Security control method, operation management billing system, application store and mobile terminal
A mobile terminal, operation management technology, applied in security devices, accounting/billing services, electrical components, etc., can solve the problems of interruption, no security processing measures, and difficulty in ensuring the security of short messages, so as to avoid interruption and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
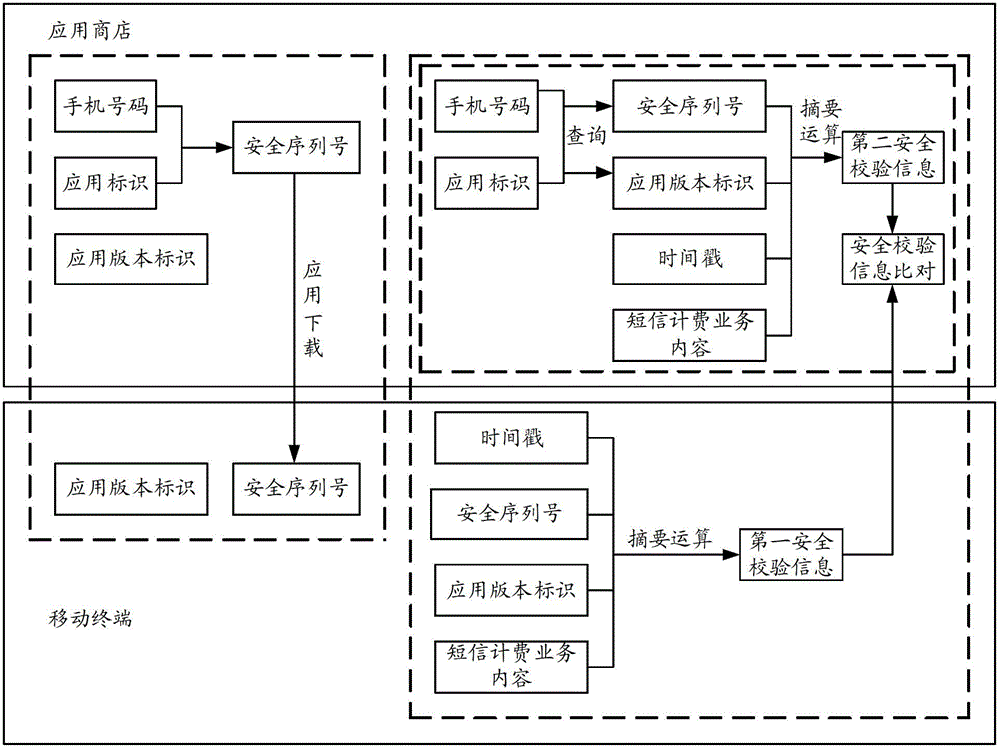
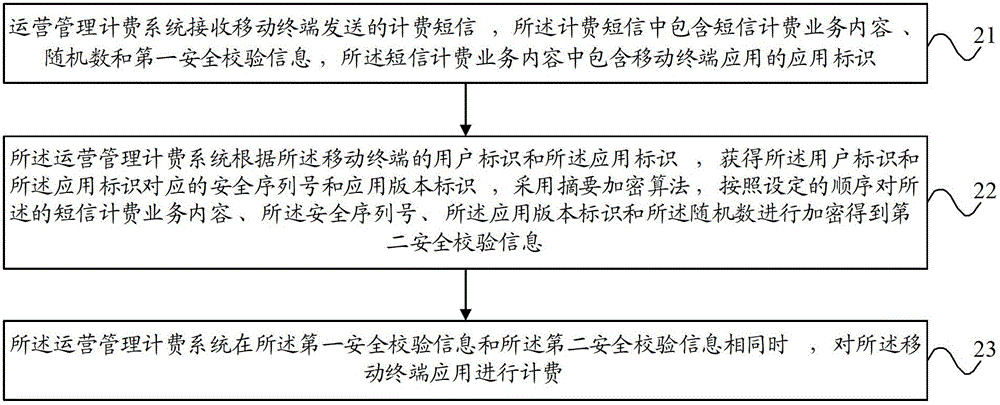
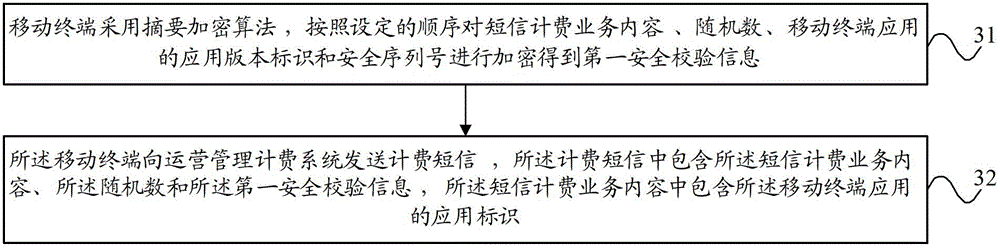
[0033] In order to solve the problem that the charging security of in-app short messages cannot be guaranteed in the prior art, the embodiment of the present invention will include security verification information in the billing short messages, and the application store will generate security verification information according to the remaining information in the billing short messages , in order to distinguish, the security verification information contained in the billing SMS can be called the first security verification information, and the security verification information generated by the app store can be called the second security verification information. By comparing the first security verification information verification information and second security verification information to verify security.
[0034] figure 1 It is a schematic diagram of the mapping relationship and process of security check information generation in the embodiment of the present invention. see...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com