Secure chip key issuing system and secure chip key issuing method
A key issuer and security technology, applied in the field of information security, can solve problems such as security risks, achieve the effects of high security, prevent illegal monitoring or interception, and enhance security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The chip key issuing system and method thereof of the present invention will be further described in detail below in conjunction with the accompanying drawings.
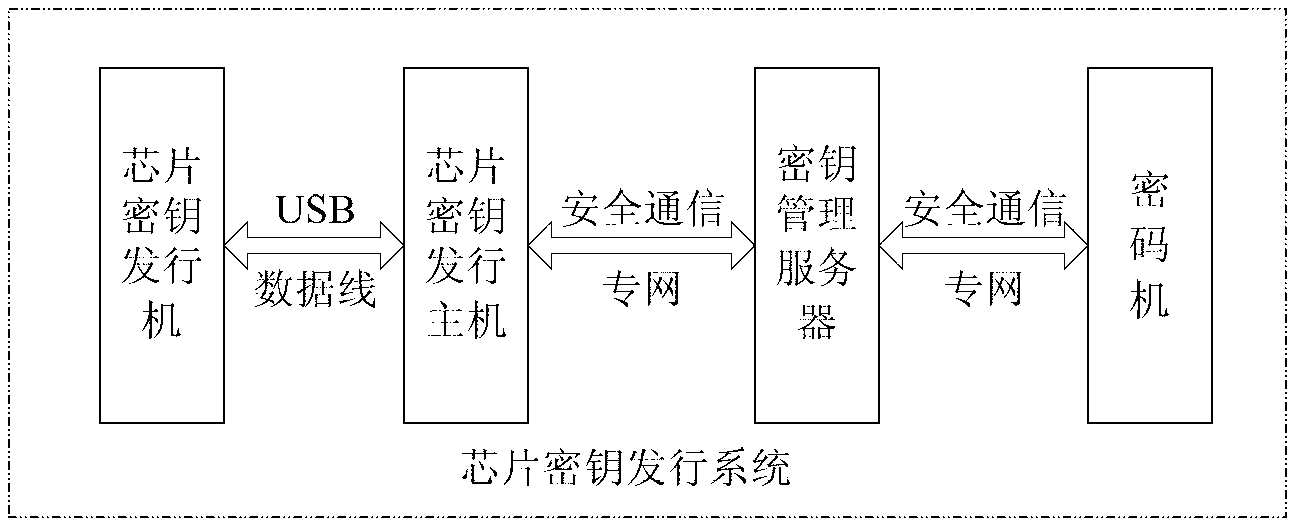
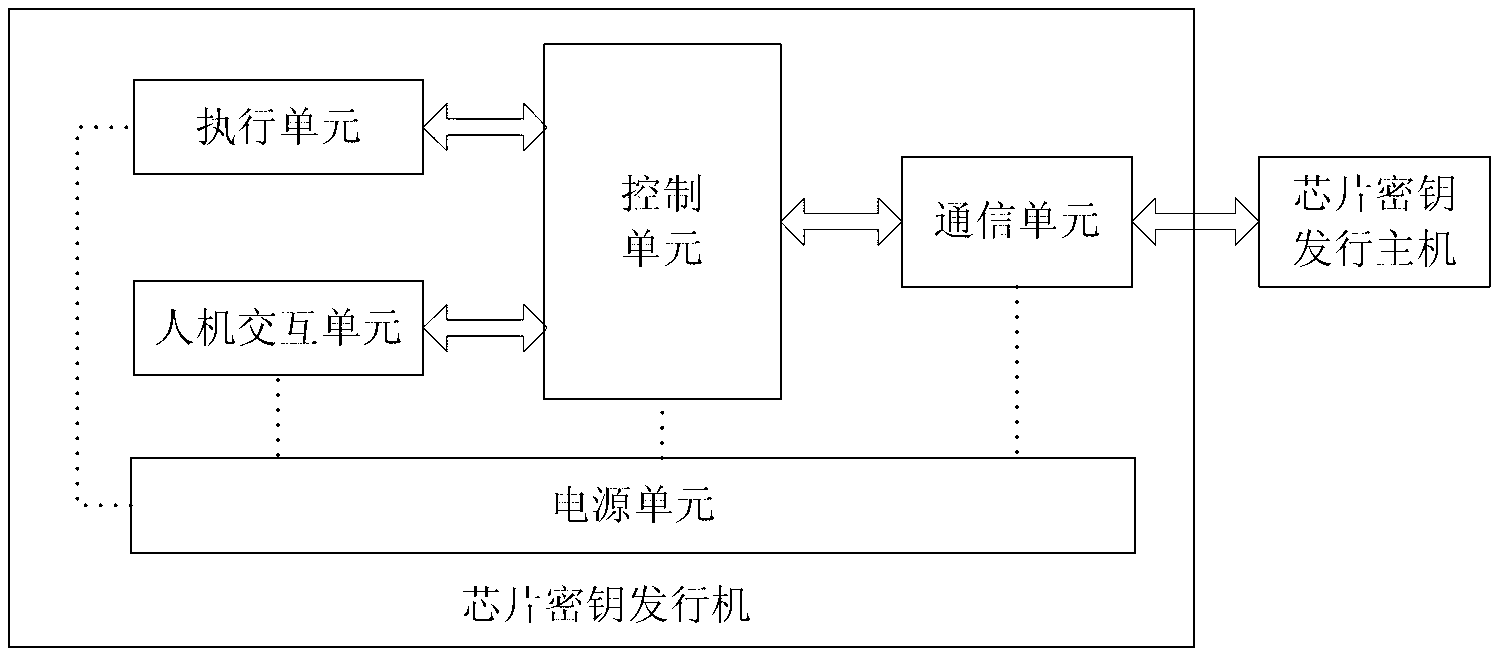
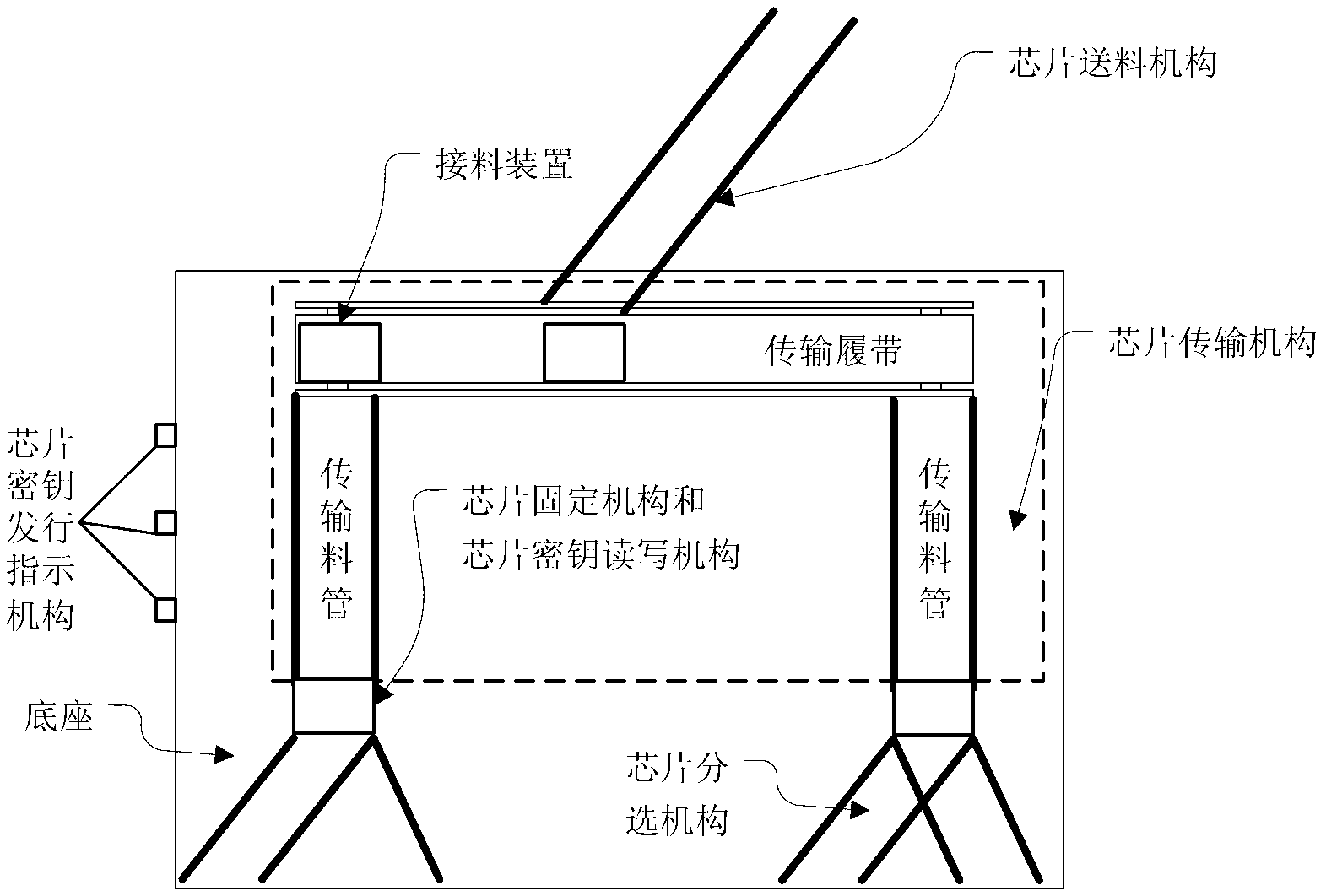
[0047] like figure 1As shown, the chip key issuing system in this example includes a chip key issuing machine, a chip key issuing host, a key management server and a cryptographic machine. The chip key issuing machine is mainly used to send the key issuing request instruction, write all kinds of keys required into the chip to be issued, and negotiate the session key with the encryption machine; the chip key issuing host is installed with the chip key Issuing software is mainly used to store key files, control the opening and closing of the data communication port connected to the chip key issuing machine, transmit the key and key issuance request information, control the issuance of chip key information and detect whether the issuance is successful; The key management server is mainly used to receive the key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com