Device and method for preventing user interface from being hijacked
A user interface and user technology, applied in computer security devices, data processing input/output processes, instruments, etc., can solve problems such as user mobile phone security threats, and achieve the effect of preventing losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The following descriptions of the various embodiments refer to the accompanying drawings to illustrate specific embodiments in which the present invention can be practiced.
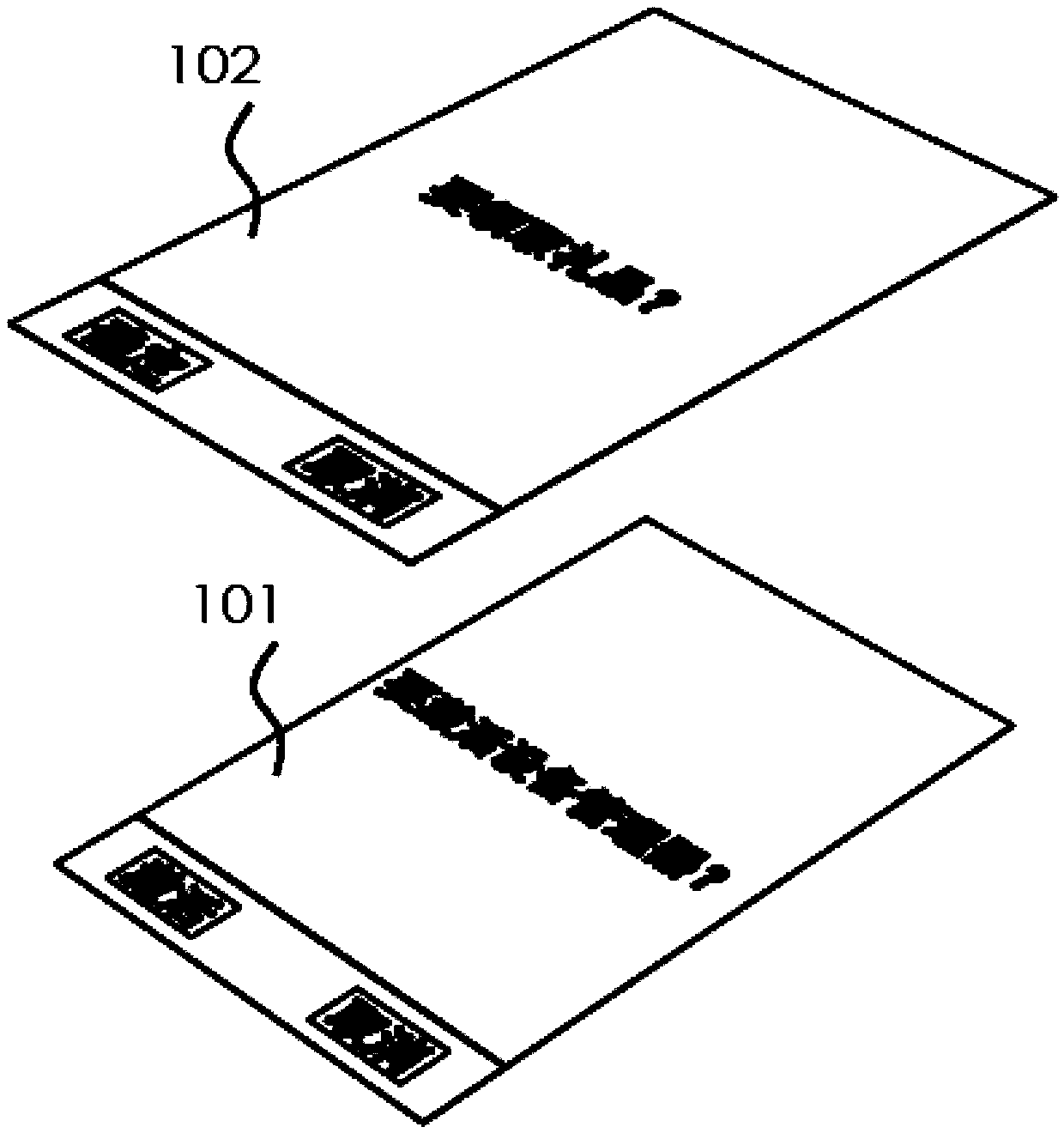
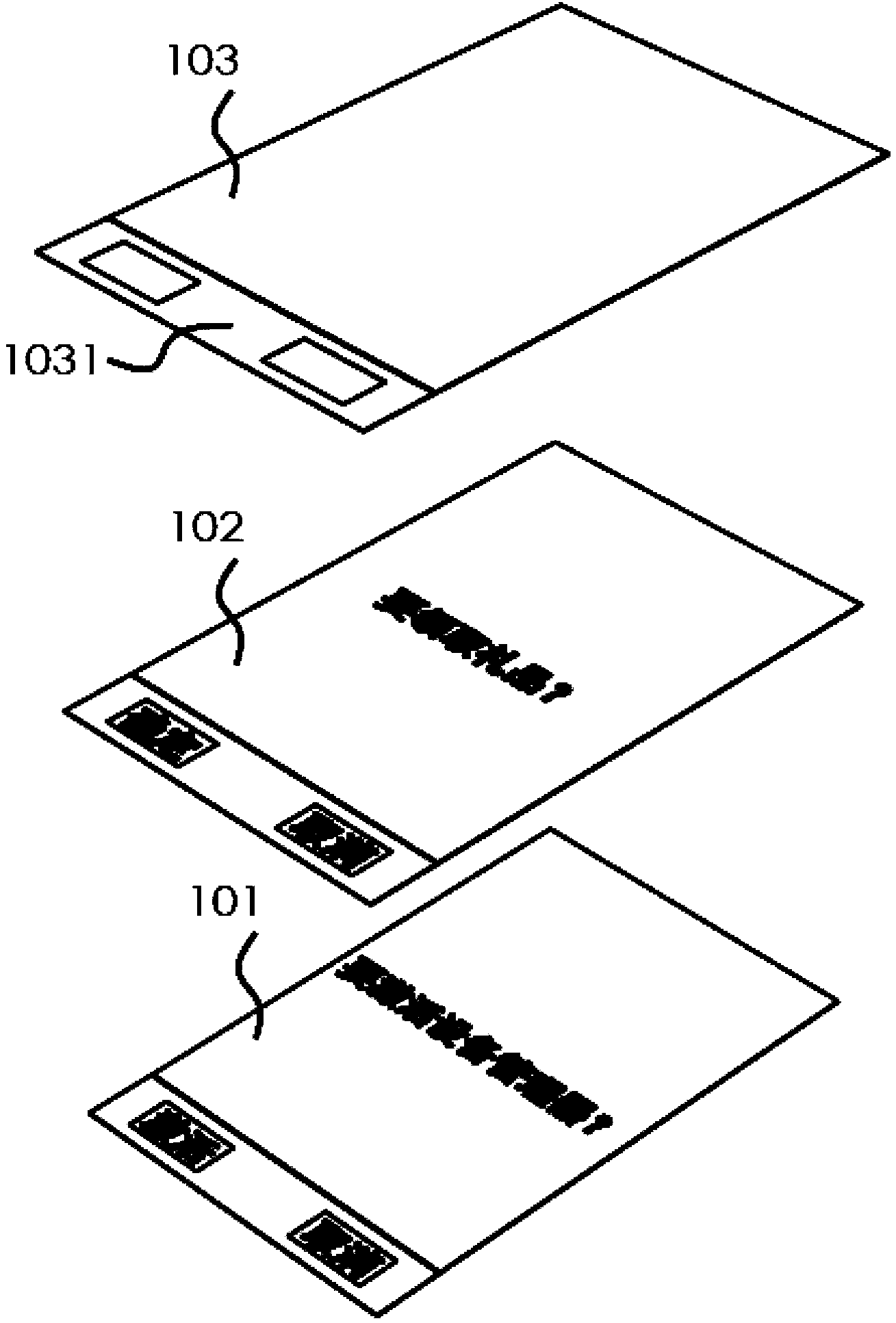
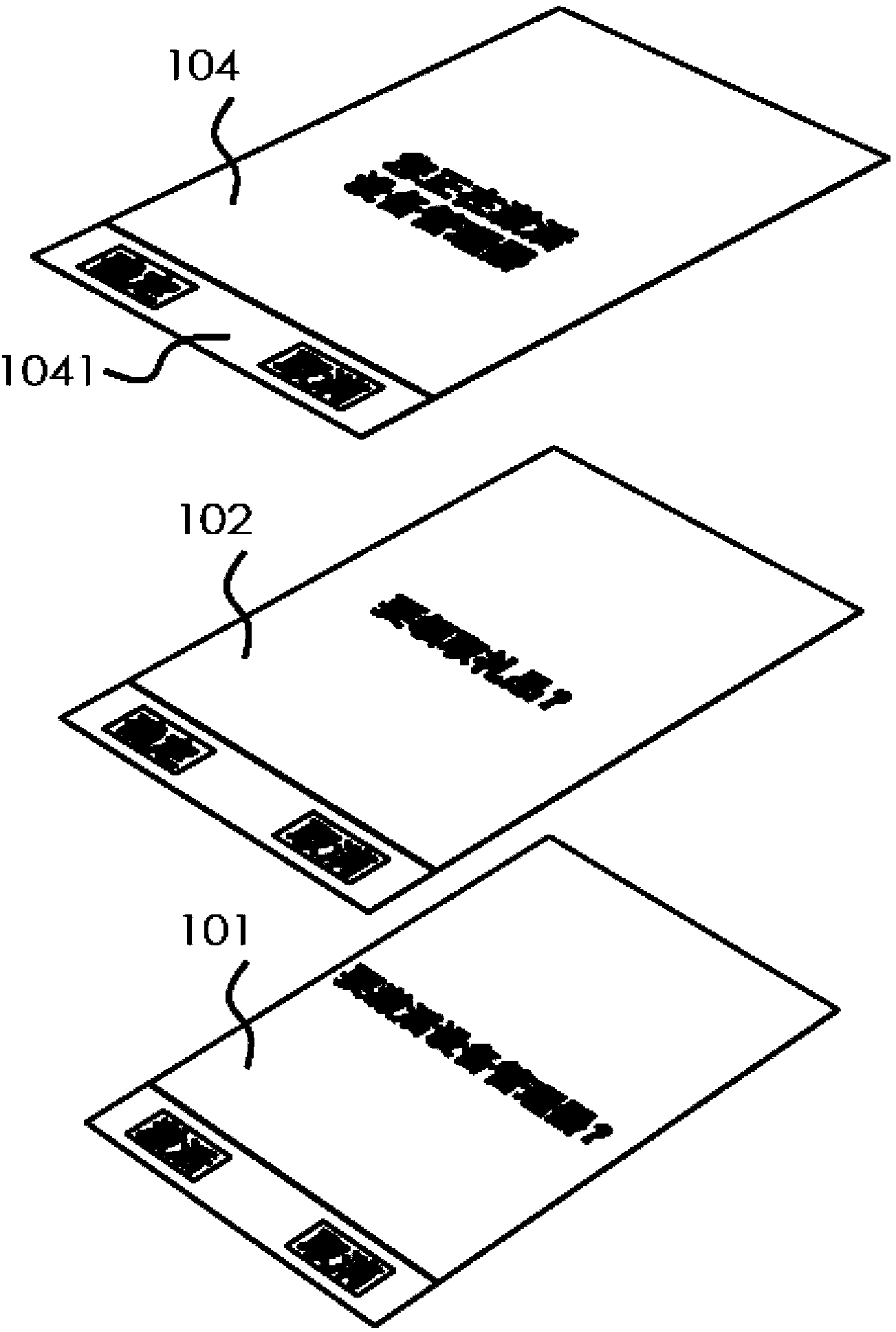
[0028] refer to Figure 1A , Figure 1B and Figure 1C , Figure 1A , 1B and 1C are schematic diagrams of the method of preventing user interface from being hijacked in the present invention. exist Figure 1A , the virus generates a floating window 102 to hijack the user interface of the user device (the user interface at this time is the activation control interface 101 of the device manager), and the user induces the user to click the corresponding button on the floating window 102 in a deceptive manner. exist Figure 1B Among them, the present invention constructs a first window 103 when it is found that a specific interface of the user equipment is invoked, the first window 103 has a first operation area 1031, the background of the first window 103 is transparent or translucent, when the use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com