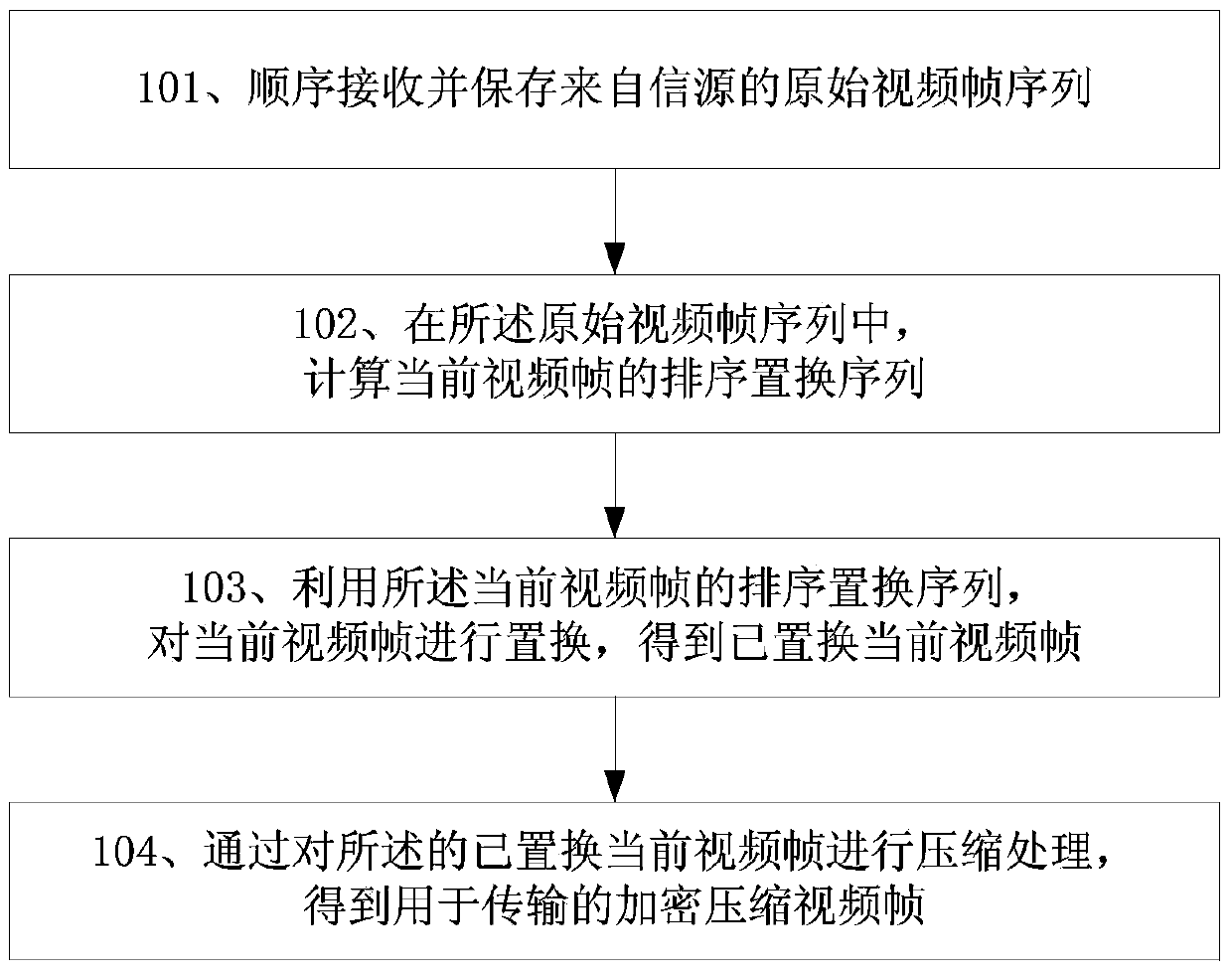
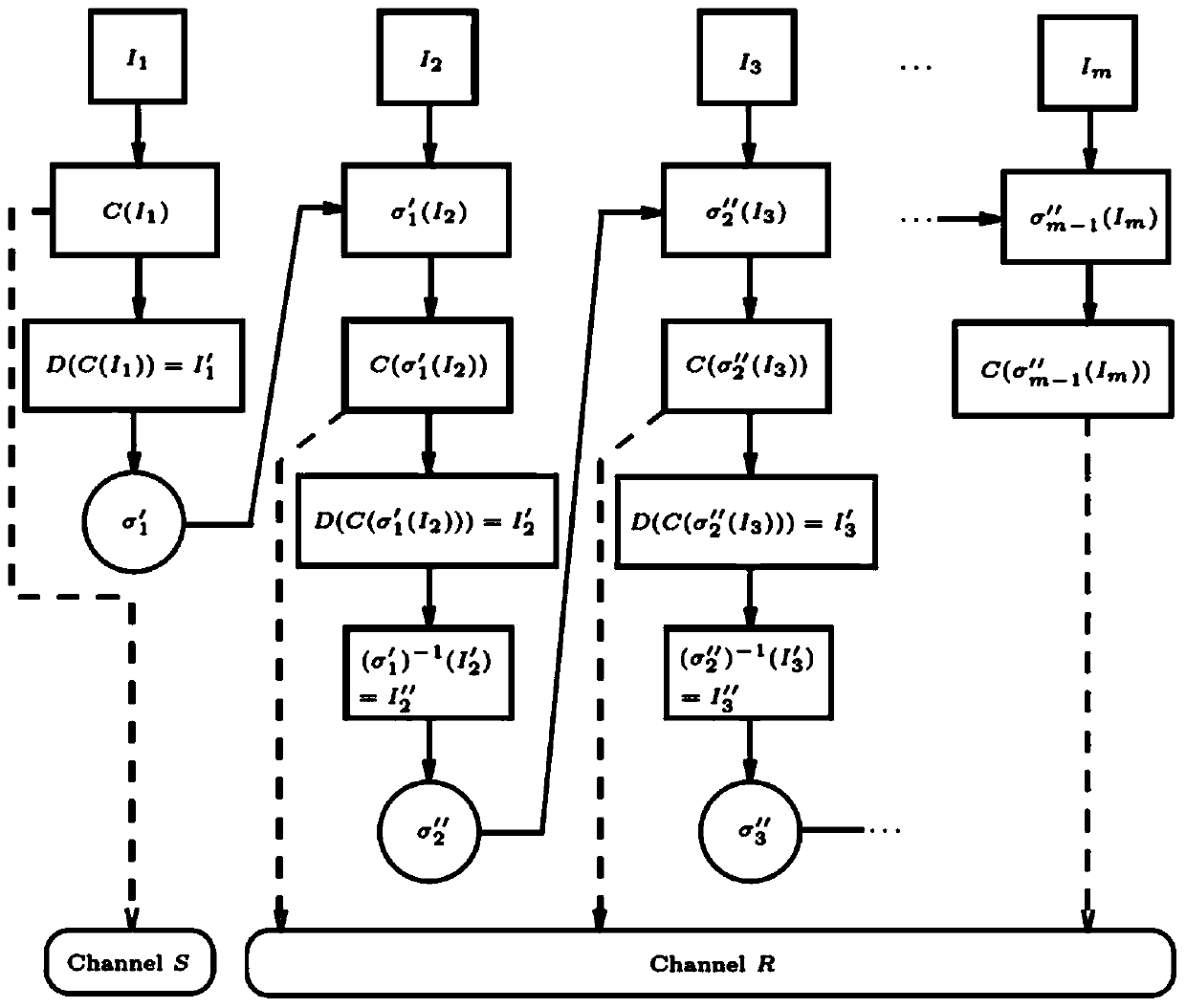
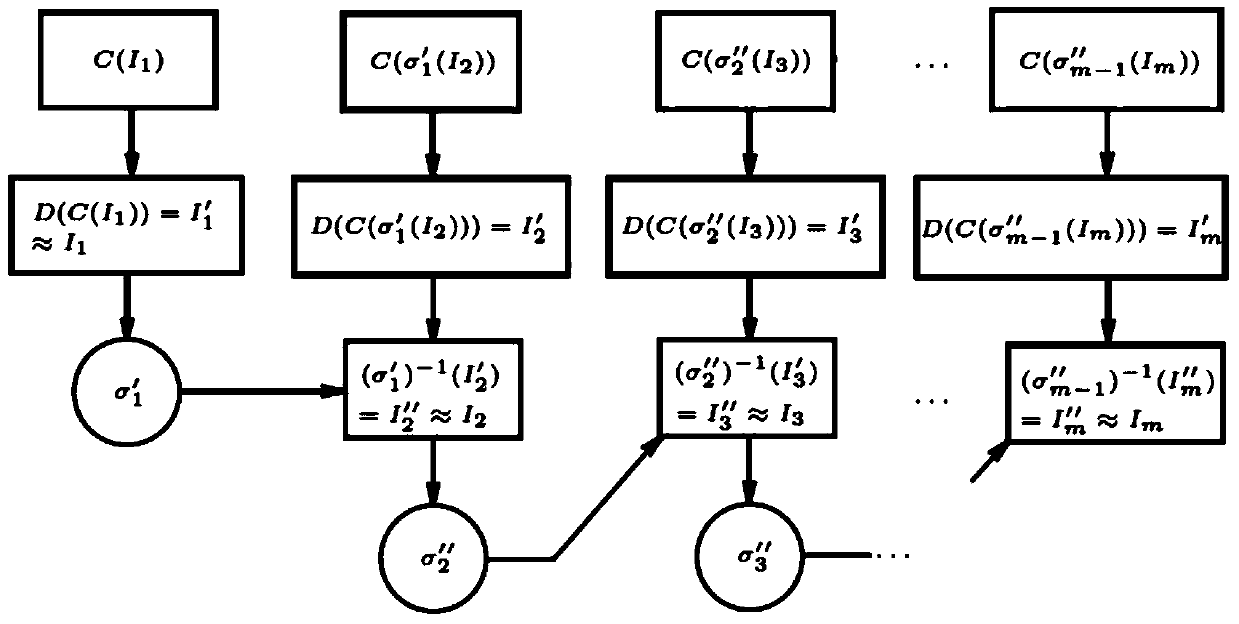
Low-bit-rate H.264 video encryption compression transmission method based on ranking permutation
An encryption compression and transmission method technology, applied in the field of video security transmission, can solve the problem of low bit rate security transmission of video images, and achieve the effect of maintaining spatial correlation, increasing or improving the compression ratio and constant bit rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
[0170] Figure 6 It is the image block provided by the embodiment of the present invention to improve the efficiency of the transformation-based encoder. The recursive sorting algorithm is used to perform the entire image raster scanning sequence and the 8×8 image block complete sorting on the 256×256 grayscale image Lena before proceeding. JPEG compression (compression quality factor is set to 50), the obtained image size is as follows Figure 6 shown. Figure 6 (a) 256×256 grayscale image Lena[JPEG=6.95KB], Figure 6 (b) Lena [JPGE=1.81KB] sorted image in raster scan order, Figure 6 (c) Fully sorted image Lena [JPEG=1.09KB] with 8×8 tiles.
[0171] From Figure 6 It can be seen that the correlation of the image is improved after sorting, and the size of the JPEG compressed data becomes smaller; and the 8×8 block is used to sort the image in the block, because the image is processed according to the encoding block size of the encoder. , which is more suitable for JPEG e...
specific Embodiment 2
[0172] Figure 7 It is the processing result of the 150th frame of the sequence Akiyo provided by the embodiment of the present invention. The encryption algorithm based on sorting and permutation is respectively embedded in the H.264 video sequence codec to conduct experiments on the sequence Akiyo, and at the same time, the basic encryption compression transmission model is also carried out. After histogram hiding and image block expansion, the processing results are as follows Figure 7 shown. Figure 7 (a) original frame image, Figure 7 (b) H.264 encodes the basic encryption algorithm to directly decode the image, Figure 7 (c) Unencrypted decoded image, Figure 7 (d) H.264 encodes the basic encryption algorithm to decode and decrypt the image after processing, Figure 7 (e) and Figure 7 (f) The image is directly decoded after being processed by the block-based H.264 encoding and encryption method (the block sizes are 32×32 and 8×8 respectively), Figure 7 (g) H.26...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com