Protection method for terminal temporary identifier, terminal, core network control entity and system
A technology for temporary identification and control of entities, which is applied in network data management, electrical components, wireless communication, etc. It can solve problems such as poor security and temporary identification cannot be updated in time, and achieve the effect of improving terminal security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
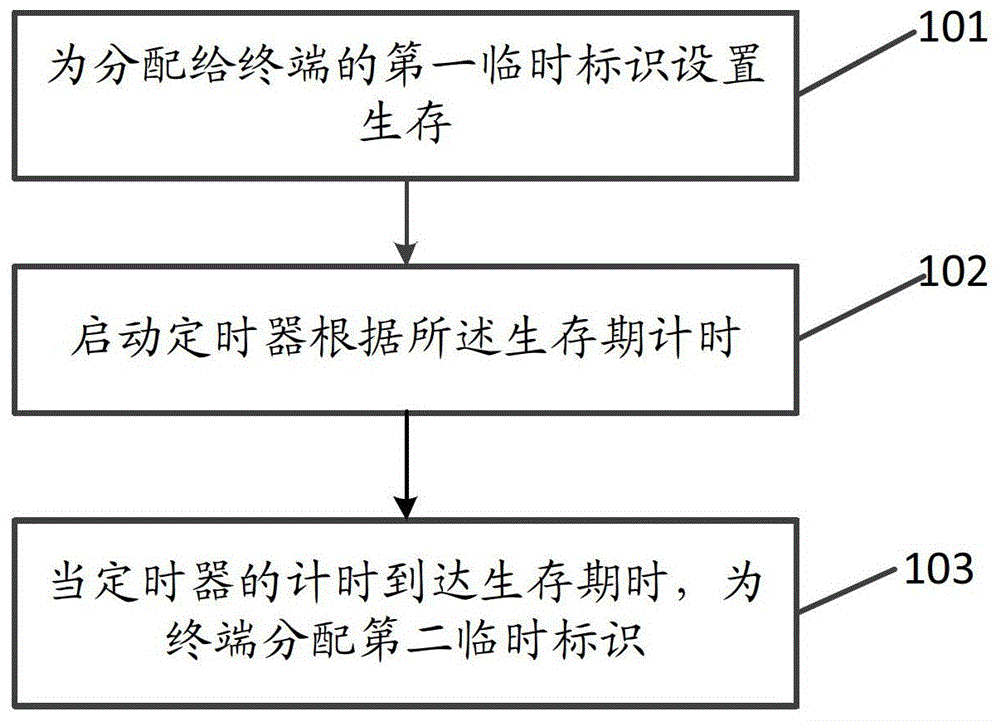
[0079] This embodiment provides a method for protecting a temporary identifier of a terminal, such as figure 1 As shown, the method includes:
[0080] 101. Set a lifetime for the first temporary identifier assigned to the terminal, and start a timer;
[0081] 102. When the timing of the timer reaches the lifetime, allocate a second temporary identifier to the terminal.
[0082] The above method can be implemented on the terminal alone, or on the core network control entity on the network side, or partly on the terminal and partly on the core network control entity through switching.
[0083] In the method provided by this embodiment, by setting a lifetime for the temporary identifier assigned by the terminal, when the lifetime of the temporary identifier expires, the network reassigns the temporary identifier to the terminal to solve the problem that the temporary identifier is caused by the mobility of the terminal. It solves the technical problem that it cannot be updated ...
Embodiment 2
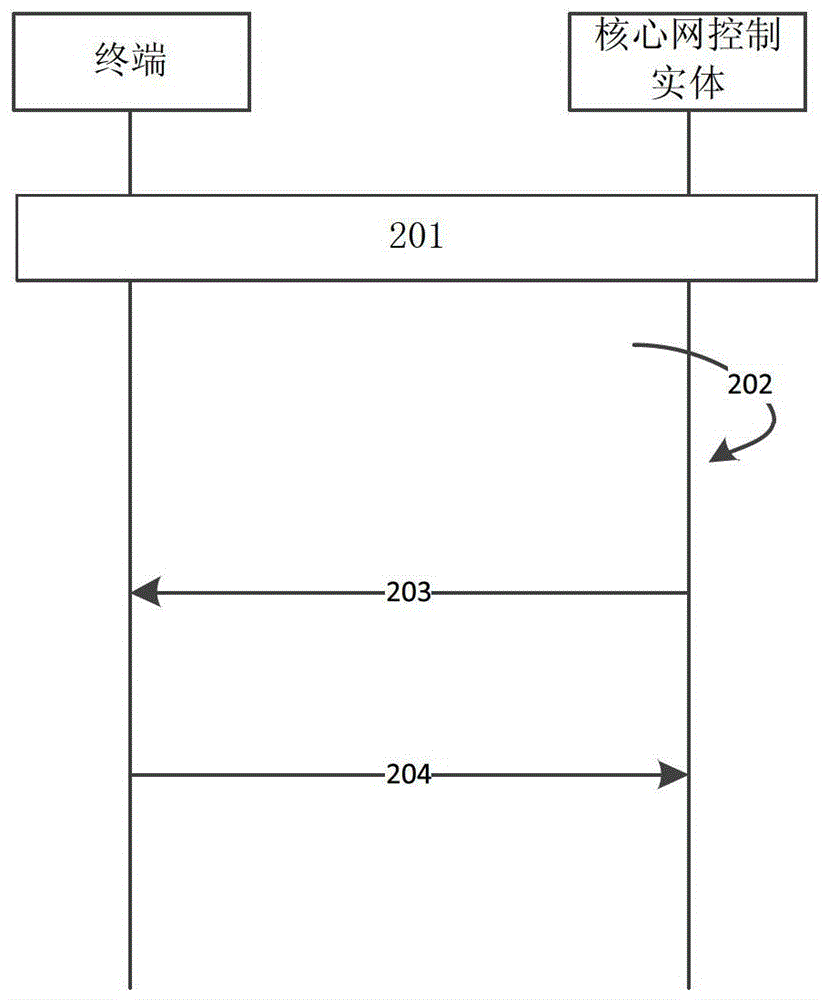
[0091] This embodiment provides a method for protecting a temporary identifier of a terminal. The method is mainly deployed on the network side to implement a scheme in which the network side sets the lifetime of the temporary identifier and maintains and updates it. Such as figure 2 As shown, the method includes:
[0092] 201. After the core network control entity assigns a first temporary identifier to the terminal, the core network control entity sets a lifetime for the terminal;
[0093] In this embodiment and the following embodiments, after the core network control entity assigns the first temporary identifier to the terminal, it means that the core network control entity follows the normal temporary identifier allocation process (such as GUTI allocation process, Attach process or TAU process) ) after assigning a temporary identifier to the terminal, and after the terminal receives the assigned temporary identifier.
[0094]202. The core network control entity starts ...
Embodiment 3
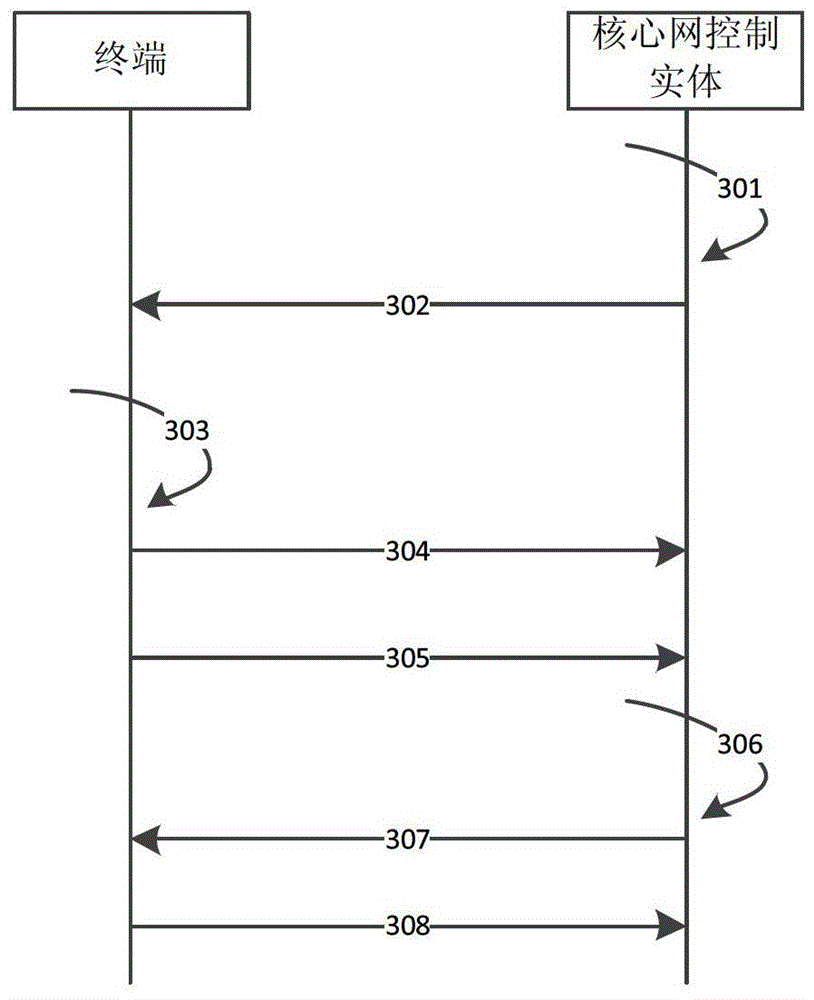
[0101] This embodiment provides a method for protecting a temporary identifier of a terminal. The method is mainly deployed on the network side and the terminal respectively to implement a solution in which the network side sets the lifetime and the terminal maintains the lifetime update. Such as image 3 As shown, the method includes:
[0102] 301. When the core network control entity allocates the first GUTI to the terminal (the specific timing can be considered as before the core network entity sends the allocated first GUTI to the terminal), the core network control entity sets a lifetime for the terminal;
[0103] Specifically, in step 301, during the ongoing Attach or TAU process, or when the network is about to initiate a GUTI reallocation process, the core network control node allocates a first GUTI to the terminal and sets the lifetime of the first GUTI.
[0104] "When the core network control entity assigns the first temporary identifier to the terminal" mentioned i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com