Design method for safe and mobile storage controller authorized and encrypted/decrypted by wireless terminal
A technology of mobile storage and design method, applied in the field of information, can solve the problems of unauthorized file hiding, inaccessibility, unrecognizable security mobile storage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
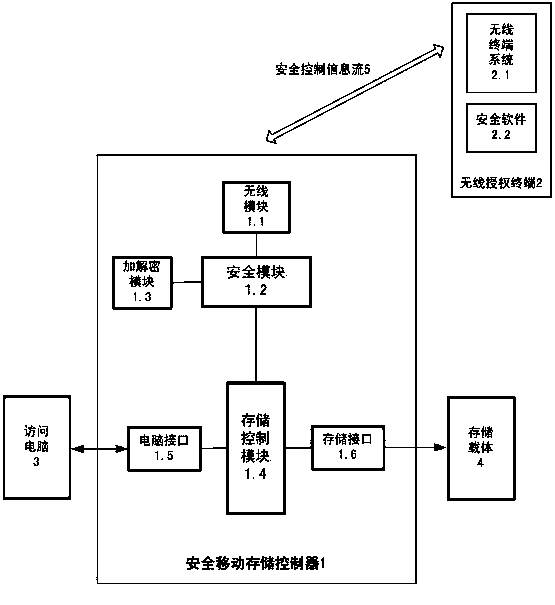
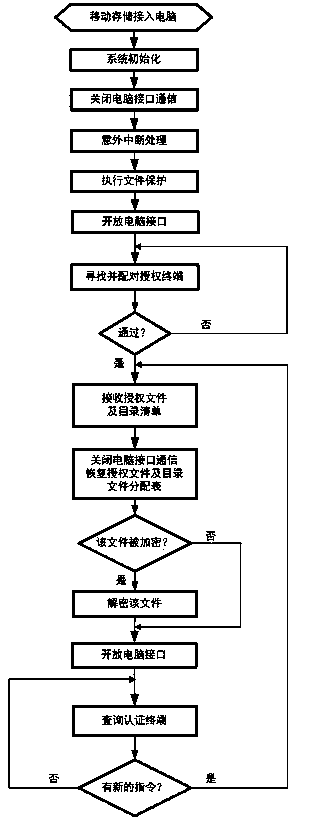
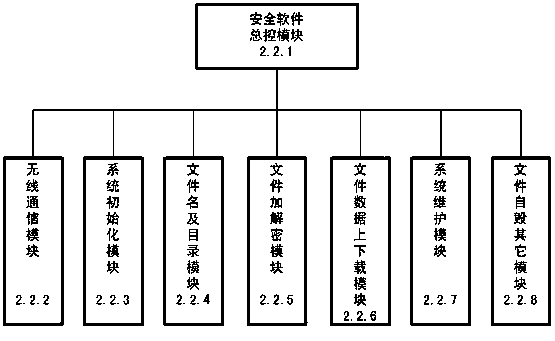
[0090] see figure 1 , the design method of the secure mobile storage controller using wireless terminal authorization authentication and encryption and decryption in the present invention consists of two parts, the first is a secure mobile storage controller 1, and the second is a wireless authorized terminal 2. If the secure mobile storage controller is regarded as the first party, and the access computer 3 is regarded as the second party, then the wireless authorized terminal is used as a third-party device, and the basic idea of the present invention is to introduce a third-party device—a wireless authorized terminal—to authenticate Authorize the access of the computer to the secure mobile storage controller, as well as the file encryption and decryption function and other security functions when the secure mobile storage controller reads out the file. At this time, for the owner of the safe mobile storage controller, it is not necessary to directly face the embarrassment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com