Unlocking method, server, mobile terminal, electronic lock and unlocking system
A mobile terminal and electronic lock technology, applied in the field of communication, can solve the problems of difficulty in unlocking processing, high cost of electronic locks, high requirements for electronic lock memory and processor computing performance, etc., and meet the requirements of reducing computing performance, Avoid costly effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
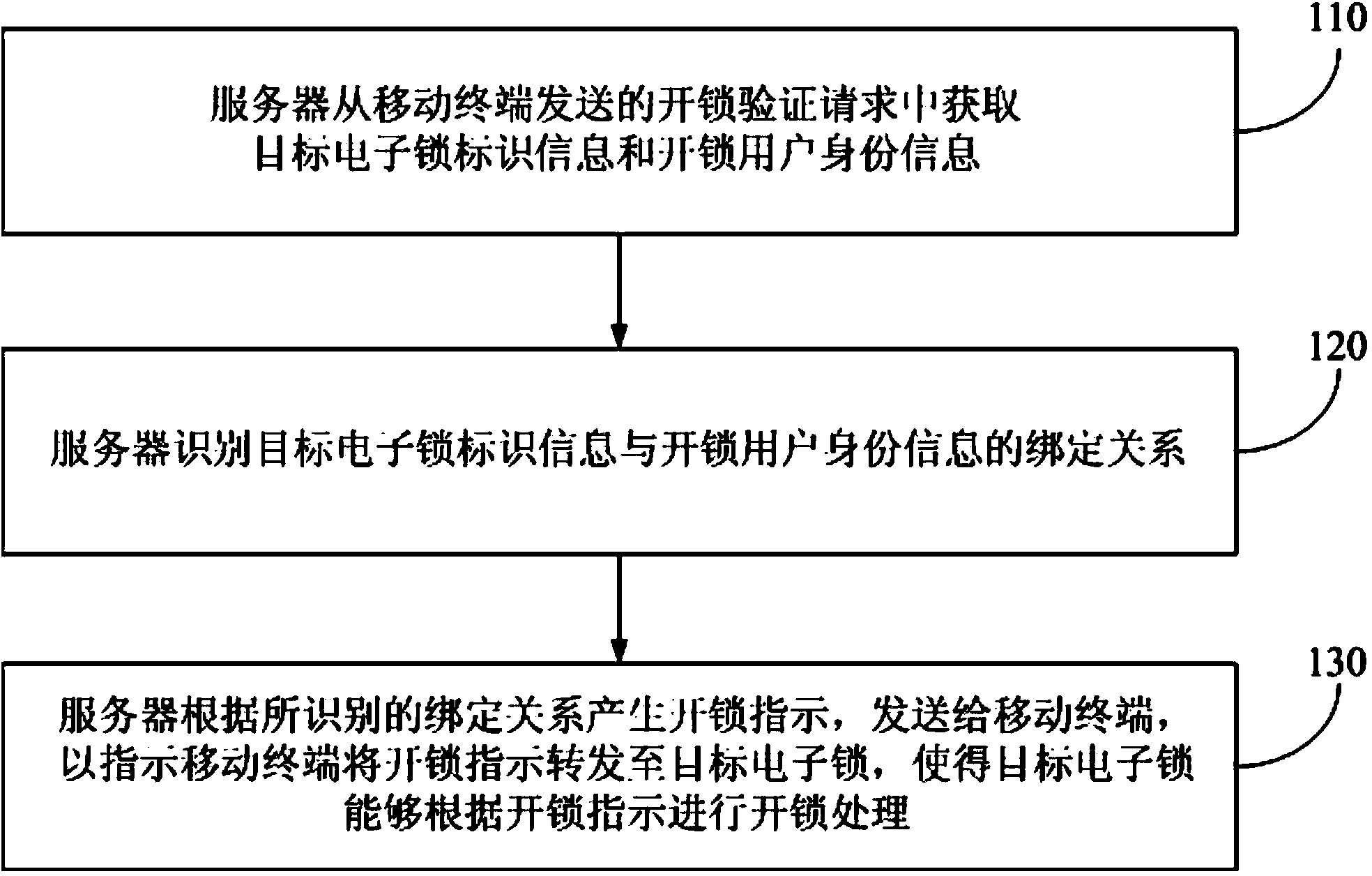
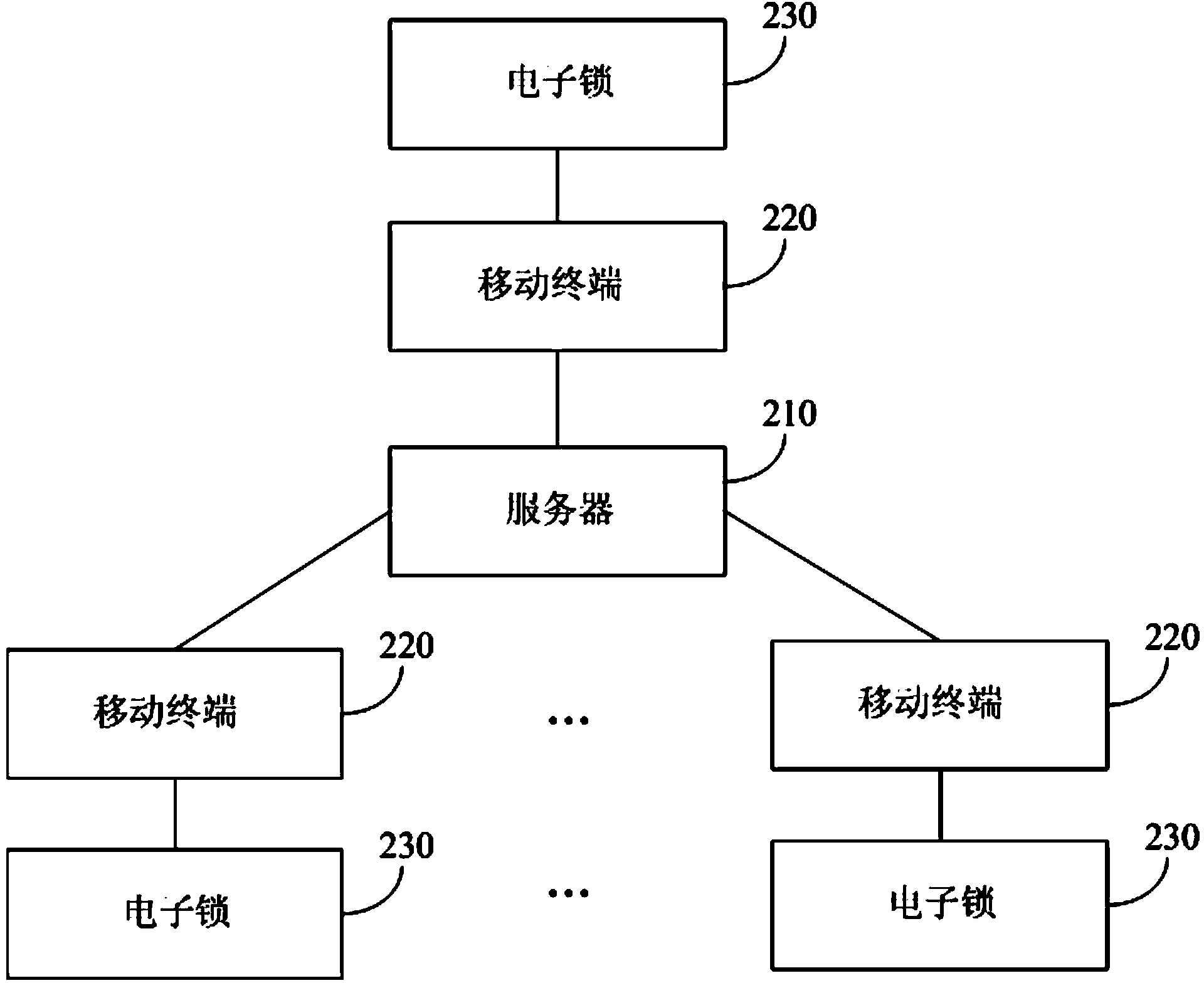
[0052] figure 1 It is a schematic flowchart of an unlocking method provided in Embodiment 1 of the present invention. figure 2 It is a schematic diagram of a system architecture used by the unlocking method provided in this embodiment. see figure 2 , the system architecture includes a server 210, at least one mobile terminal 220, and an electronic lock 230 corresponding to each mobile terminal, wherein the server 210 and the mobile terminal 220 can perform data interaction through wireless communication technology, and the mobile terminal 220 and its corresponding electronic lock 230 can Data interaction is carried out through short-range wireless communication technology. The unlocking method described in this embodiment is executed by the server. For convenience of description, this embodiment will take a mobile terminal and its corresponding electronic lock (target electronic lock) in the network architecture as an example to illustrate the technical solution of the un...
Embodiment 2
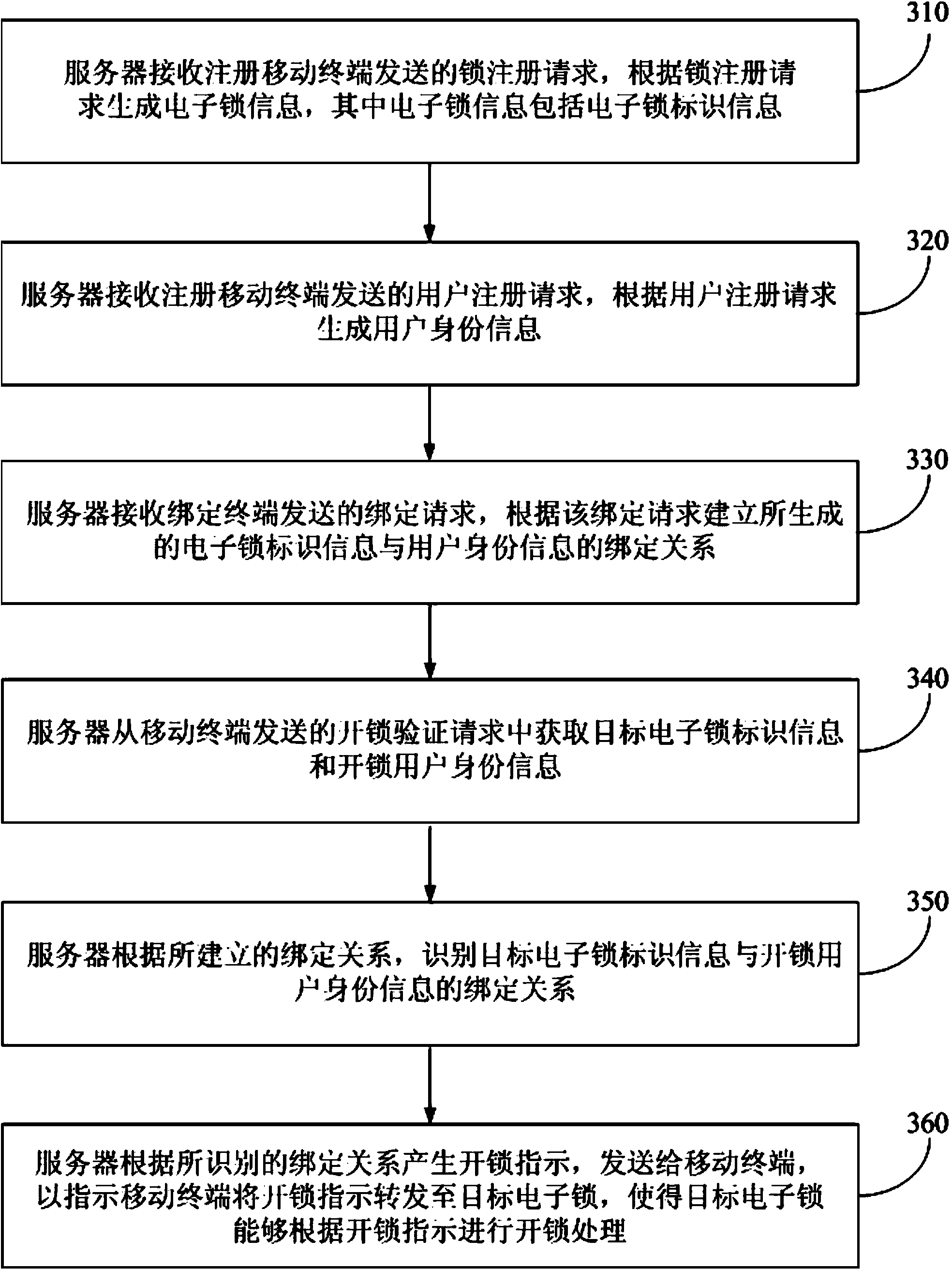
[0069] image 3 It is a schematic flowchart of an unlocking method provided in Embodiment 2 of the present invention. This embodiment adds an electronic lock registration step, a user registration step, and an electronic lock user binding step on the basis of the first embodiment above. The unlocking method is still executed by the server. join image 3 , the unlocking method specifically includes the following steps:
[0070] 310. The server receives the lock registration request sent by the registered mobile terminal, and generates electronic lock information according to the lock registration request, wherein the electronic lock information includes electronic lock identification information;
[0071] 320. The server receives the user registration request sent by the registered mobile terminal, and generates user identity information according to the user registration request;
[0072] 330. The server receives the binding request sent by the binding terminal, and establ...
Embodiment 3
[0119] Figure 7 It is a schematic flowchart of another unlocking method provided by the third embodiment of the present invention. This method can still be applied to figure 2 in the system architecture shown. The unlocking method described in this embodiment is executed by the mobile terminal, and may be executed in cooperation with the aforementioned unlocking method implemented by the server. see Figure 7 , the unlocking method specifically includes the following steps:
[0120] 710. The mobile terminal obtains the identification information of the target electronic lock;
[0121] 720. The mobile terminal obtains the identity information of the unlocking user;
[0122] 730. The mobile terminal sends an unlock verification request containing the target electronic lock identification information and the unlock user identity information to the server;
[0123] 740. The mobile terminal receives the unlocking instruction returned by the server according to the unlocking...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com