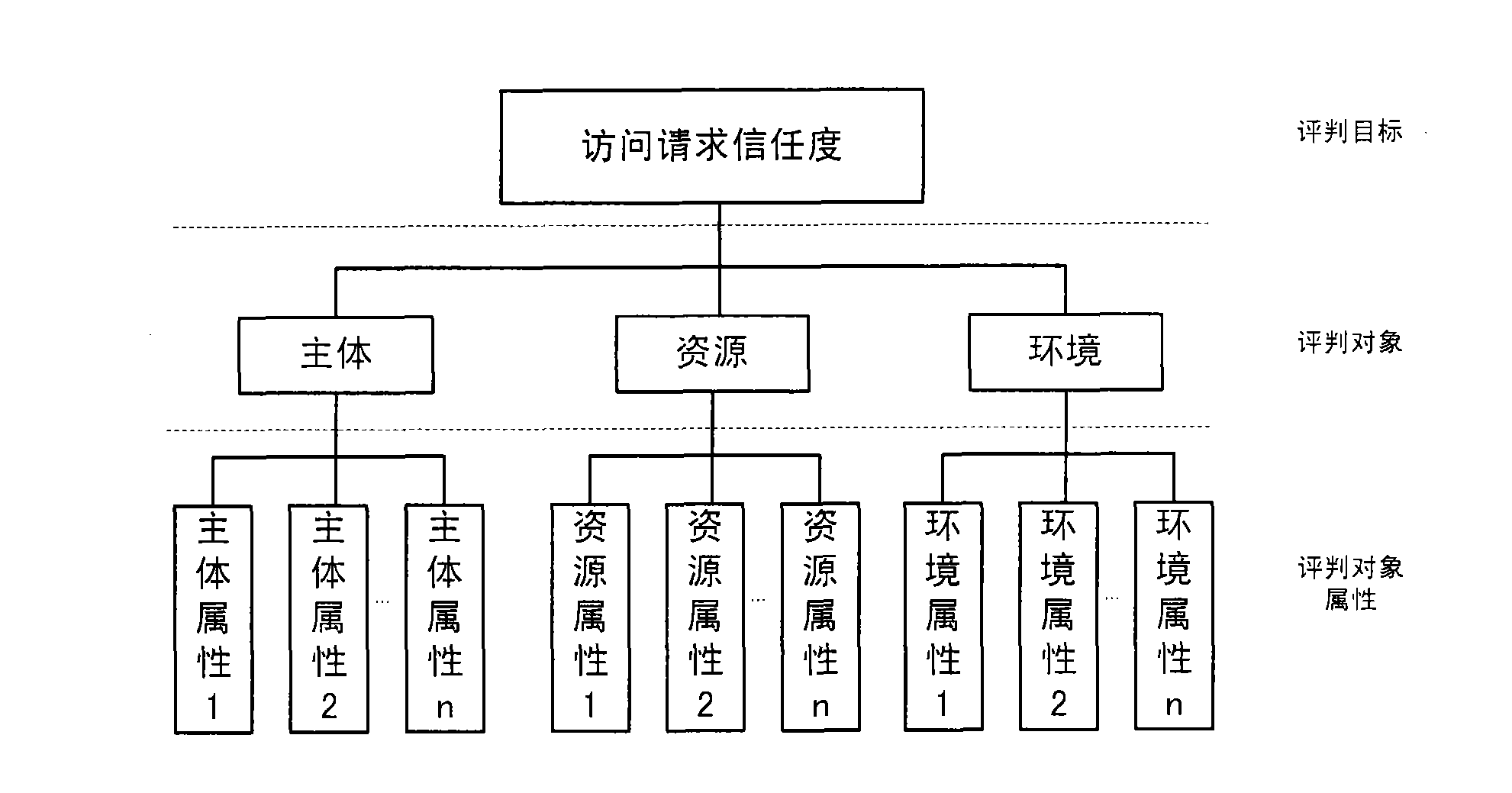
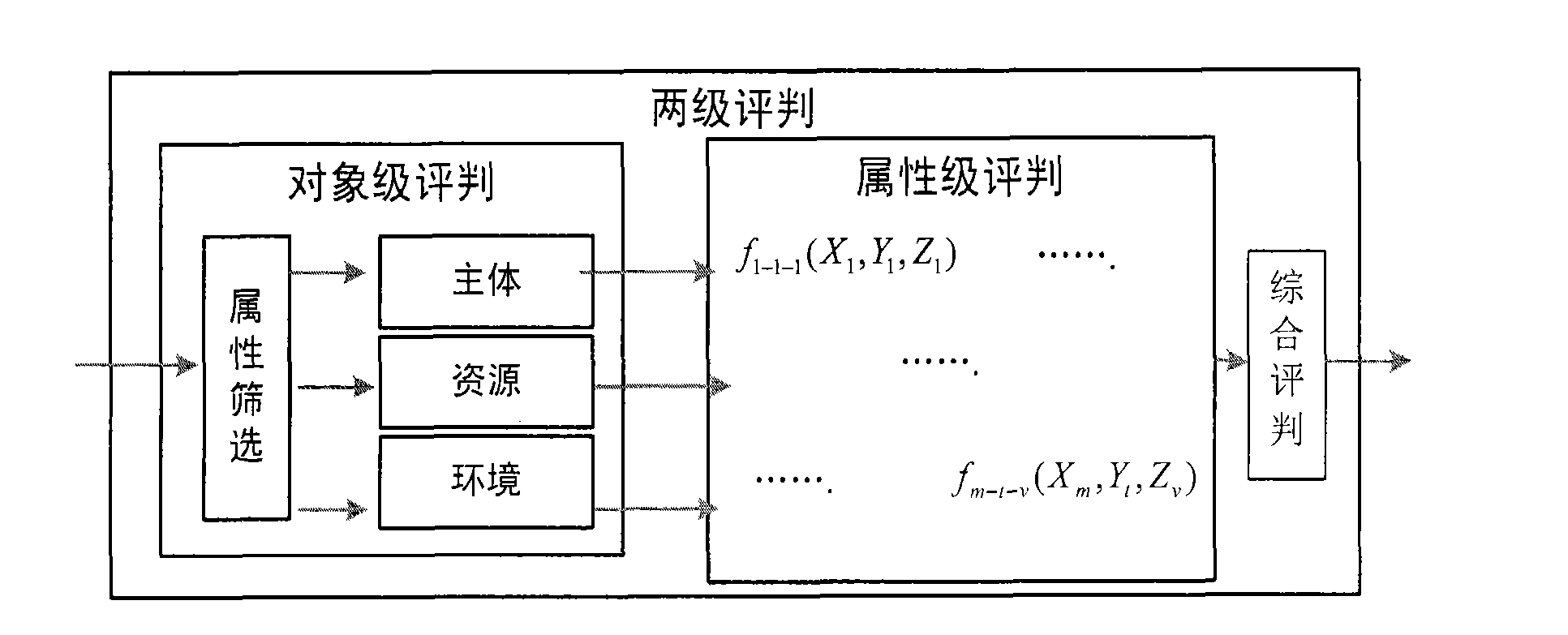
Attribute-based fuzzy access control calculation method
An access control and access controller technology, applied in the field of network security, can solve the problems such as affecting the authorization speed, the precise matching model cannot be dynamically adjusted, etc., to achieve the effect of improving the completeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The preferred embodiments will be described in detail below in conjunction with the flow charts. It should be emphasized that the following descriptions are only illustrative, not intended to limit the scope of the present invention and its application.
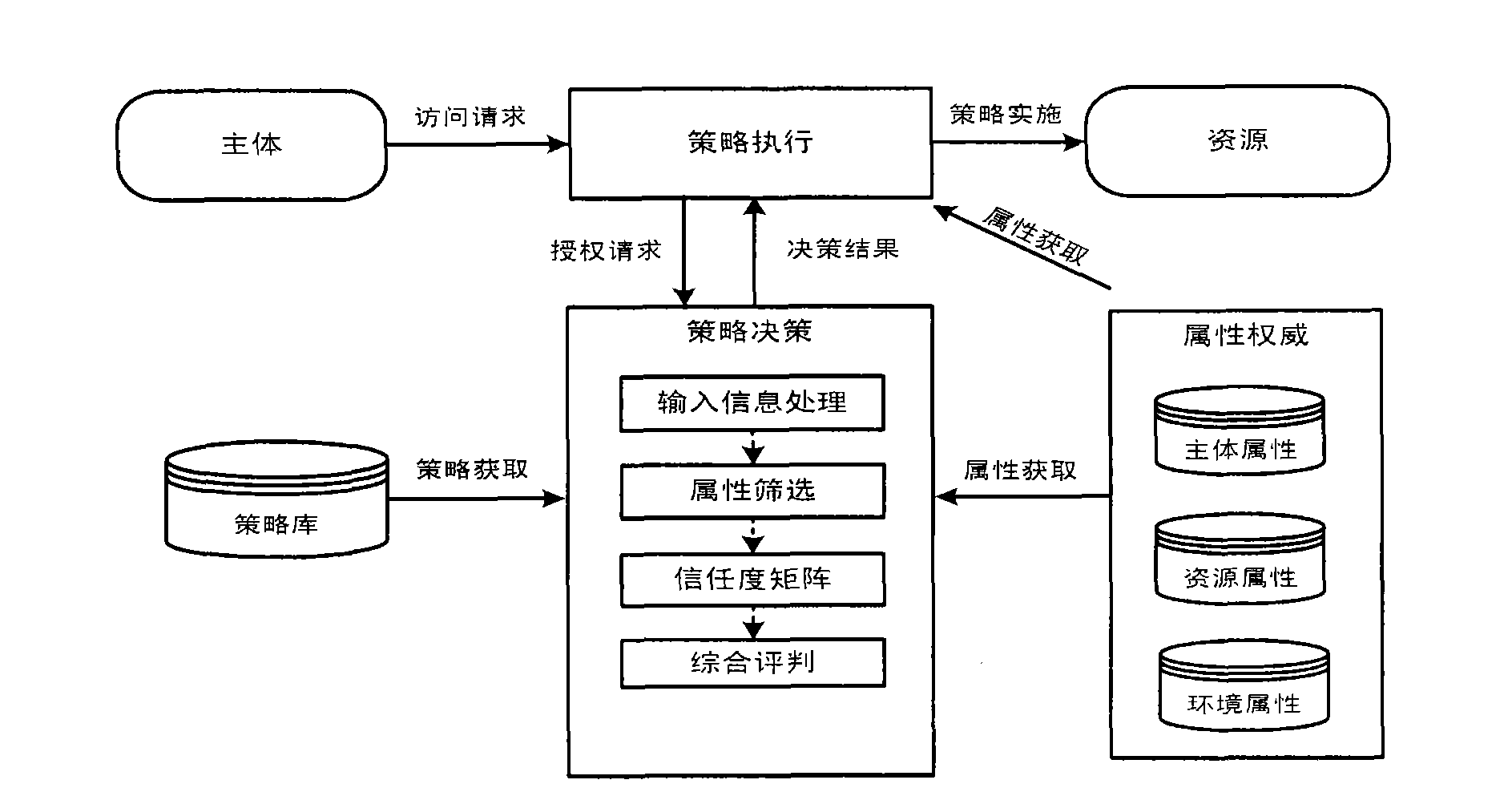
[0047] Step 1: The policy execution module is responsible for parsing the user's access request, extracting the subject attributes, and sending the authorization request and subject attributes to the policy decision module. The policy enforcement module can be distributed in multiple locations in the entire network environment, and the request subject cannot bypass the policy enforcement module and directly access resources.
[0048] Step 2: The strategy decision module makes a fuzzy strategy decision, and the specific steps are as follows:
[0049] Step 1): Input information processing.
[0050] Since some access request information and policy information are not in numerical form, data format conversion is required....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com