step A1: Turn on the token device and generate the first random number;
[0068] In this embodiment, preferably, the token device uses a random number generator to generate a first random number with a length of 6 bits.
[0069] Further, the token device can also change the device serial number according to preset rules to generate the first random number.
[0070] Step A2: The token device reads the original key of the token from the first storage area, calculates and generates the second response code according to the original key of the token and the first random number, and uses the first random number + the second response code as an activation request The code is saved to the token display buffer area, and the activation request code is disp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com