Method and system for simulating and detecting cloud security
A detection method and detection system technology, applied in the field of information security, can solve the problems of ignoring the characteristics and status of the internal security defense system, failing to detect and know the security status of the network system, etc., to achieve the effect of improving defense capabilities and comprehensive detection results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
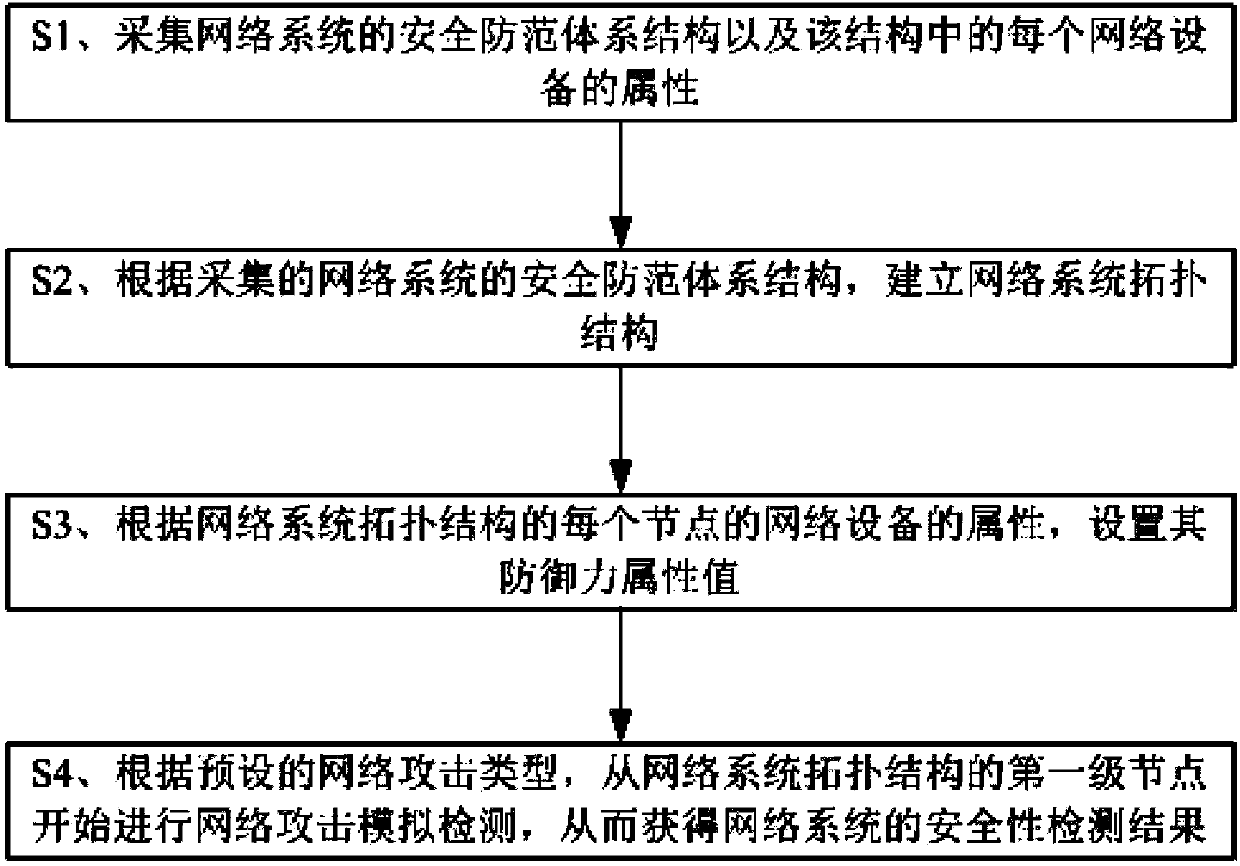
[0070] A specific embodiment of a cloud security simulation detection method of the present invention is as follows:
[0071] A cloud security simulation detection method, comprising:
[0072] S1. Collect the security protection architecture of the network system and the attributes of each network device in the structure; network devices include the Internet, and also include one or more of hubs, switches, firewalls, routers, computers or servers, here because Network attacks are initiated by various terminal devices through the Internet, so the Internet is also regarded as network equipment, and the source of network attacks is generally considered to be the Internet. The security protection architecture of the network system is actually the structure of the network system, and the structure of the network system composed of various network devices is called the security method architecture of the network system.
[0073] S2. Establish the network system topology structure a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com