Fishing web page clustering method and device
A technology of phishing web pages and clustering method, applied in the field of information security, can solve the problem of not completely preventing the spread of phishing web pages from the source, and achieve the effect of preventing the spread and reducing the false positive rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
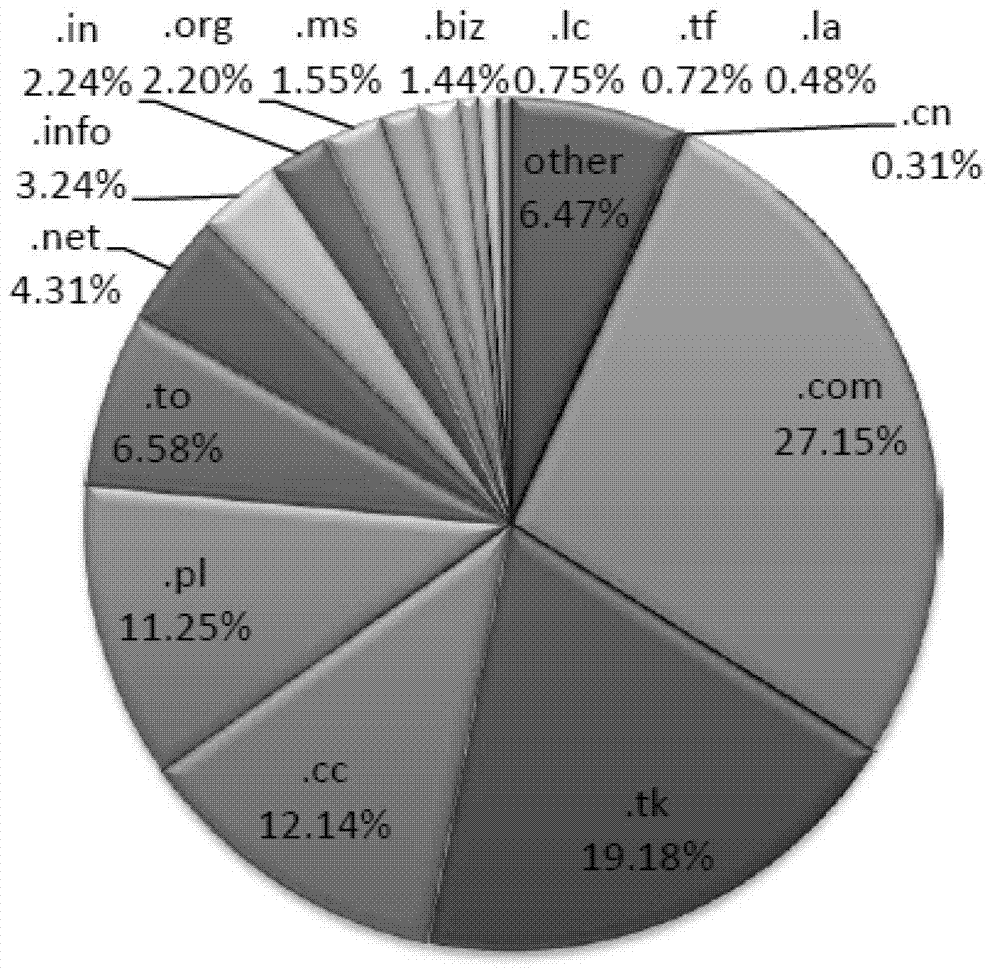
[0048] At present, there are various clustering methods for phishing webpages, but the feature of "domain name type" has not been utilized yet. The inventor of the present invention thought of using "domain name type" to solve the problem of phishing webpage clustering, effectively avoiding the drawbacks of the prior art. When phishing criminals use the sub-domain name of the second-level domain name to commit crimes, they can use the feature of "domain name type" to directly cluster the phishing web pages into the sub-domain name of the second-level domain name applied by the phishing criminal, and identify them as phishing web pages , completely stop the spread of phishing webpages at the source. Among them, the domain name type can include top-level domain name and second-level domain name, etc., for example, .com is a top-level domain name, which can also provide sub-domain application, cn.ms is a second-level domain name, which can provide sub-domain registration, for For...
Embodiment 2
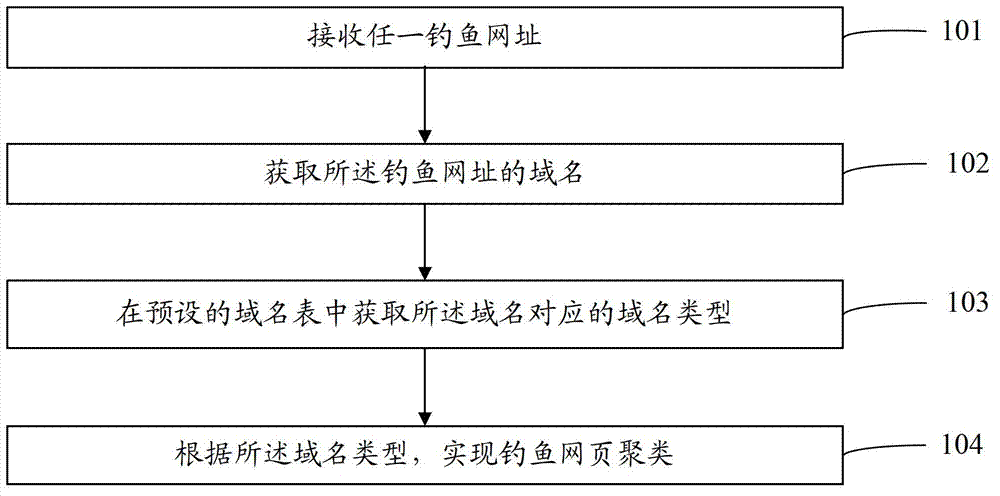
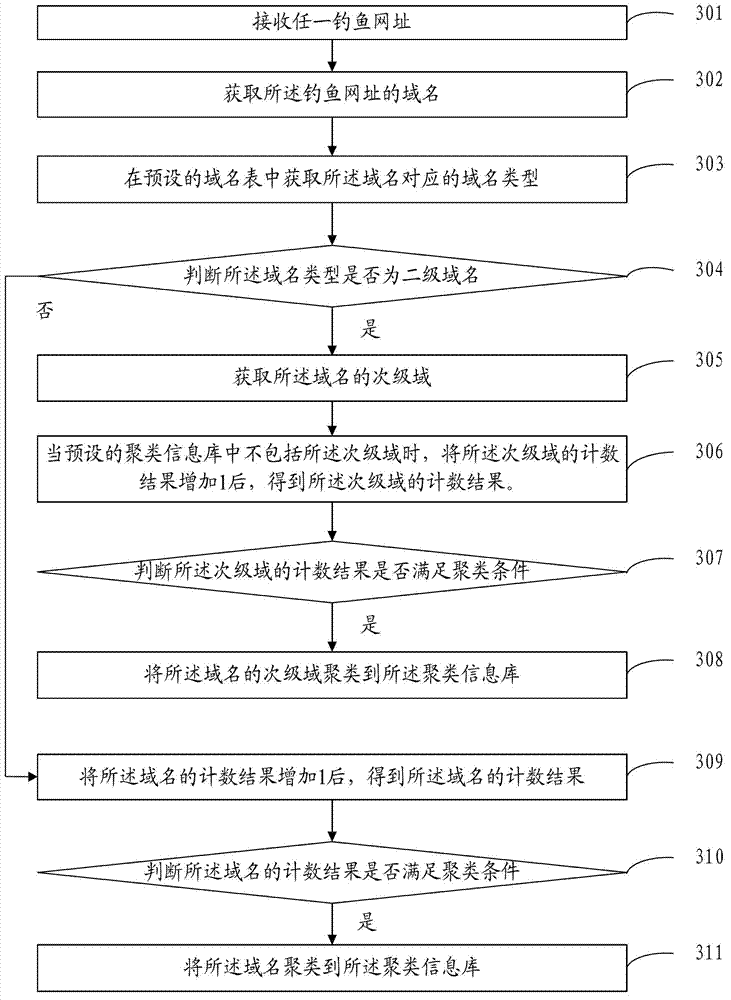
[0066] refer to image 3 , image 3 The flow chart of the phishing web page clustering method provided in this embodiment may specifically include:
[0067] Step 301: receiving any phishing URL;
[0068] Step 302: Obtain the domain name of the phishing website;
[0069] Step 303: Obtain the domain name type corresponding to the domain name in the preset domain name table;
[0070] Steps 301 to 303 in this embodiment are the same as steps 101 to 103 in Embodiment 1, and will not be repeated here.
[0071] Step 304: Determine whether the domain name type is a second-level domain name, if yes, go to step 305, if not, go to step 309.
[0072] In this embodiment, after acquiring the domain name type corresponding to the domain name, it is first judged whether the domain name type belongs to the second-level domain name, if yes, go to step 305 , otherwise go to step 309 .
[0073] In actual operation, after determining the domain name type, you can refer to Table 2 to determine...
Embodiment 3
[0097] refer to Figure 4 , Figure 4 The structural diagram of the phishing web page clustering device provided in this embodiment, the device may include:
[0098] A receiving module 401, configured to receive any phishing URL;
[0099] The first obtaining module 402 is used to obtain the domain name of the phishing website;
[0100] The second acquiring module 403 is configured to acquire the domain name type corresponding to the domain name in the preset domain name table;
[0101] The clustering module 404 is configured to implement clustering of phishing webpages according to the type of the domain name.
[0102] Wherein, the clustering module may include:
[0103] The first judging submodule is used to judge whether the domain name type is a second-level domain name;
[0104] A first acquiring submodule, configured to acquire the secondary domain of the domain name when the result of the first judging submodule is yes;
[0105] The first adding submodule is used t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com