Ciphertext generation method, ciphertext decryption method and encryption/ decryption device
A ciphertext and technology to be encrypted, which is applied in the field of communication security, can solve problems such as low security, and achieve the effect of solving low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
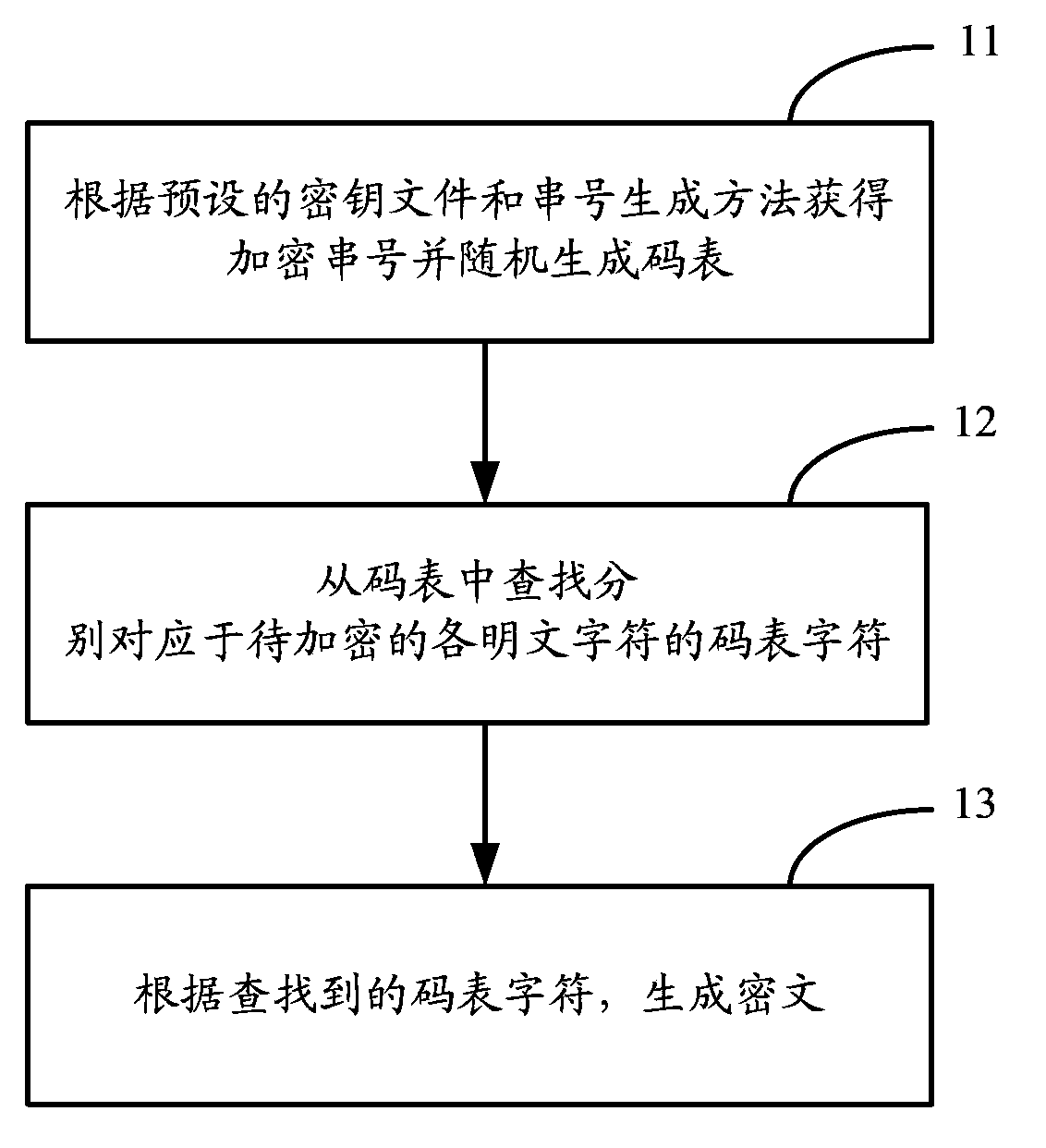
[0030] Based on the above basic idea, the flow chart of a method for generating ciphertext provided by the embodiment of the present invention is as follows figure 1 As shown, it specifically includes the following steps:
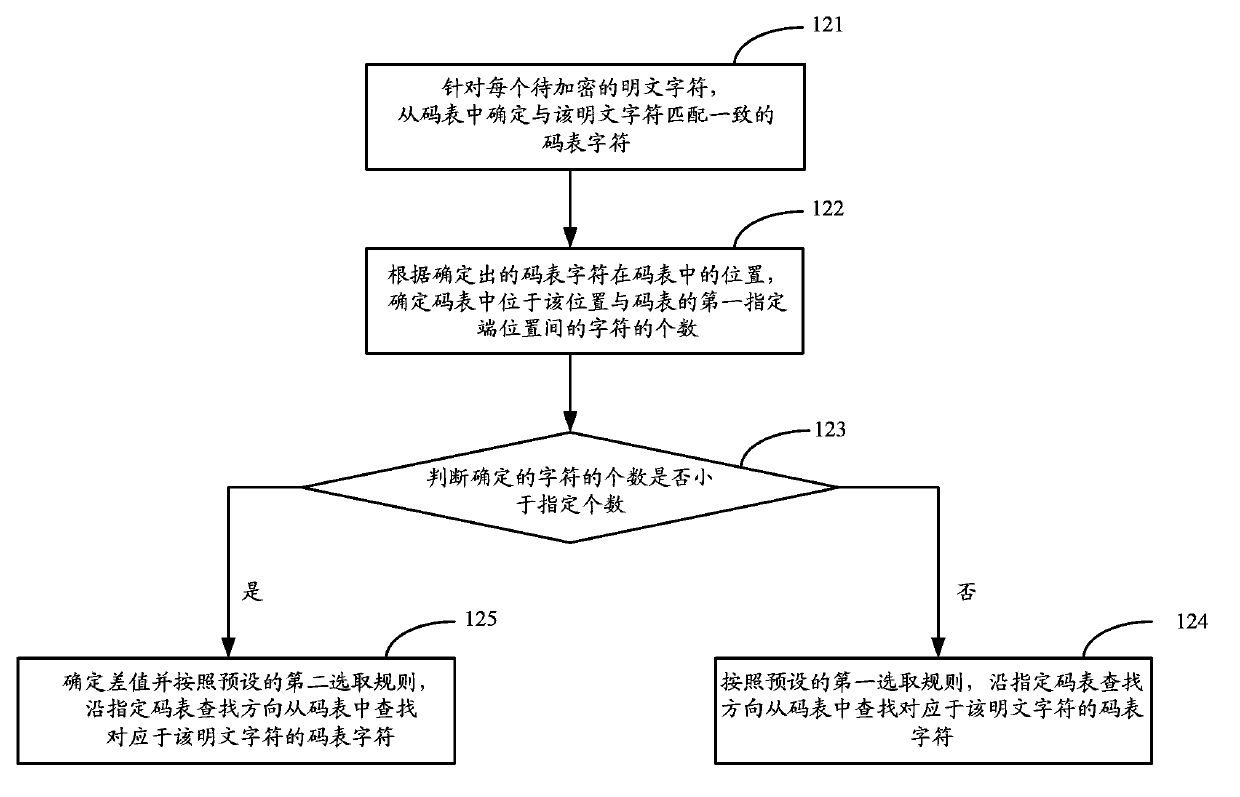
[0031] Step 11. Obtain the encrypted serial number according to the preset key file and serial number generation method, and randomly generate a code table, which is a string composed of the above-mentioned code table characters arranged randomly.
[0032] Wherein, the preset key file may be a text file, and the content of the file may be a character string composed of numbers and / or letters of an indeterminate length, as long as the length is no less than 8 bits and no more than 65535 bits.
[0033] There are many ways to generate the serial number, for example, the number of characters contained in the key file can be used as the encrypted serial number; the number of digits contained in the key file can be used as the encrypted serial number; The number...
Embodiment 2
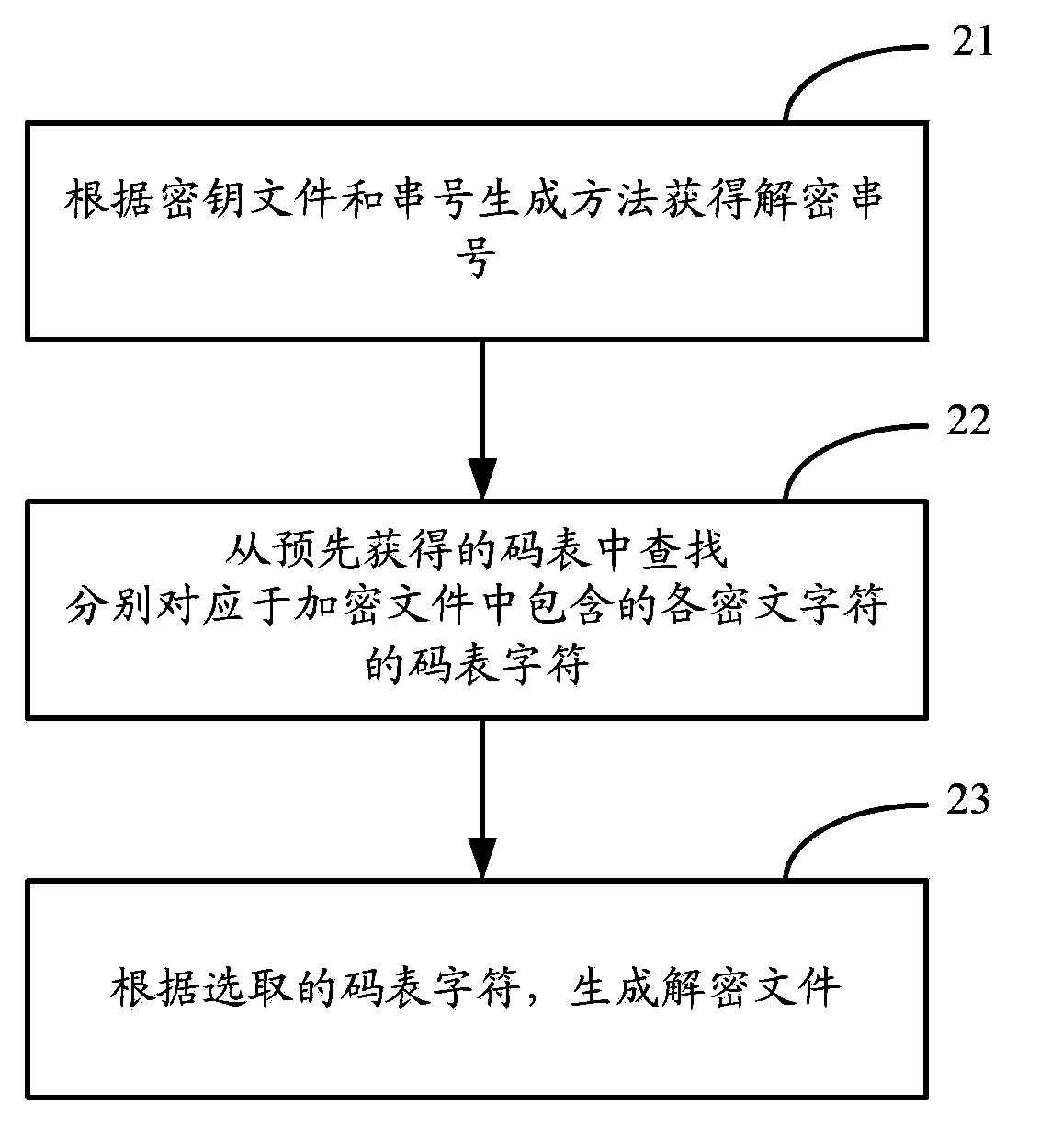
[0072] The method for generating ciphertext and the method for decrypting ciphertext provided by the embodiment of the present invention will be specifically described below in combination with examples.
[0073] First, for the code table, assume that the randomly generated code table is:
[0074] SboJU9#dL,O+a&sh:c / mpIj;*FE_V64]Dvz0uf7yCnM.~)t\rKxA
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com