Secure recovery apparatus and method
A safe and secure boot technology, applied in the direction of program control devices, instruments, error detection/correction, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
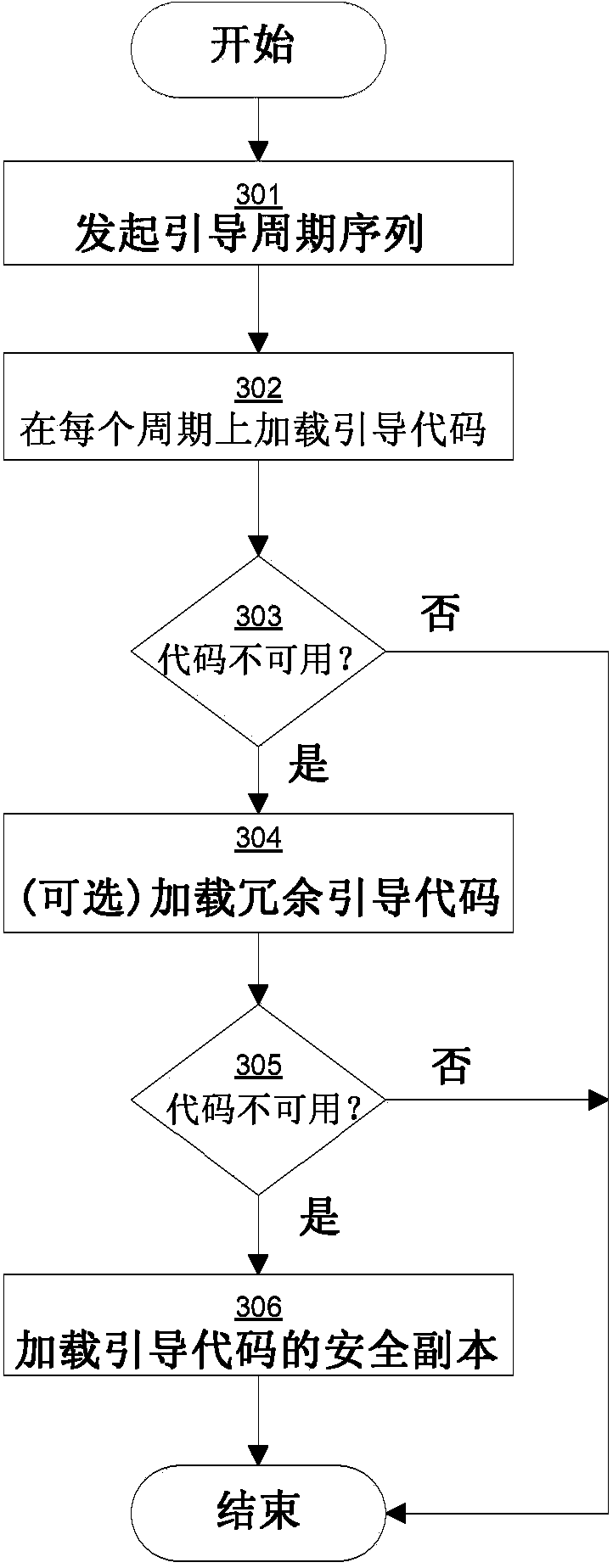
[0016] Modern computers can include various backup and recovery mechanisms. Due to data corruption (eg, due to malware or hardware failure), it may be desirable to replace or repair an image of the firmware or operating system on a bootable hard disk or other storage mechanism. However, restoring an image using a restore image can also be complex, if not a difficult process, and the restore image itself can also be prone to data corruption. Therefore, restoration of a corrupted image may inevitably require the intervention of computer technicians at considerable cost. The subject technology provides a secure bank of data that users can turn to when all else fails, alleviating the need for user or computer technician intervention.
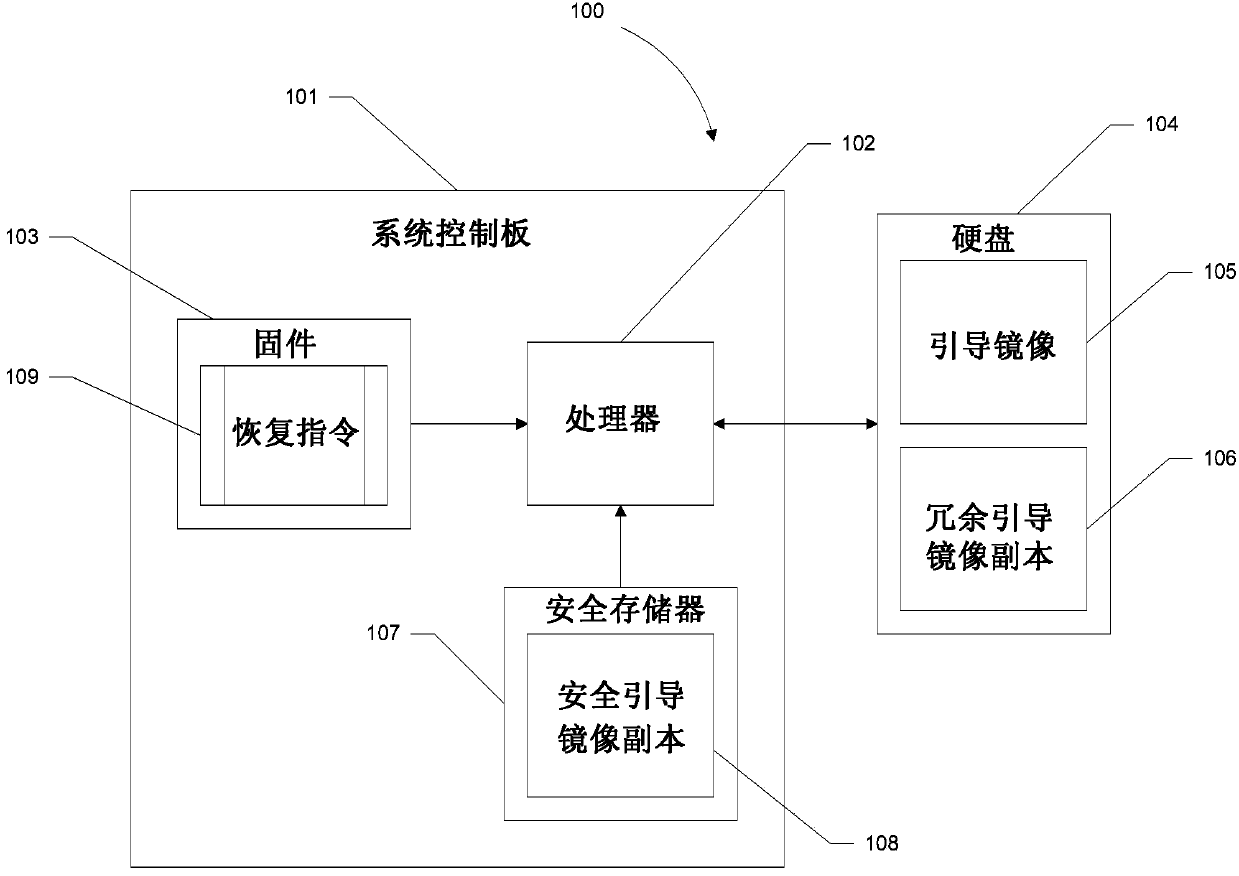
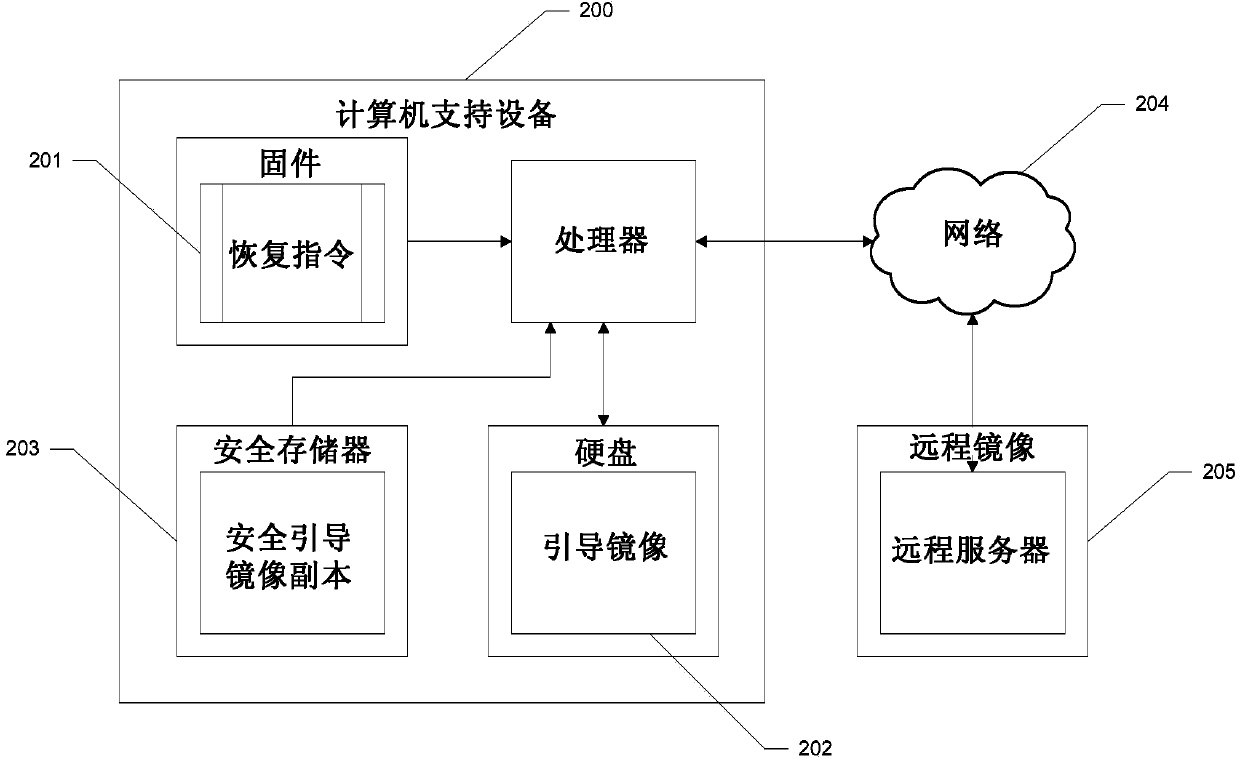
[0017] figure 1 is an exemplary diagram of an apparatus and system for loading a boot image including firmware and secure memory locations in accordance with one aspect of the subject technology. According to one aspect, computer system 100 may i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com