Secure chip
A security chip and hardware security technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems of high waste rate of hardware resources, reduced security, high chip cost, etc., to extend product cycle, improve security, and reduce chip cost Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
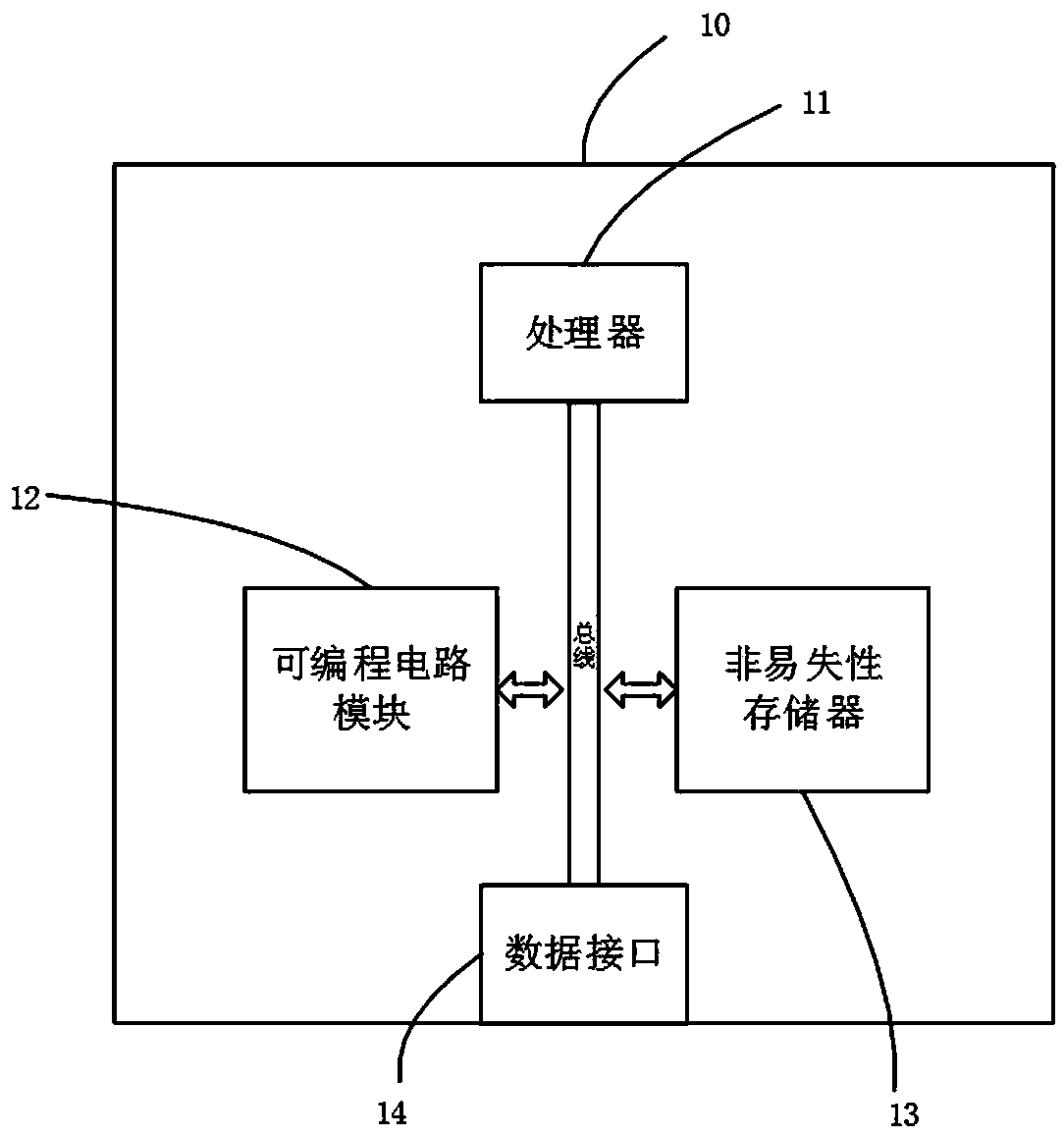
[0020] like figure 2 As shown, in the embodiment of the present invention, a security chip 10 is provided, which includes a processor 11, a programmable circuit module 12, a non-volatile memory 13 and a data interface 14, the programmable circuit module 12, the The non-volatile memory 13 and the data interface 14 are connected to the processor 11 through a bus.
[0021] The processor 11 is the master device on the internal bus of the security chip 10, and is used to read and execute instructions from the non-volatile memory 13, and to complete the chip by reading and writing access to each module in the chip. various functional operations.
[0022] The programmable circuit module 12 is used to implement the hardware security circuit of the security chip according to a preset configuration file. The programmable circuit module 12 is implemented using eFPGA (embedded Field Programmable Gate Array, embedded Field Programmable Gate Array) technology. The hardware security circ...
Embodiment 2
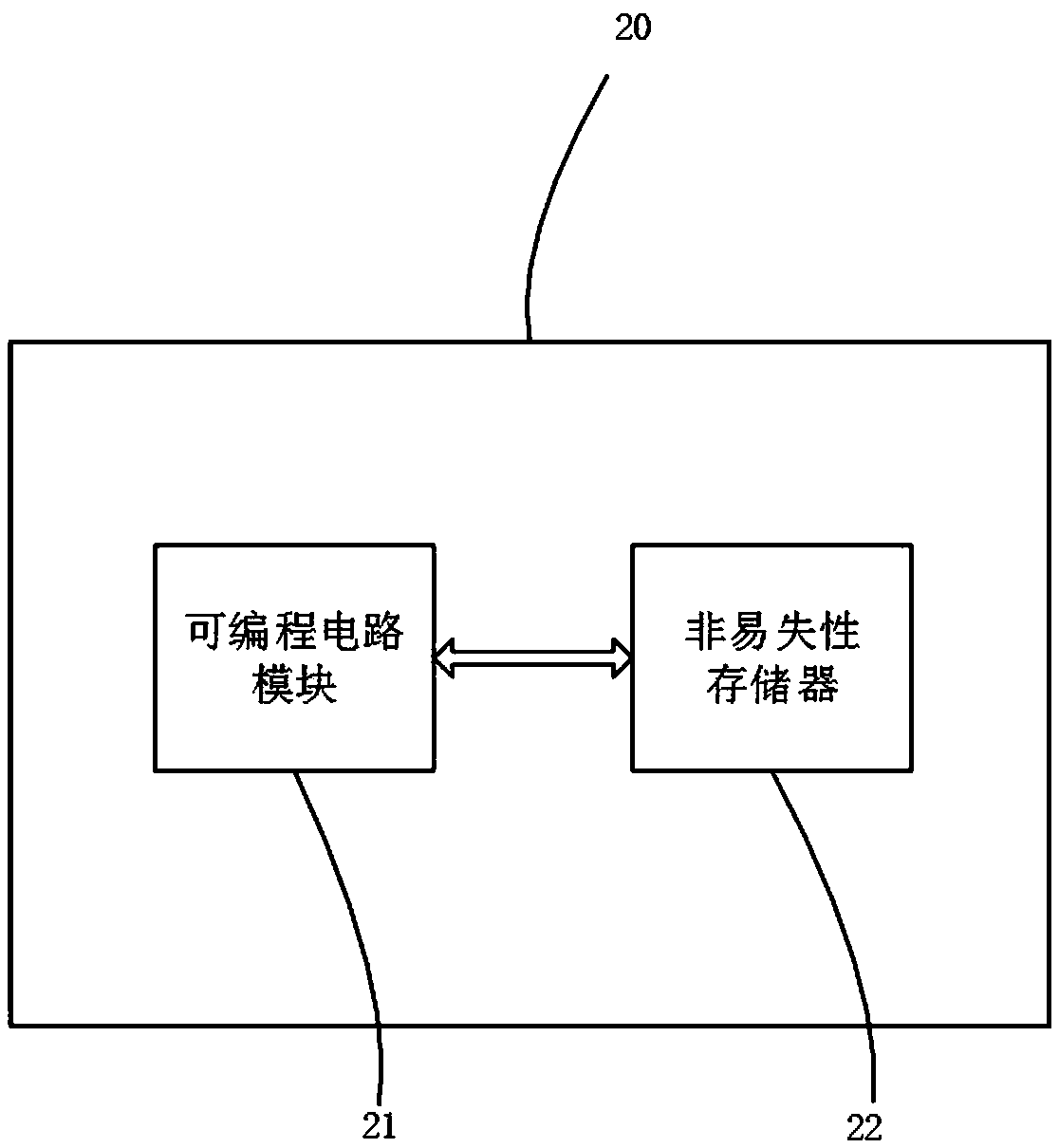
[0027] like image 3 As shown, in this embodiment, a security chip 20 is provided, which includes a programmable circuit module 21 and a non-volatile memory 22, and the programmable circuit module 21 is used to realize the described The hardware security circuit of the security chip, the non-volatile memory 22 is used to store the preset configuration file. The hardware security circuit includes one or more of a cryptographic algorithm circuit, a key extraction and protection circuit, a data encryption storage circuit, and a data download and management circuit.
[0028] The programmable circuit module 21 is implemented using eFPGA technology. Further, the programmable circuit module 21 is also used to implement circuits such as a processor, a bus, and a data interface.
[0029] It should be noted that the second embodiment is based on the same inventive concept as the first embodiment, and the technical means and technical effects it adopts are basically the same as those o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com