Verification information pushing method and device, and identity authentication method and device
A technology for verifying information and identity authentication, which is applied in the fields of methods and devices for pushing verification information, methods and systems for identity authentication, and can solve the problems of easy eavesdropping of short message interfaces and security loopholes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
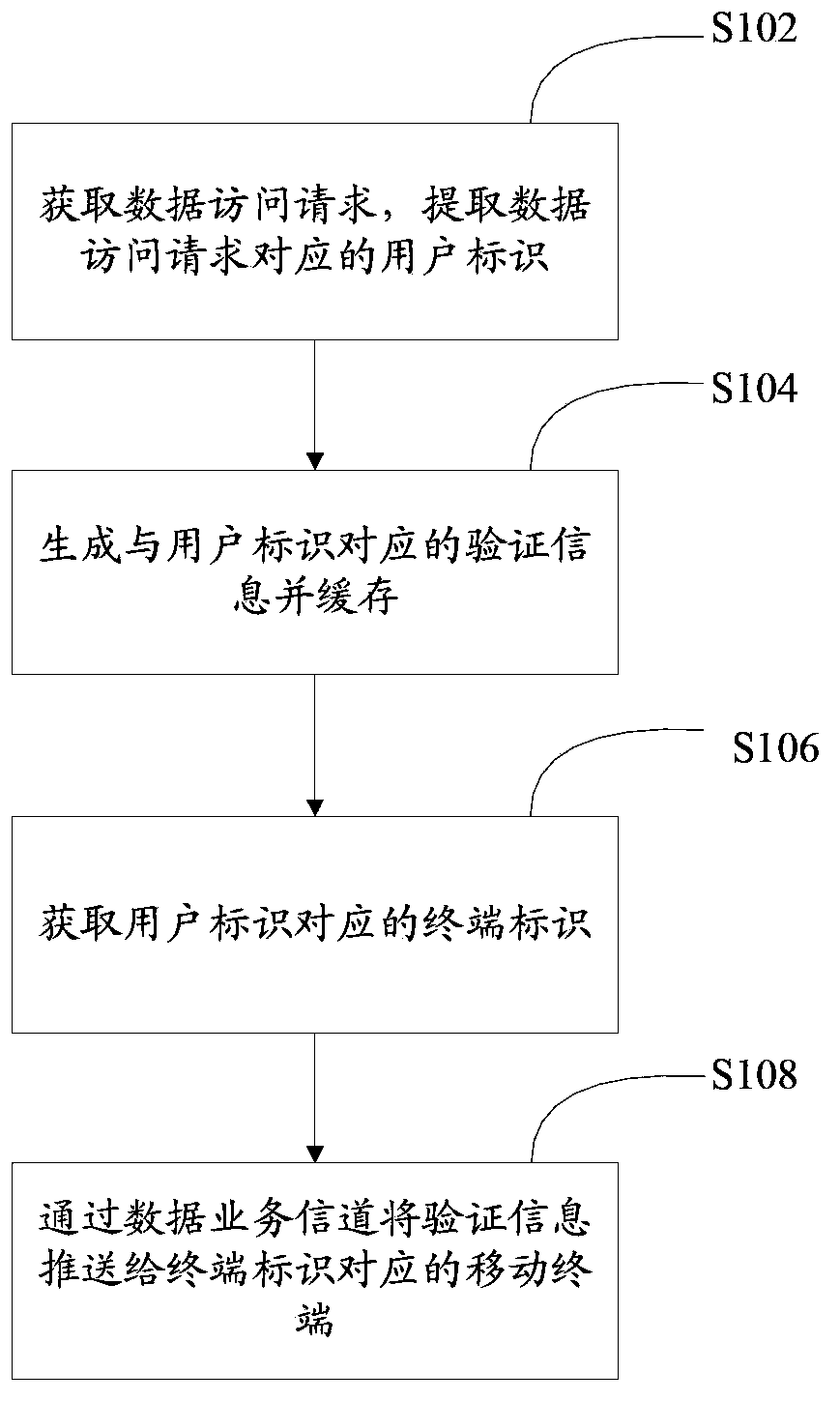
[0054] In one embodiment, such as figure 1 As shown, a verification information push method includes:
[0055] Step S102, acquiring a data access request, and extracting a user identifier corresponding to the data access request.
[0056] A data access request is a request initiated by a terminal device to perform data read and write operations on data on the server. For example, if a user wants to modify their personal information, they can initiate a data access request and add the modified personal information to the request; if a user wants to transfer money through online banking, the data request can include the transfer amount, transfer account number, etc. and other information.
[0057] The terminal device that initiates the data access request may be a personal computer, a smart terminal, a mobile terminal, and the like. User IDs are included in data access requests to distinguish different users.
[0058] Step S104, generating and caching verification informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com