Secure card communication method based on credible environment, and mobile terminal
A technology for secure communication and mobile terminals, applied in the field of card-based secure communication methods and mobile terminals, can solve the problems of personal information data leakage, forgery and duplication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
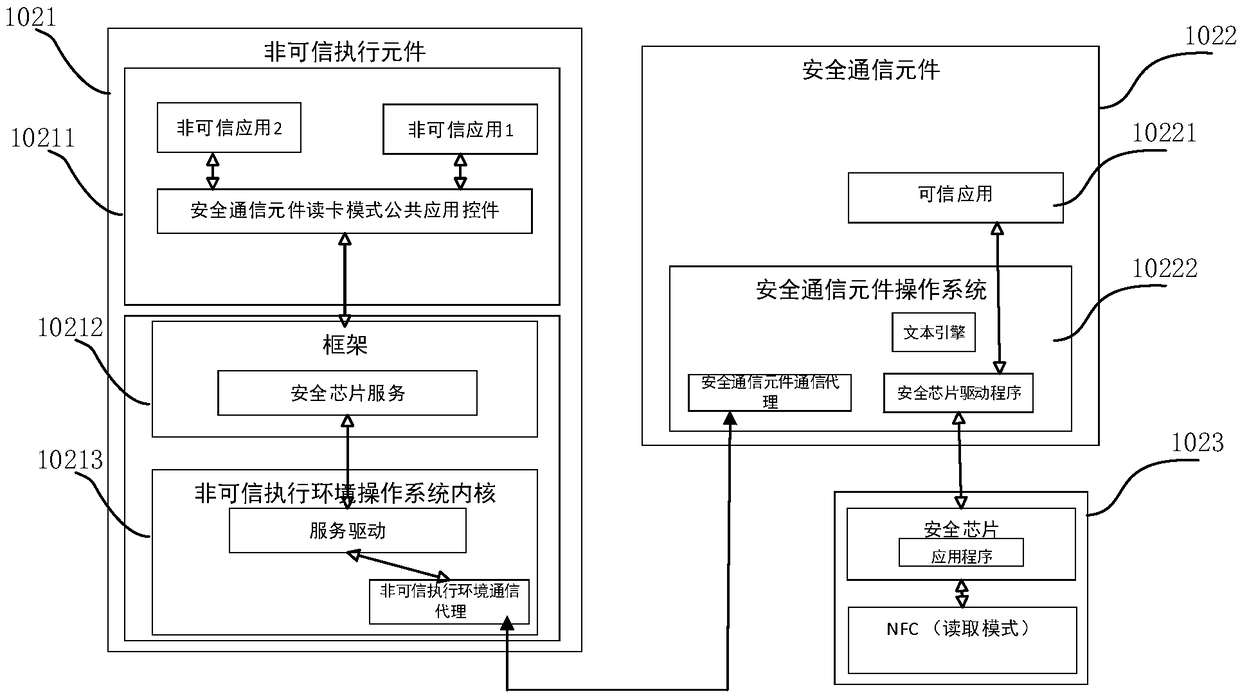
[0033] Combined with the above figure 1 The structure of the safety communication system is introduced, and the following is combined with the attached figure 2 The specific structure of the mobile terminal 102 in this application is further introduced, wherein the mobile terminal 102 includes an untrusted execution element 1021 , a secure communication element 1022 and a security chip 1023 . The untrusted execution element 1021 and the secure communication element 1022 are hardware or software integrated on the chip card in the mobile terminal to realize the communication function of the mobile terminal.
[0034] Among them, the untrusted execution element 1021 includes a three-layer structure, namely the application layer 10211, the framework layer 10212, the untrusted execution element operating system kernel 10213, and the application layer 10211 includes various public applications and controls, and the front server for implementation and business processing and other e...
Embodiment 2
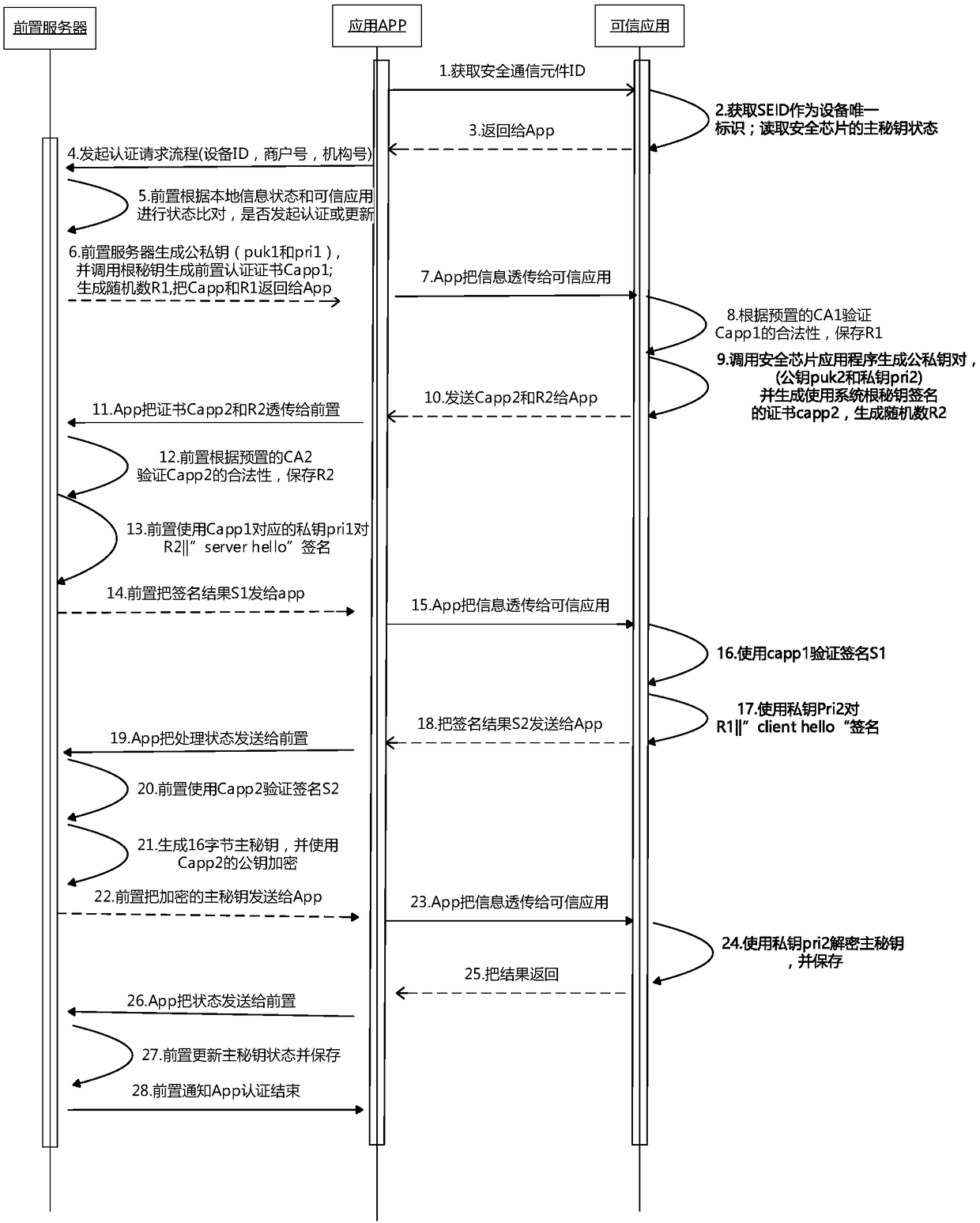
[0038] The structures of the secure communication system and the mobile terminal have been described above, and the working methods of the secure communication system and the mobile terminal are introduced below. The secure communication method includes the following steps:
[0039] Step S310, in response to the wireless communication information sent by the physical card, the security chip encrypts the received wireless communication information.
[0040]Step S320, sending the encrypted wireless communication information to a secure communication element;
[0041] Step S330, the secure communication element forwards the wireless communication information to the public application;
[0042] Step S340, the public application sends the wireless communication information to the service processing front-end server for processing.
[0043] Two-way authentication is implemented between the front-end server for business processing and the trusted application of the secure communicat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com