An authorization method for offline power trading information system based on rsa public key cryptography
A technology of power information and public key cryptography, which is applied in the transmission system, public key of secure communication, electrical components, etc. It can solve the problems of large security risks, vulnerability to attacks, and low password complexity, and achieves easy implementation and easy The effect of the operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
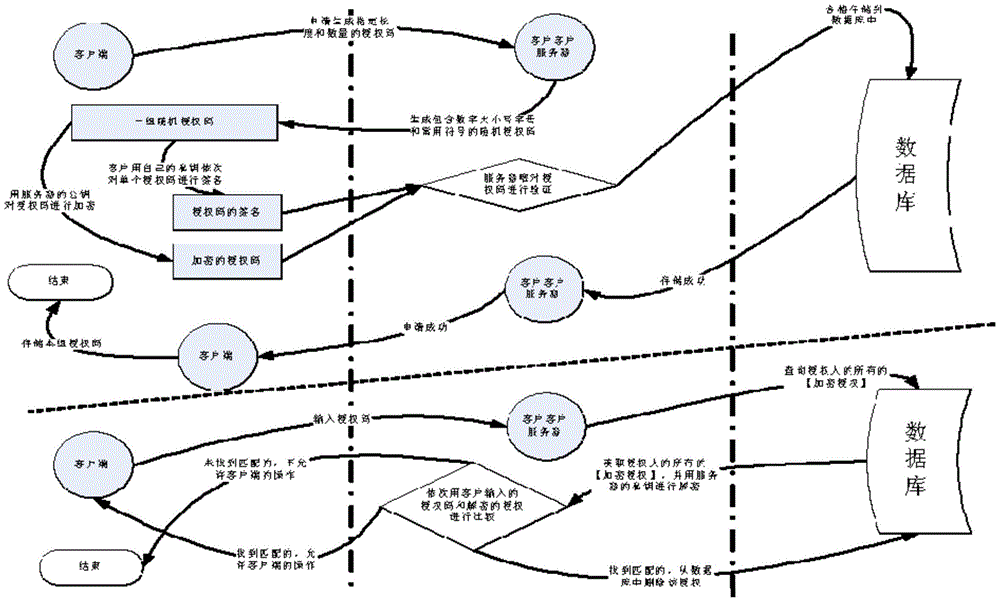
[0043] Take the confirmation transaction in electricity transaction as an example:
[0044]After the power transaction declaration of a power generation company is approved, the person in charge of the power generation company A must confirm it. At this time, the person in charge A cannot confirm it in person due to special circumstances, and the trader B of the power generation company has no authority to confirm the transaction. Time is running out. If the transaction cannot be confirmed in time, the power generation company may not be able to complete the transaction and must wait until the next transaction, which will bring greater losses to the power generation company. At this time, only person in charge A can remotely authorize trader B to complete the transaction.
[0045] The person applying for authorization is trader B. After logging into the power trading management system, B submits an application for confirmation of the transaction. The system requires A to autho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com