Method for achieving user authentication by utilizing camera
An identity verification and camera technology, applied in the fields of digital data authentication, character and pattern recognition, deception detection, etc., can solve the problems of loss, theft, easy forgetting, etc., to improve security, ensure picture quality, improve reliability and The effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
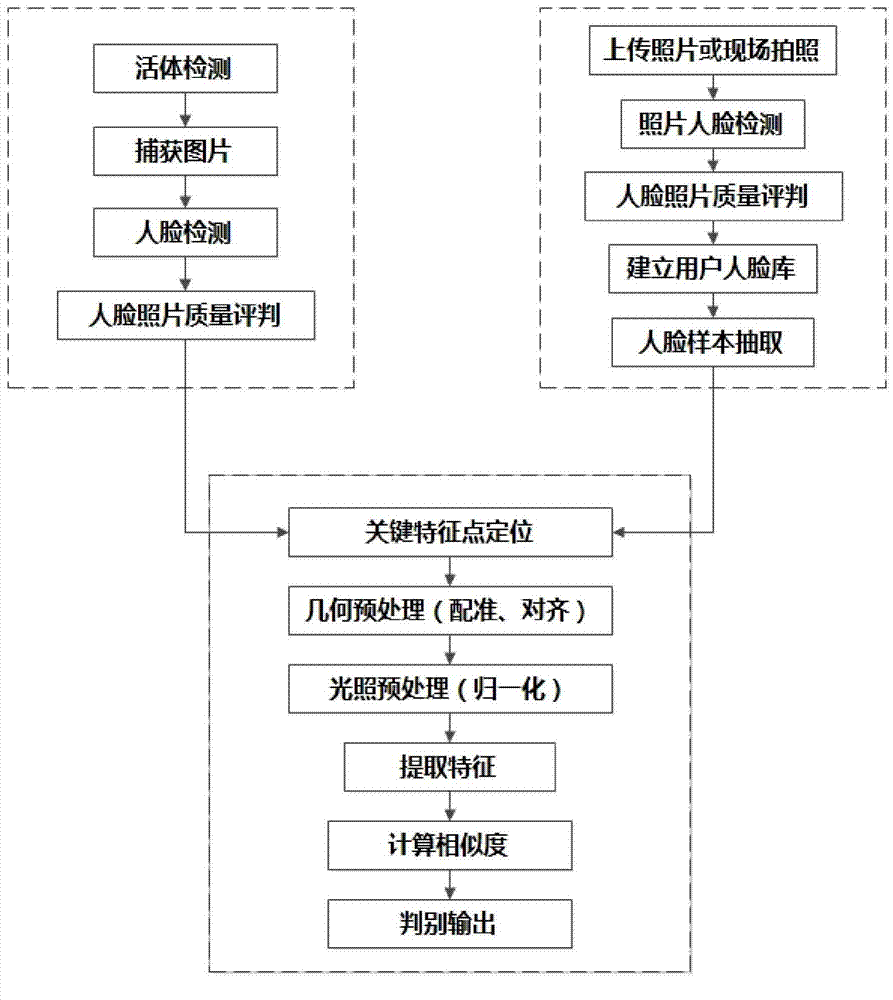
Image
Examples
Embodiment 1
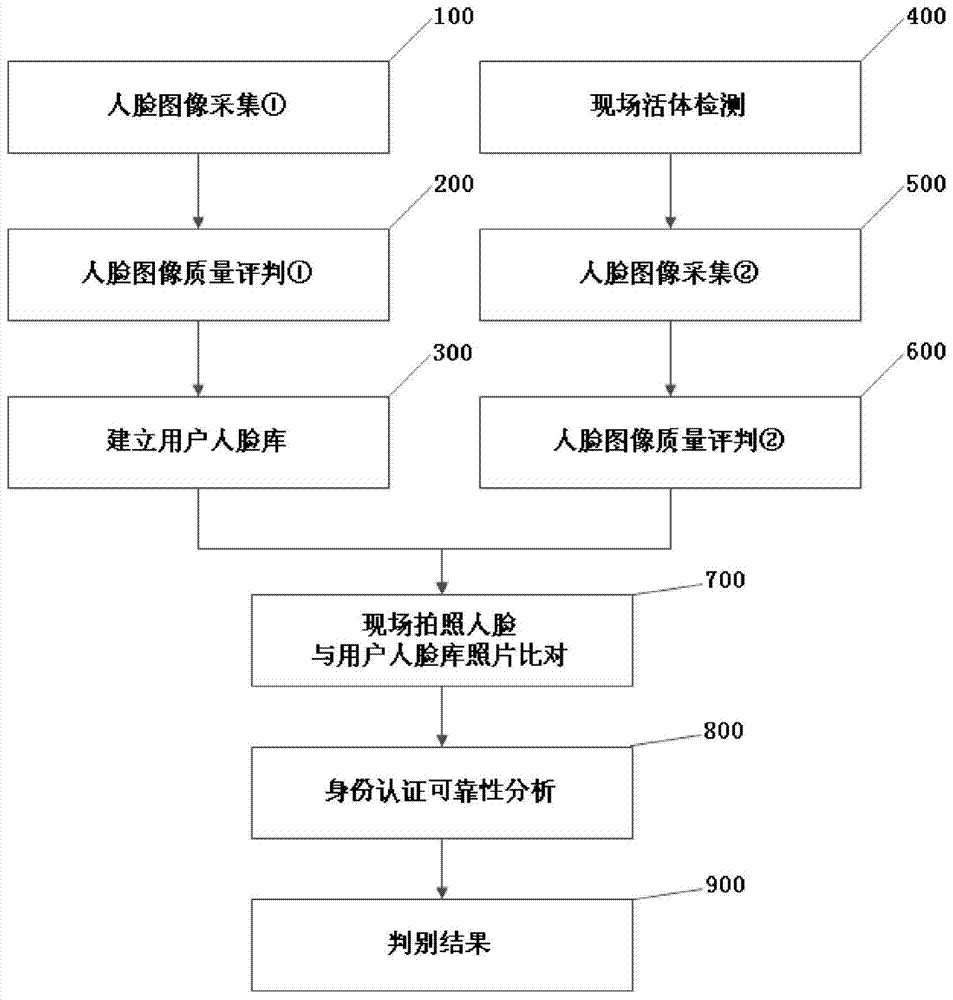
[0036] Such as figure 1 As shown, a method for using a camera to implement identity verification described in this embodiment includes the following steps:
[0037] S100: Pre-collect the user's face image.
[0038] There are two methods of image collection: one is to use the camera to take pictures on the spot, and the other is to use the system photo upload function to upload electronic photos with the user's front profile picture.
[0039] S200: Carry out face image quality evaluation on the image collected in step S100.
[0040] The function of image quality evaluation is to judge the quality of face imaging. The quality of face image will directly affect the accuracy and reliability of the identity verification system. Therefore, before establishing the face image database for identity verification, it is necessary to The image quality of the face image obtained by taking the photo and the uploaded photo is judged, including the following judging elements:
[0041] (1) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com