Patents
Literature
39 results about "Secure copy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Secure copy protocol (SCP) is a means of securely transferring computer files between a local host and a remote host or between two remote hosts. It is based on the Secure Shell (SSH) protocol. "SCP" commonly refers to both the Secure Copy Protocol and the program itself. According to OpenSSH developers in April 2019 the scp protocol is outdated, inflexible and not readily fixed.
Circuit chip for cryptographic processing having a secure interface to an external memory
InactiveUS20060059369A1Improve process capabilityInhibit involvementUser identity/authority verificationUnauthorized memory use protectionInternal memoryStatic random-access memory
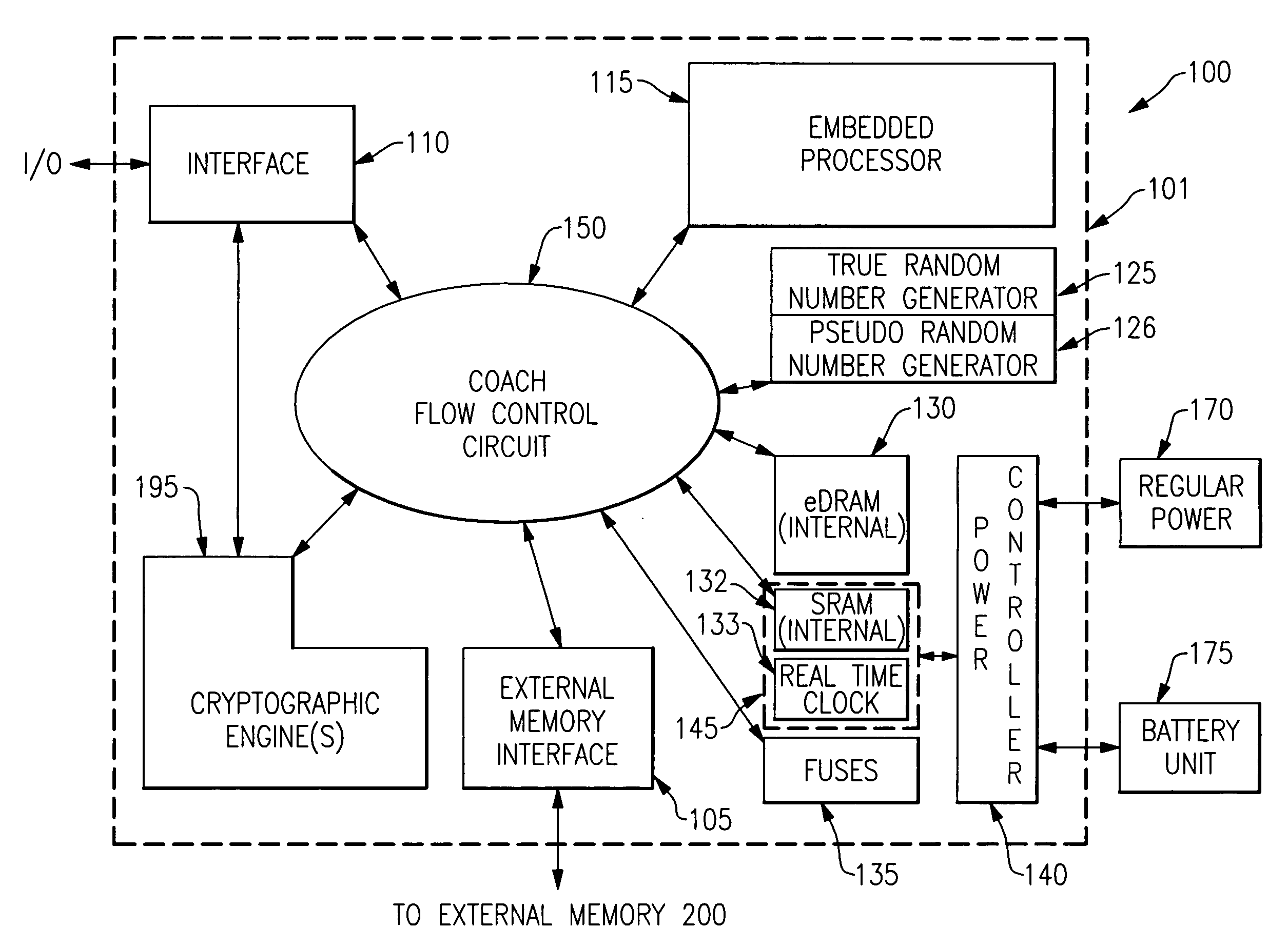
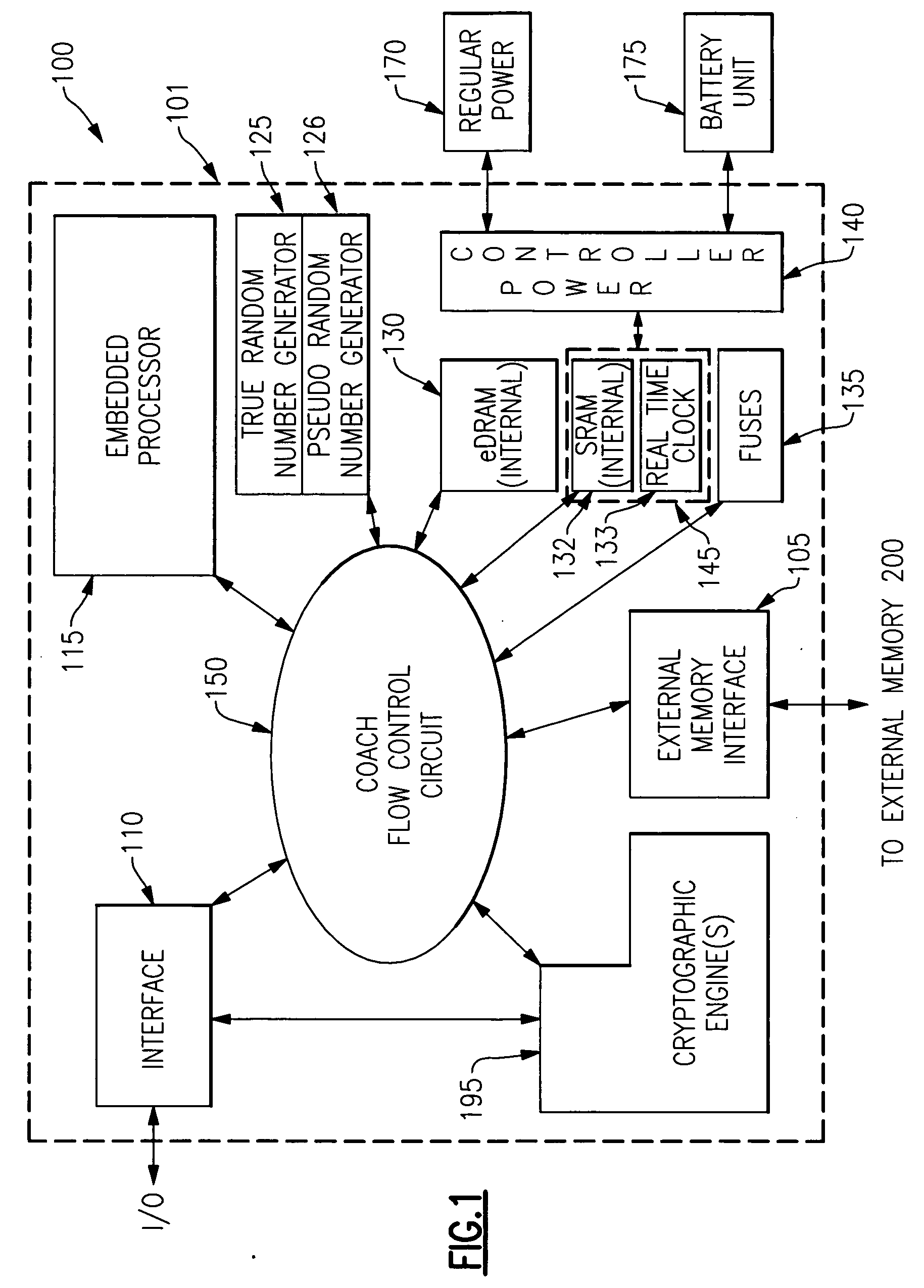
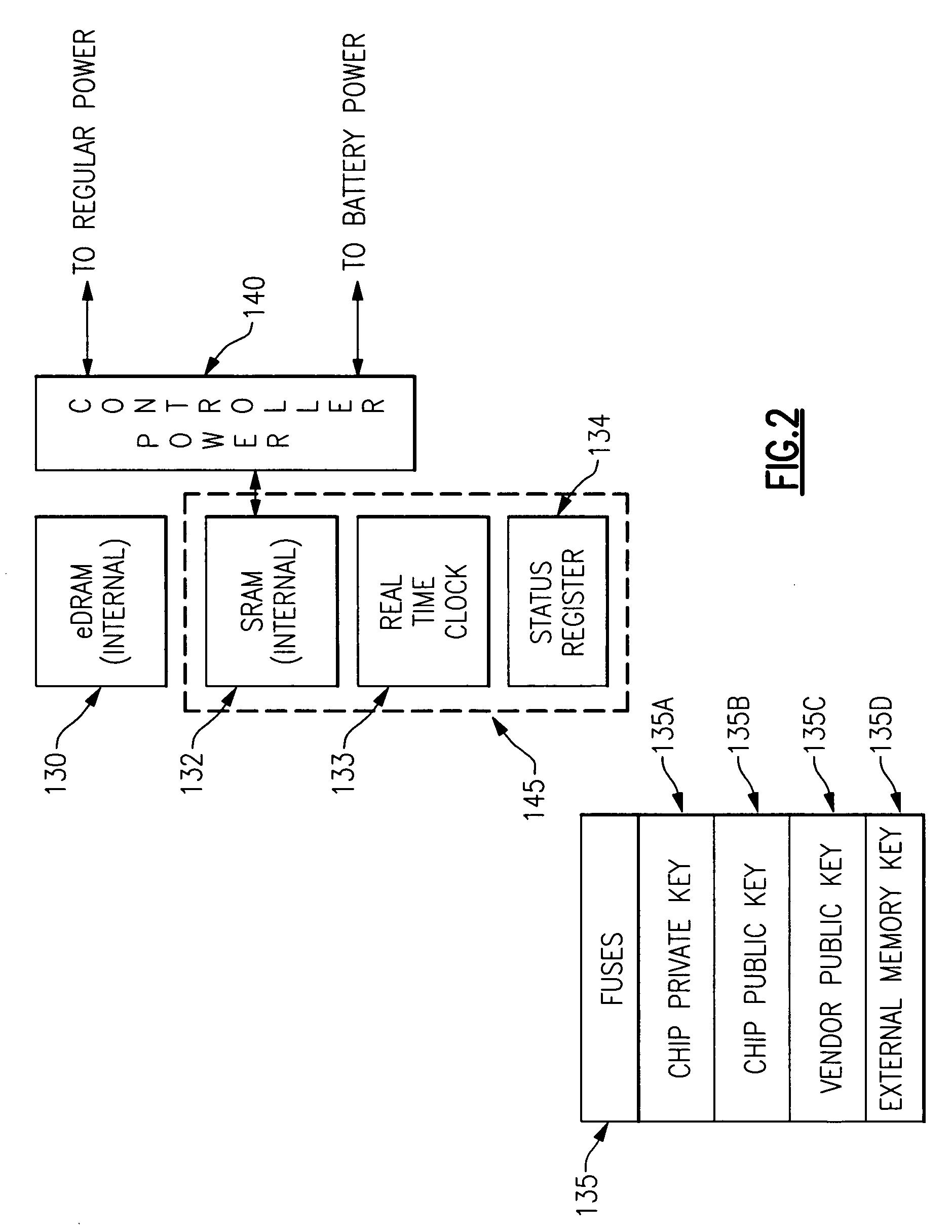
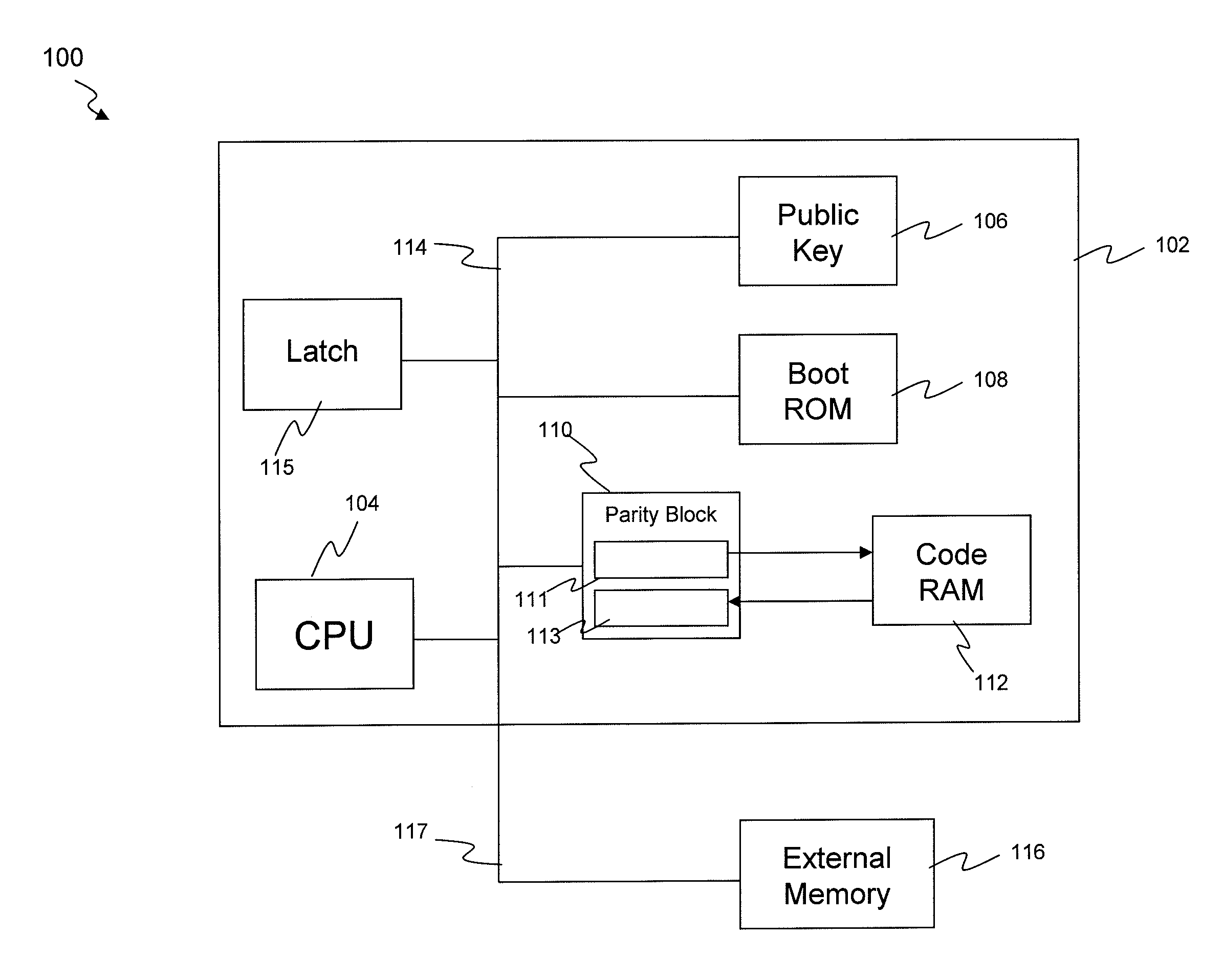
A mechanism is provided in which a secure chip for performing cryptographic and / or other functions is able to securely access a separate random access memory externally disposed with respect to a secure chip boundary. Addressing of the external memory is controlled so as to define certain regions therein which receive and store only encrypted information from the chip. Other regions of the external memory are set aside for the receipt and storage of unencrypted information. Access to the external memory is provided through a controlled interface which communicates with internal chip hardware which operates to control the flow of communication between various internal components such as cryptographic engines, data processors, internal memory of both the volatile and the nonvolatile variety and an external interface which provides the only other access to the chip. The internal chip hardware with which the external memory interface communicates is implemented as a combined ASIC and programmable hardware circuit, wherein the programmable hardware circuit is also securely configurable.
Owner:IBM CORP
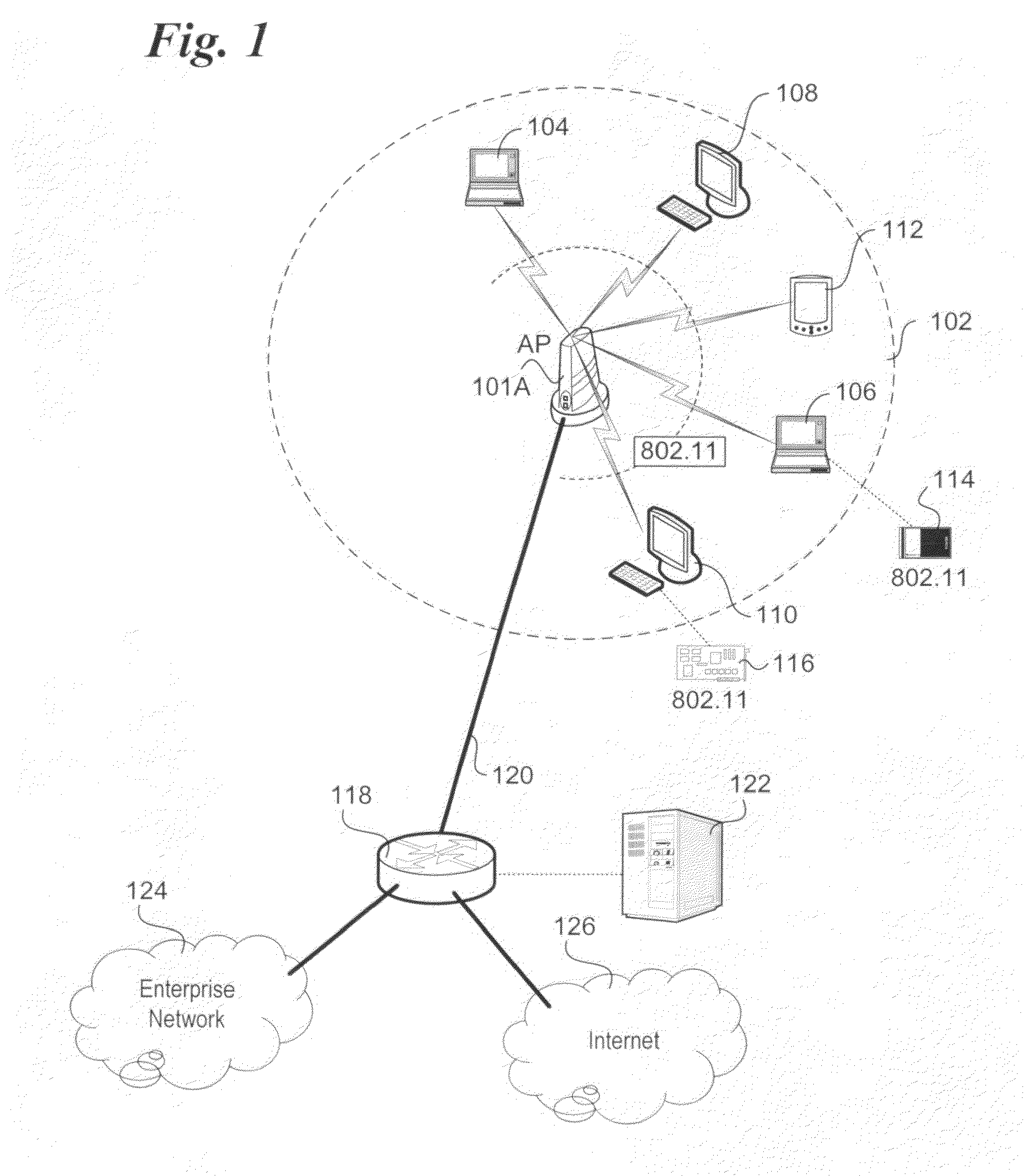
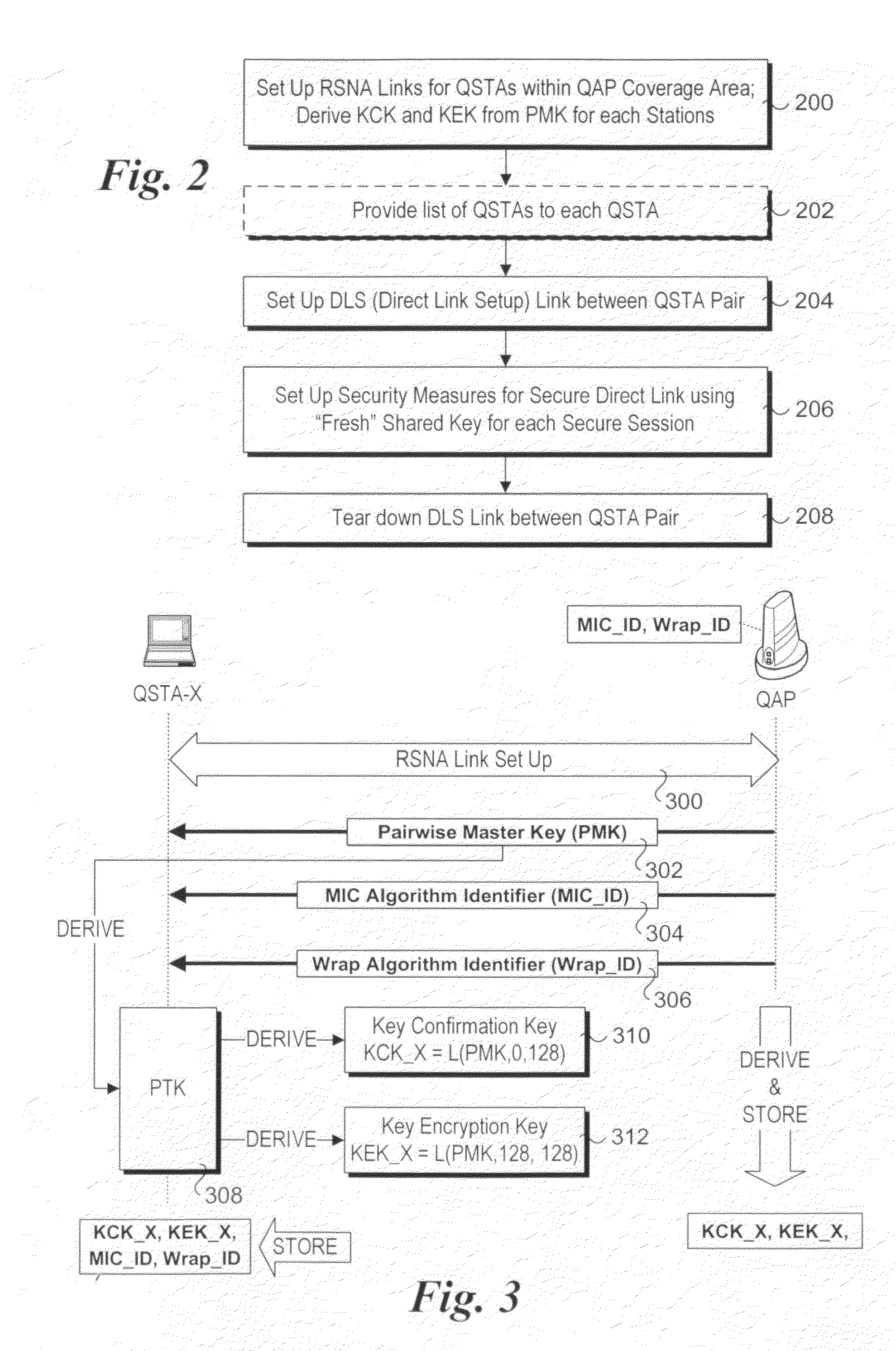
Method and system of secured direct link set-up (DLS) for wireless networks
ActiveUS20100070767A1User identity/authority verificationNetwork topologiesWireless mesh networkSecure copy
Method and system of secured direct link set-up (DLS) for wireless networks. In accordance with aspects of the method, techniques are disclosed for setting up computationally secure direct links between stations in a wireless network in a manner that is computationally secure. A direct link comprising a new communication session is set up between first and second stations in a wireless local area network (WLAN) hosted by an access point (AP), the direct link comprising a new communication session. The AP generates a unique session key for the new communication session and transfers secured copies of the session key to each of the first and second stations in a manner under which only the first and second stations can obtain the session key. A security mechanism is then implemented on the unsecured direct link to secure the direct link between the first and second stations using a secure session key derived from the session key.
Owner:INTEL CORP
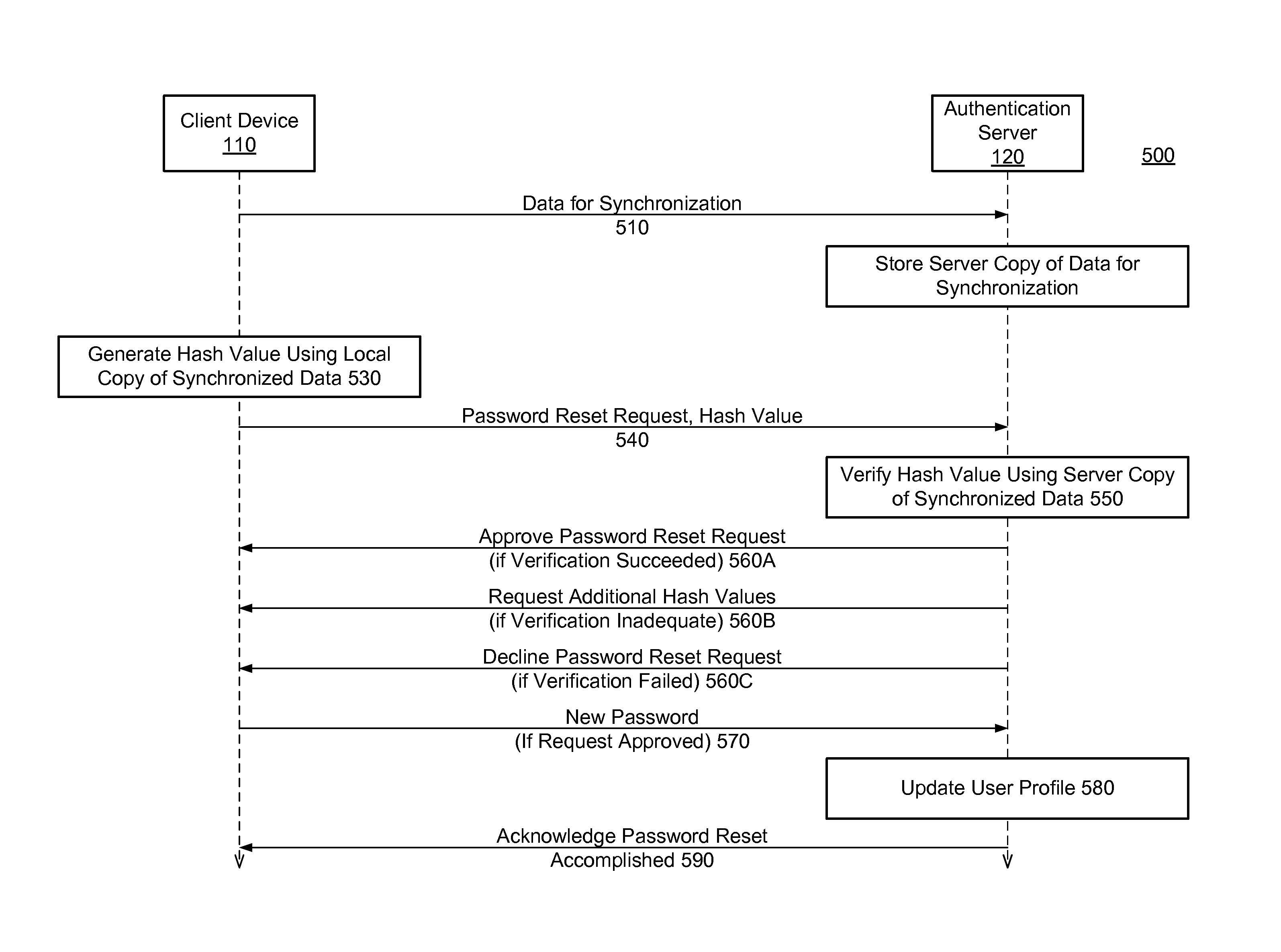
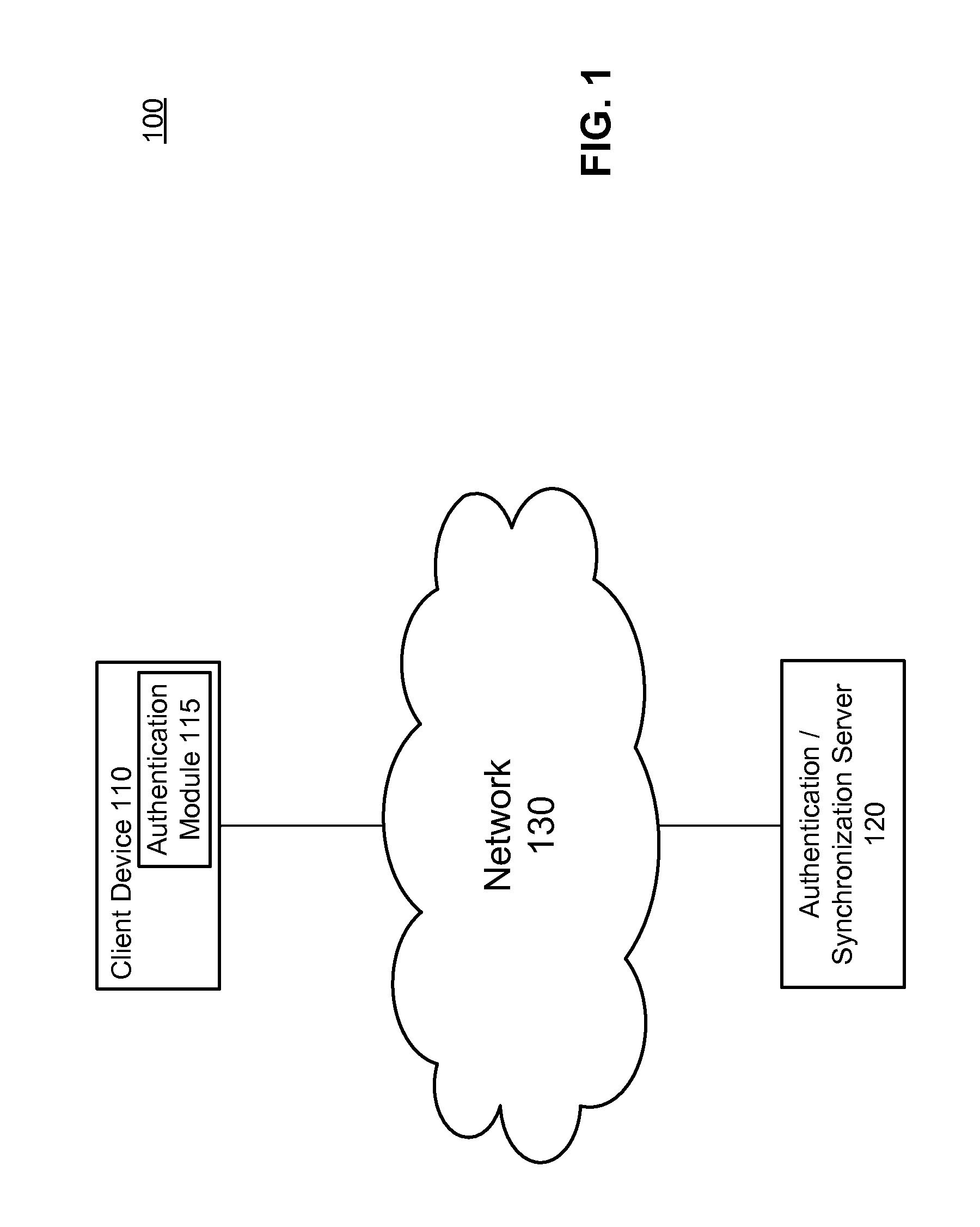
Possession of synchronized data as authentication factor in online services
ActiveUS8453222B1Digital data processing detailsMultiple digital computer combinationsAuthentication serverClient-side
A user's possession of synchronized data is used as an authentication factor. When the user requests an authentication configuration change, an authentication server requests the user to prove possession of synchronized data for that user. The user launches an authentication module on a client device hosting a local copy of the synchronized data. The authentication module creates a hash of the local copy and transmits the hash to the authorization server. Upon successfully verifying the received hash using a server copy of the synchronized data, the authentication server considers the user authorized and thus allows the user to make the authorization configuration change.
Owner:NORTONLIFELOCK INC
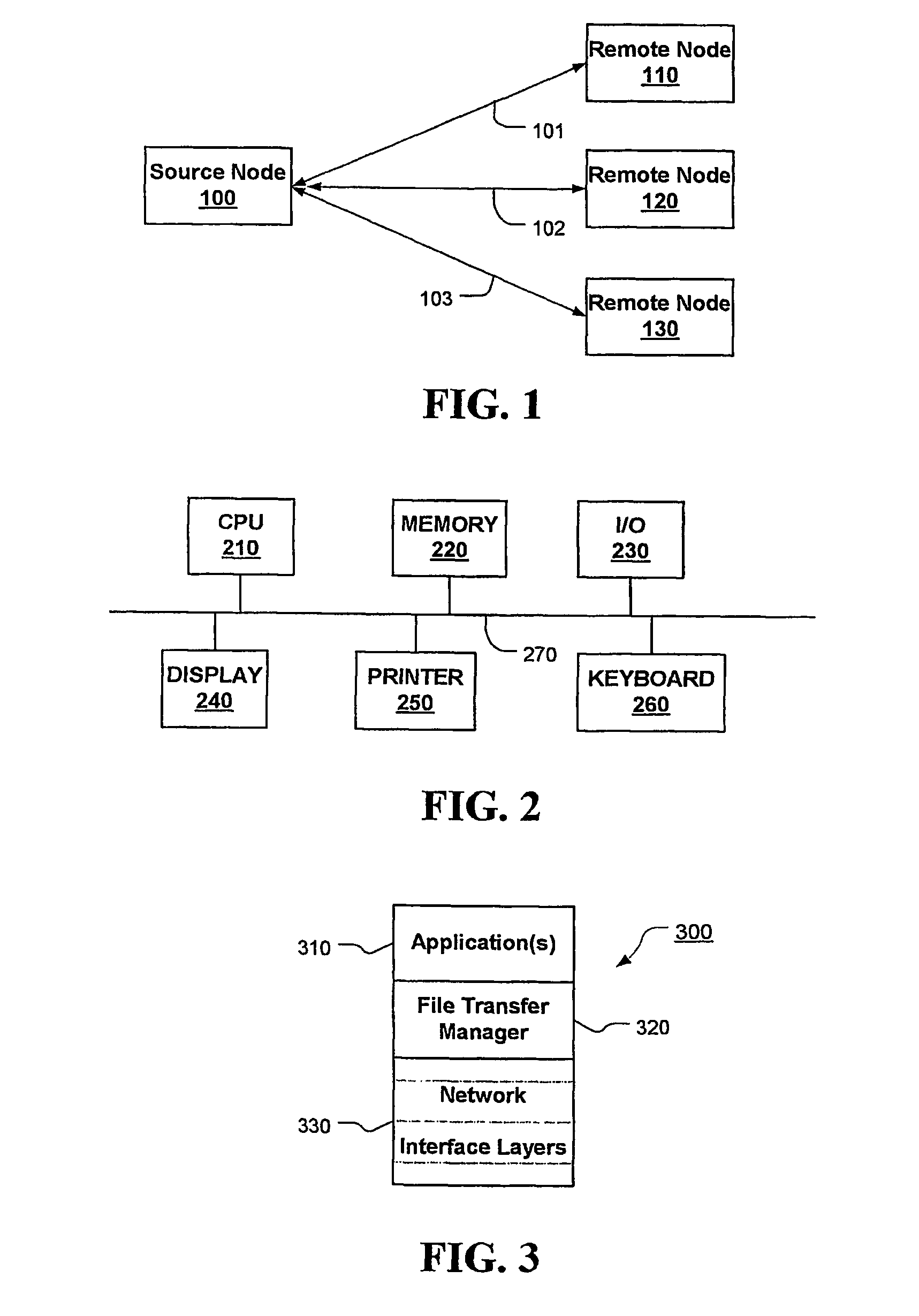
Safe output protocol for files to multiple destinations with integrity check
ActiveUS20040243686A1Multiple digital computer combinationsElectric digital data processingCommunications systemTransfer procedure
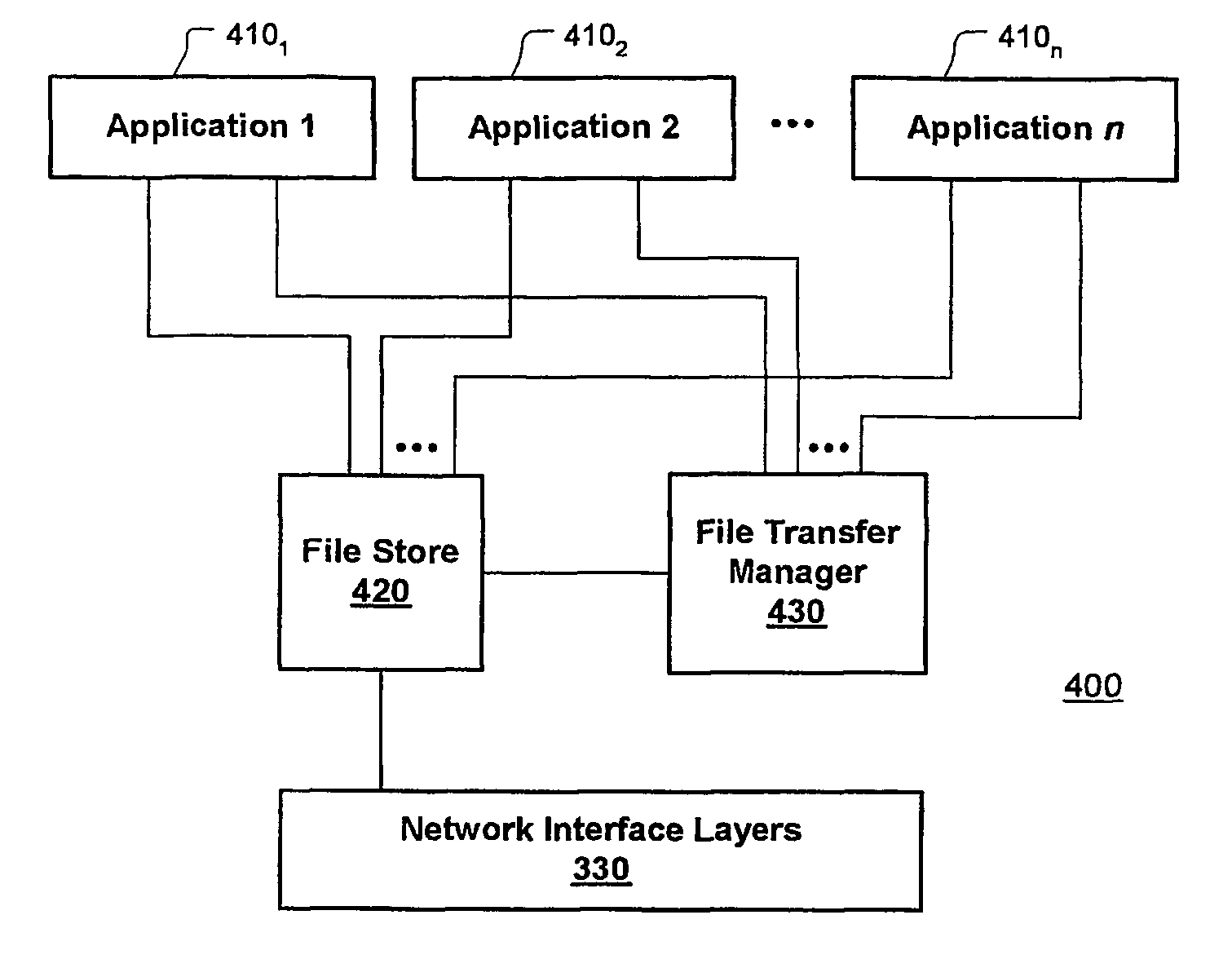
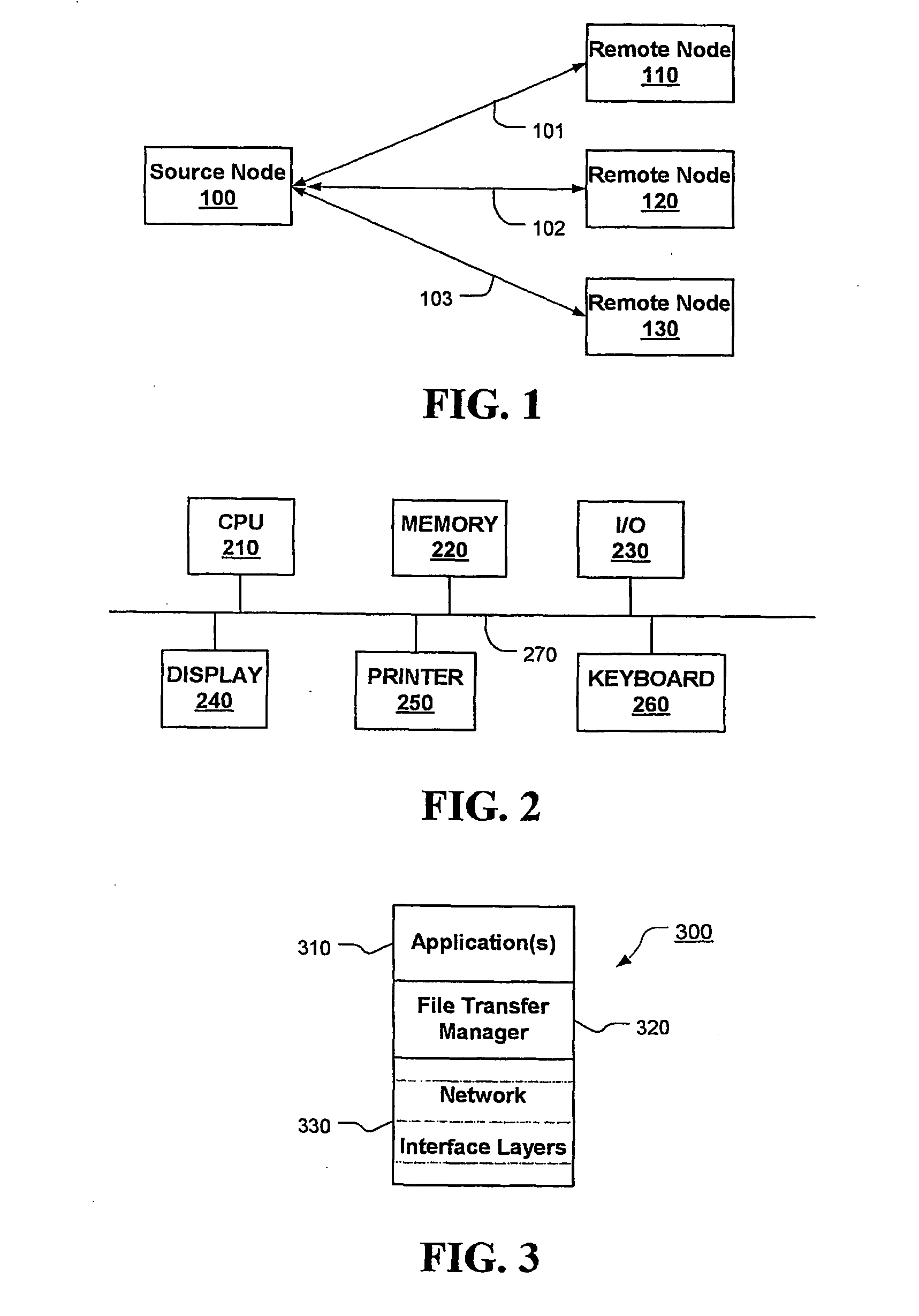
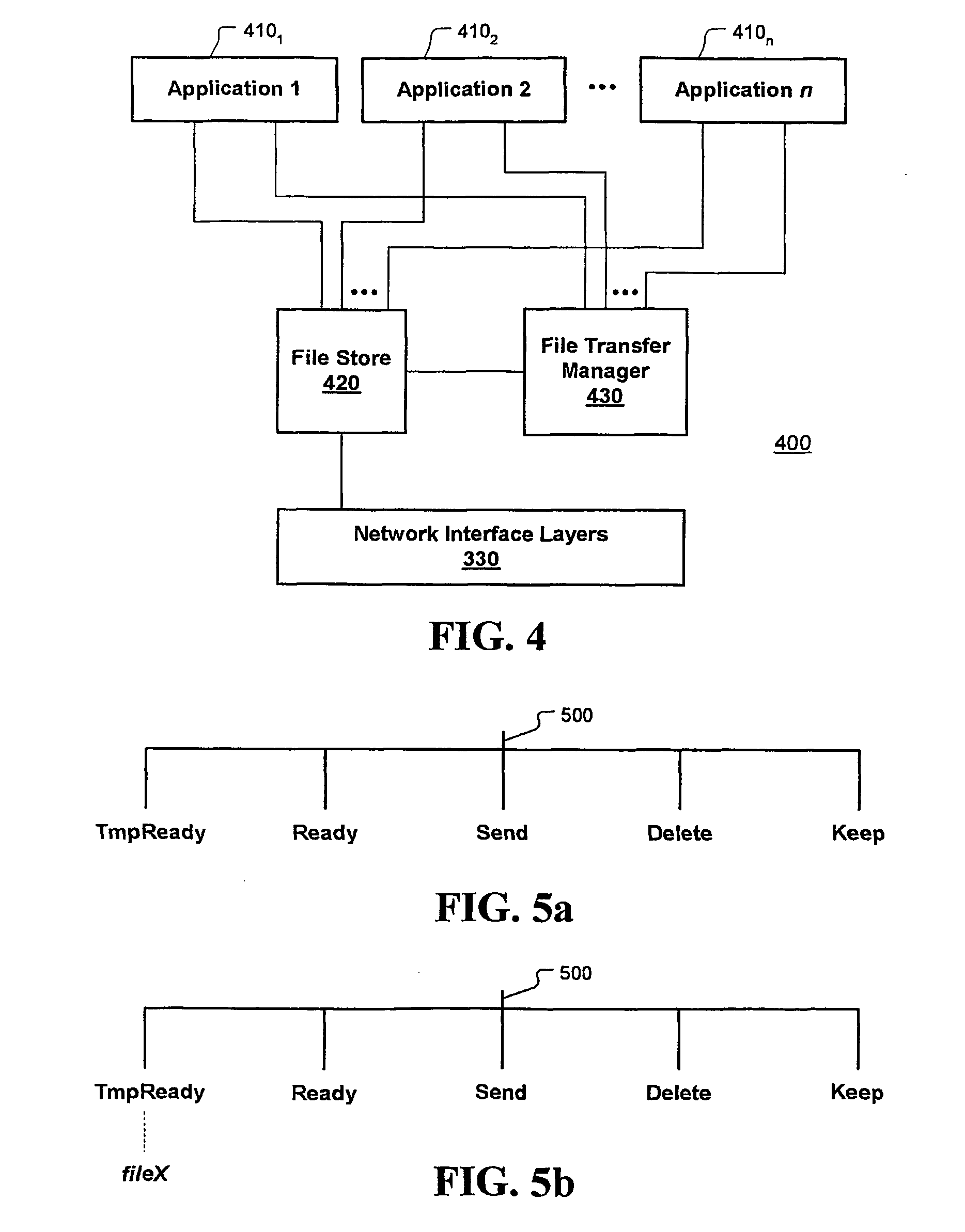
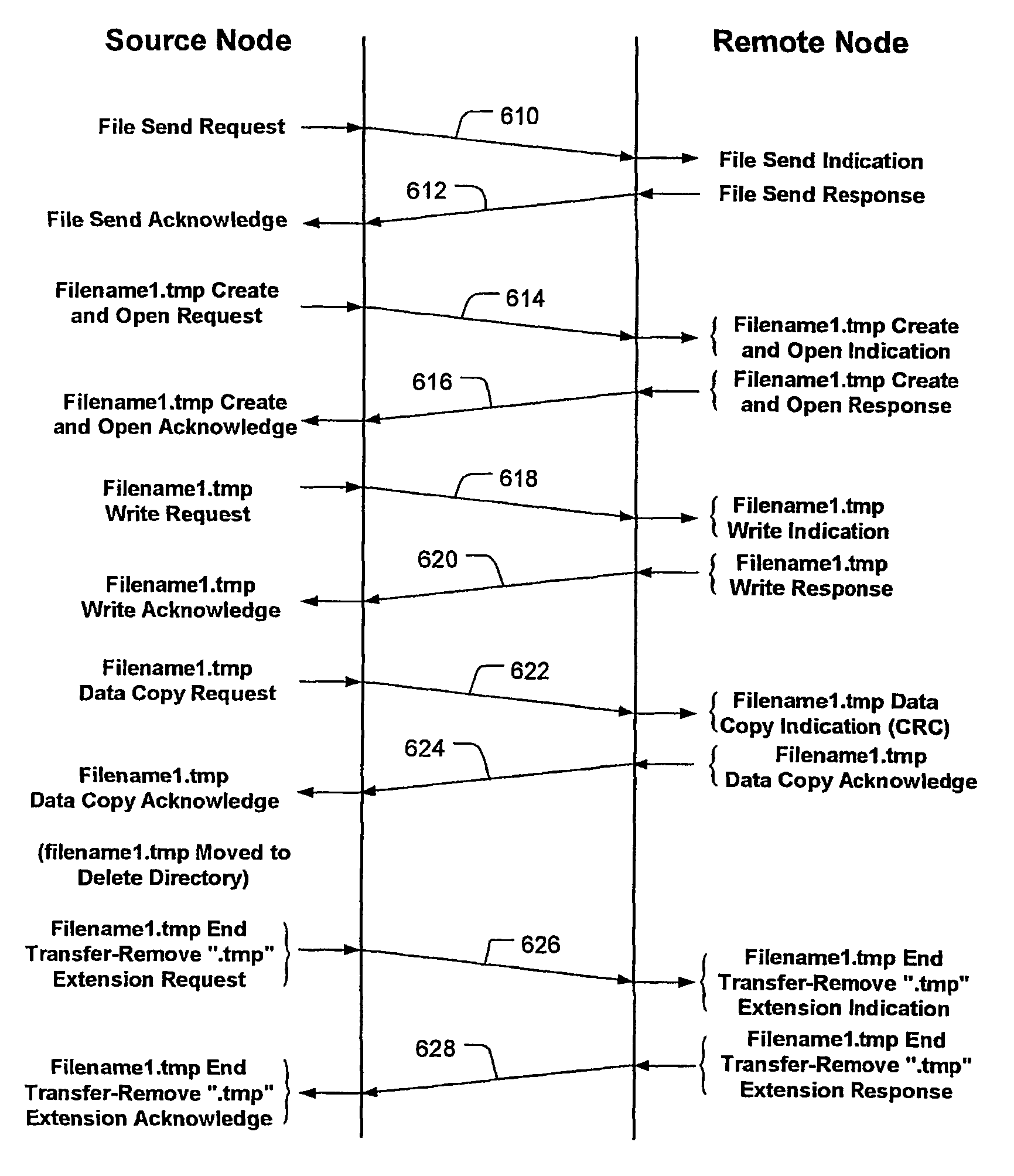
Protocol is provided for safe transfer of files from between nodes of a communication system. The protocol includes a handshake operation between a source (local or initiating) node sending one or more files and a remote (responding) node receiving the files to ensure that control of the file remains with the source node until the file is successfully transferred. The protocol is provided by a file transfer manager that controls the transfer process through a series of file moves that include moving the file into a directory associated with the file transfer manager, from which the file is sent and moving the file out of that directory after the remote node acknowledges a safe copy operation of the file. Files are maintained in the sending directory and under control of the source node at least for a configurable amount of time until the file is safely transferred. Files can be retrieved by the remote node after they have been transmitted for a configurable amount of time, after which they will be deleted from the local node.
Owner:TELEFON AB LM ERICSSON (PUBL)
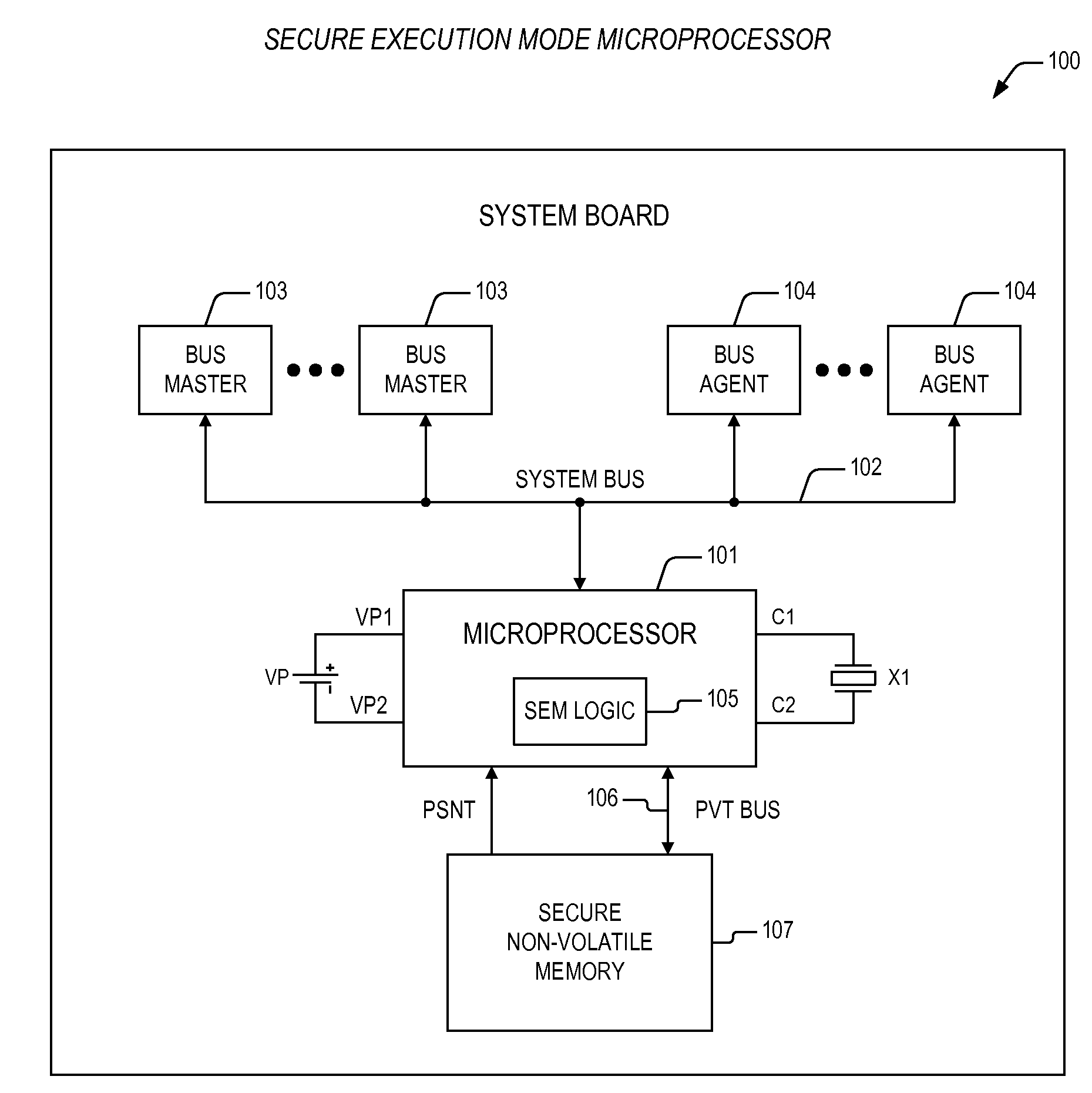
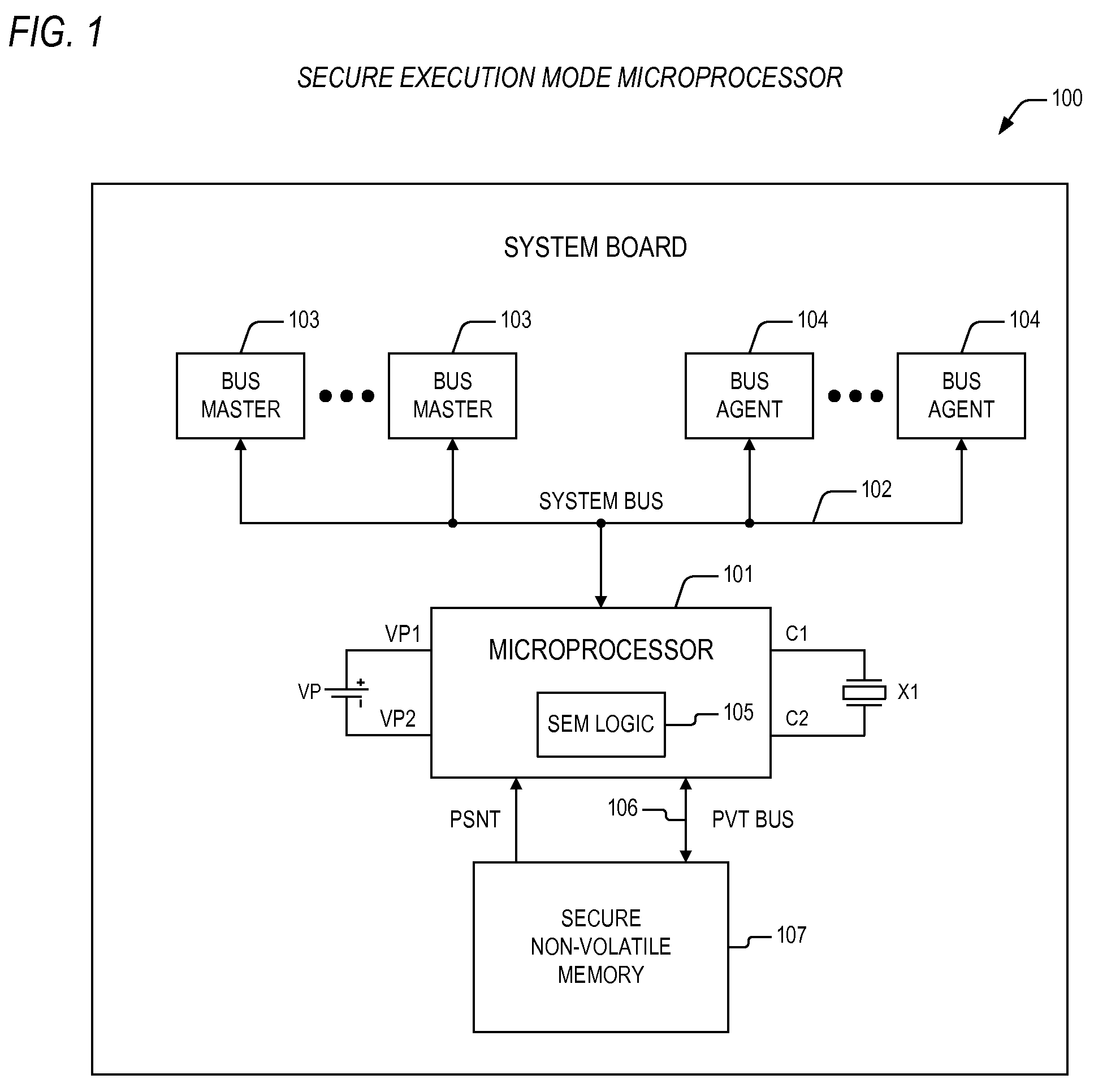
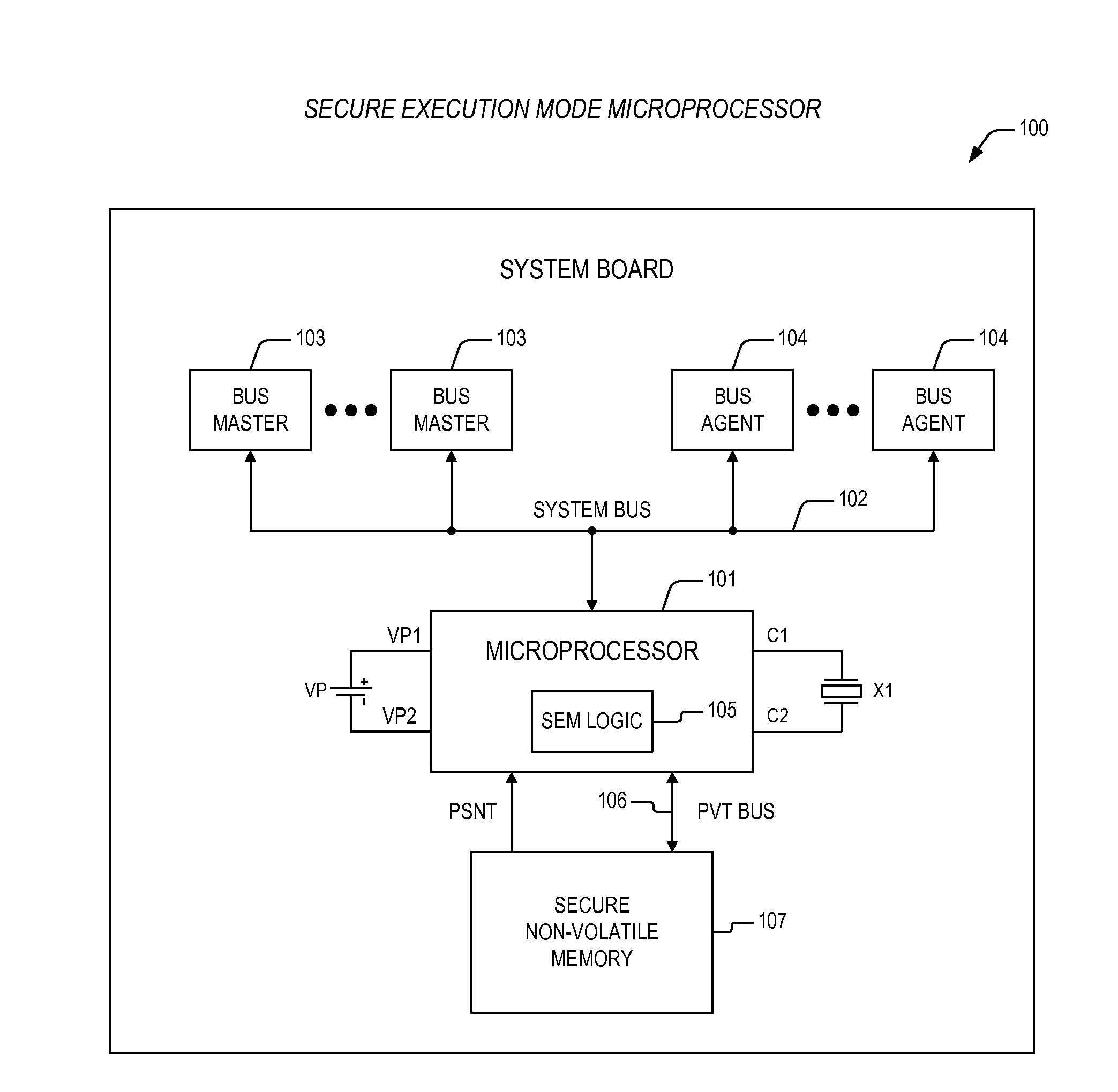
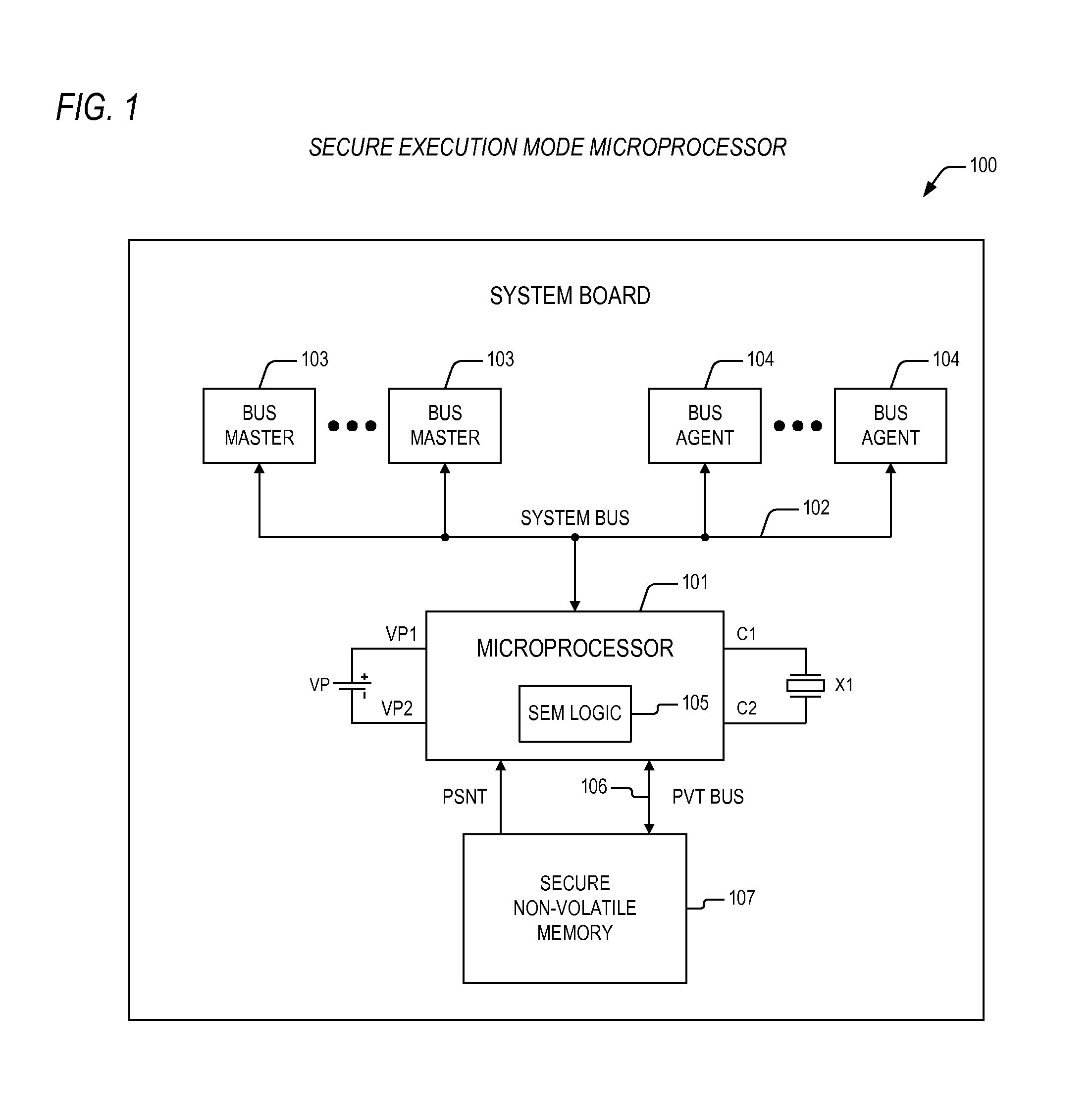
Termination of secure execution mode in a microprocessor providing for execution of secure code
ActiveUS20090293129A1Digital data processing detailsHardware monitoringApplication softwareSecure copy
An apparatus providing for a secure execution environment including a microprocessor and a secure non-volatile memory. The microprocessor is configured to execute non-secure application programs and a secure application program, where the non-secure application programs are accessed from a system memory via a system bus. The microprocessor has secure execution mode logic that is configured to detect execution of a secure execution mode return event, and that is configured to terminate a secure execution mode within the microprocessor, where the secure execution mode exclusively supports execution of the secure application program. The secure non-volatile memory is coupled to the microprocessor via a private bus and is configured to store the secure application program prior to termination of the secure execution mode, where transactions over the private bus between the microprocessor and the secure non-volatile memory are isolated from the system bus and corresponding system bus resources within the microprocessor.
Owner:VIA TECH INC
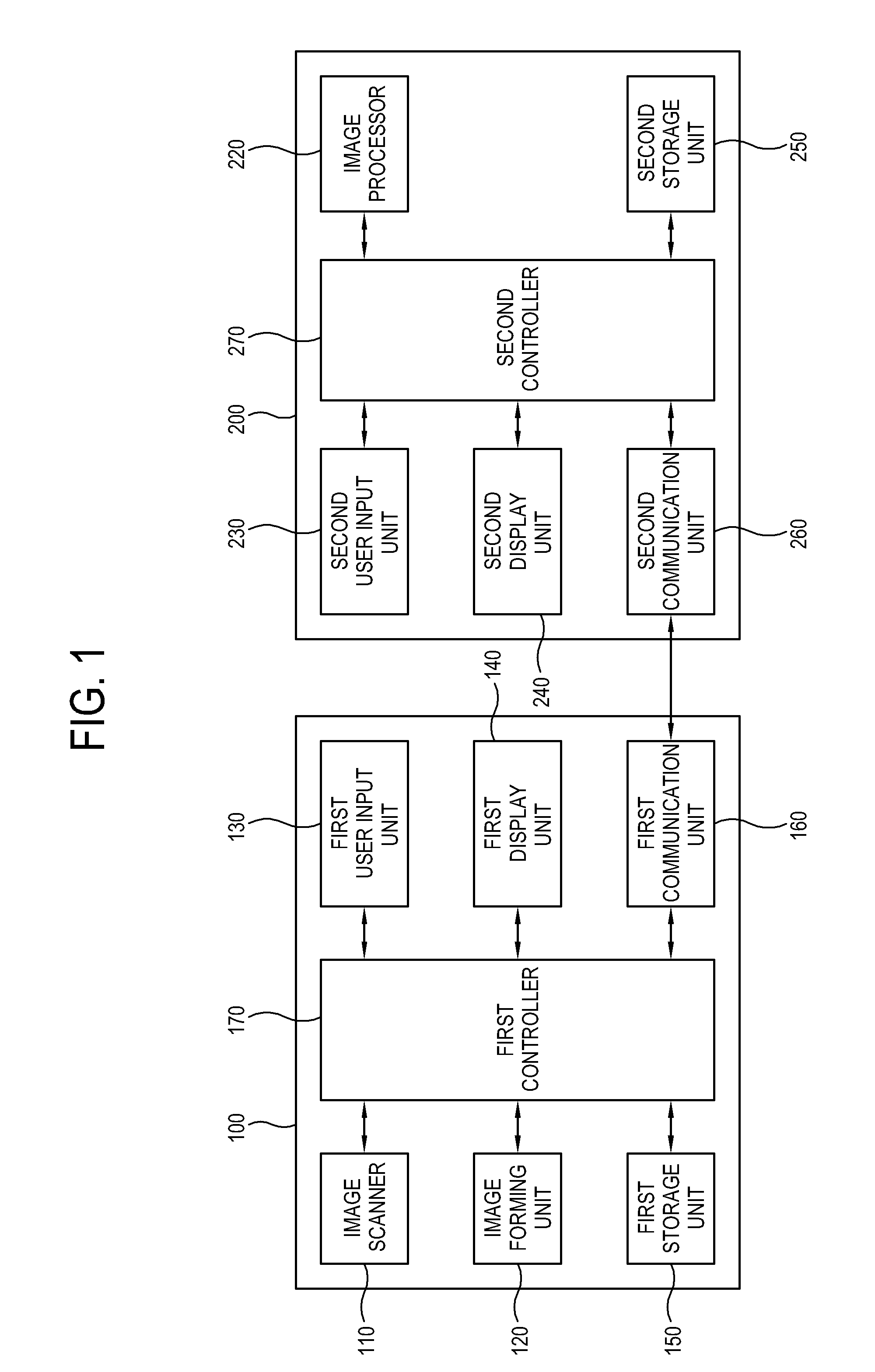
Image forming apparatus, host apparatus, and security copy method thereof
InactiveUS20110128566A1Quantity minimizationSimple printing processVisual presentationSpecial data processing applicationsComputer graphics (images)Image formation
A security copy method of an image forming apparatus includes generating scan data by scanning a document including predetermined additional information, determining whether to security-print the document by using the additional information of the generated scan data, determining whether the scan data include color information corresponding to the security area, and printing the scan data excluding a security area corresponding to the color information from the scan data according to the determination result. With this, the image forming apparatus minimizes the amount of the security information included in a bar code or mark and enables a simple print process.
Owner:S PRINTING SOLUTION CO LTD
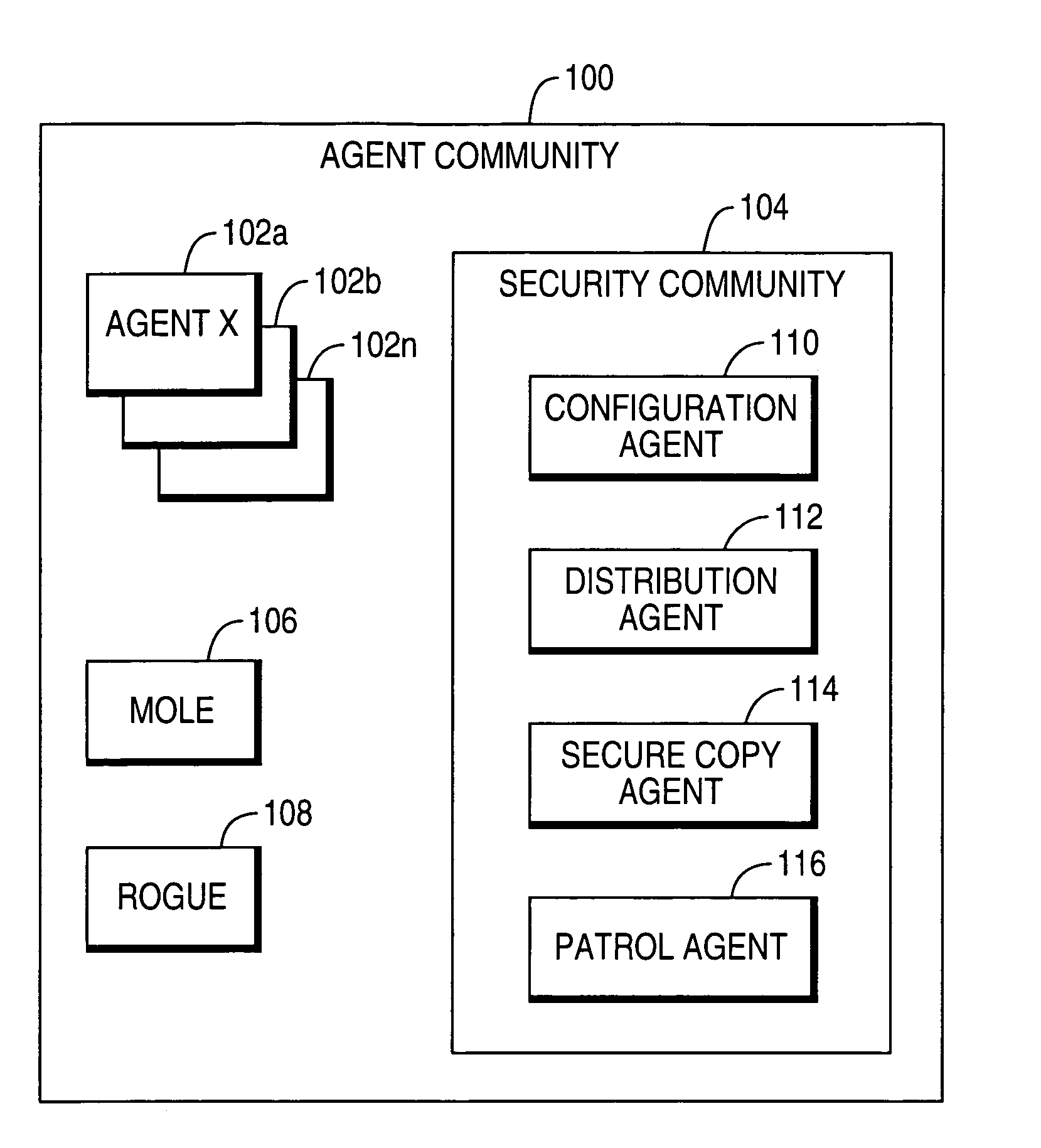
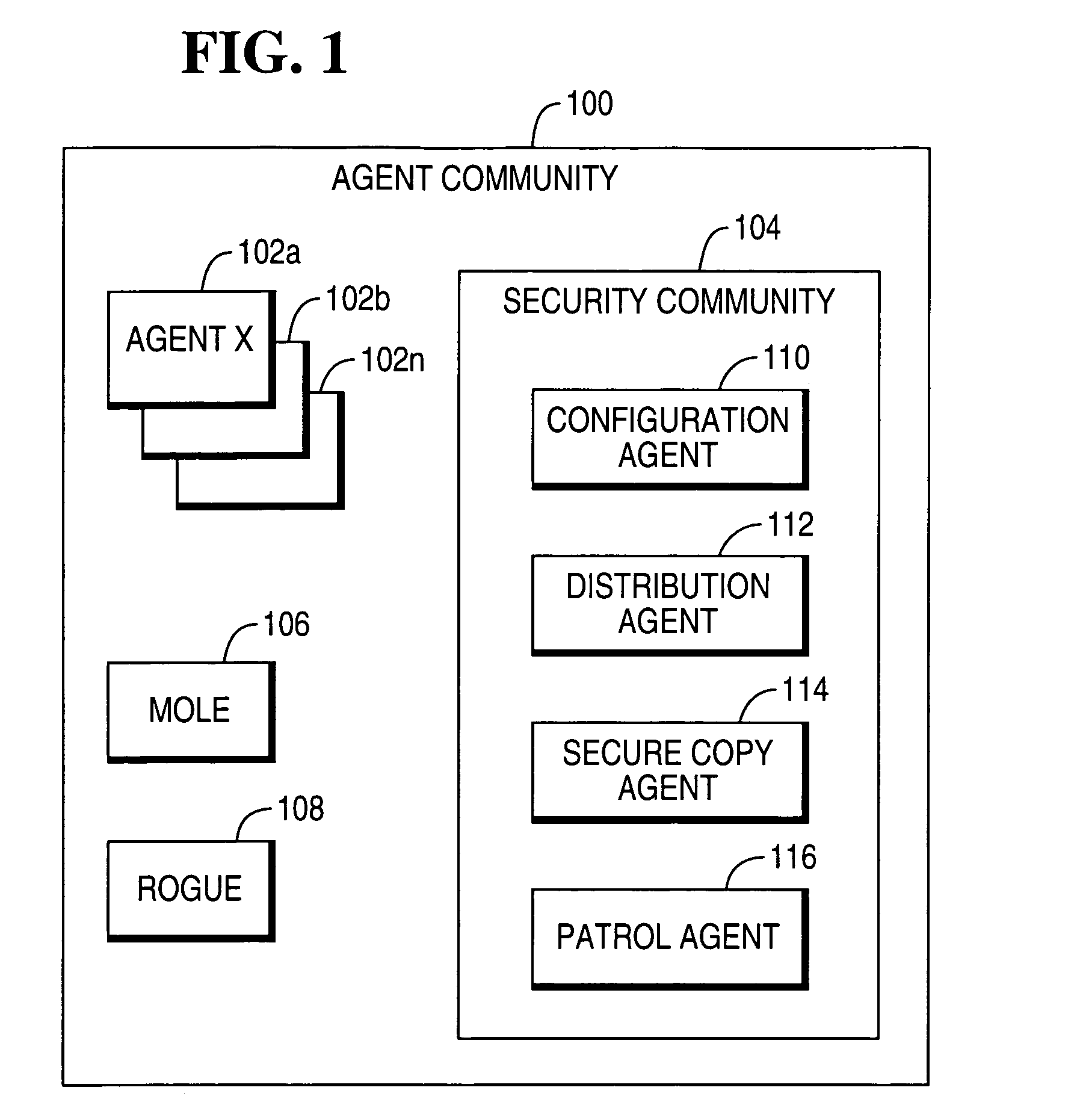
Intelligent agents used to provide agent community security
InactiveUS7131142B1Improve efficiencyReduce the burden onMemory loss protectionError detection/correctionInternet privacySecure copy
A method and apparatus for using security agents to perform security-related functions in an agent community is described. More particularly, security agents are used to monitor and police an agent community for abnormal actions of agents within an agent community and to detect and police non-approved agents within the community. The security agents include a configuration, a distribution, a secure copy, and a patrol agent.
Owner:TERADATA US
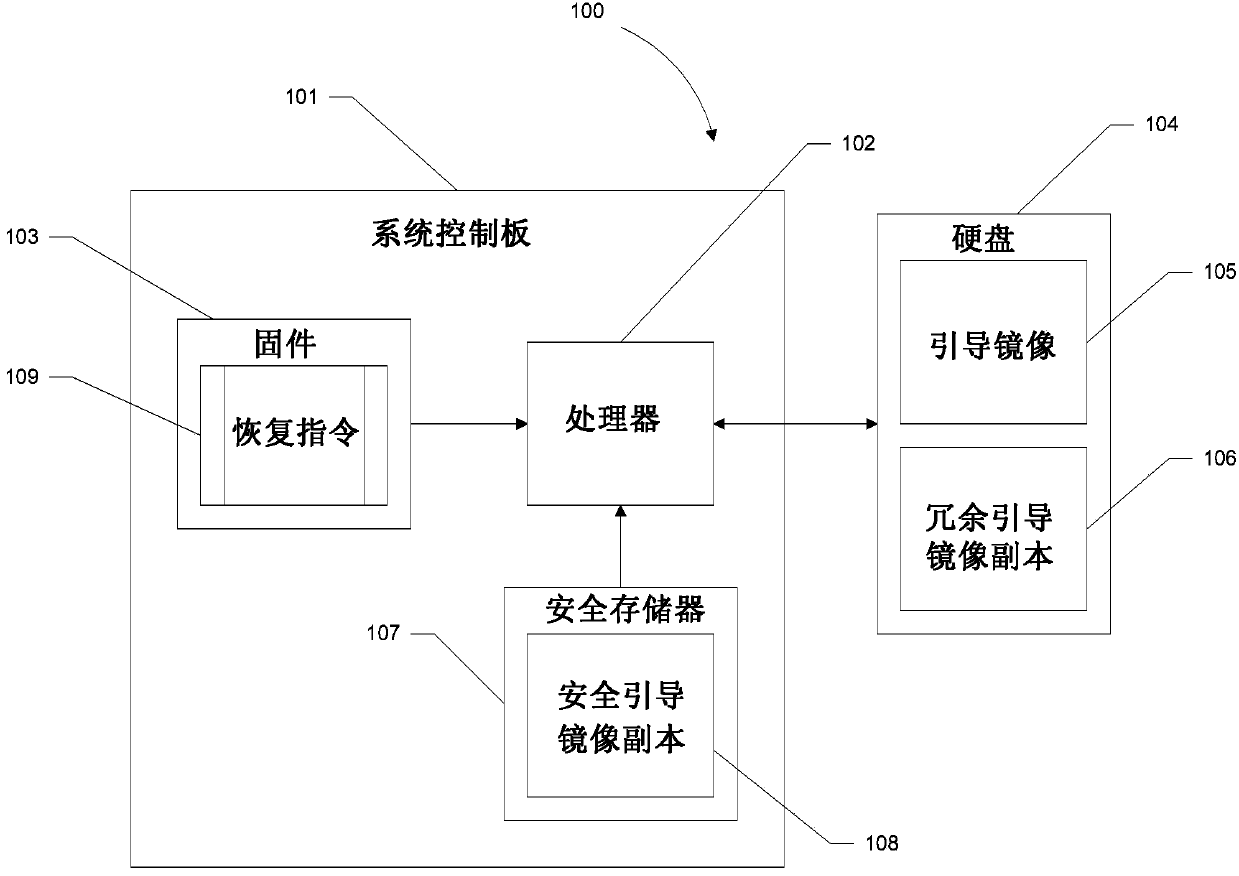
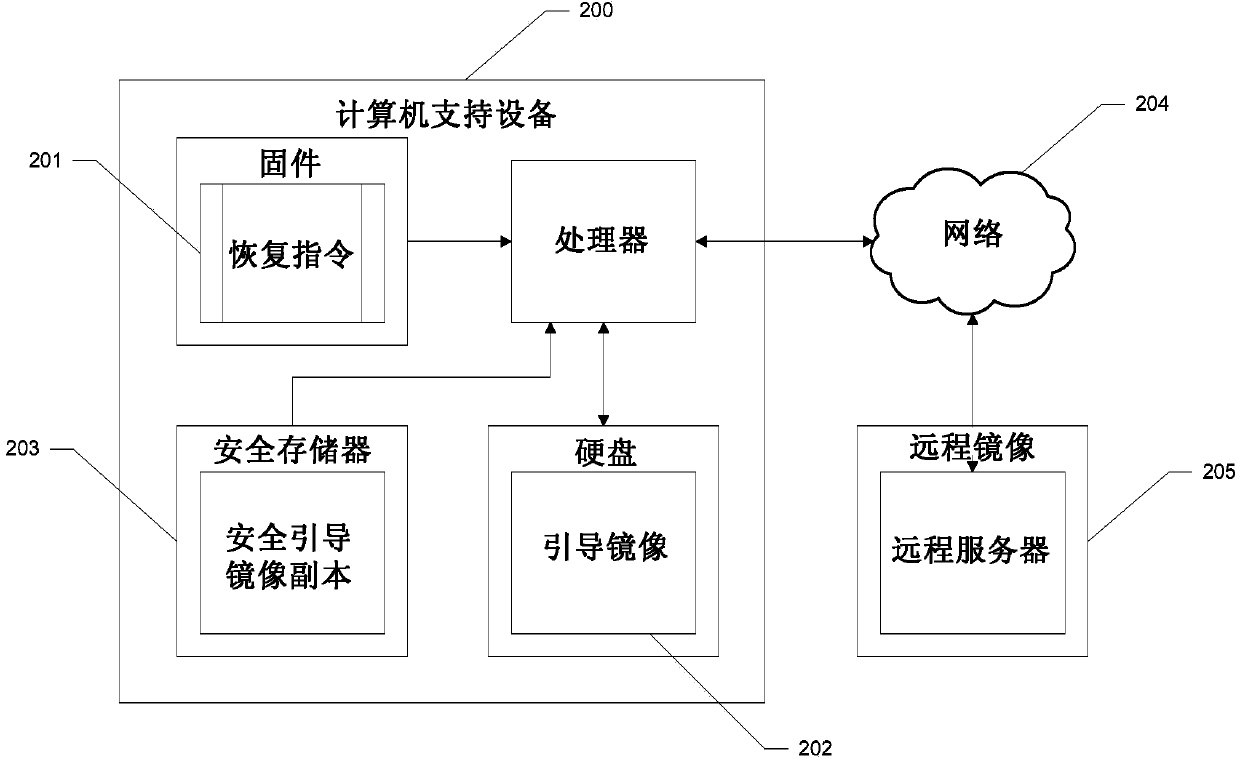
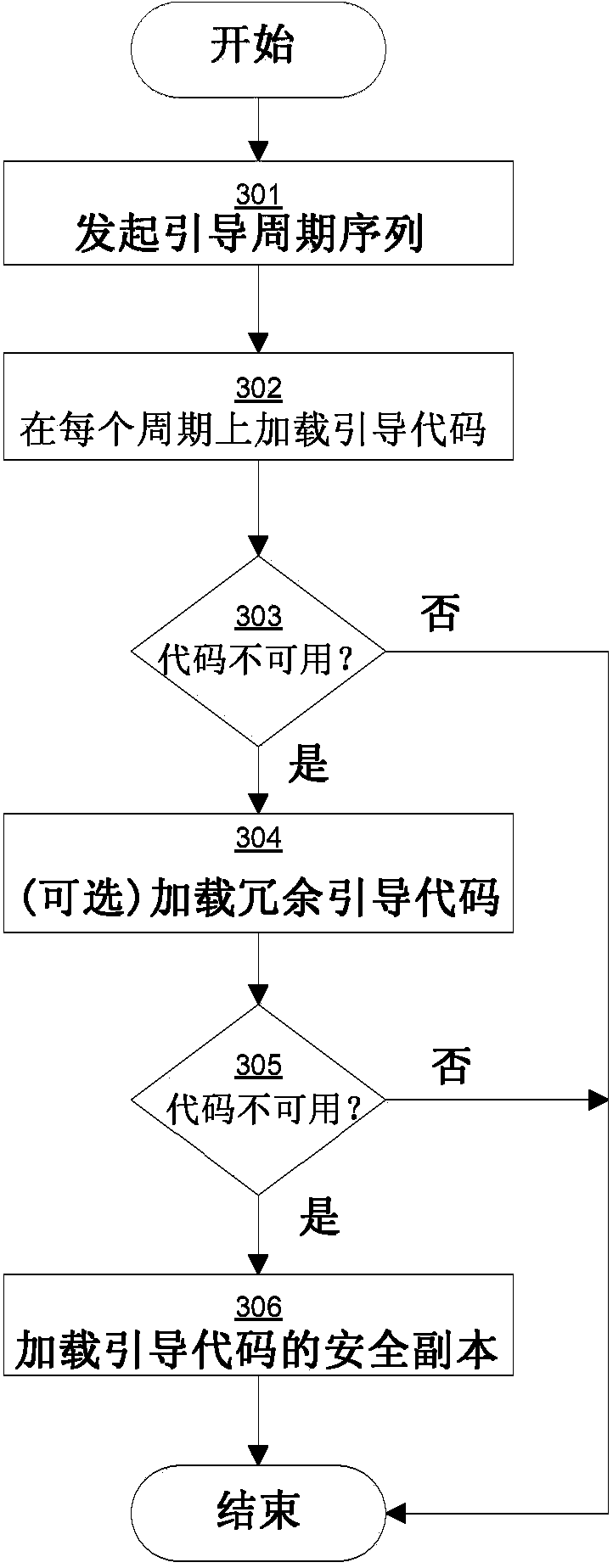
Secure recovery apparatus and method
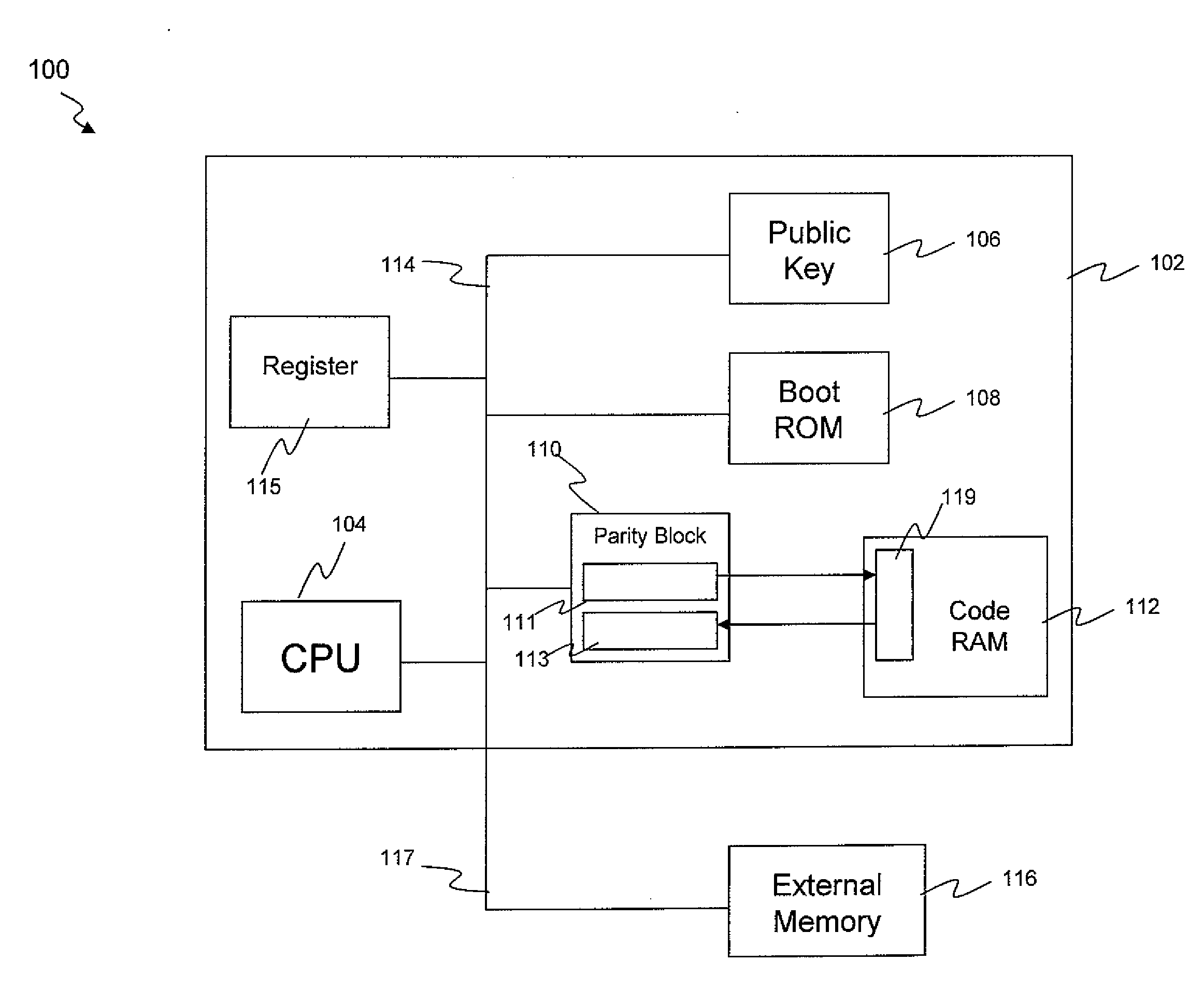
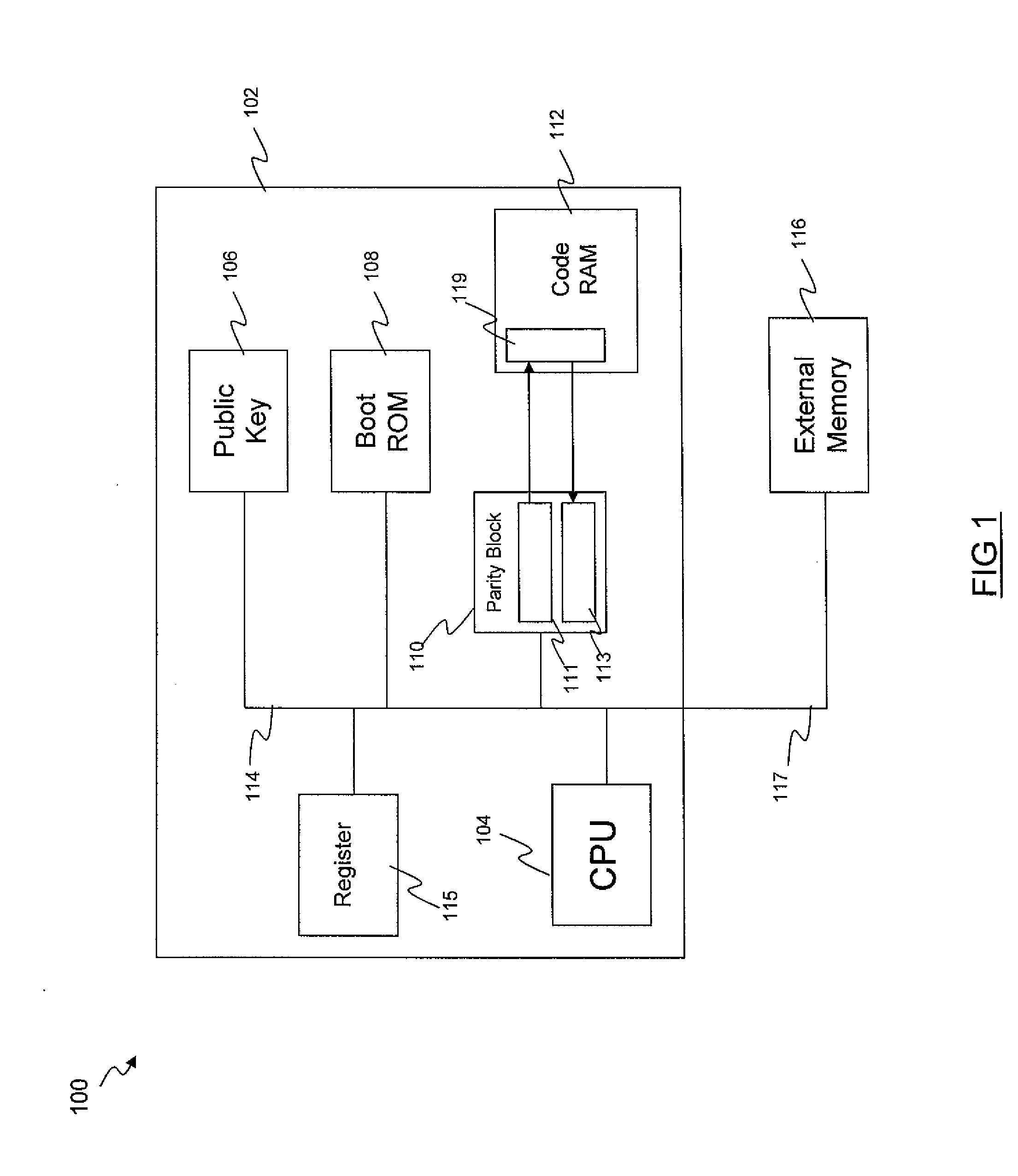
A system and method is disclosed for recovering a boot image from a secure location. Hardware instructions initiate a sequence of boot cycles to launch a computer operating system on a computer-enabled device. During the boot cycles, multiple levels of boot code are verified and a determination is made whether each level is usable by the device. If a level of boot code is determined to be unusable, a secure copy of the boot code is loaded from a secure read-only location to repair the unusable code to launch the computer operating system.
Owner:GOOGLE LLC
Secure chips with serial numbers
ActiveUS20180069710A1High information storage densityHigh densityMultiple keys/algorithms usageSemiconductor/solid-state device detailsSemiconductor chipEngineering
An electronic device comprising a semiconductor chip which comprises a plurality of structures formed in the semiconductor chip, wherein the semiconductor chip is a member of a set of semiconductor chips, the set of semiconductor chips comprises a plurality of subsets of semiconductor chips, and the semiconductor chip is a member of only one of the subsets. The plurality of structures of the semiconductor chip includes a set of common structures which is the same for all of the semiconductor chips of the set, and a set of non-common structures, wherein the non-common structures of the semiconductor chip of the subset is different from a non-common circuit of the semiconductor chips in every other subset. At least a first portion of the non-common structures and a first portion of the common structures form a first non-common circuit, wherein the first non-common circuit of the semiconductor chips of each subset is different from a non-common circuit of the semiconductor chips in every other subset. At least a second portion of the non-common structures is adapted to store or generate a first predetermined value which uniquely identifies the first non-common circuit, wherein the first predetermined value is readable from outside the semiconductor chip by automated reading means.
Owner:ASML NETHERLANDS BV
Safe output protocol for files to multiple destinations with integrity check
ActiveUS8117274B2Multiple digital computer combinationsElectric digital data processingCommunications systemSecure transmission
Protocol is provided for safe transfer of files from between nodes of a communication system. The protocol includes a handshake operation between a source (local or initiating) node sending one or more files and a remote (responding) node receiving the files to ensure that control of the file remains with the source node until the file is successfully transferred. The protocol is provided by a file transfer manager that controls the transfer process through a series of file moves that include moving the file into a directory associated with the file transfer manager, from which the file is sent and moving the file out of that directory after the remote node acknowledges a safe copy operation of the file. Files are maintained in the sending directory and under control of the source node at least for a configurable amount of time until the file is safely transferred. Files can be retrieved by the remote node after they have been transmitted for a configurable amount of time, after which they will be deleted from the local node.
Owner:TELEFON AB LM ERICSSON (PUBL)
Mobile terminal
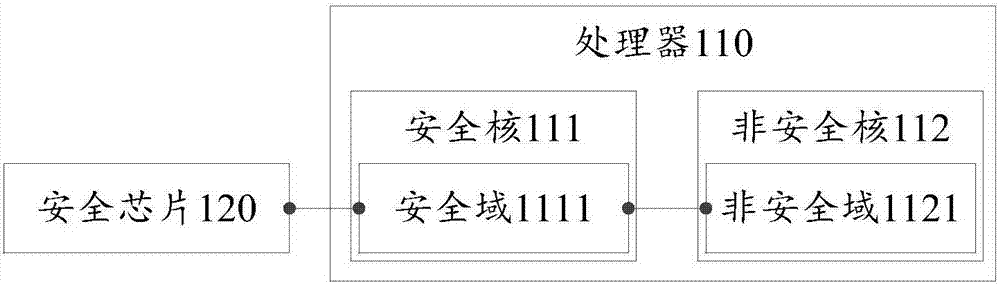
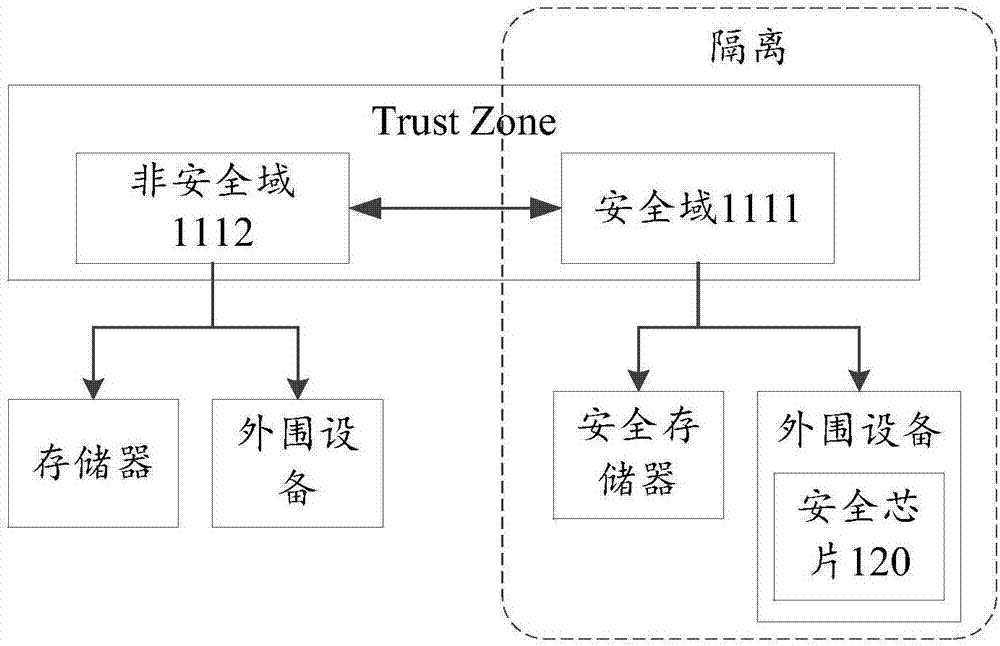
ActiveCN106897595ASafe storageImprove securityInternal/peripheral component protectionDigital data authenticationSecurity levelSecure copy
An embodiment of the present invention provides a mobile terminal. The mobile terminal is configured with a processor and a secure chip. The processor is provided with a virtual secure kernel and a virtual non-secure kernel; a secure domain is run in the secure kernel, a non-secure domain is run in the non-secure kernel, and the secure domain is accessed to the secure chip; and a first fingerprint template fragment is stored in the secure domain, a second fingerprint template fragment is stored in the secure chip, and the first fingerprint template segment and the second fingerprint template segment belong to the same fingerprint template data. According to the mobile terminal disclosed by the embodiment of the present invention, the deep security architecture of the non-secure domain, the secure domain, and the secure chip is constructed in the mobile terminal, if the hacker wants to crack the mobile terminal and obtains the fingerprint template data, the secure domain and the secure chip need to be cracked at the same time, and the security level of the secure chip can reach the EAL5+ security level, so that the program crack and physical attacks can be effectively resisted; and the self-destruction mechanism can be configured, so that the crack behavior by the hacker can be effectively prevented.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
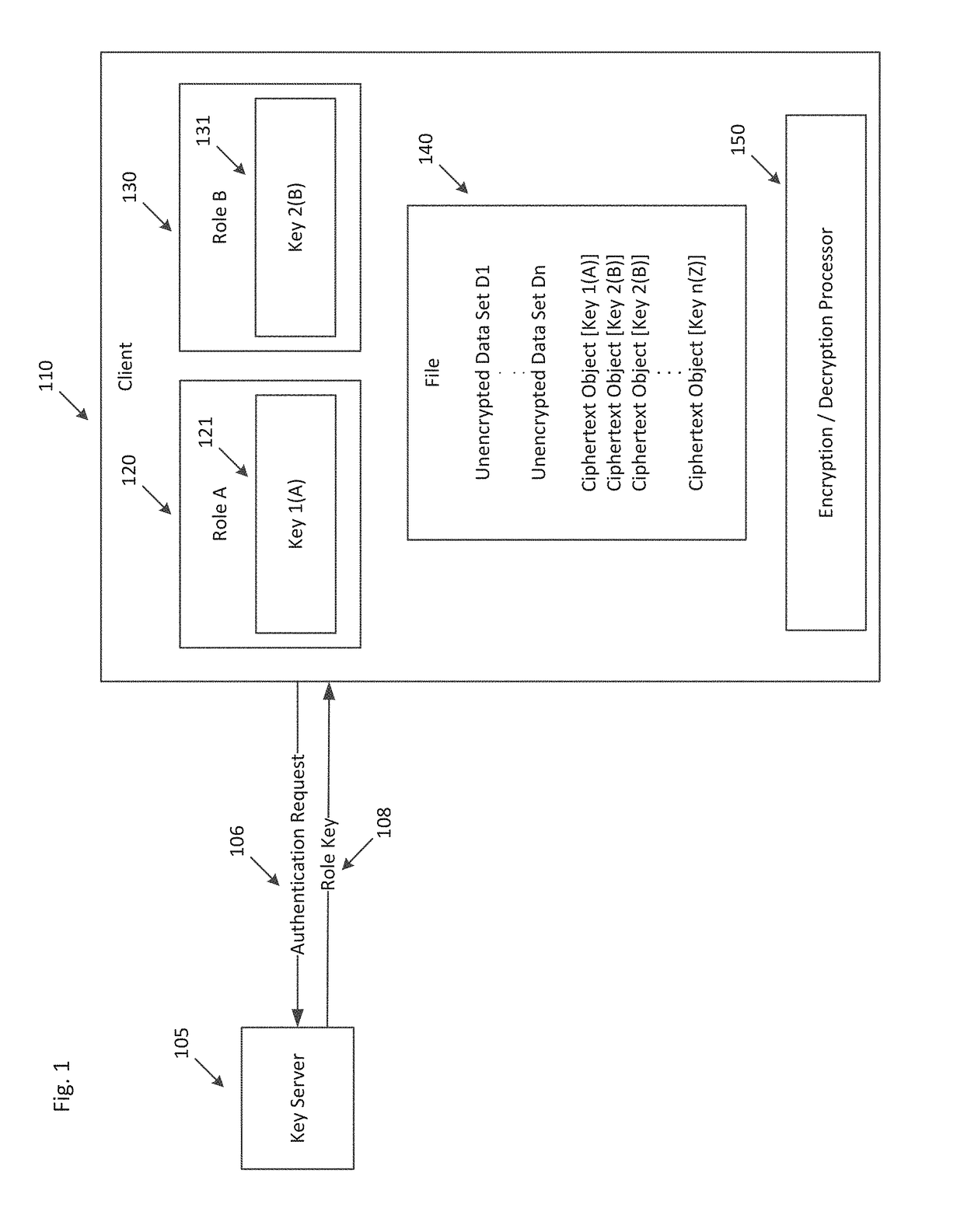
Securing portable data elements between containers in insecure shared memory space
ActiveUS10061932B1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesData setMultiple applications
Systems and methods for encrypting an unencrypted data set within a file are provided. The disclosed systems and methods can be configured to create a ciphertext object within the existing data structures of a native file format. The systems and methods enable the secure copying data between multiple applications while displaying a revealed form of the data to a user.
Owner:WINDTALKER LLC
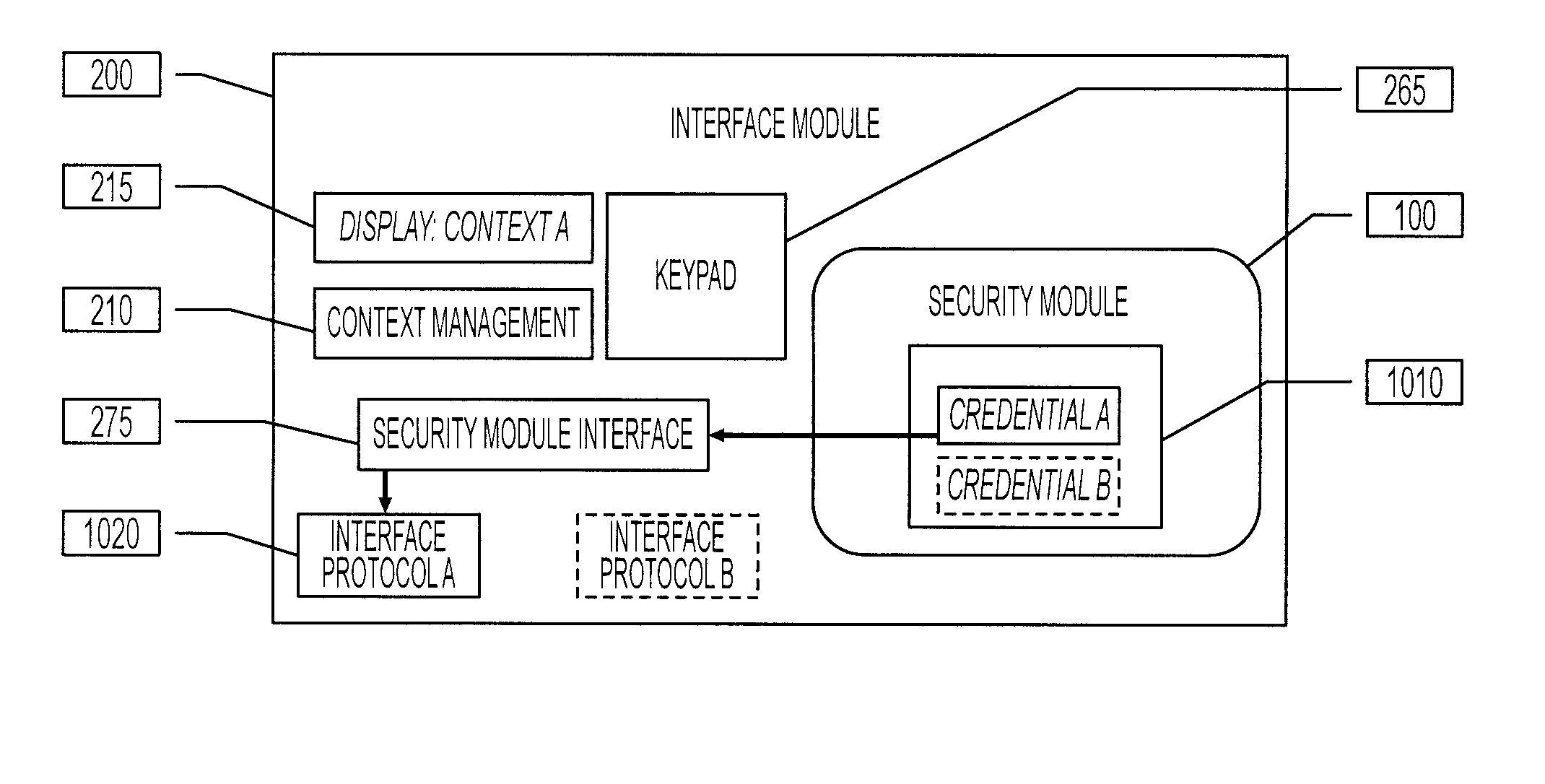
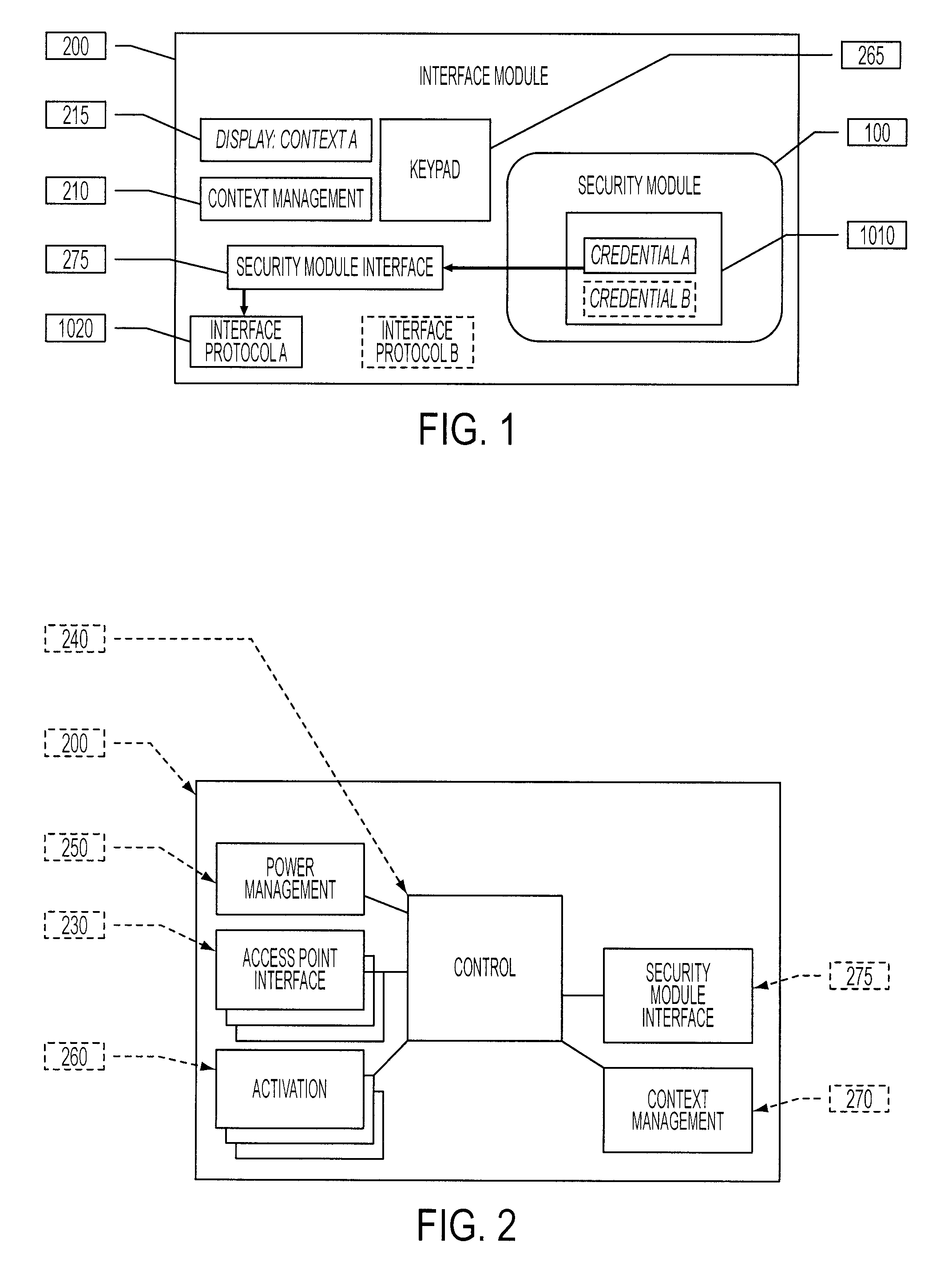
Configurable digital badge holder
ActiveUS8628019B2Electric signal transmission systemsMultiple keys/algorithms usageCommunication interfaceSmart card
A portable authentication system includes a security module, that may be a smart card, SIM (Subscriber Identity Module), USB controller with a secure chip, or similar module capable of storing one or more credentials, and an interface module such as a digital badge holder that is able to communicate with the security module, for instance by providing a smart card communication interface. The portable authentication system may be either a single integrated system or a dual system where the security module can be removed or disconnected from the interface system.
Owner:ASSA ABLOY AB
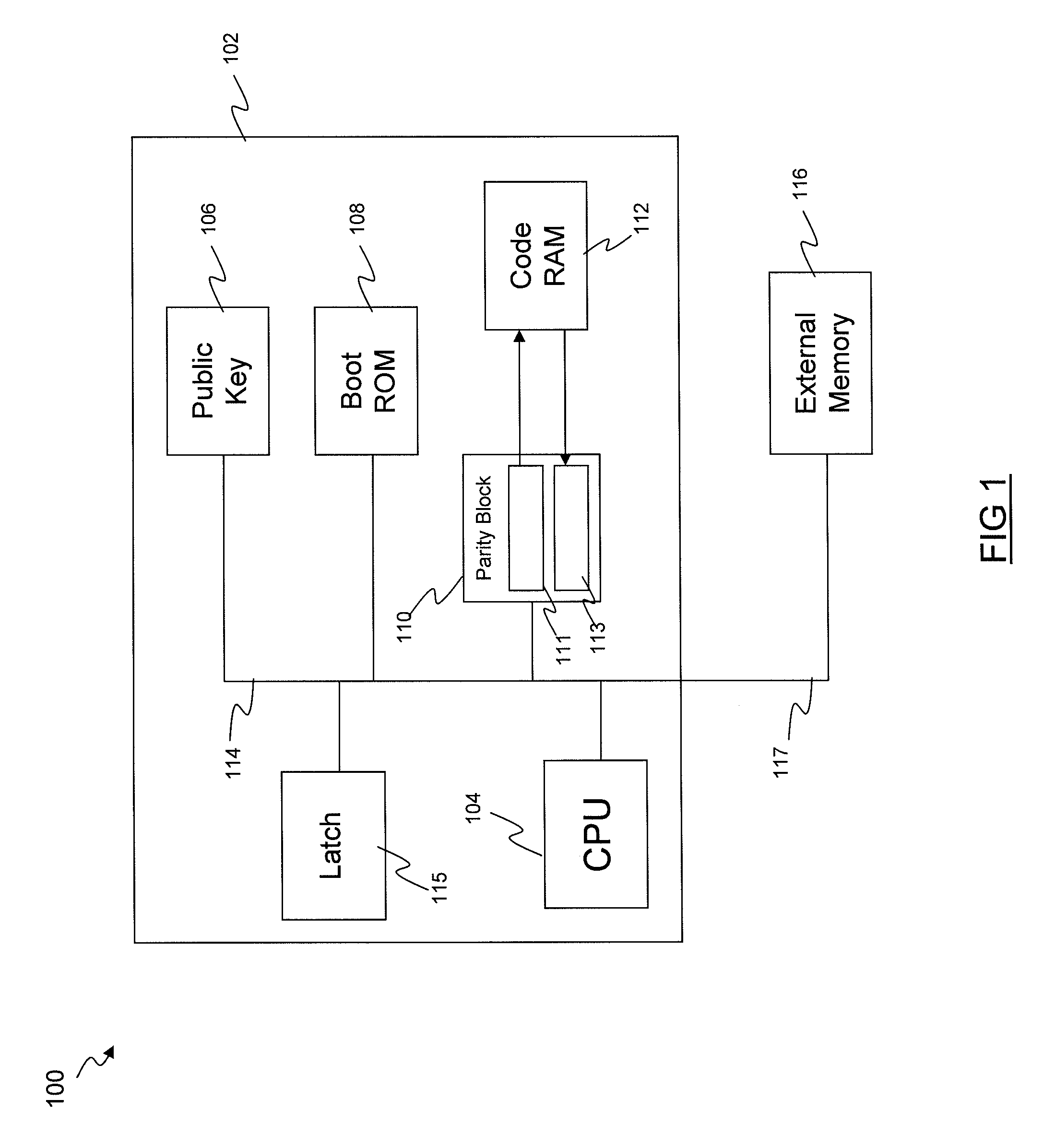
Loading secure code into a memory
ActiveUS20110004721A1Ensure integrityAvoid writingMemory adressing/allocation/relocationComputer security arrangementsComputer hardwareComputer science
A method and system of controlling access to a programmable memory including: allowing code to be written to the programmable memory in a first access mode; preventing execution of the code stored in the programmable memory in the first access mode; verifying the integrity of the code stored in the programmable memory; if the integrity of the code stored in the programmable memory is verified, setting a second access mode, wherein in the second access mode, further code is prevented from being written to the programmable memory, and execution of the code stored in the programmable memory is allowed.
Owner:STMICROELECTRONICS (RES & DEV) LTD
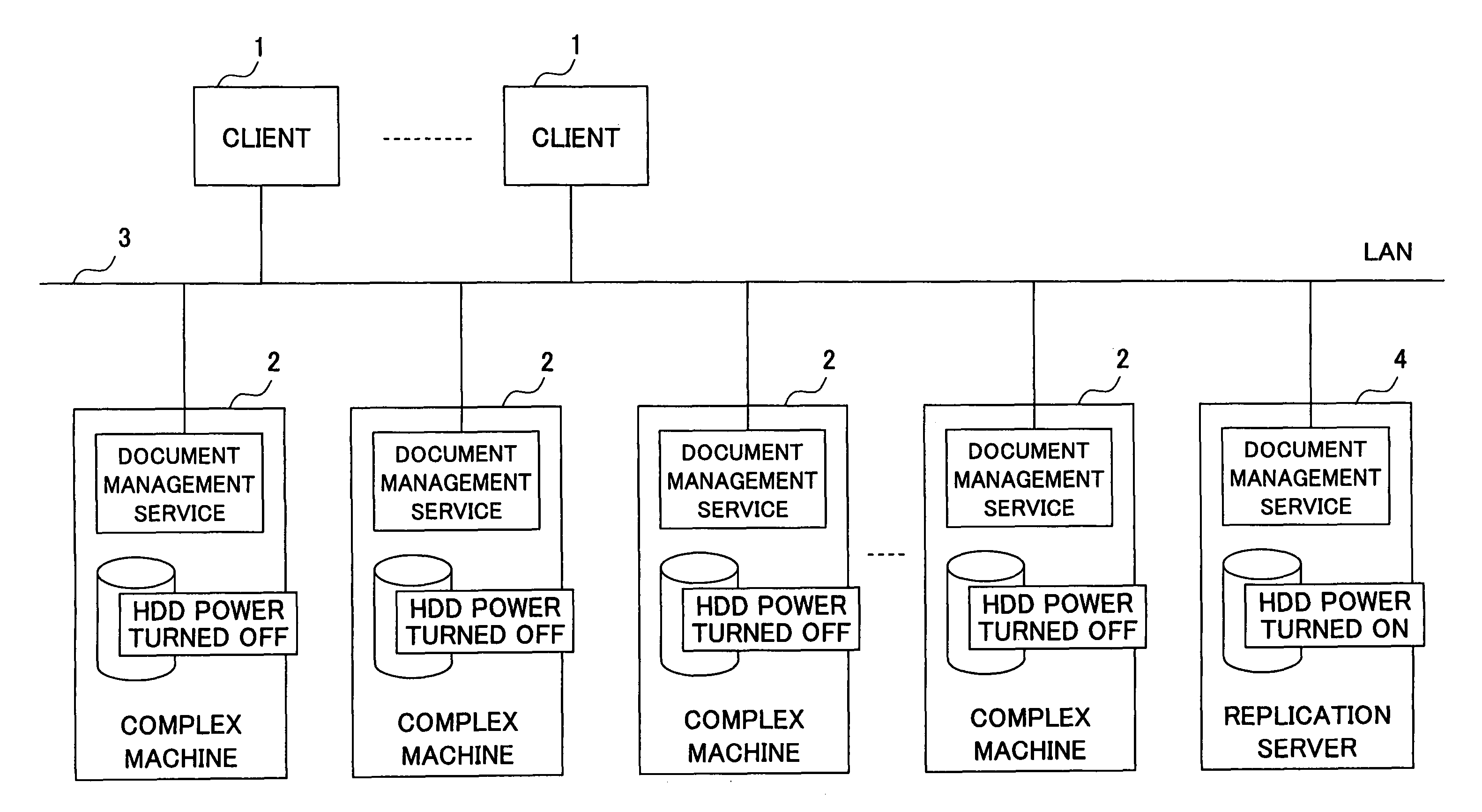
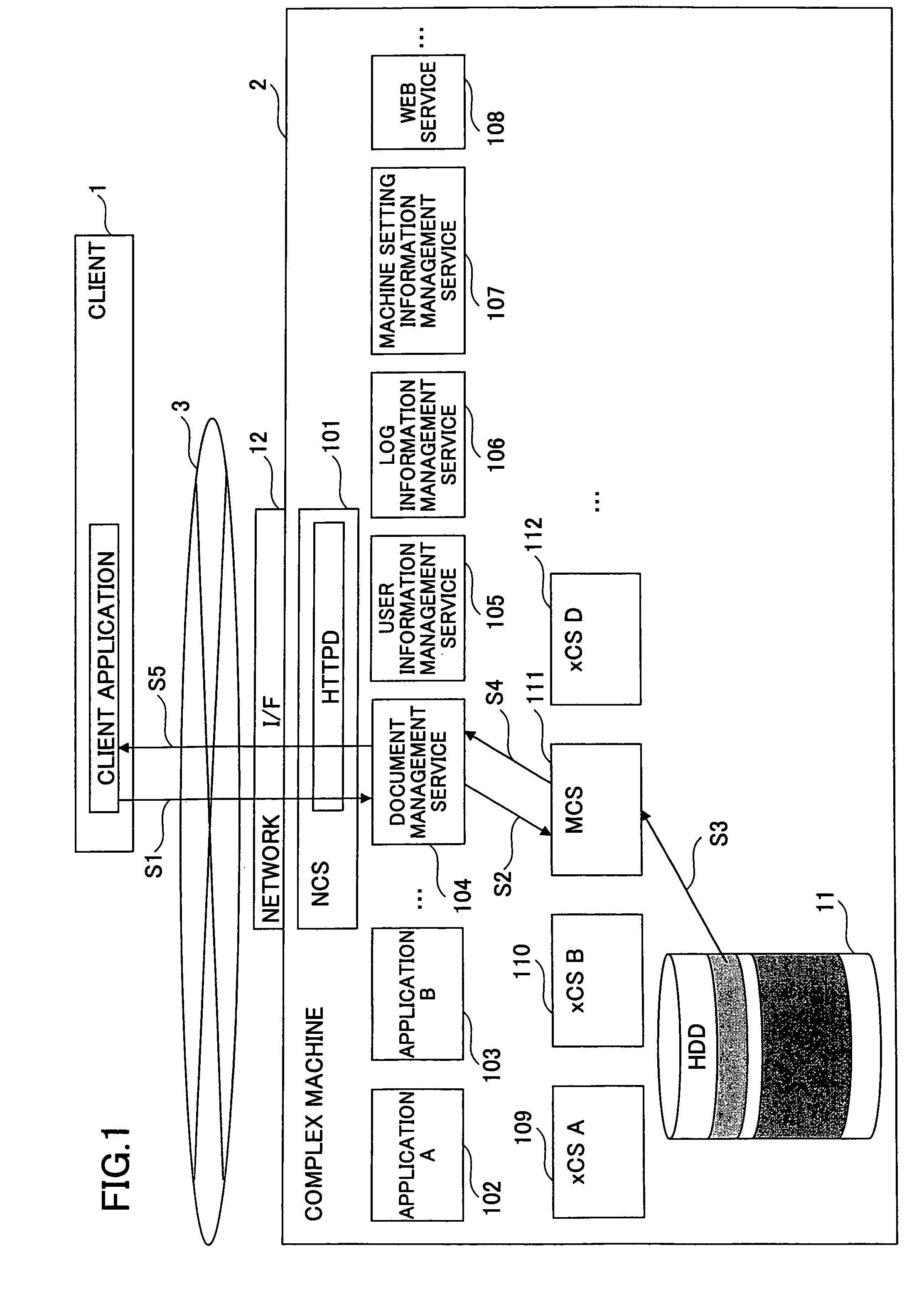
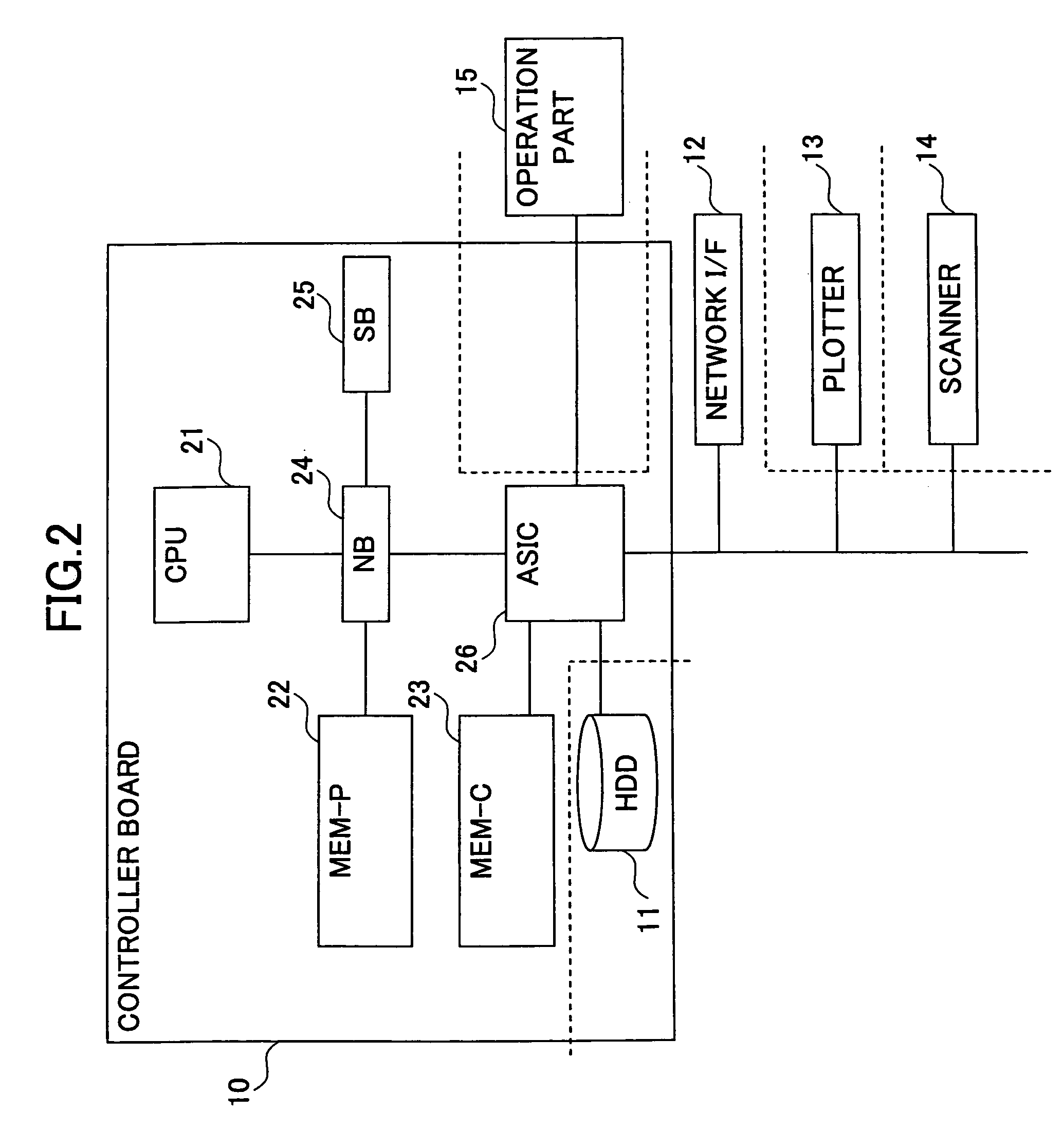
Information processing apparatus using server copy of predetermined information when storing part is in power saving mode
InactiveUS7979726B2Avoid spendingSave powerEnergy efficient ICTVolume/mass flow measurementInformation processingPower mode
An information processing apparatus having a plurality of power modes having different power consumptions, includes: a storing part storing therein predetermined information; and a control part using the predetermined information from another server apparatus in which the predetermined information has been copied and stored, upon receiving a request for the predetermined information when the power mode of the storing part is a power saving mode.
Owner:RICOH KK
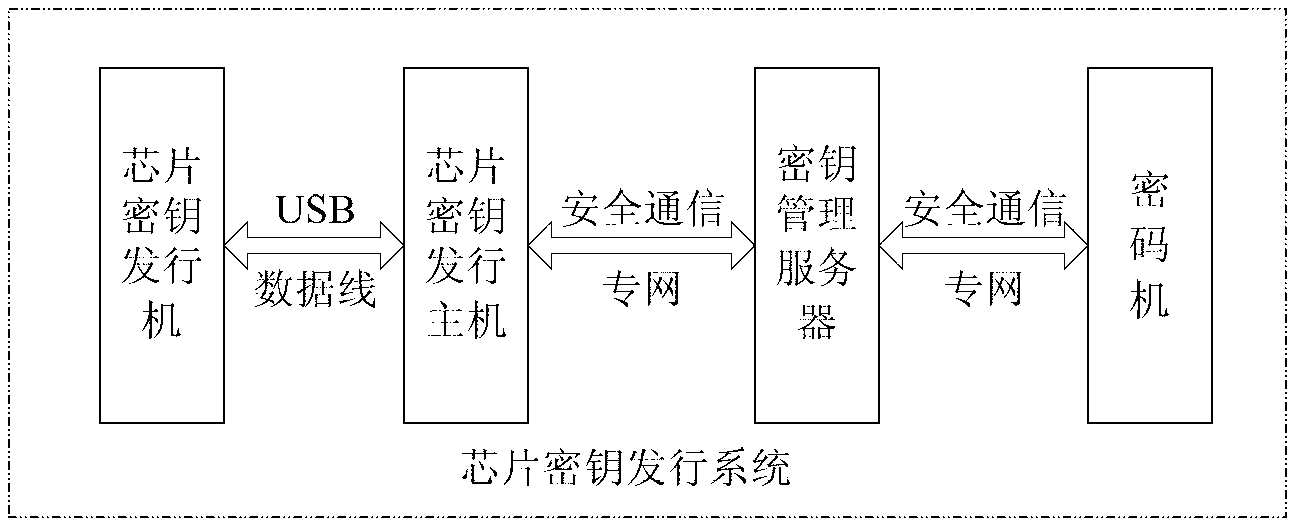
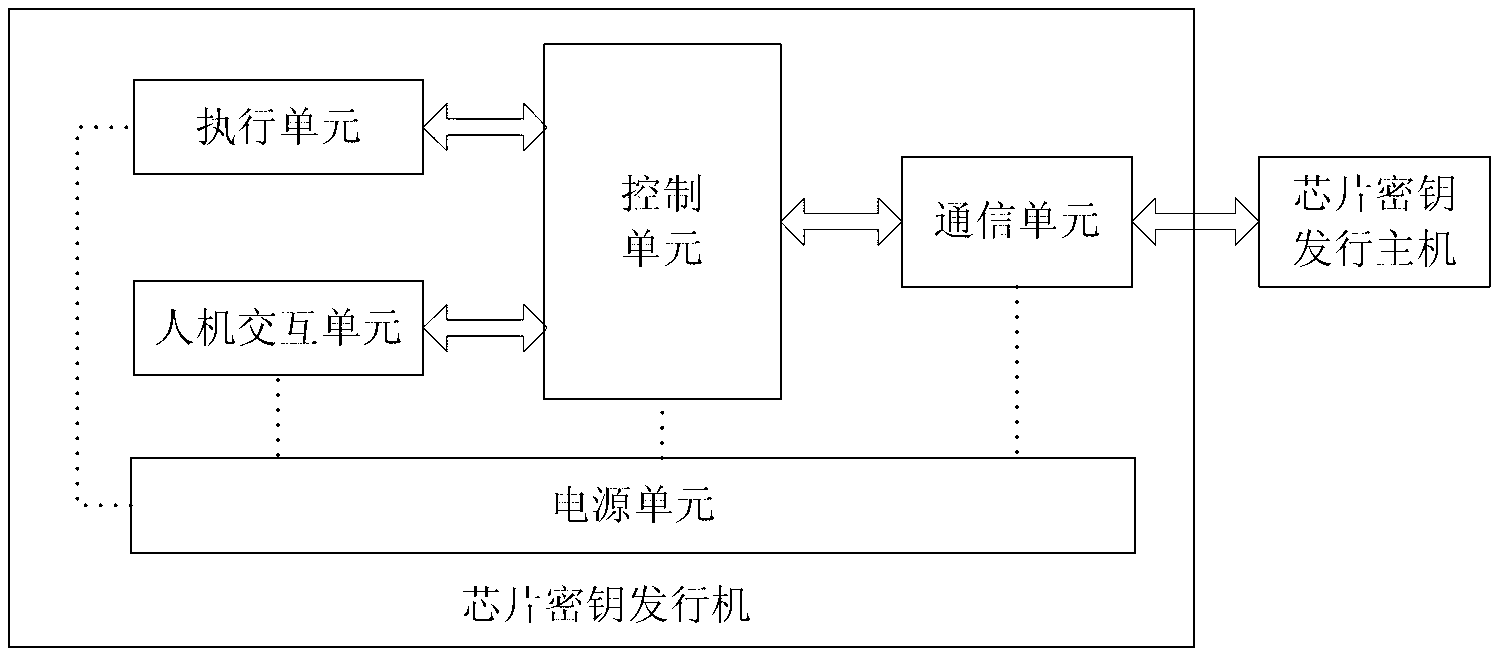
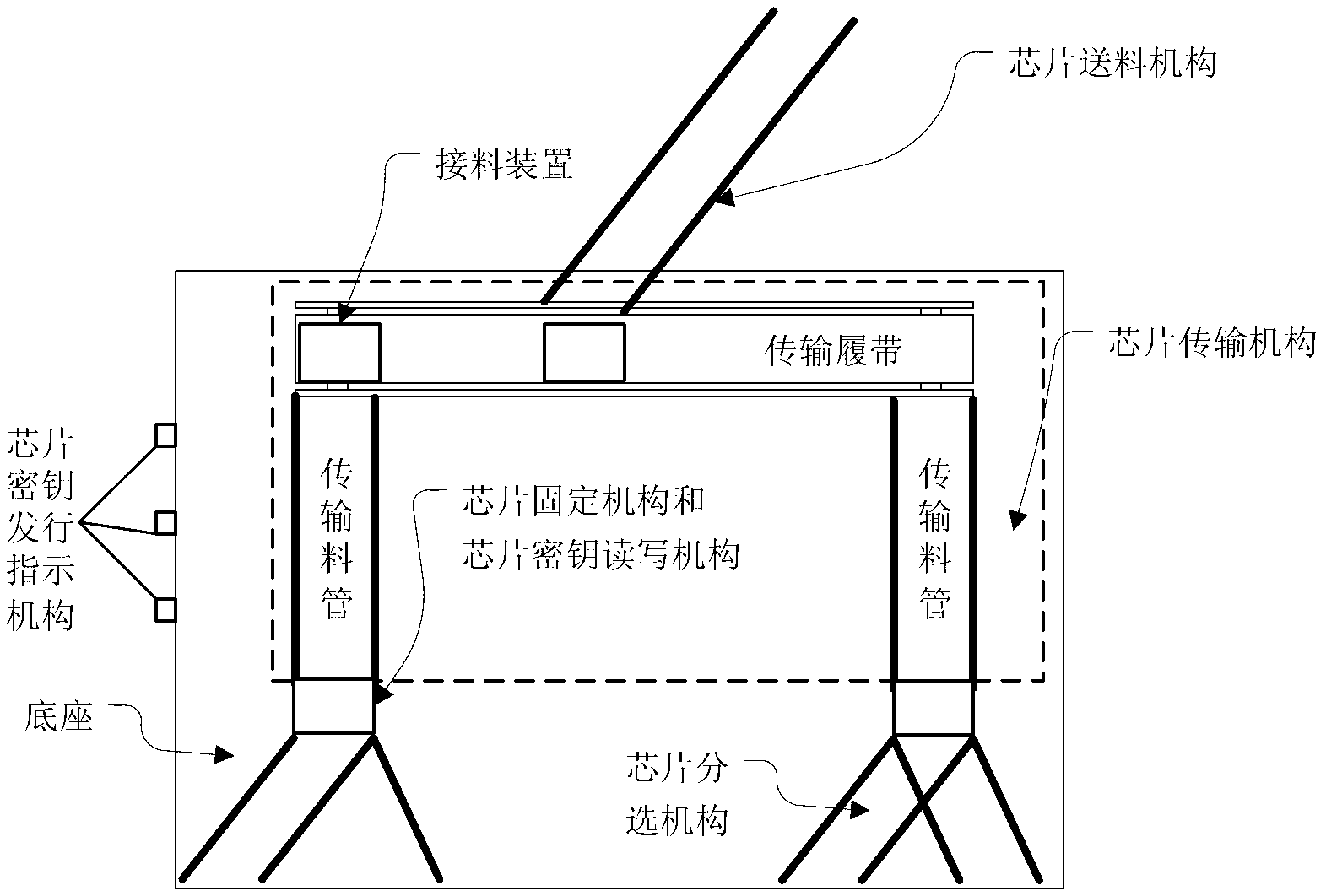
Secure chip key issuing system and secure chip key issuing method
ActiveCN103178953ASimple structureEasy to operateKey distribution for secure communicationTelecommunications linkKey issues
The invention provides a secure chip key issuing system and a secure chip key issuing method. The system comprises a chip key issuer, a chip key issuing mainframe, a key management server and a cipher machine. A certain improvement is made to the chip key issuer and the cipher machine, namely, in the chip key issuer, a chip key reading-writing mechanism is directly fixed on the chip key issuer, and a chip fixing device is embedded in the chip reading-writing mechanism to enable the chip fixing device to be directly in physical connection with a pin of an issued chip so as to effectively prevent information monitoring and key interception of the chip key issuer from the outside. In the system and the method, a secure chip and the cipher machine of the chip key issuer are supportive of the symmetric encryption technology and the asymmetric encryption technology and have a data encryption and decryption operation function, an SSL (safety session link) is established between the chip key issuer and a server cipher machine by performing session key negotiation through the symmetric encryption technology and the asymmetric encryption technology, and safety of a chip key issuing system is effectively improved.
Owner:CHINA ELECTRIC POWER RES INST +1
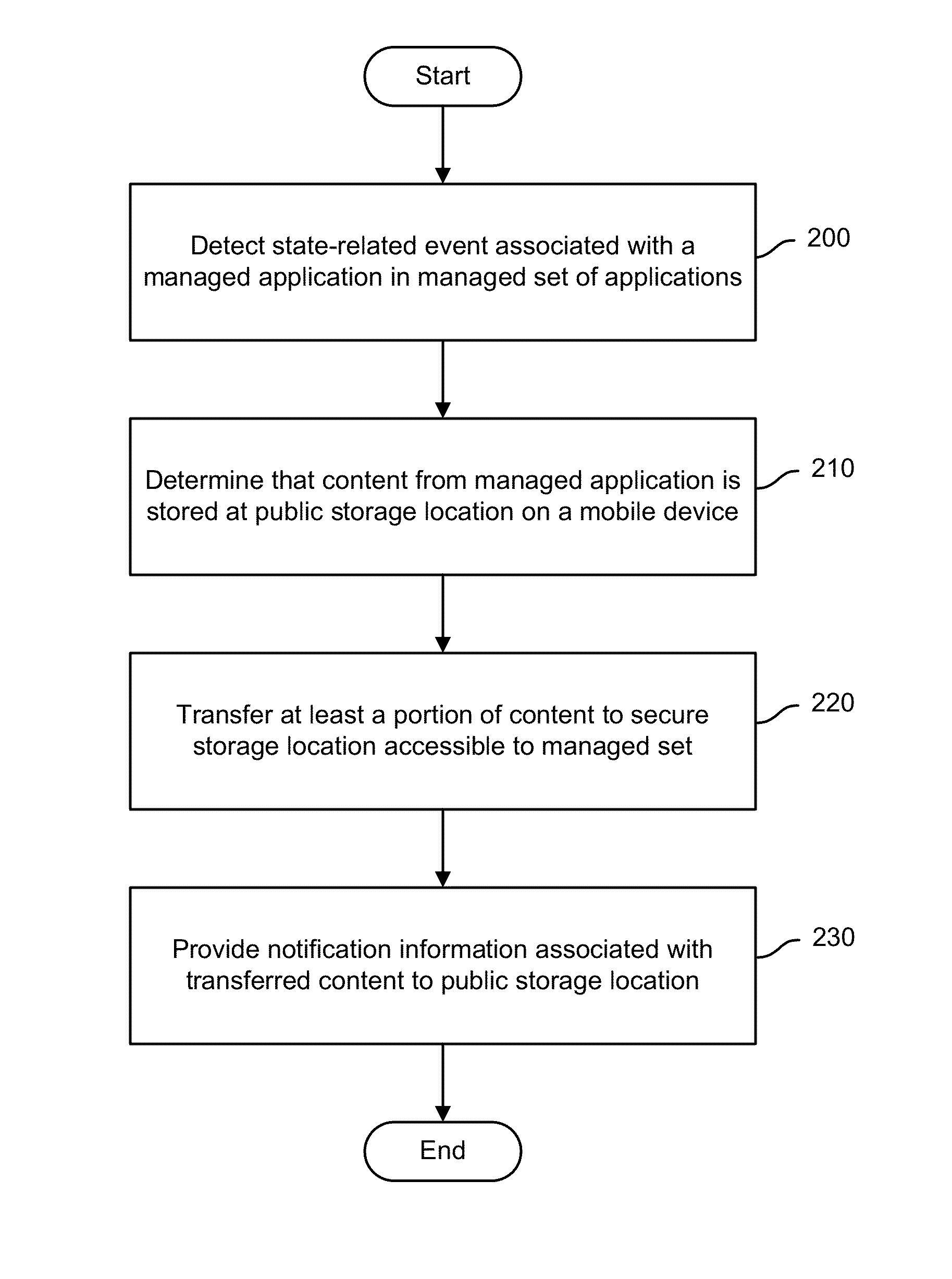
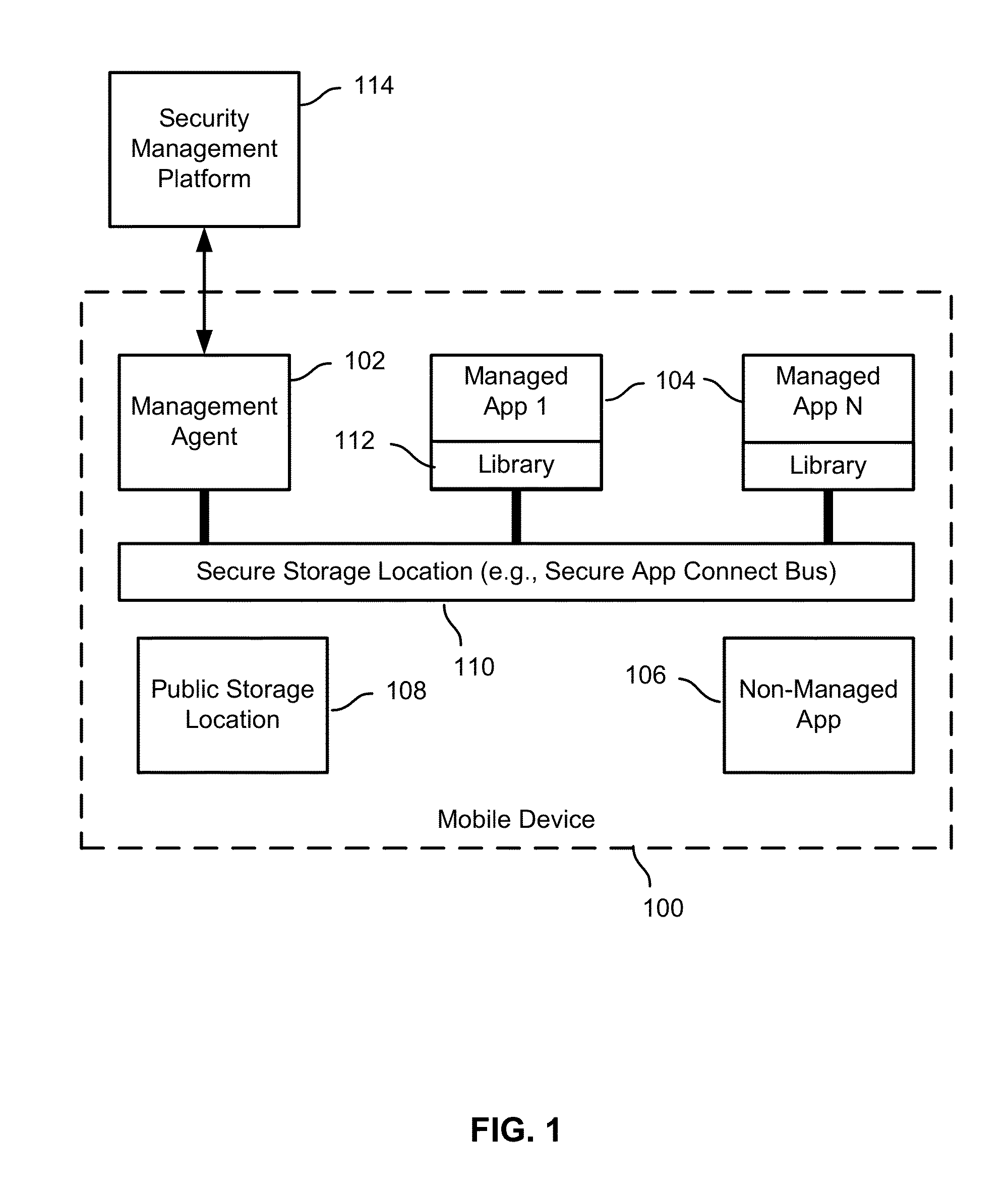
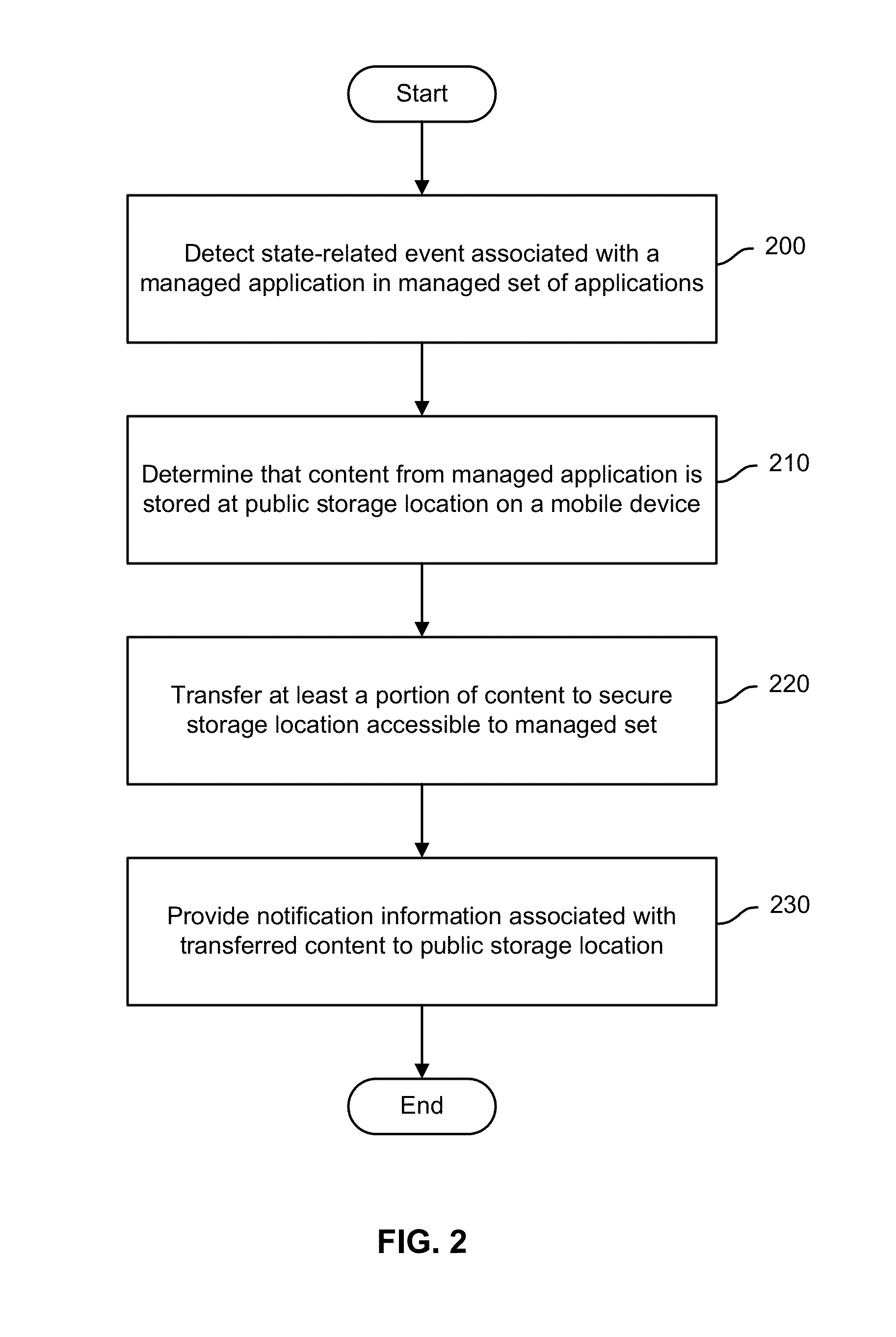
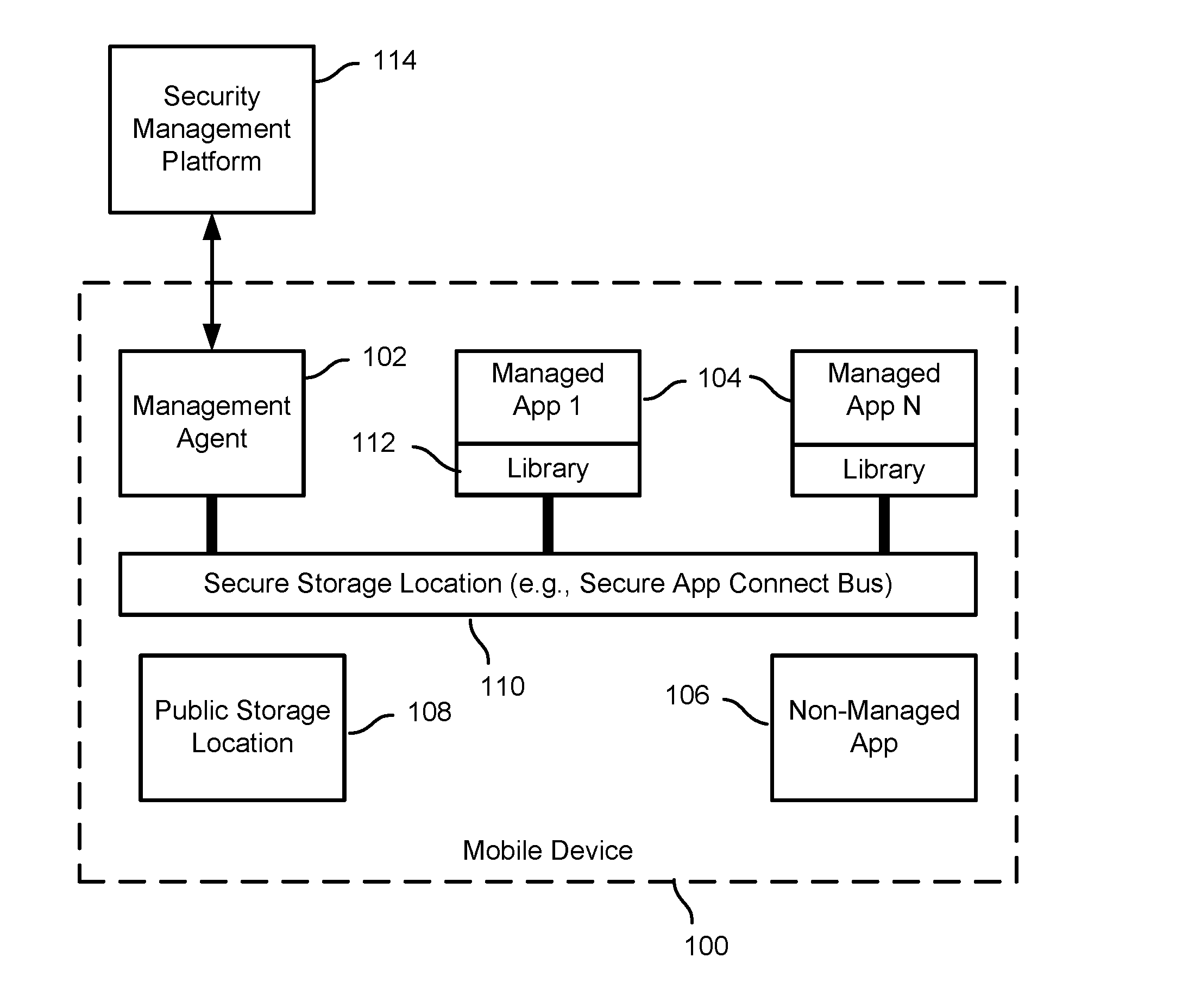
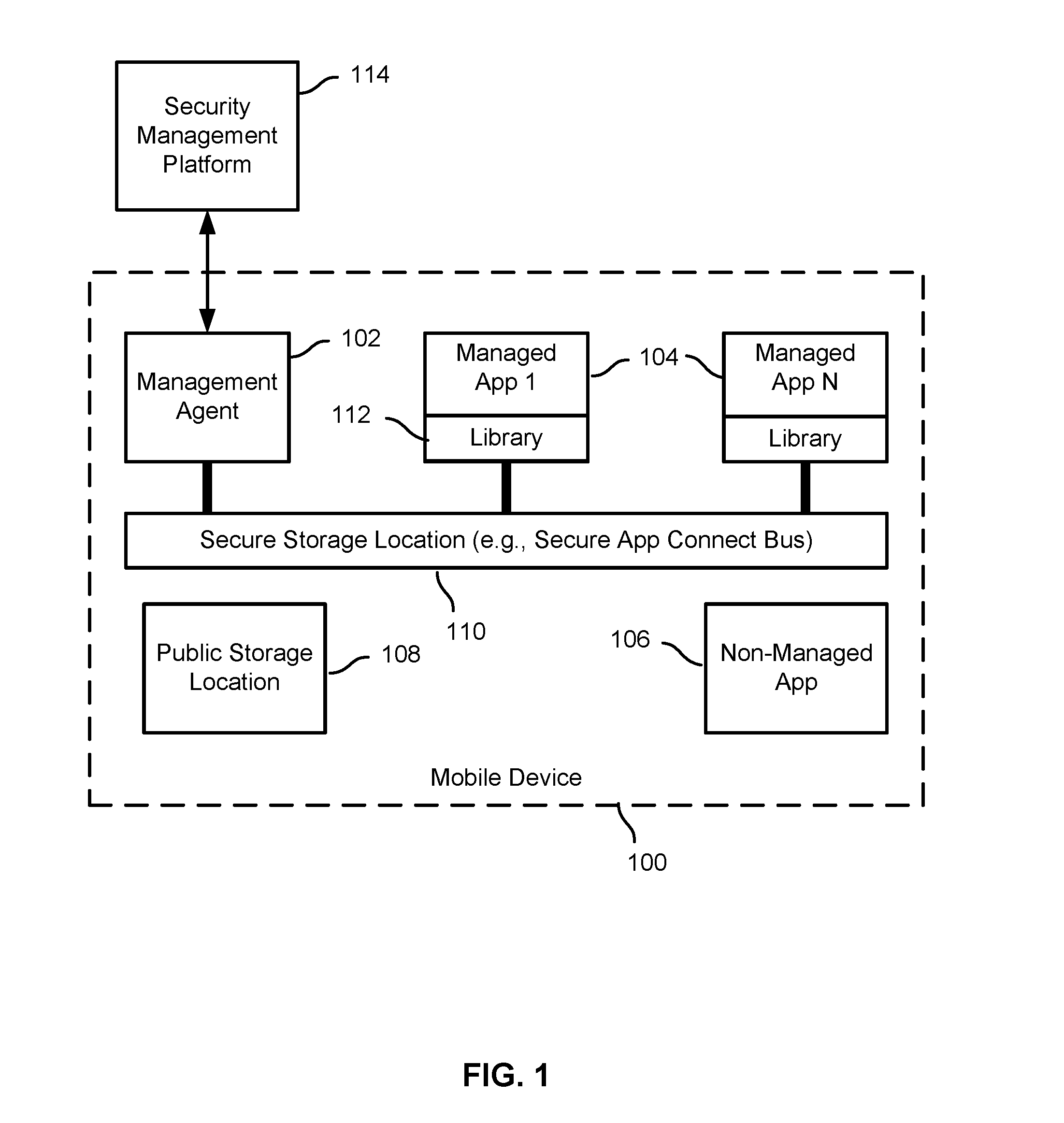
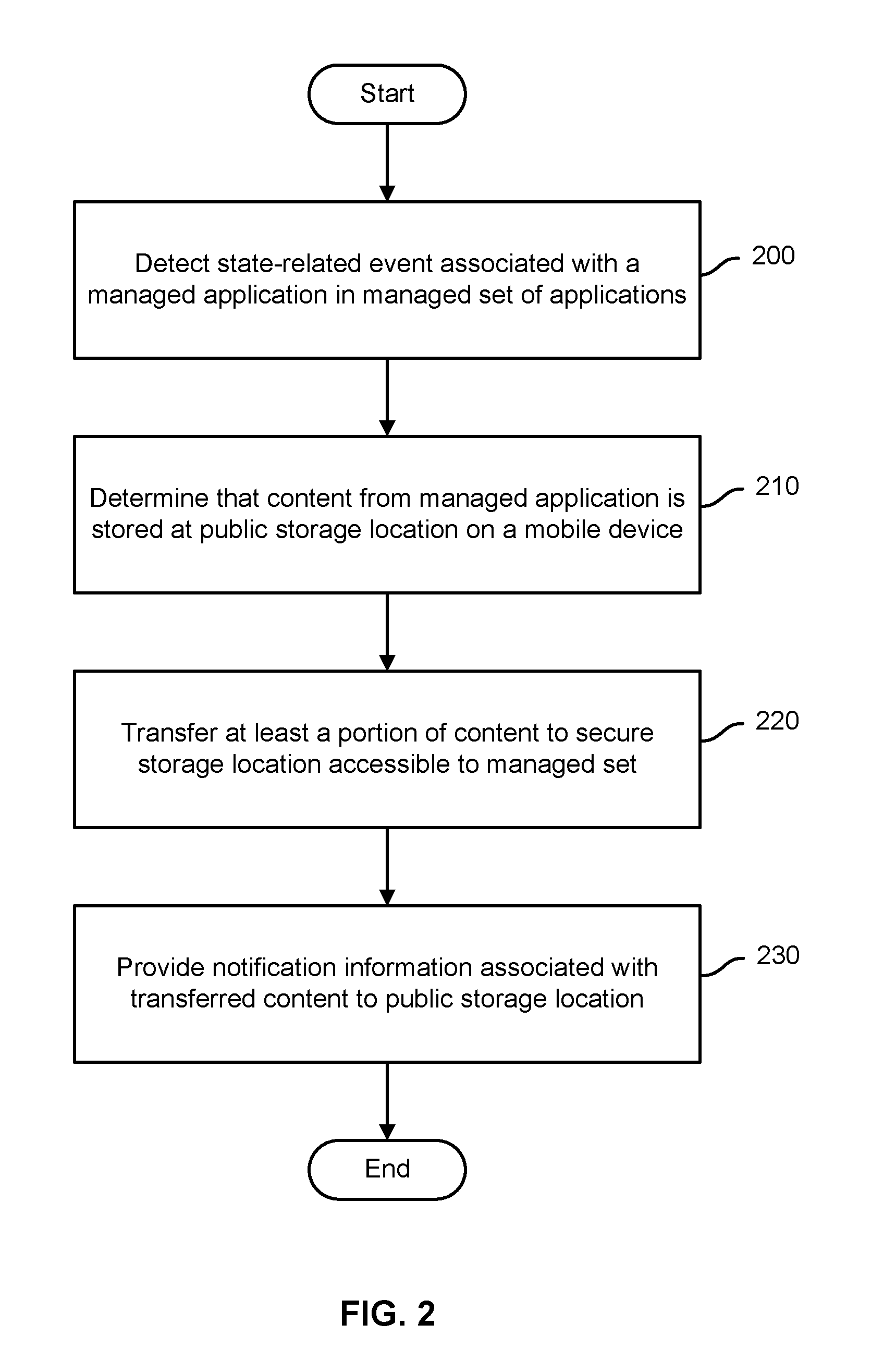
Secure copy and paste of mobile app data
ActiveUS9235717B1Digital data processing detailsInterprogram communicationMobile appsState dependent
Secure transfer of mobile application content is disclosed. A state-related event associated with a managed application in a managed set of applications may be detected. It may be determined that content from the managed application is stored at a public storage location on a mobile device. At least a portion of the content may be transferred to a secure storage location accessible to the managed set.
Owner:IVANTI INC
Initialization of a microprocessor providing for execution of secure code
ActiveUS20090292929A1Safety arrangmentsEncryption apparatus with shift registers/memoriesDirect entrySecure copy
An apparatus including a microprocessor and a secure non-volatile memory. The microprocessor executes non-secure application programs and a secure application program. The microprocessor has secure execution mode initialization logic and an authorized public key. The secure execution mode initialization logic provides for initialization of a secure execution mode within the microprocessor. The secure execution mode initialization logic employs an asymmetric key algorithm to decrypt an enable parameter directing entry into the secure execution mode. The authorized public key is used to decrypt the enable parameter, the enable parameter having been encrypted according to the asymmetric key algorithm using an authorized private key that corresponds to the authorized public key. The secure non-volatile memory stores the secure application program, where transactions over the private bus between the microprocessor and the secure non-volatile memory are isolated from the system bus and corresponding system bus resources within the microprocessor.
Owner:VIA TECH INC
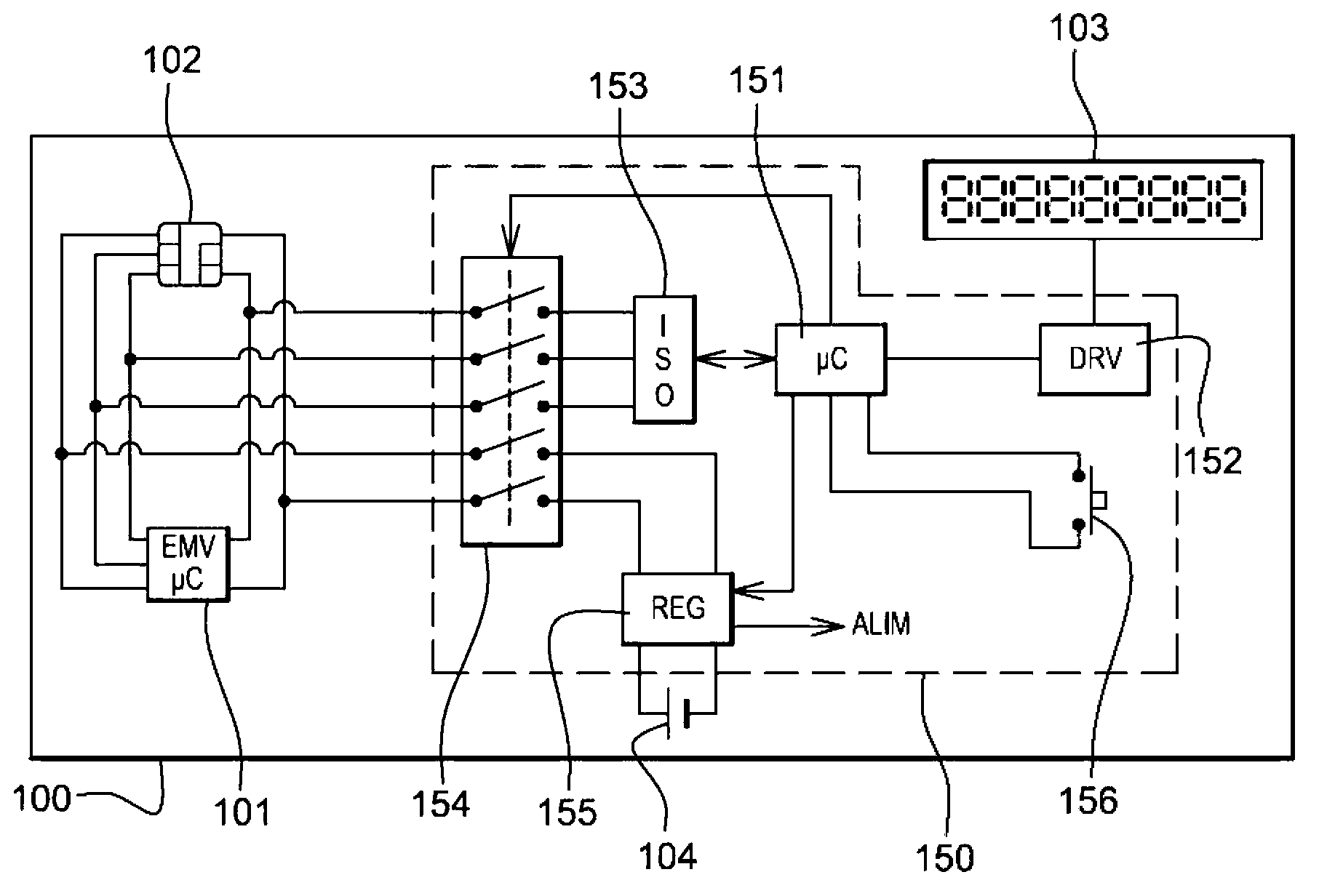
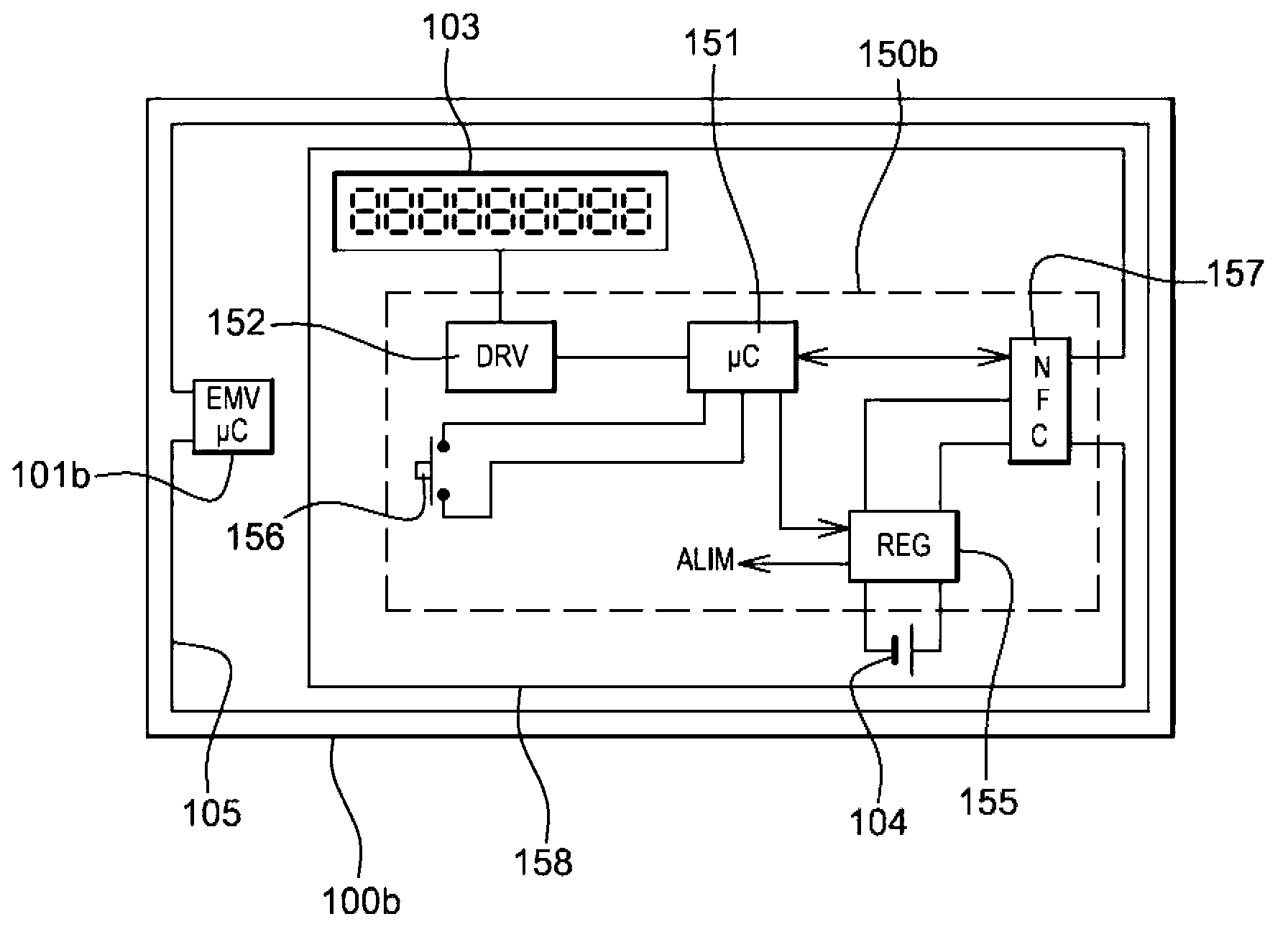
Bank card with display screen
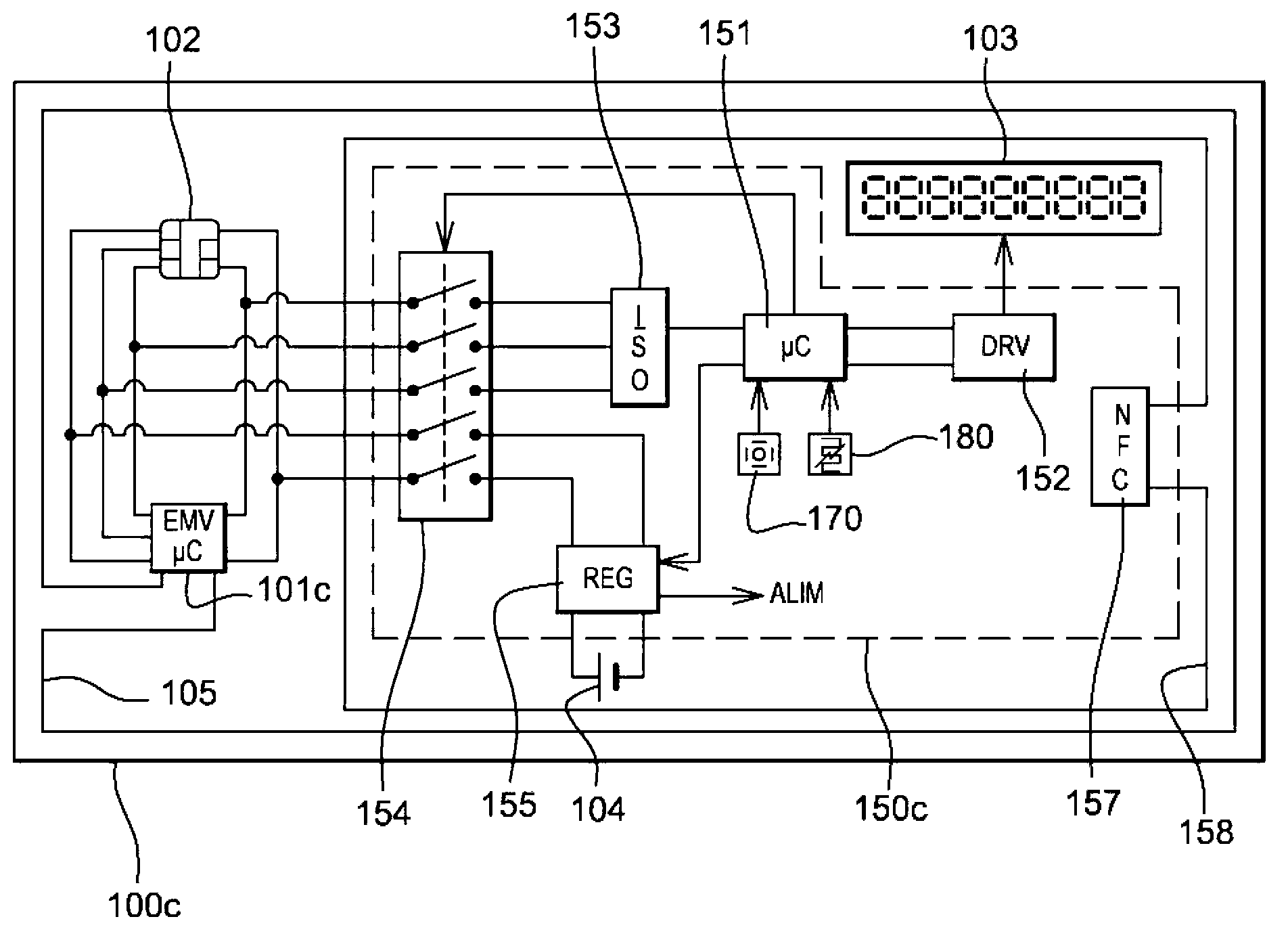
ActiveUS8794535B2Record carriers used with machinesVerifying markings correctnessCommunication interfaceDisplay device
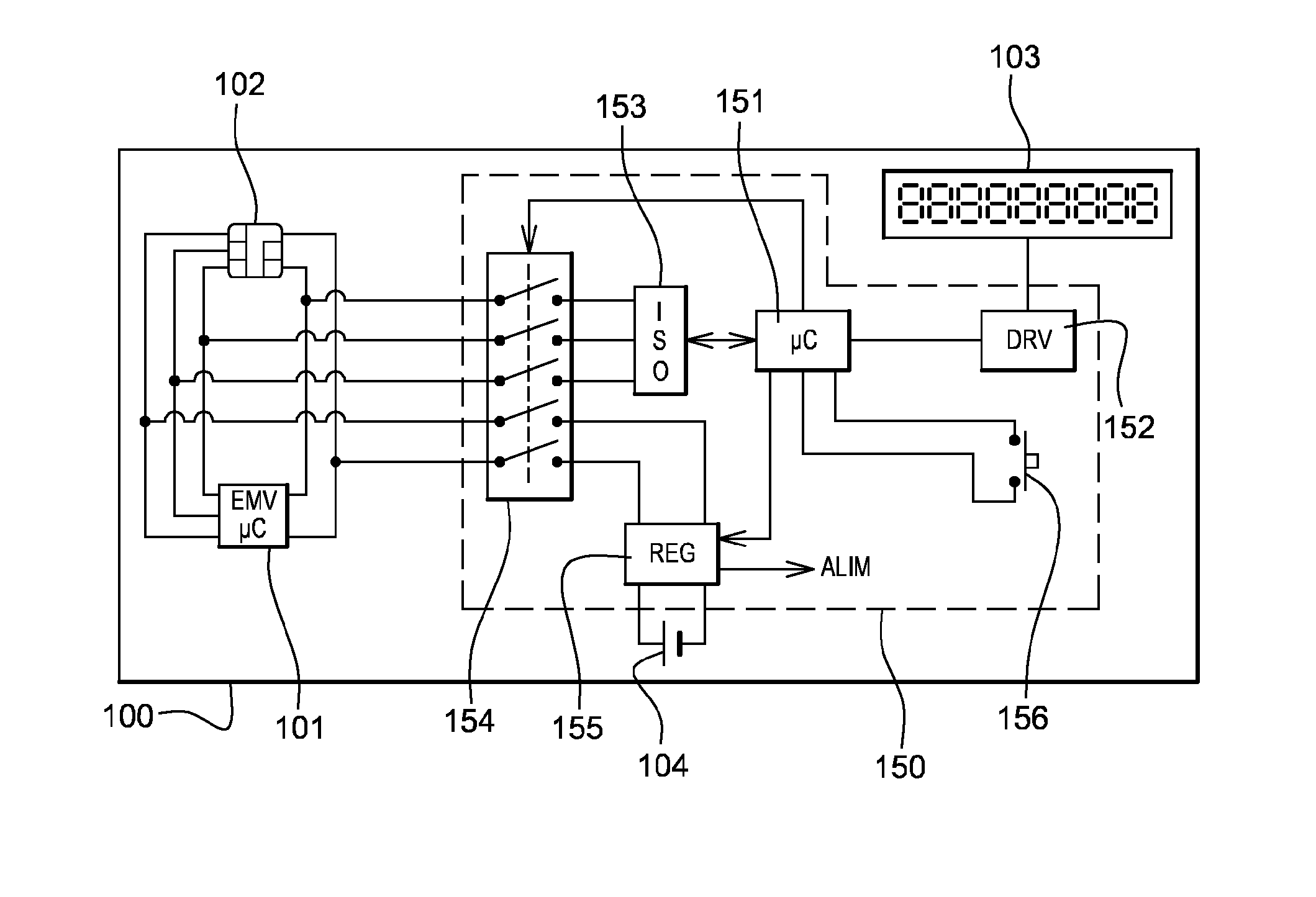
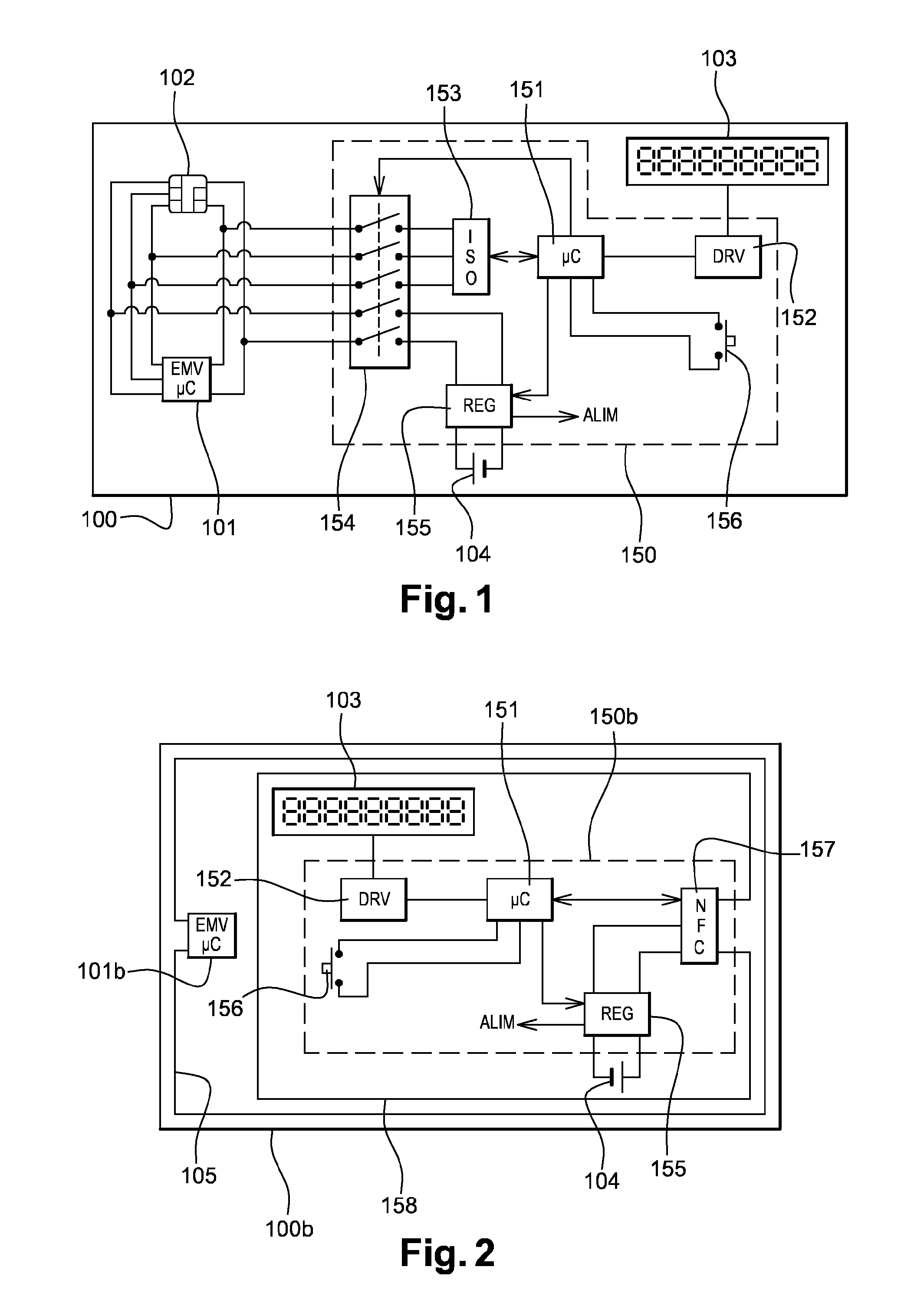
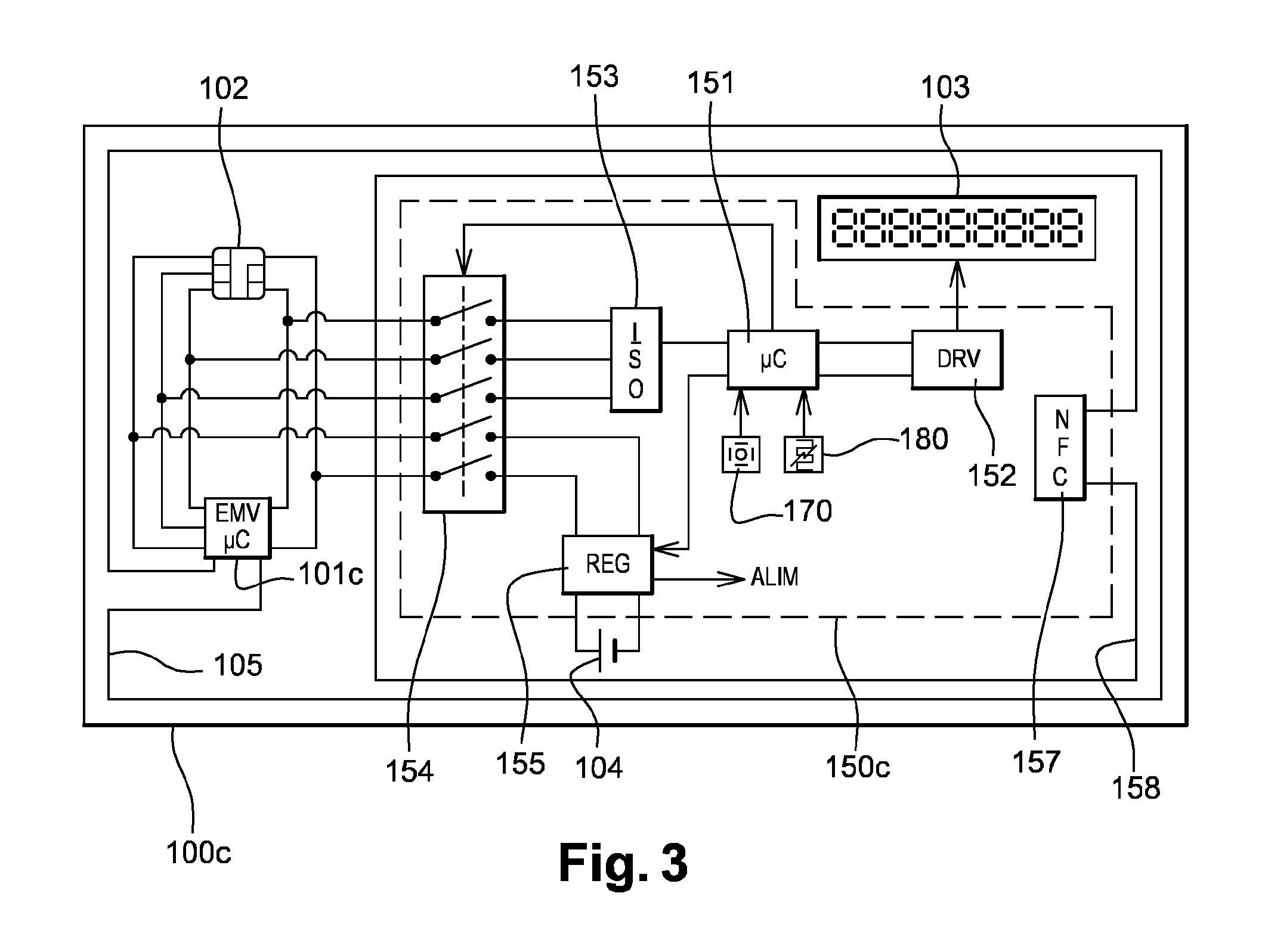
In order to allow a display of the latest transactions, a smart card 100c for secure transactions comprises at least one secure chip 101c, for example of the EMV type, with at least one communication interface to communicate with a card reader in order to carry out a transaction, an electronic display 103, an independent battery 104, a card reader circuit 150c connected to a communication interface of the secure chip in order to access the information contained in the secure chip to be able to display it on the display.
Owner:GEMPLU
Secure channel indication lamp operation state certification mechanism
The present invention relates to a secure channel indication lamp operation state certification mechanism. The mechanism comprises: a secure channel indication lamp arranged above a secure channel ofa stage and configured to display a secure icon corresponding to the secure channel by employing a green background to indicate the position of the secure channel to audiences; a control switch connected with the secure channel indication lamp and arranged above the secure channel of the stage and configured to control the on or off of the secure channel indication lamp; a scene video mechanism configured to perform video operation facing the secure channel of the stage to obtain and output a corresponding secure channel entrance image; and a brightness extraction device connected with the scene video mechanism and configured to emit scene transfer signals when the difference of the whole brightness value of the secure channel entrance image and the whole brightness value of the standard scene image exceeds a preset brightness difference threshold value. The efficiency of stage device certification is improved.
Owner:ZHEJIANG DAFENG IND
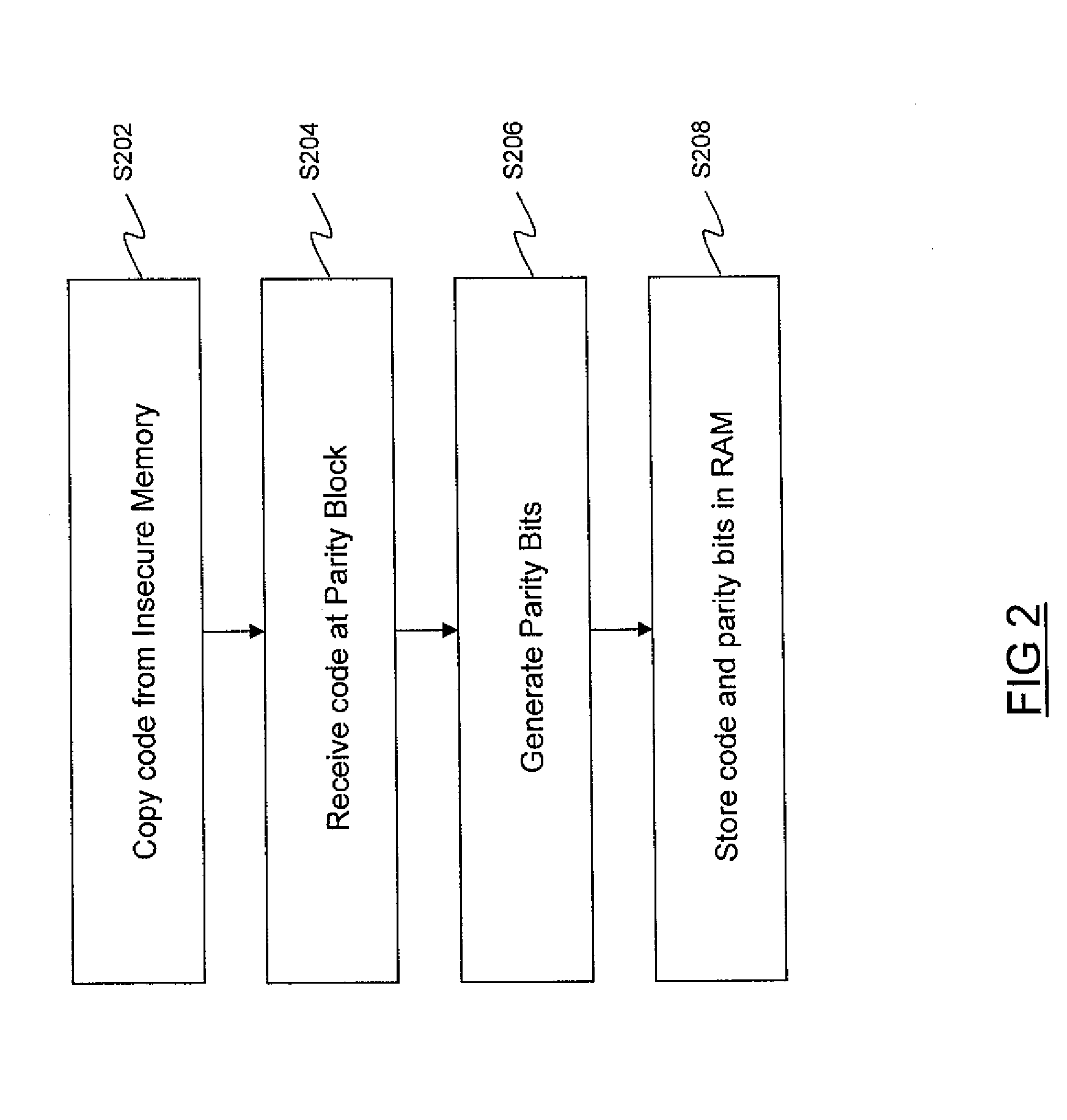
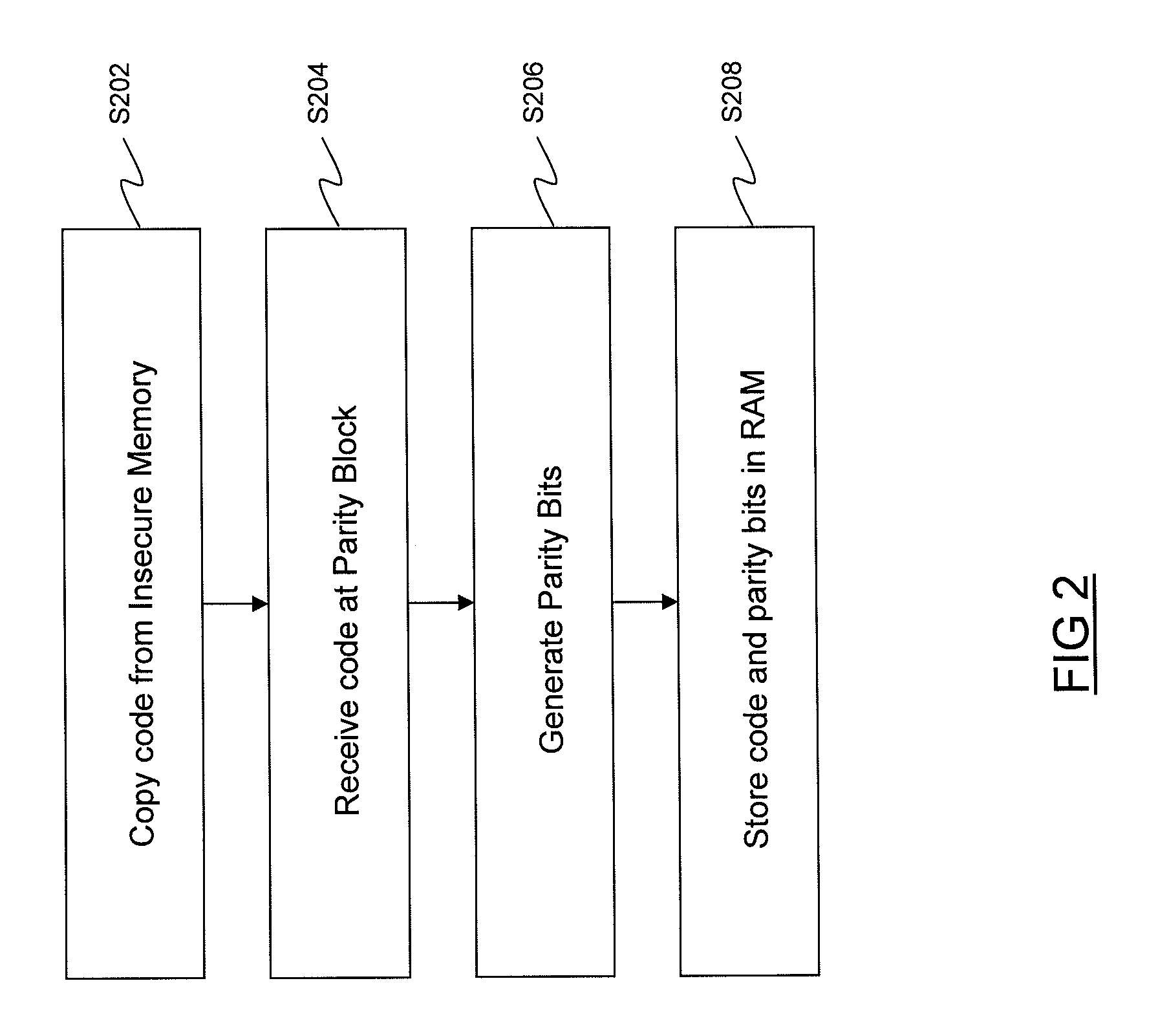
Loading secure code into a memory
ActiveUS20110004807A1Authenticity of the code can be verifiedProvide protectionError preventionTransmission systemsComputer hardwareSecure copy
A method of verifying the integrity of code in a programmable memory, the method including: receiving the code from an insecure memory; generating error detection bits for the code as it is received from the insecure memory; storing the code and the error detection bits in the programmable memory; and verifying the integrity of the code stored in the programmable memory by performing an authentication check on the code and the error detection bits stored in the programmable memory.
Owner:STMICROELECTRONICS (RES & DEV) LTD
Bank card with display screen
To allow the display of the latest transactions, a chip card 100c for secure transaction comprises at least one secure chip 101c, for example of EMV type, furnished with at least one communication interface so as to be able to communicate with a card reader so as to perform a transaction, an electronic display 103, an autonomous battery 104, a card reader circuit 150c connected to a communication interface of the secure chip so as to be able to access information contained in the secure chip so as to be able to display same on the display.
Owner:GEMPLU
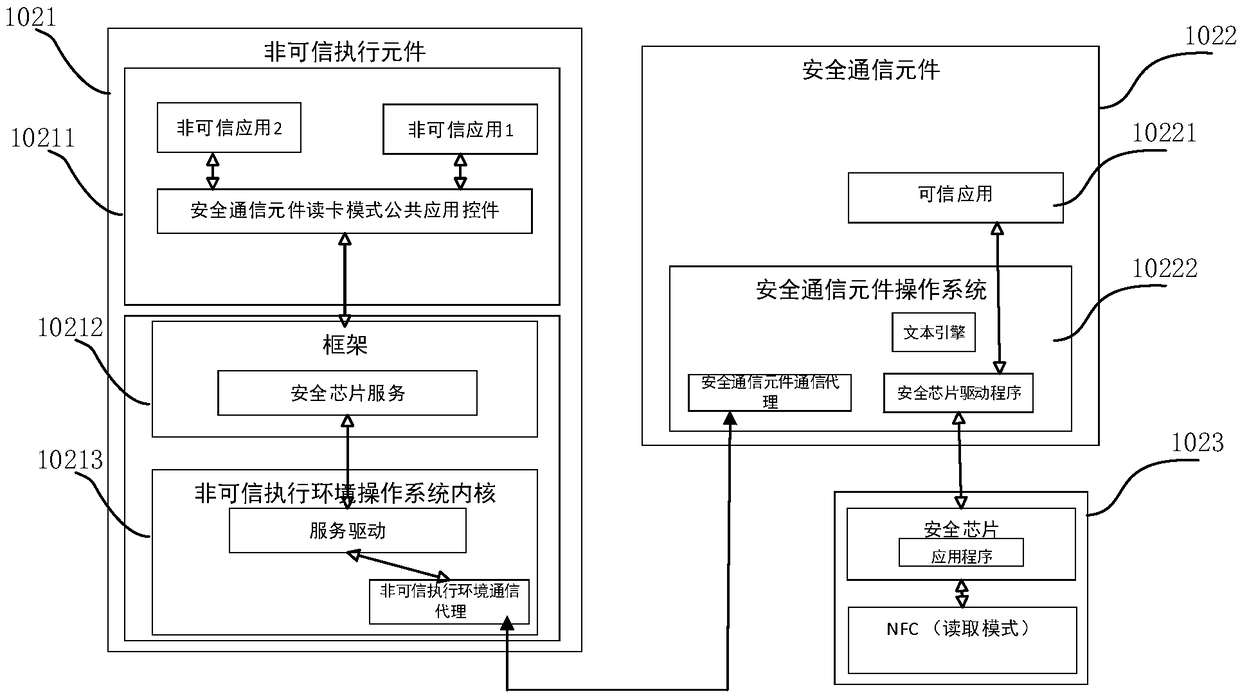
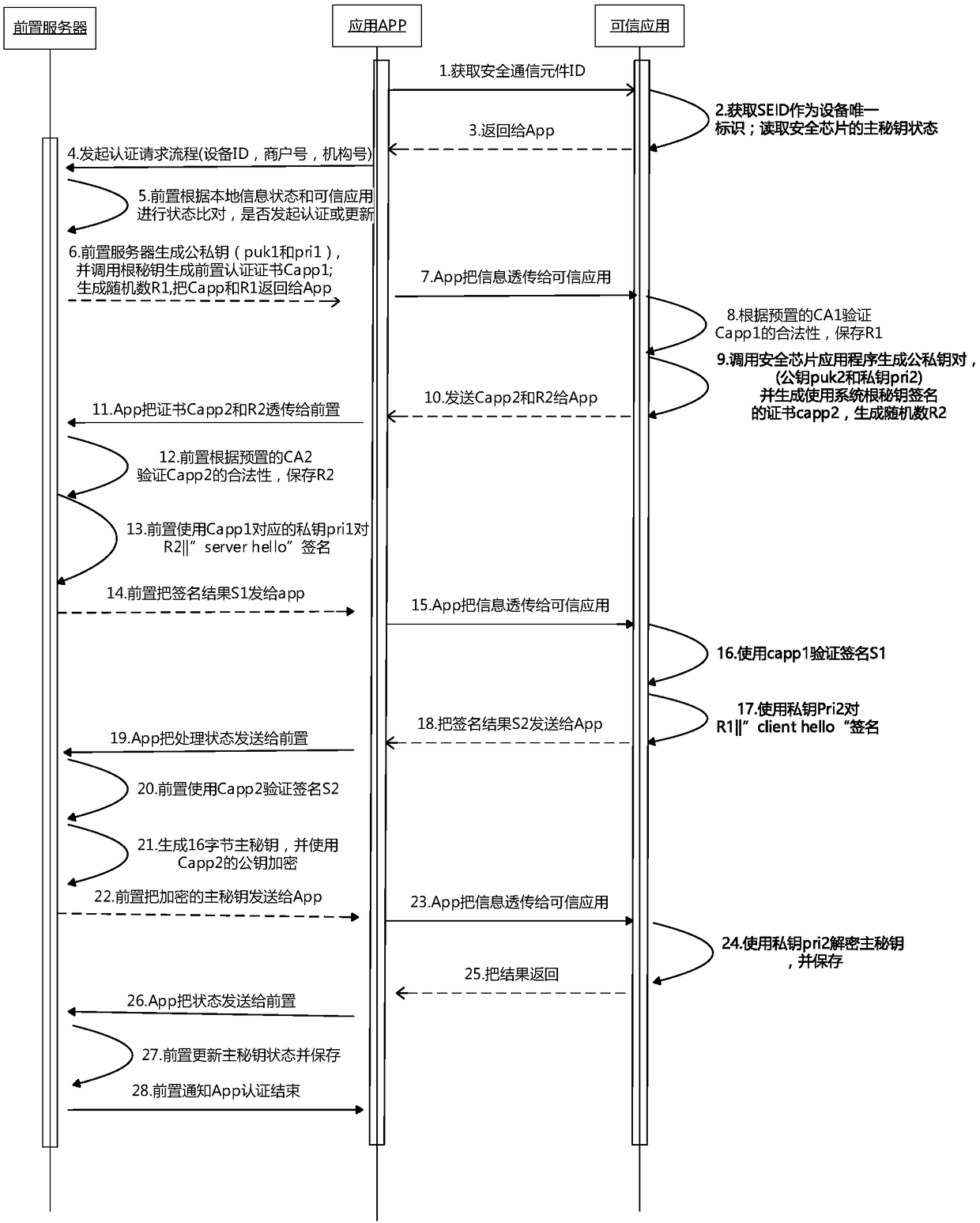
Secure card communication method based on credible environment, and mobile terminal
ActiveCN108924822AConsistent effectKey distribution for secure communicationSecurity arrangementSecure communicationSecure copy
The invention discloses a secure card communication method based on a credible environment. The method is applied to a mobile terminal with a secure chip and a secure communication element, and comprises the steps as follows: in response to wireless communication information sent by a physical card, the secure chip encrypts the received wireless communication information; the encrypted wireless communication information is sent to the secure communication element; and the secure communication element forwards the wireless communication information to a public application. The secure card communication method based on the credible environment provided by the invention is applied to the field of secure accesses.
Owner:JIANGSU HENGBAO INTELLIGENT SYST TECH CO LTD
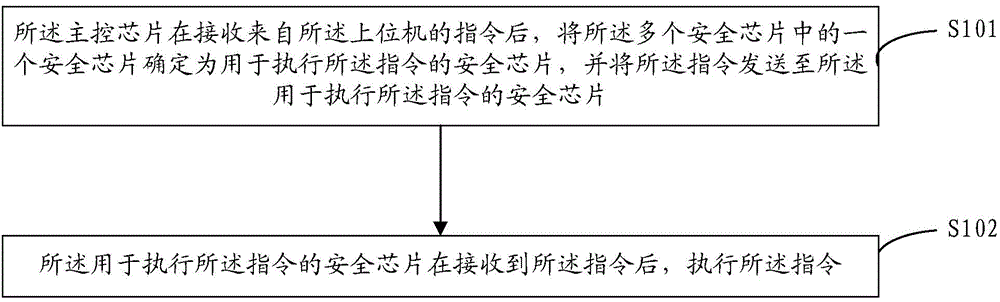
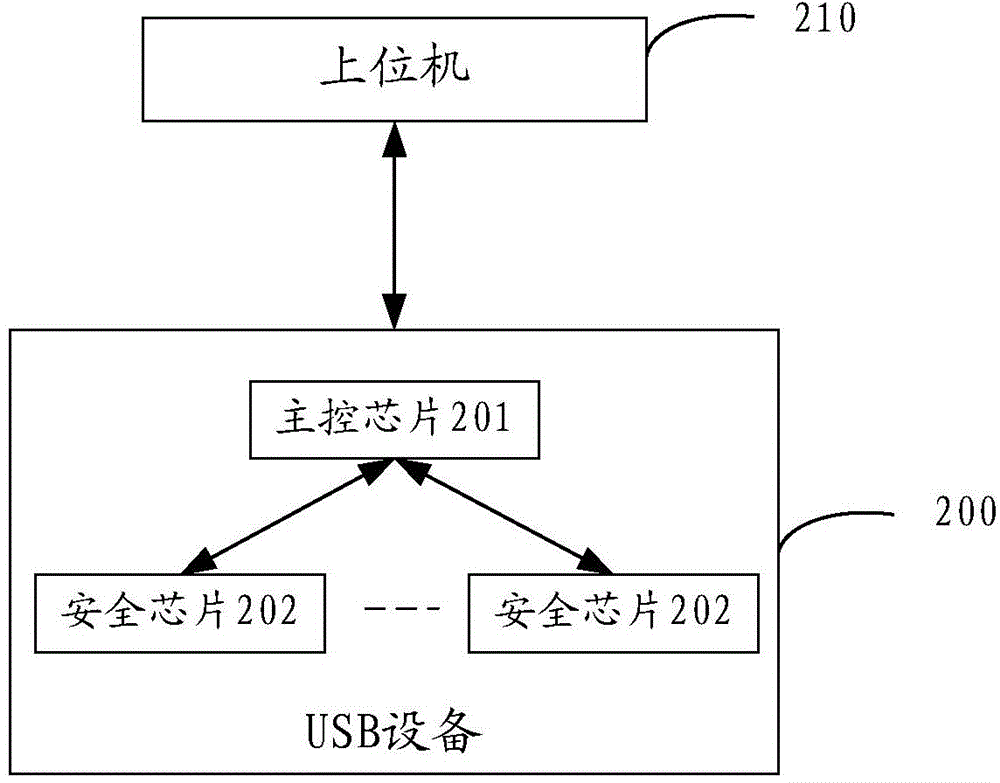
Data processing method for USB equipment and USB equipment
The embodiment of the invention discloses a data processing method for the USB equipment. The USB equipment is connected with an upper computer through a USB interface and comprises a main control chip and a plurality of security chips. The method comprises the following steps: after receiving an instruction from the upper computer, the main control chip determines one of the security chips to be a secure chip for executing the instruction and transmits the instruction to the security chip executing the instruction; and after receiving the instruction, the security chip used for executing the instruction executes the instruction. The concurrent operation is implemented through the plurality of security chips, the arithmetic speed of a cryptographic algorithm is increased, and meanwhile, the additional problems of high cost or high calorific value are also avoided.
Owner:WATCHDATA SYST
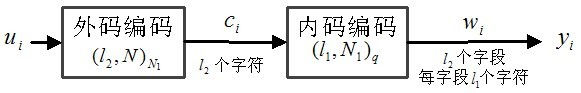
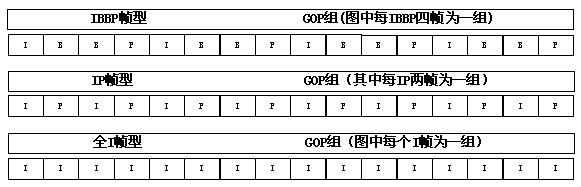
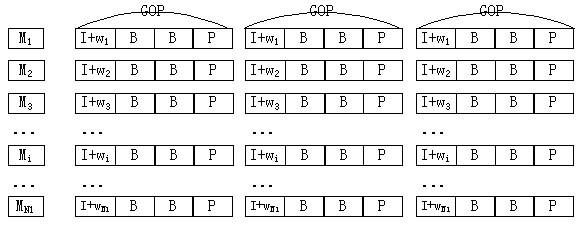
Quickly generating method of user copy based on video GOP (Group of Picture)
InactiveCN101976323AQuick buildShorten the timeDigital data protectionTelevision systemsGroup of picturesComputer graphics (images)
The invention relates to the technical field of digital content safety protection, in particular to a quickly generating method of a user copy based on a video GOP (Group of Picture), which is based on a cascade fingerprint code technology. The user-copy generating process comprises the following steps of: generating female copy video source files according to an internal code sequence of a fingerprint code; according to an external code of a user, sequentially extracting corresponding image block groups from the corresponding female copy video source files; and generating an only user copy by combining and splitting the GOP image block groups. The invention reduces time for generating a user video copy to time for copying a video resource from time for coding a video resource, can quickly generate large numbers of video copies in short time and is suitable for a real-time on-line publication system of audio-video works which face to large-scale users. The provided algorithm of the invention has good universality and good practicability and can be suitable for common video coding standards, such as H.264, MPEG(Motion Picture Experts Group)-2, MPEG-4, AVS (Advanced Visual System), and the like.
Owner:WUHAN UNIV
Secure body of memory card reader
ActiveUS9871375B2Easy to assemblePossible to fixCasings/cabinets/drawers detailsSensing by galvanic contactsCard readerSecure copy
A body of a memory card reader, which has an overall rectangular parallelepiped shape including a slot for inserting a memory card. The reader body includes, on a rear surface thereof, a recess for receiving a memory card connector, the receiving recess being of a predetermined volume shape and including at least one conductive track.
Owner:BANKS & ACQUIRERS INT HLDG
Secure copy and paste of mobile app data
ActiveUS20160092690A1Digital data processing detailsAnalogue secracy/subscription systemsMobile appsState dependent
Secure transfer of mobile application content is disclosed. A state-related event associated with a managed application in a managed set of applications may be detected. It may be determined that content from the managed application is stored at a public storage location on a mobile device. At least a portion of the content may be transferred to a secure storage location accessible to the managed set.
Owner:IVANTI INC
Providing method of record carriercomprising encryption indication information, reader and recorder and method
InactiveCN1830030BAccessories for indicating/preventing prior/unwanted useRecord information storageData storingData store
Owner:KONINK PHILIPS ELECTRONICS NV
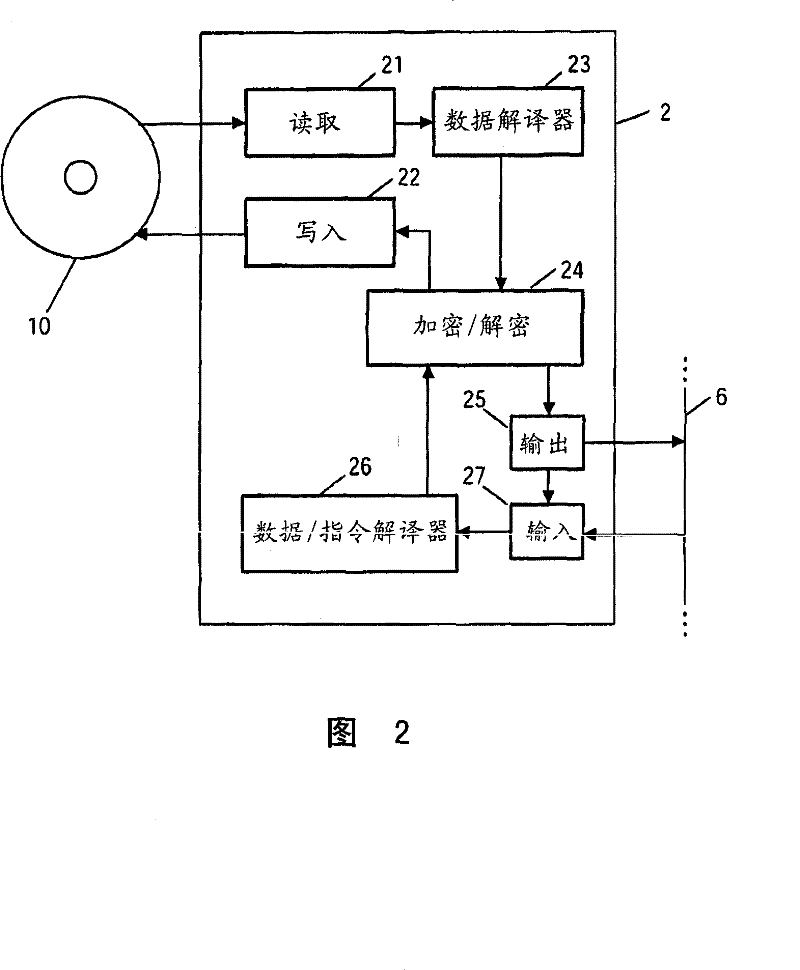
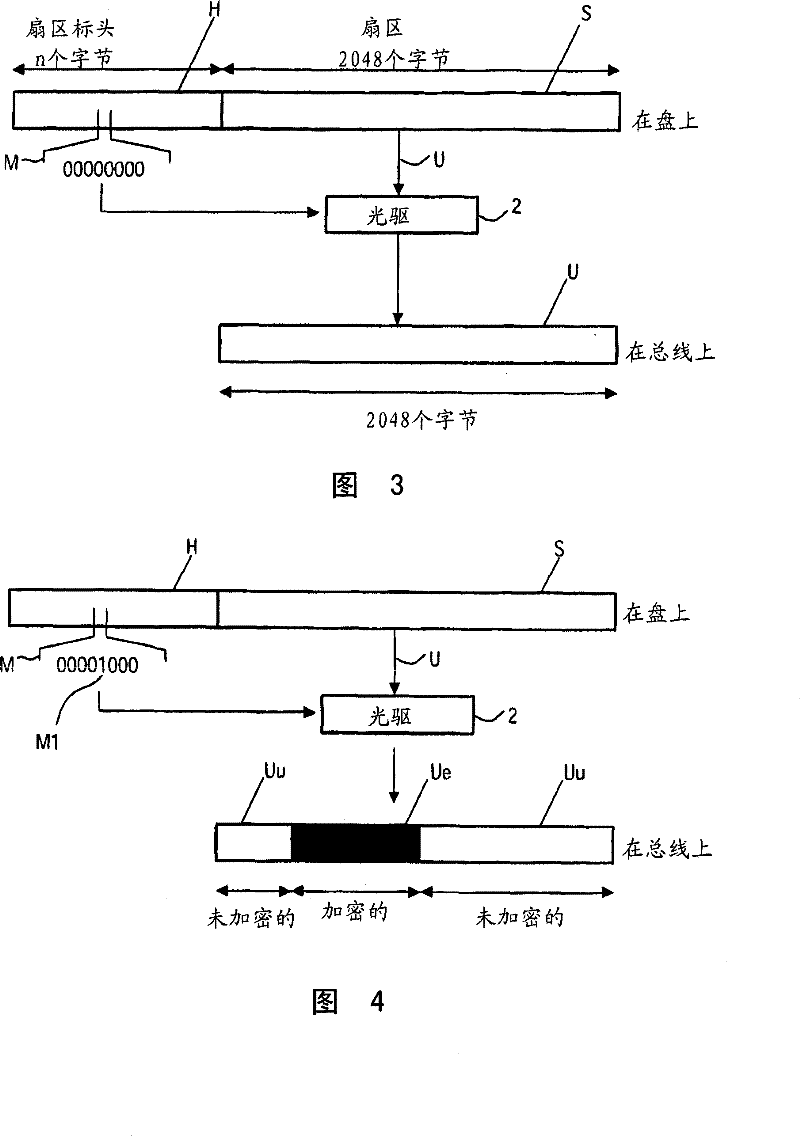
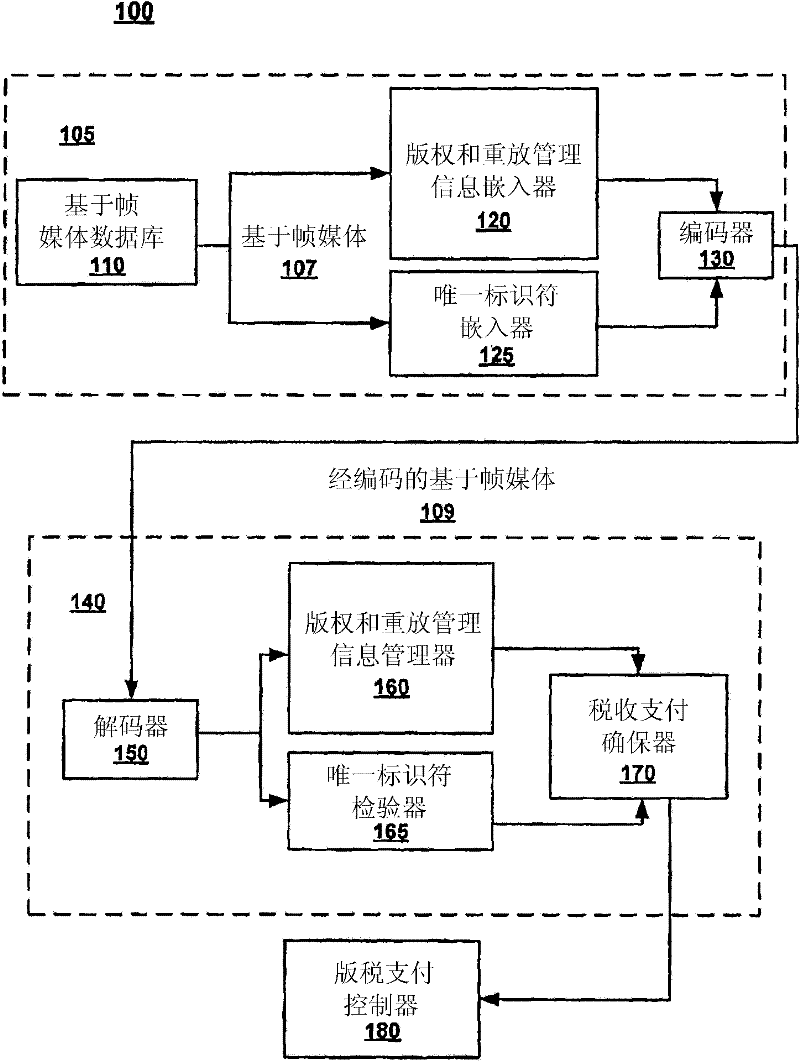
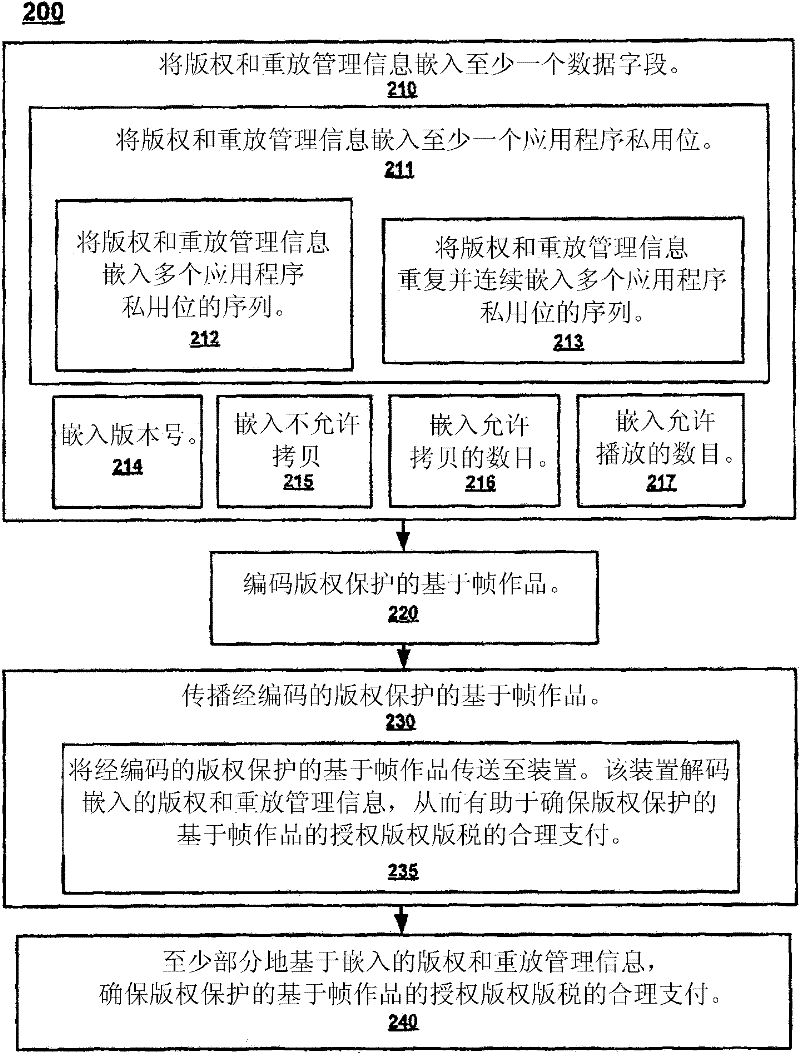
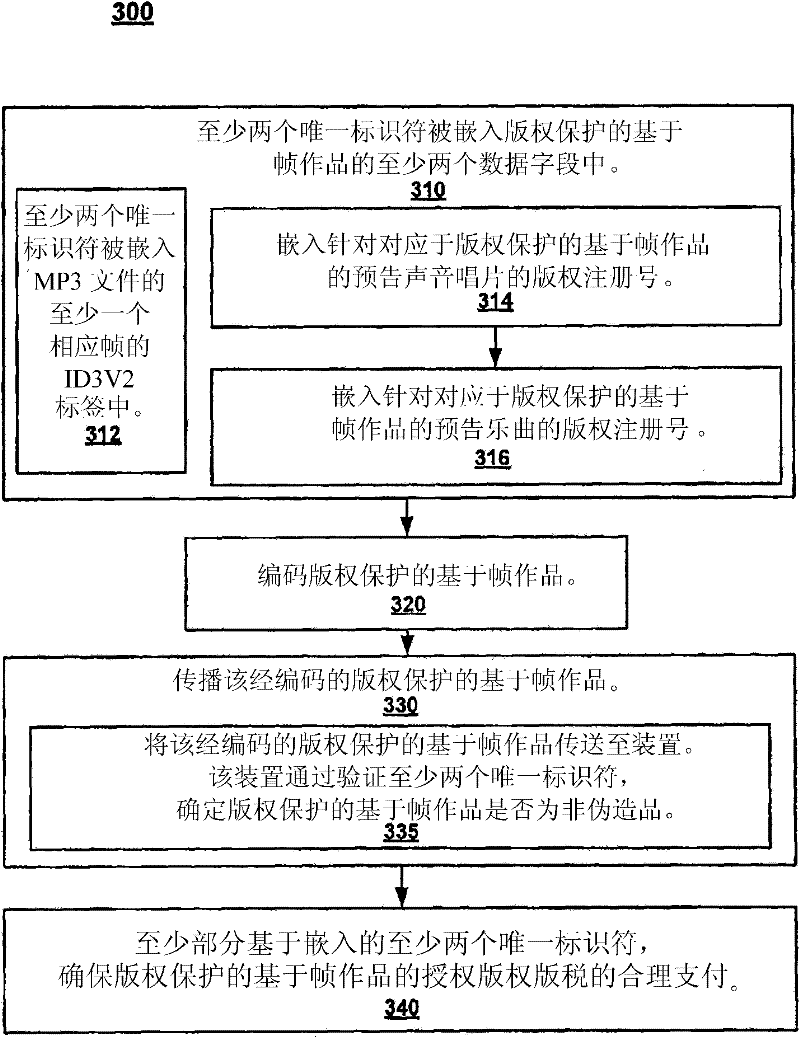
Secure copy and/or playback protection
InactiveCN102449637ARecording carrier detailsRecord information storageFrame basedSerial Copy Management System
A system and method of secure copy and / or playback control of a usage protected frame-based work is disclosed. The method includes accessing serial copy management system information for the usage protected frame-based work. In addition, the method validates the serial copy management system information. Copy management information of the usage protected frame-based work is also accessed. In so doing, the copy management information is utilized to determine if a secure copy / playback application is authorized to generate a copy of the usage protected frame-based work. Thus the copy management information acts as a technological measure which "effectively controls access to a work" by requiring the application of information, with the authority of the copyright owner, to gain access to the work.
Owner:MEDIA RIGHTS TECH
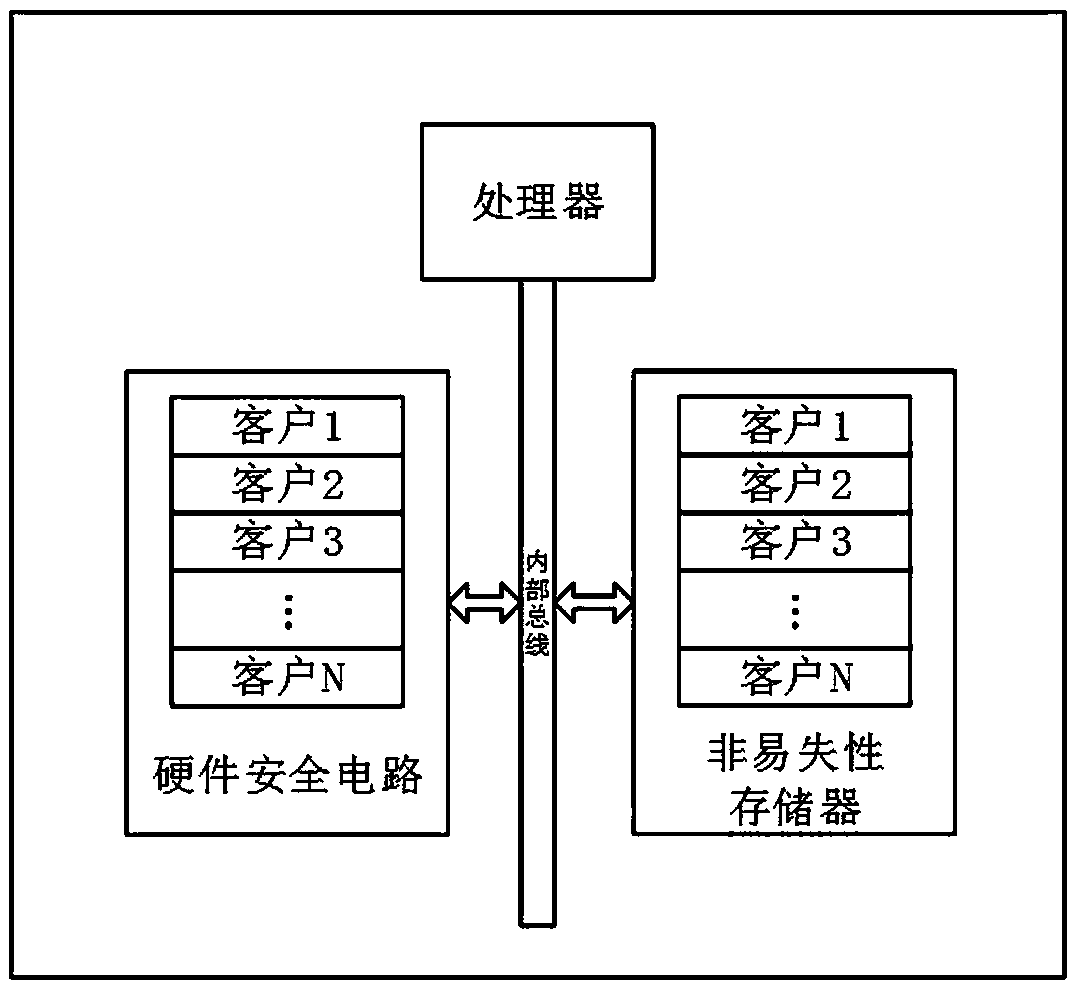
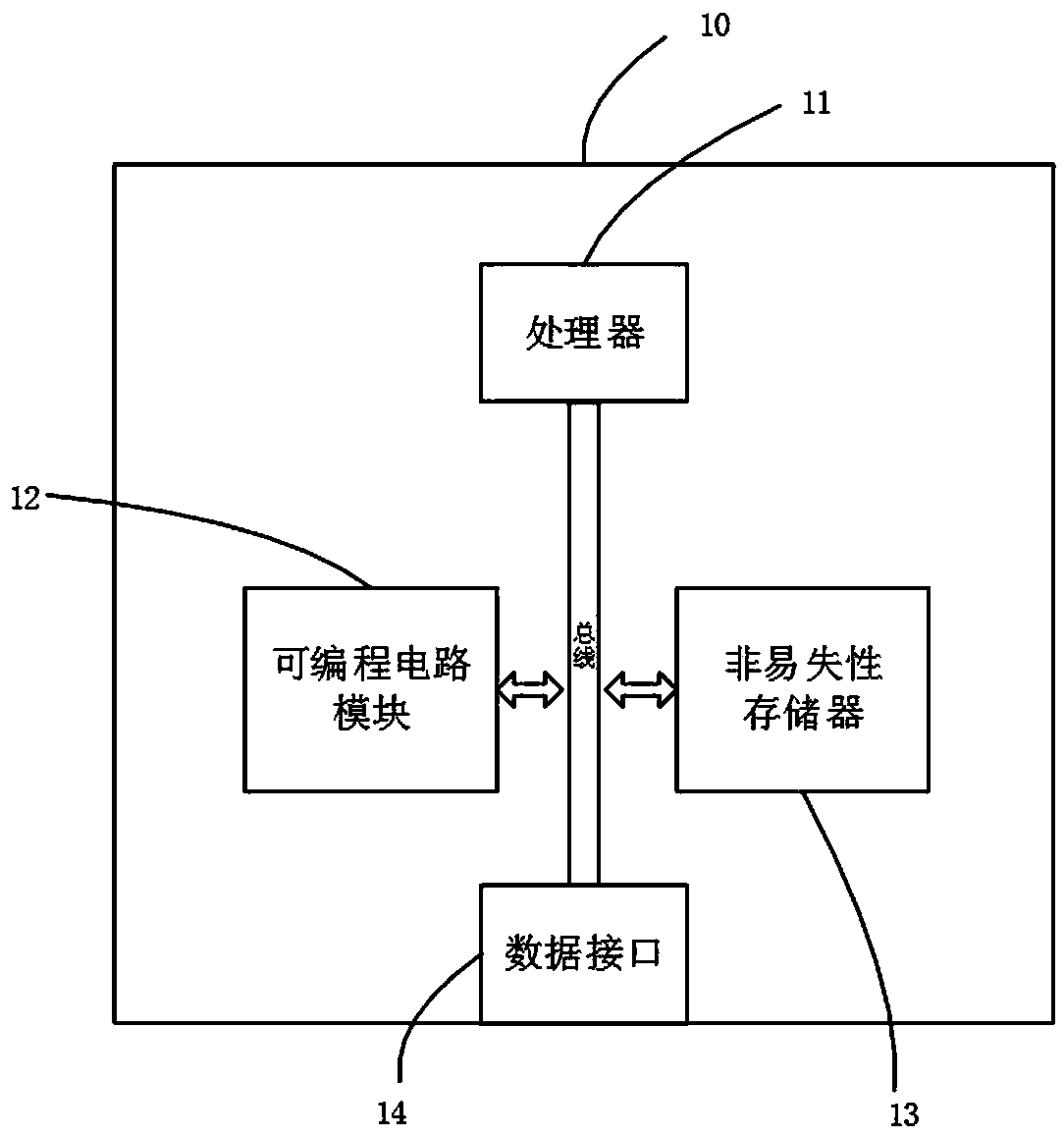
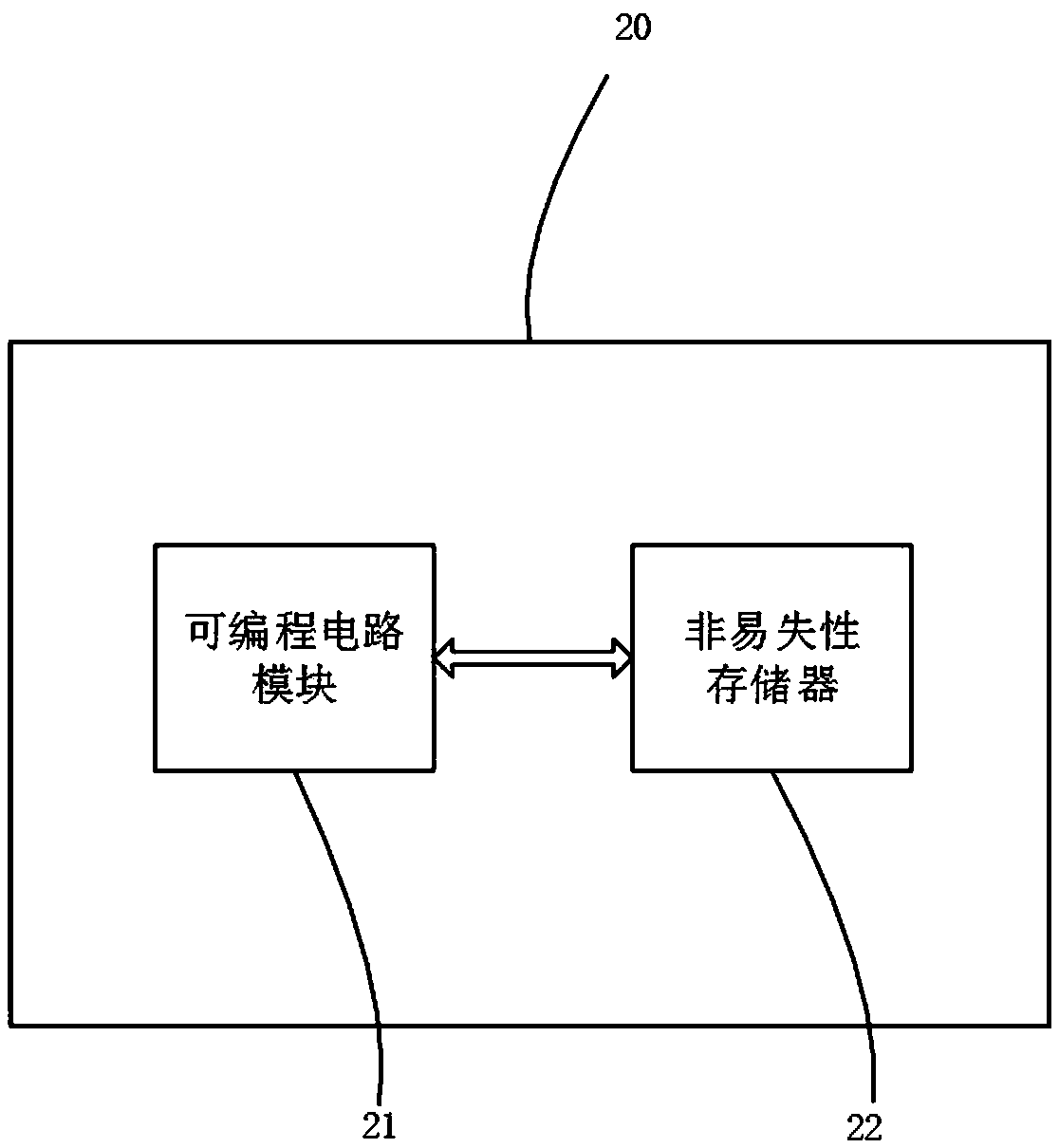
Secure chip
InactiveCN108280372ALow costImprove securityInternal/peripheral component protectionProgrammable circuitsSecure copy
The invention discloses a secure chip. The secure chip comprises a processor, a programmable circuit module and a nonvolatile memory. The programmable circuit module and the nonvolatile memory are connected with the processor through a bus, the programmable circuit module is used for realizing a hardware safety circuit of the secure chip according to a preset configuration file, and the nonvolatile memory is used for storing the preset configuration file. The secure chip is high in safety, and the personable safety circuit of a customer is convenient to update.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com