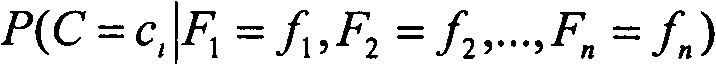Anomaly detection device and method for security information interaction
A security information and anomaly detection technology, applied in the field of anomaly detection devices, can solve the problems of high false alarm rate and false negative rate, inappropriate feature selection, and inability to detect local anomalies well, achieving high security and low Effect of False Positive and False Negative Rates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
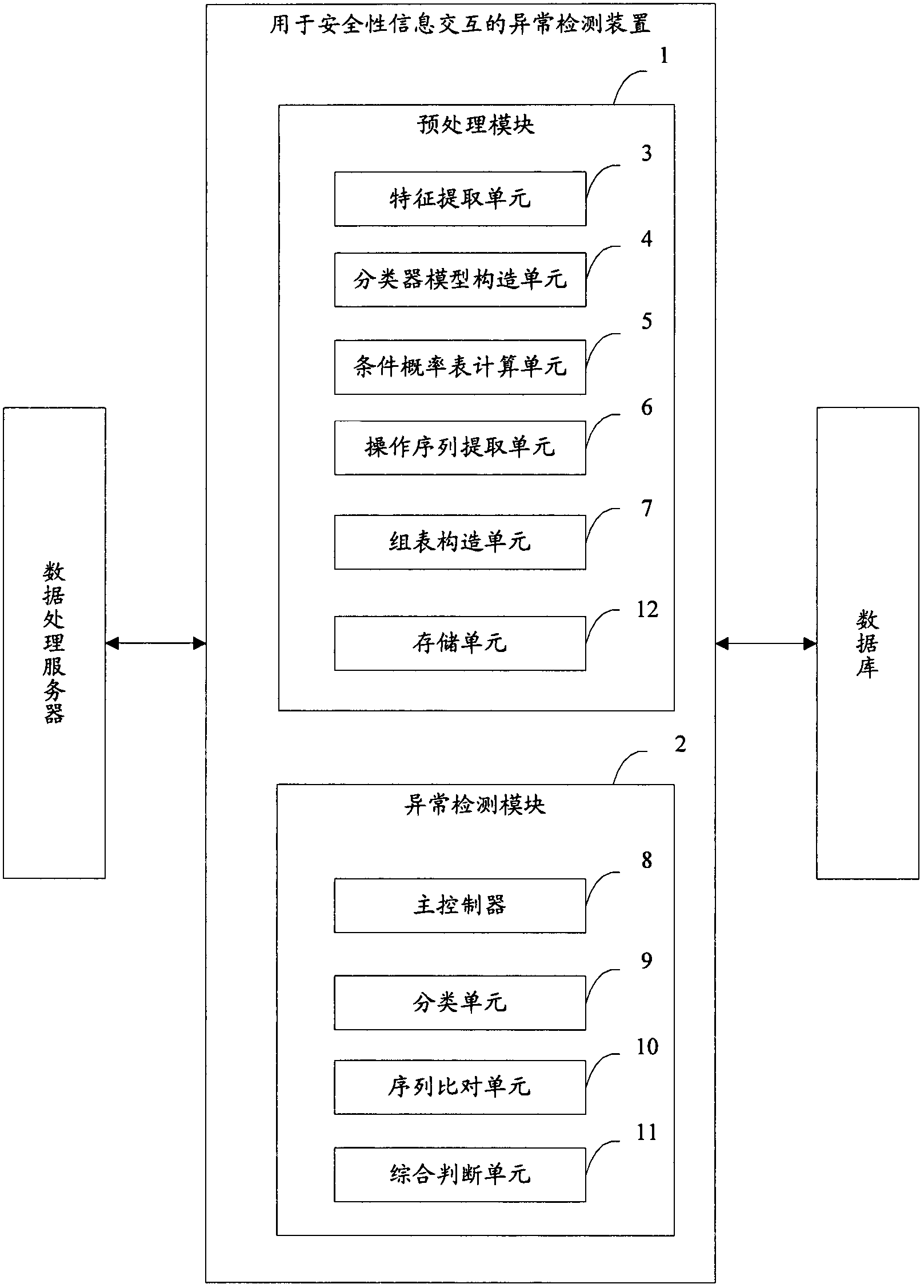
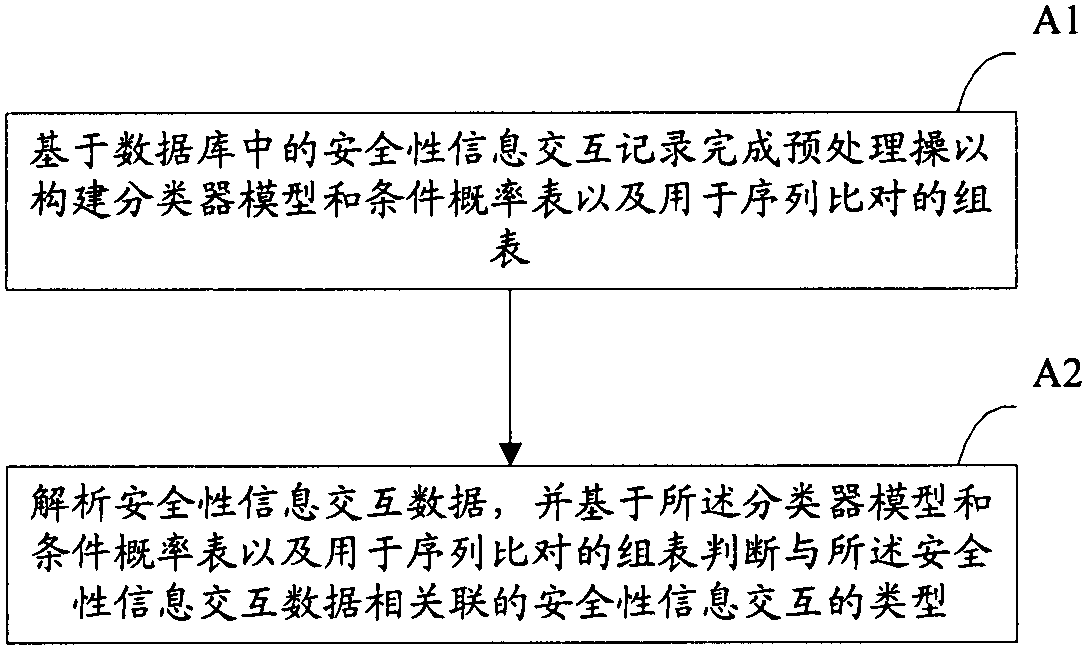
[0042] figure 1 is a schematic structural diagram of an anomaly detection device for security information interaction according to an embodiment of the present invention. like figure 1 As shown, the anomaly detection device disclosed in the present invention includes a preprocessing module 1 and an anomaly detection module 2 . Wherein, the preprocessing module 1 is used to complete the preprocessing operation based on the safety information interaction records in the database to construct a classifier model, a conditional probability table and a group table for sequence comparison. The anomaly detection module 2 is used to receive and analyze the security information interaction data from a data processing server (such as a transaction processing server), and judge and determine the difference based on the classifier model, conditional probability table and group table used for sequence comparison. The type of security information interaction (such as financial transaction) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com